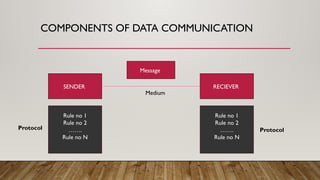
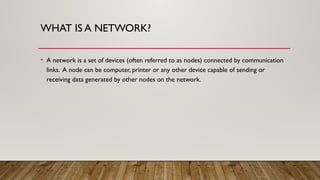
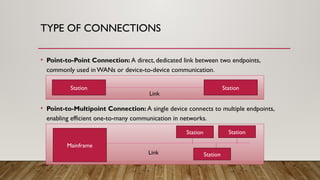
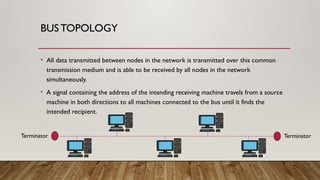
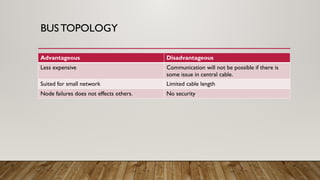
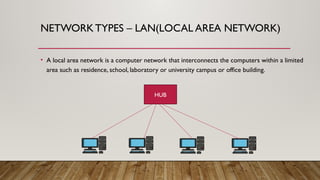
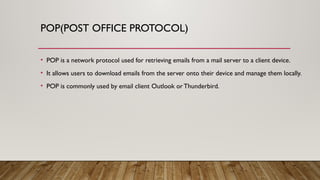
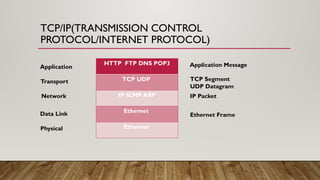
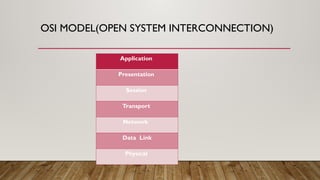
The document provides an overview of data communication and networking concepts, including components of data communication, data flow types, network types, protocols, and the OSI model. It explains different network topologies such as bus, ring, star, and mesh, along with their advantages and disadvantages. Additionally, the document covers various protocols like TCP, IP, and SMTP, which facilitate data transmission and communication between devices.