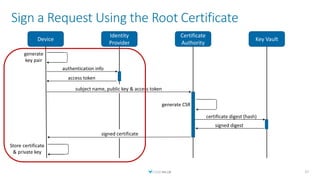
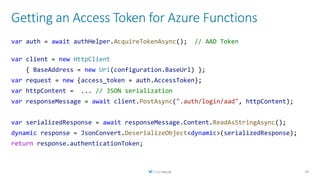
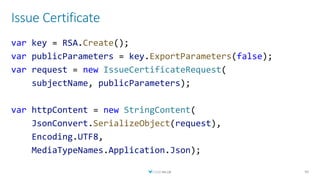
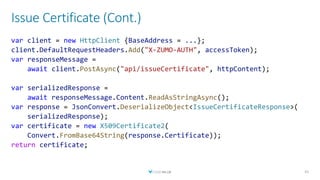
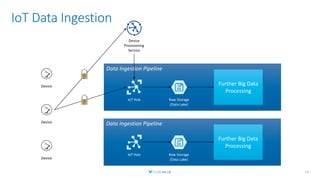
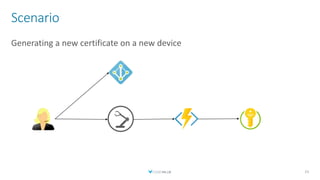
The document discusses creating a serverless Public Key Infrastructure (PKI) using .NET and Azure Key Vault, outlining various aspects such as issuing, managing, and utilizing certificates. It covers the importance of PKI in managing secure communications for IoT devices and provides technical details for implementing a serverless certificate authority. The presentation includes code examples and emphasizes leveraging Azure Key Vault for secure certificate handling.




















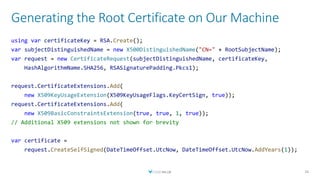


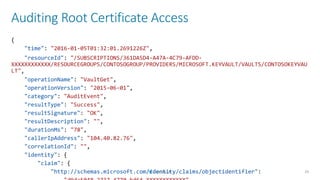
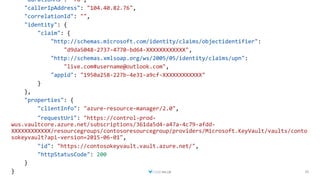

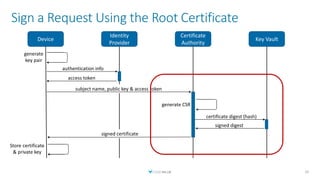
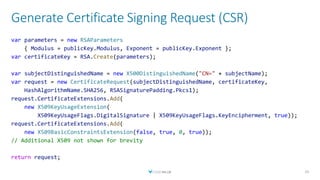
![Sign Certificate with Root Key
34
CertificateRequest request = CreateCertificateRequest(subjectName, certificateKey);
byte[] certificateSerialNumber = await _serialNumberGenerator.GenerateSerialAsync();
RSA rsaKeyVault = _keyVaultClient.ToRSA(
certificateBundle.KeyIdentifier, issuerCertificate);
var generator = X509SignatureGenerator.CreateForRSA(
rsaKeyVault, RSASignaturePadding.Pkcs1);
var certificate = request.Create(
issuerCertificate.SubjectName, generator,
DateTime.Today, DateTime.Today.AddYears(1),
certificateSerialNumber);](https://image.slidesharecdn.com/createyourownserverlesspkiwithnetazurekeyvault-191025173956/85/Create-Your-Own-Serverless-PKI-with-NET-Azure-Key-Vault-33-320.jpg)