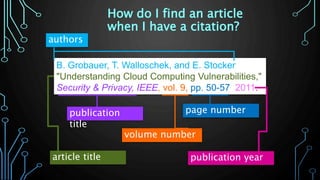
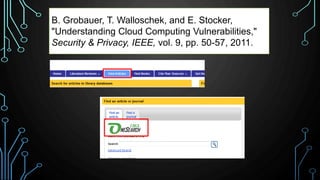
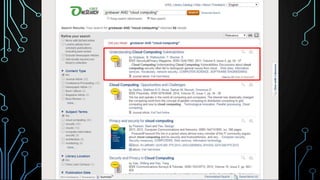
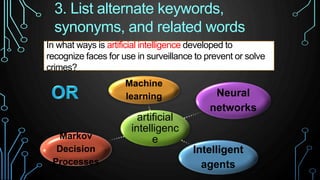
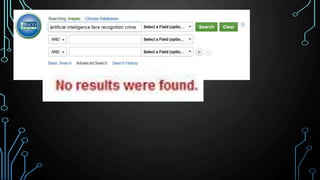
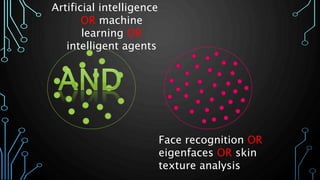
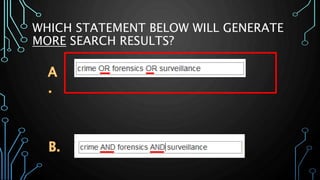
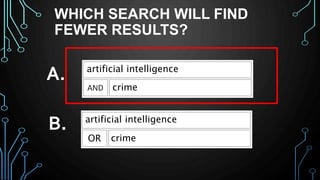
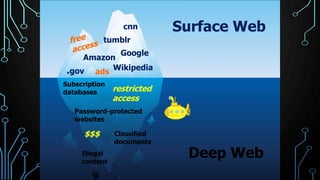
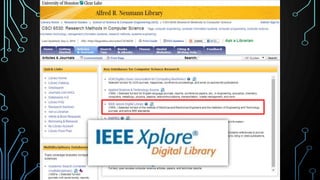
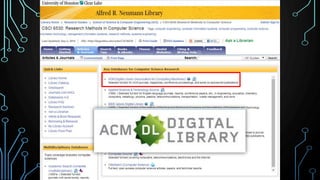
This document provides an overview of research for computer science. It discusses academic research, reviewing literature, authoritative sources, and peer review. It covers different types of scholarly sources like journals, periodicals, and gray literature. It also discusses principles of good searching like determining research questions, keywords, Boolean operators, and database limiters. Finally, it discusses accessing subscription databases and citing sources. The document is intended to help students learn how to effectively conduct research for computer science topics.