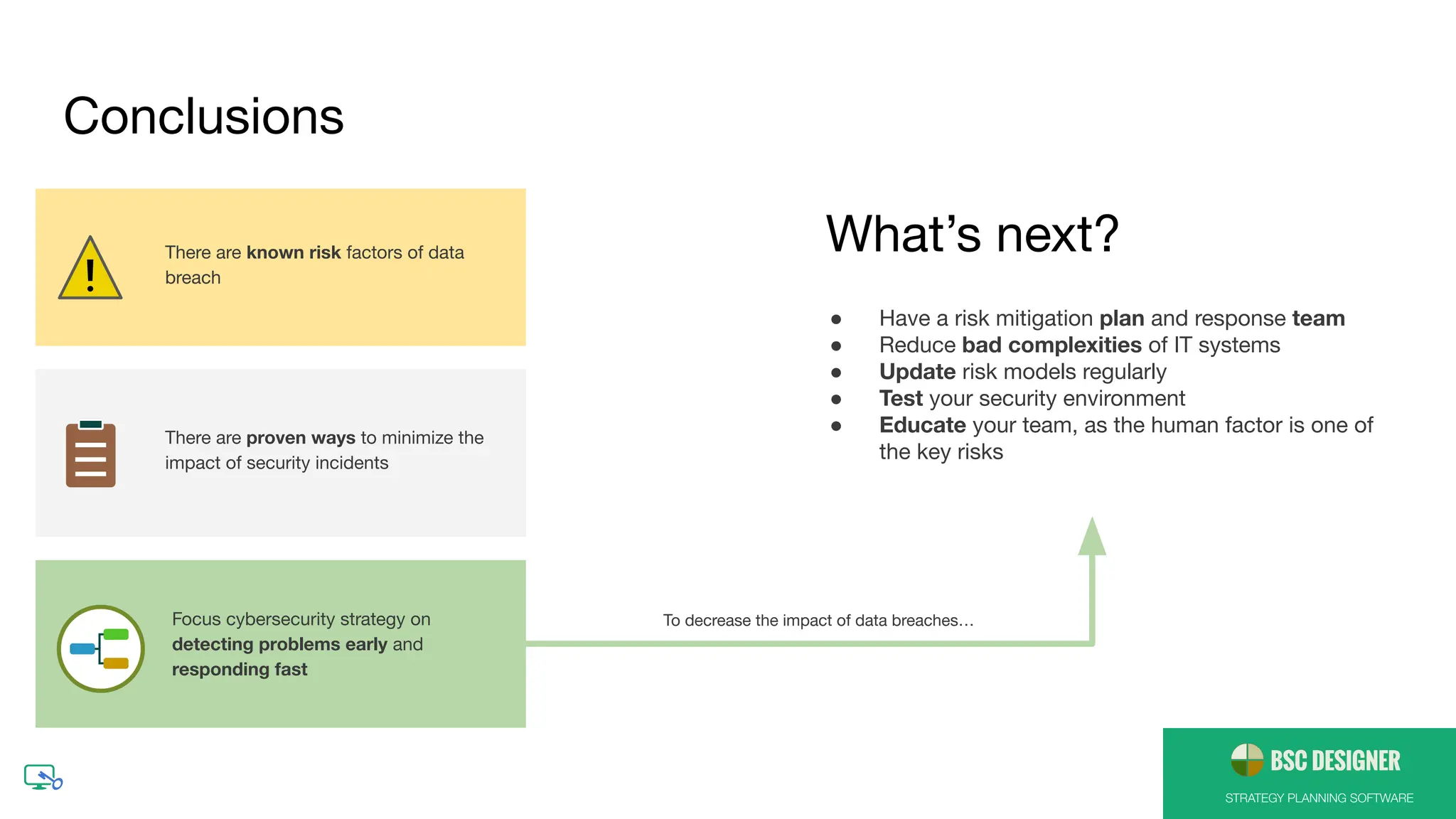
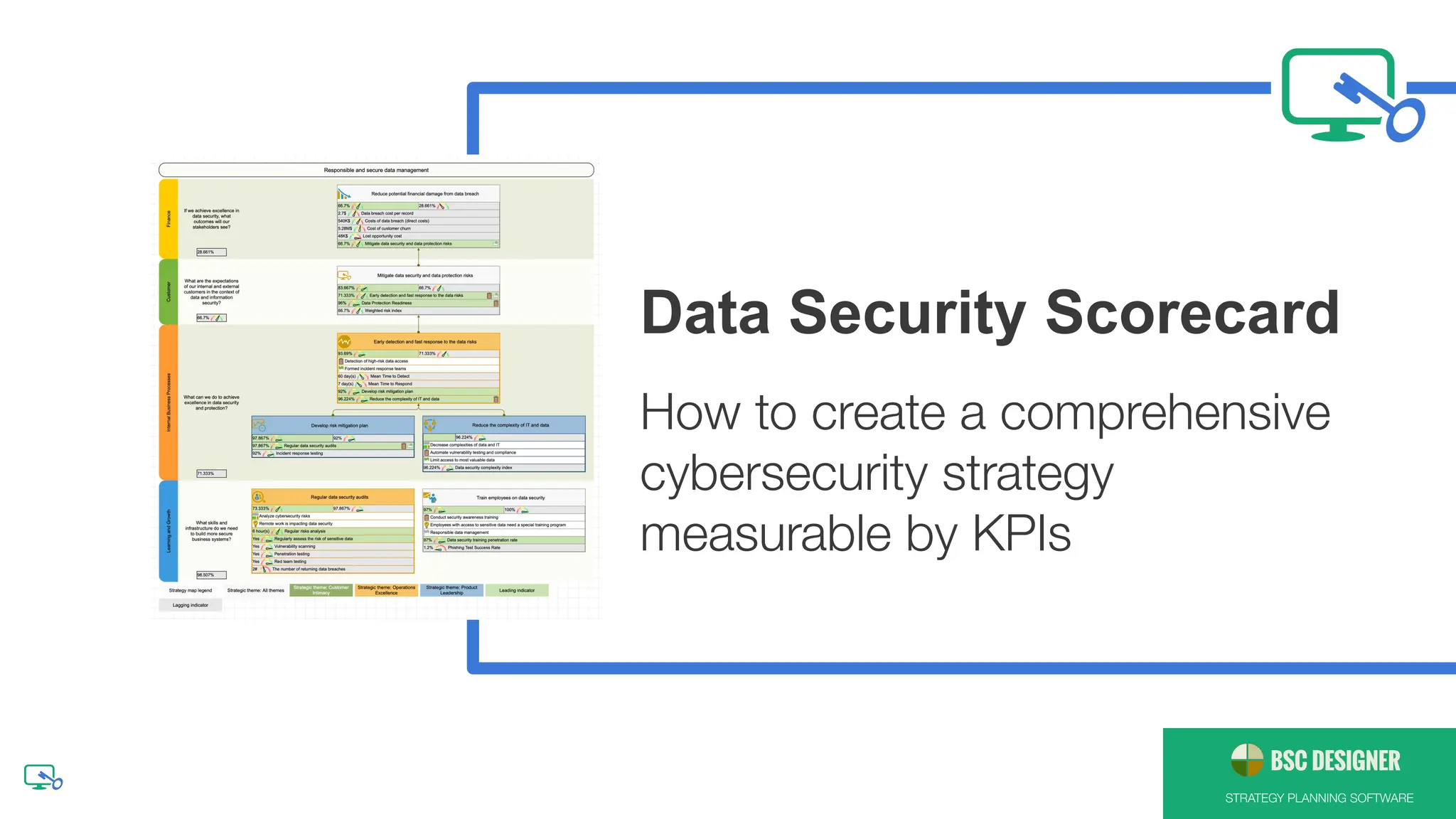
The document outlines how to create a comprehensive cybersecurity strategy, emphasizing the importance of measurable KPIs and the alignment of cybersecurity initiatives with broader organizational goals. It identifies key factors that contribute to data breaches and suggests proven methods to minimize their impact, such as implementing security automation, preparing a response team, and educating employees. Additionally, it highlights the importance of regularly updating risk models and testing security environments to effectively mitigate risks.

![STRATEGY PLANNING SOFTWARE
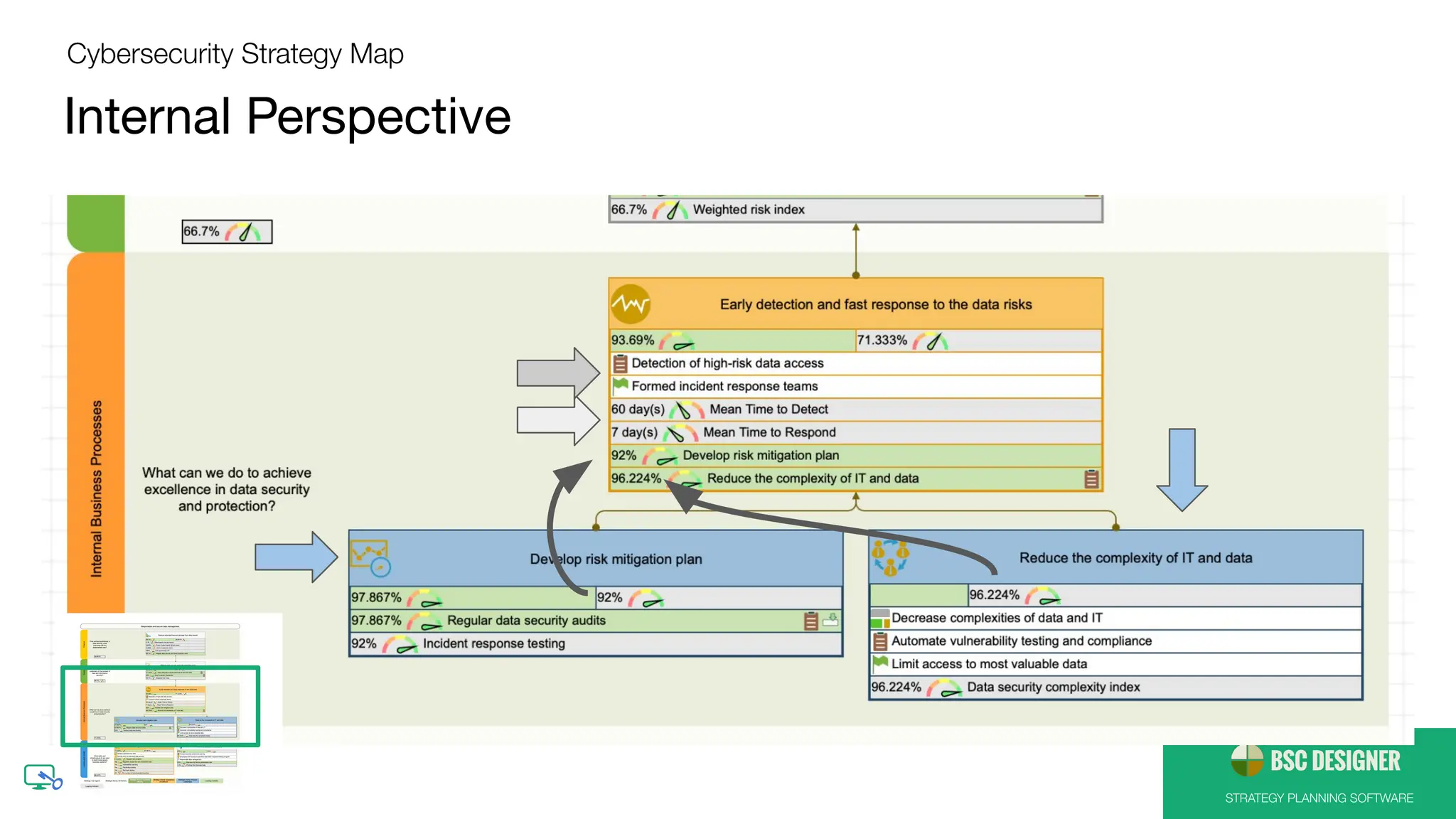
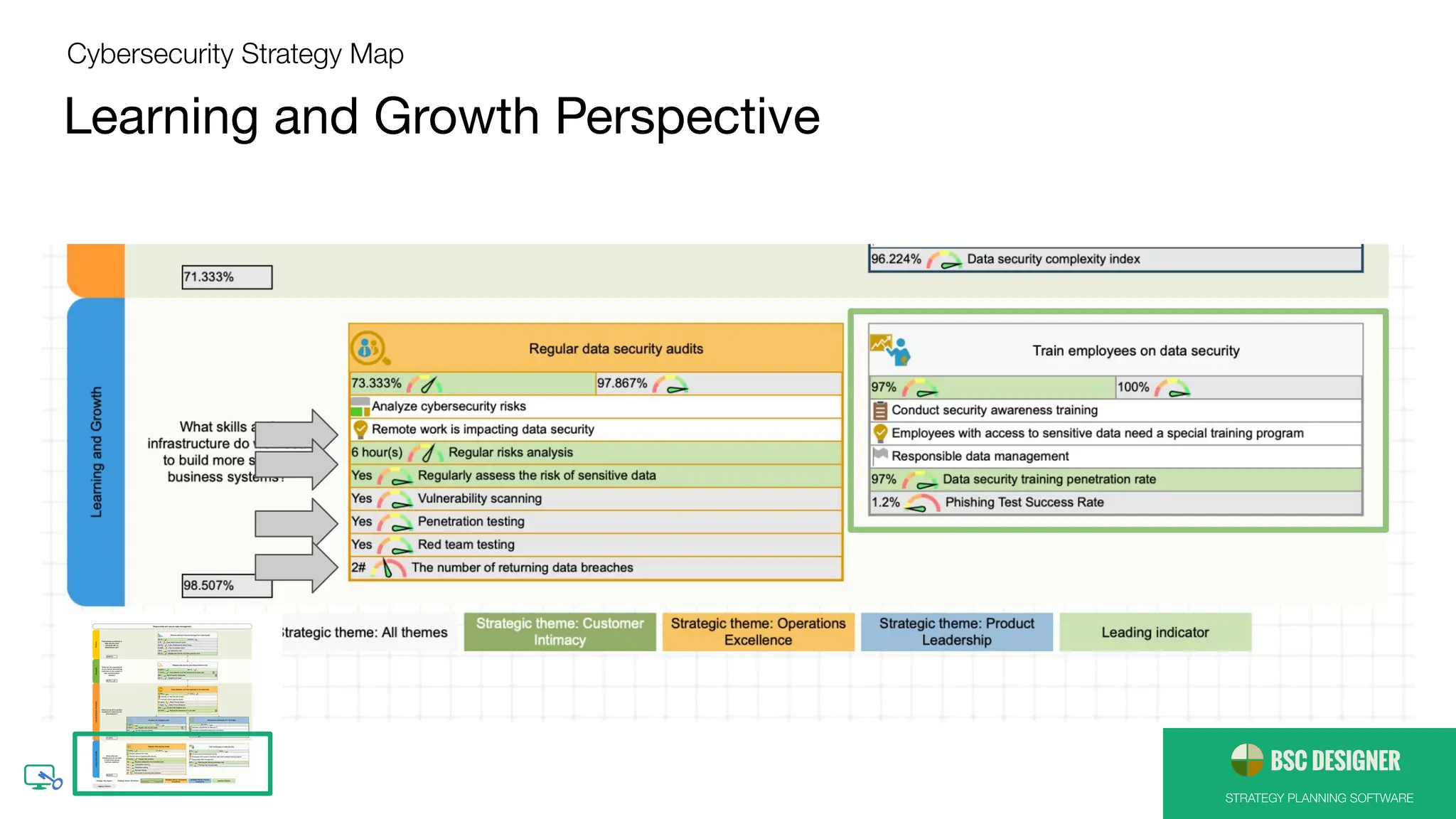
Outcomes and Drivers of Cybersecurity Strategy
● Implement security automation
● Have a response team and response plan
ready
● Educate employees
● Test business environment
Expected
outcomes
Drivers
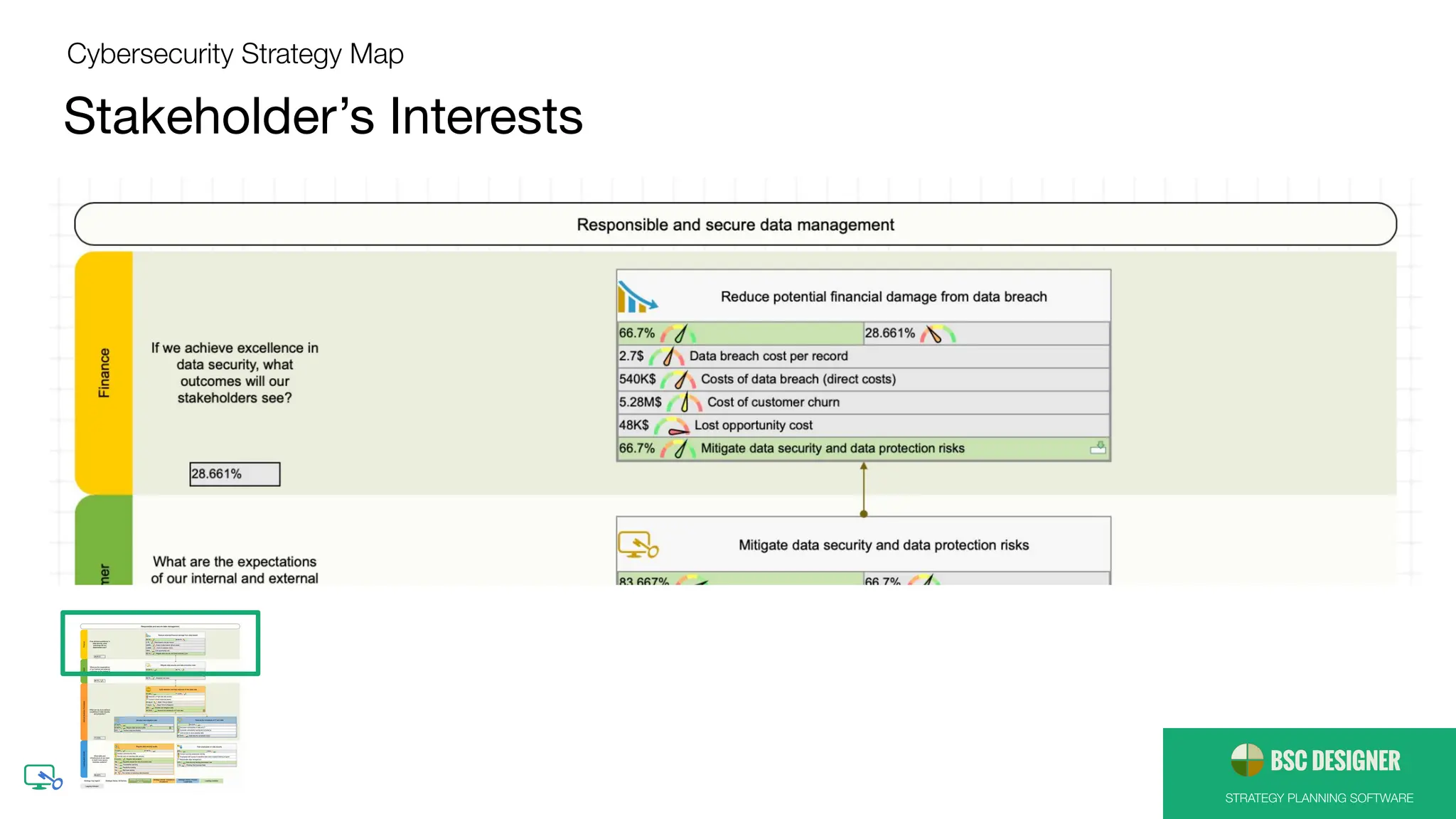
● [Stakeholders] Reduce potential financial
damage from data breach
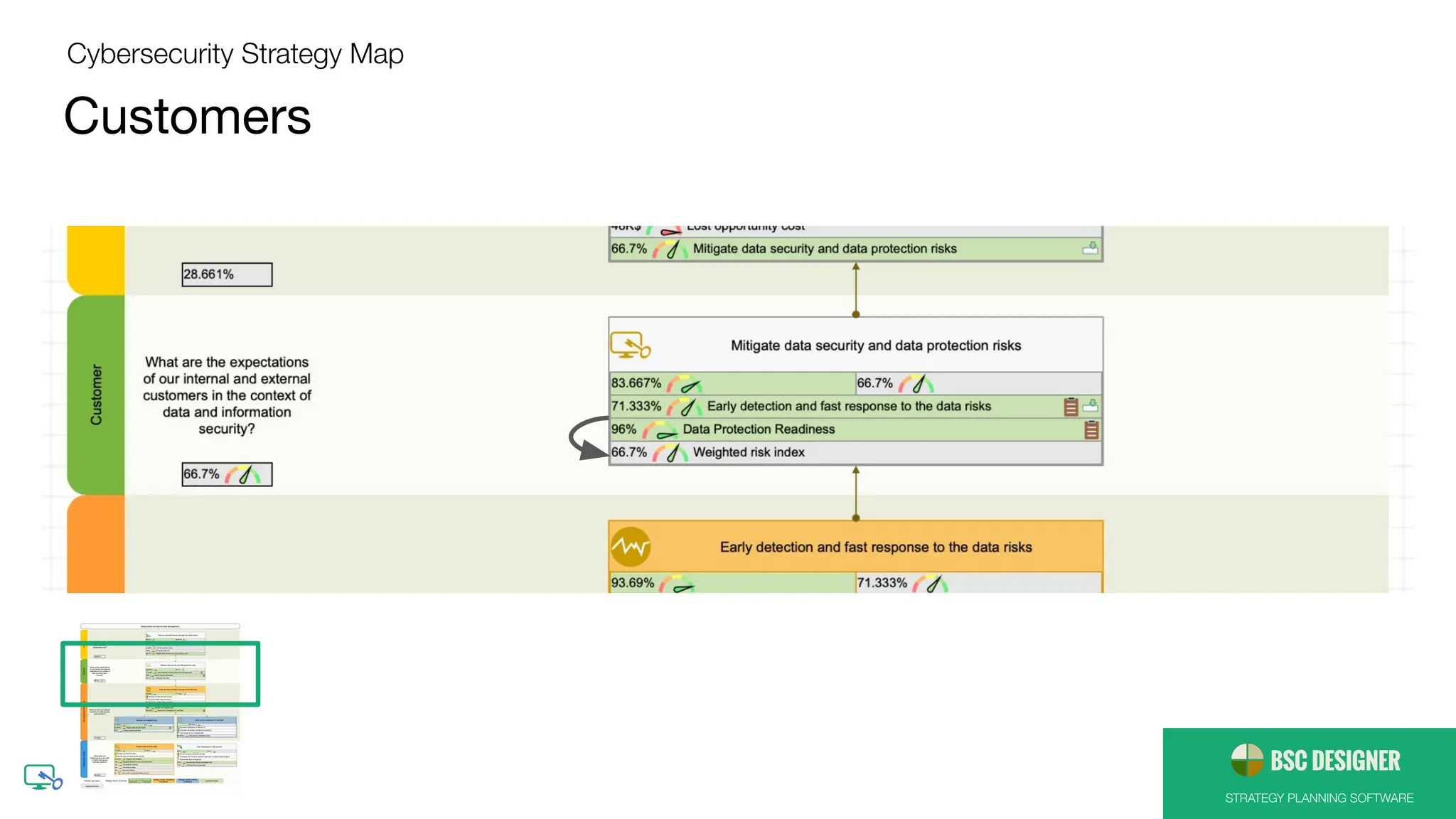
● [Customers] Mitigate data security and data
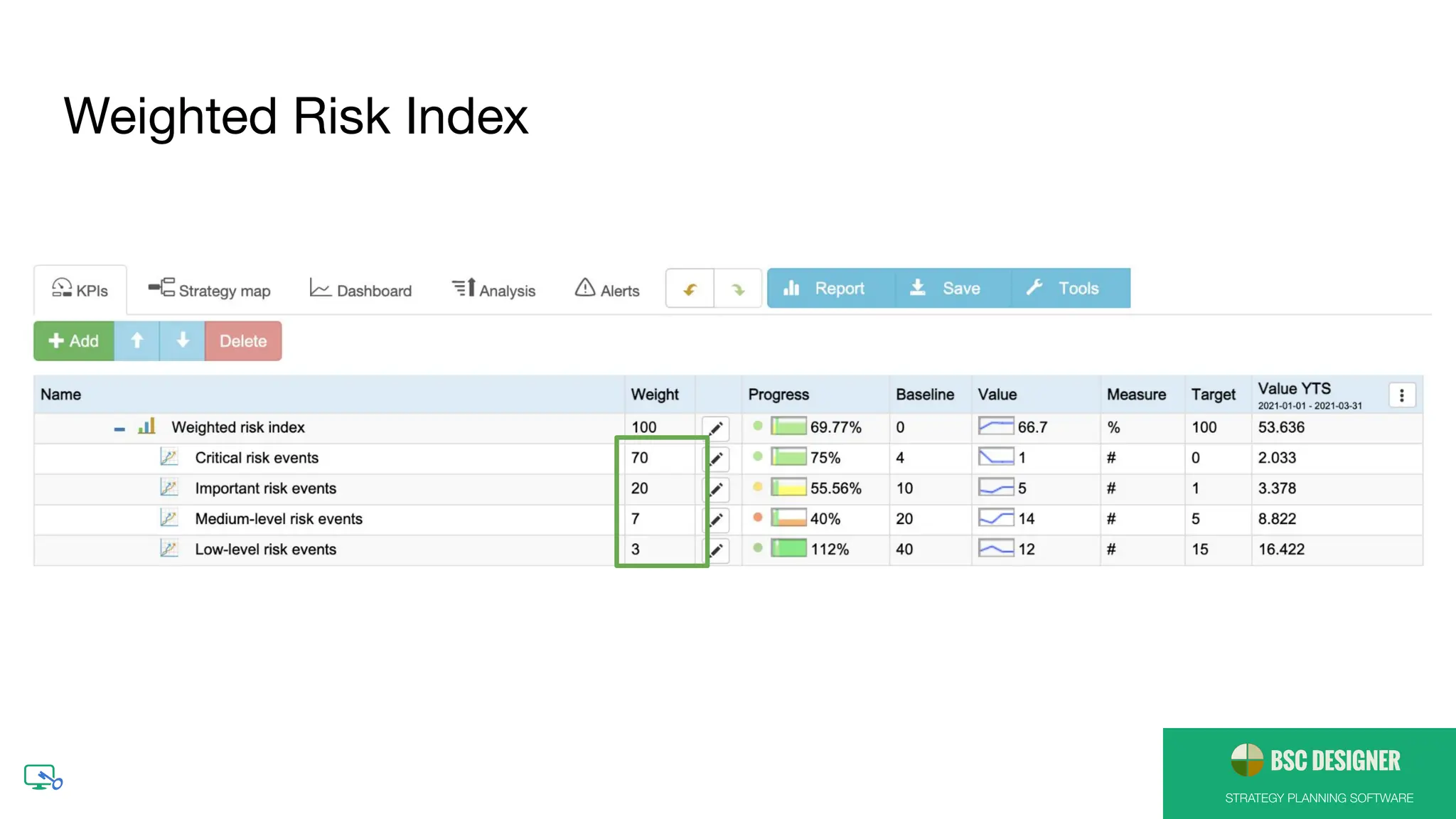
protection risks
* Access Cybersecurity Strategy template under the BSC Designer free plan](https://image.slidesharecdn.com/en-cybersecurityvideo-240606214220-c9b56911/75/Cybersecurity-Strategy-Building-a-Balanced-Scorecard-with-Effective-KPIs-5-2048.jpg)