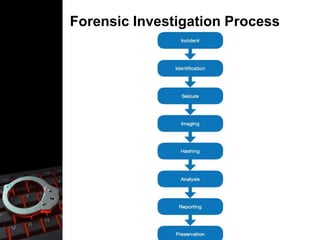
Jay Mehta is a cyber forensics investigator. His responsibilities include identifying and preserving crime scenes and evidence, documenting findings, and maintaining chain of custody of electronic evidence. Cyber forensics is important because digital evidence can be altered, damaged, or destroyed easily and crosses borders quickly. Various groups like law enforcement, companies and individuals use cyber forensics to investigate crimes and lawsuits.