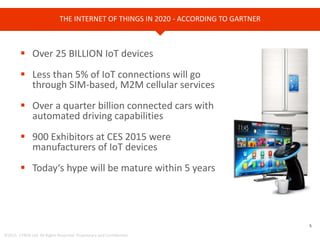
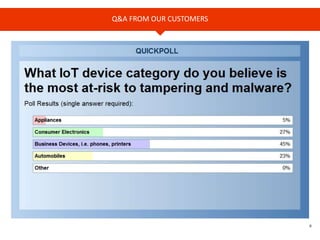
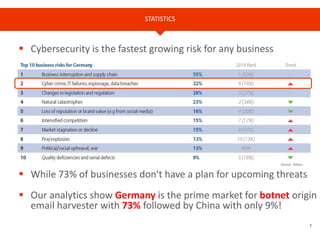
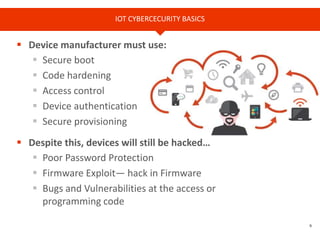
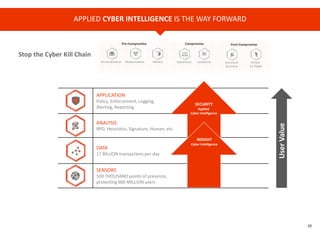
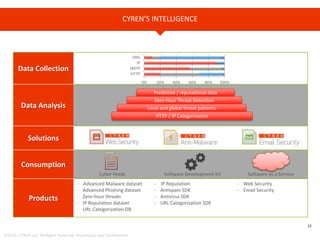
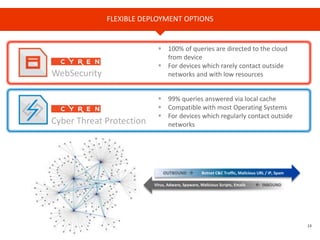
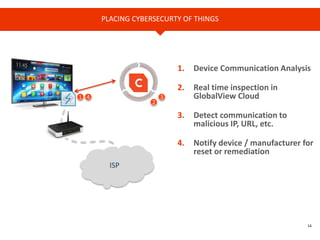
The document provides an overview of Cyren, a cybersecurity company, and its role in the rapidly growing Internet of Things (IoT) market. It highlights the increasing importance of cybersecurity, noting that many businesses lack plans for emerging threats, and stresses the necessity for device manufacturers to implement security measures. Cyren offers a range of cybersecurity solutions and emphasizes the need for protecting IoT devices through real-time analysis and cloud-based services.