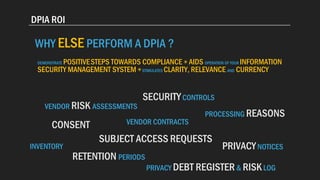
The document is a practical guide for conducting a Data Privacy Impact Assessment (DPIA) to ensure compliance with GDPR and assess risks associated with personal data processing. It outlines steps for preparation, discovery, and remediation, emphasizing the importance of involving stakeholders and following best practices to mitigate privacy risks. Failing to perform a DPIA when necessary can lead to significant fines from supervisory authorities.