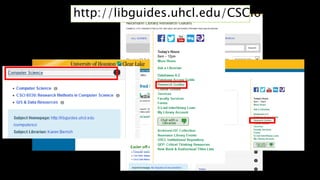
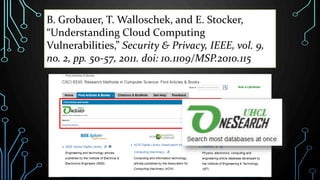
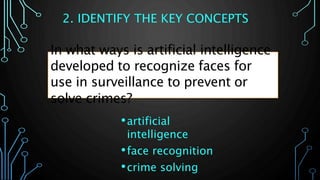
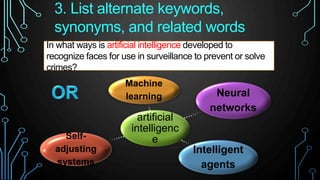
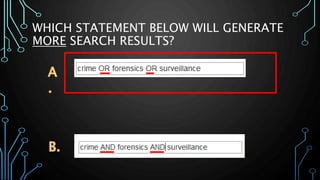
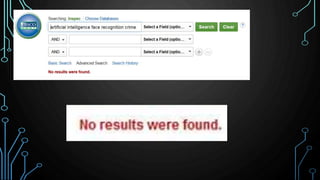
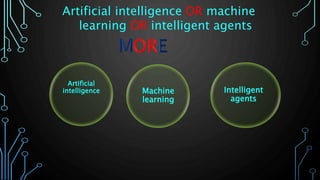
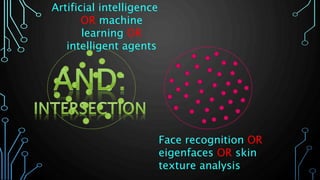
This document provides an overview of conducting academic research for computer science. It discusses key aspects of the research process such as literature reviews, peer review, and types of scholarly sources. It also outlines principles of effective searching, including developing a research question, identifying key concepts, using appropriate search techniques and filters. Finally, it introduces some research databases and tools for locating relevant academic literature.