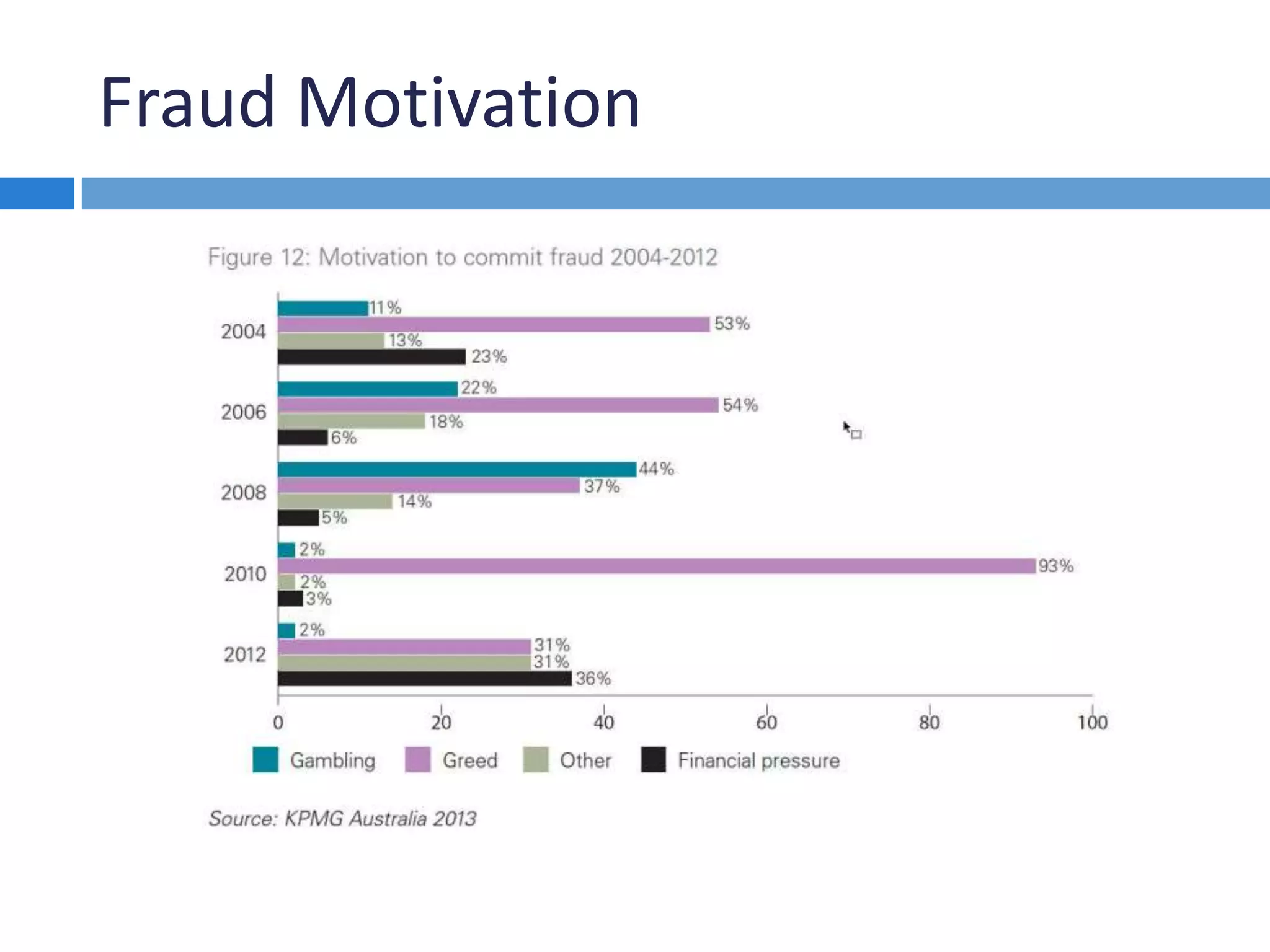
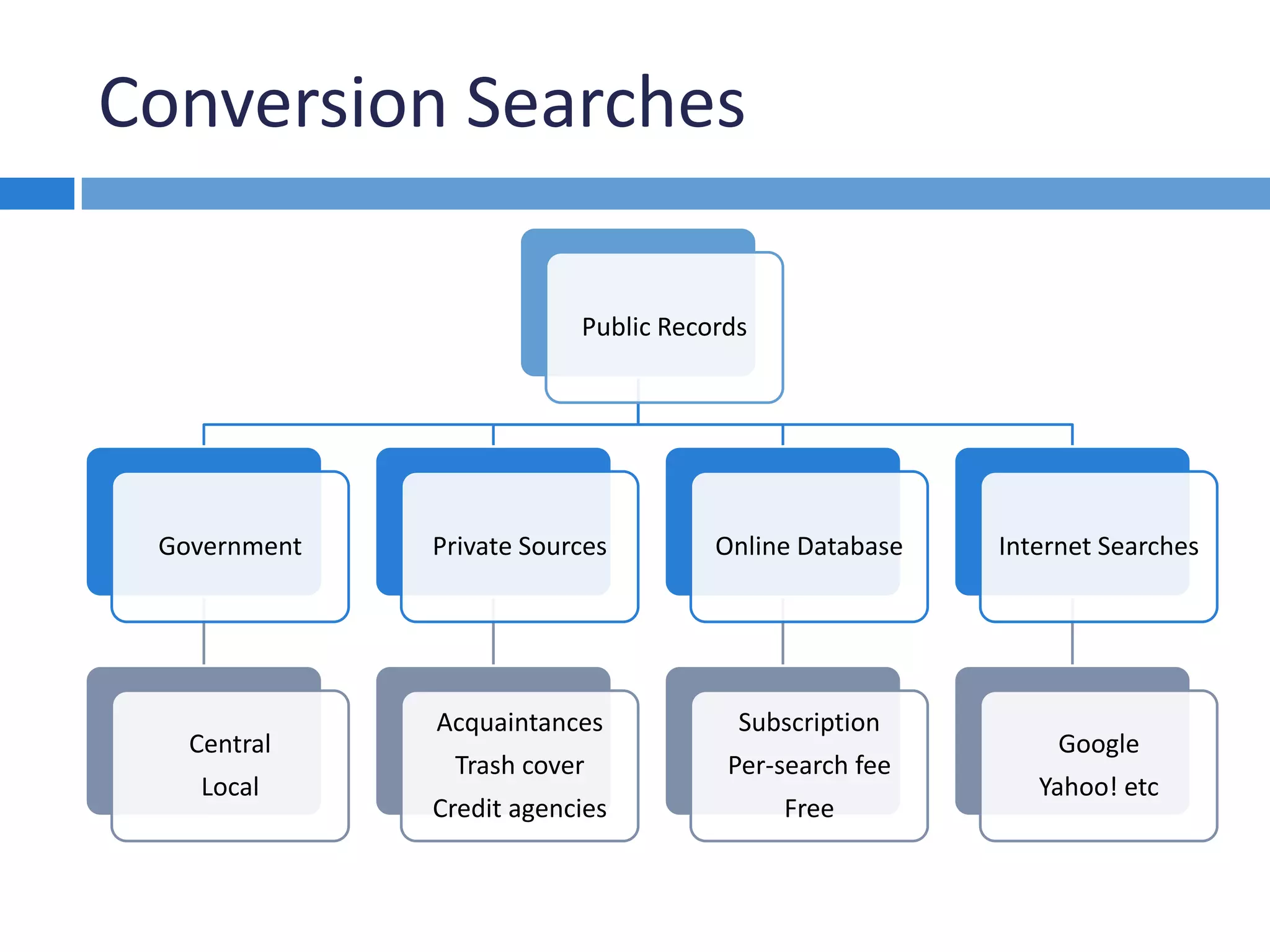
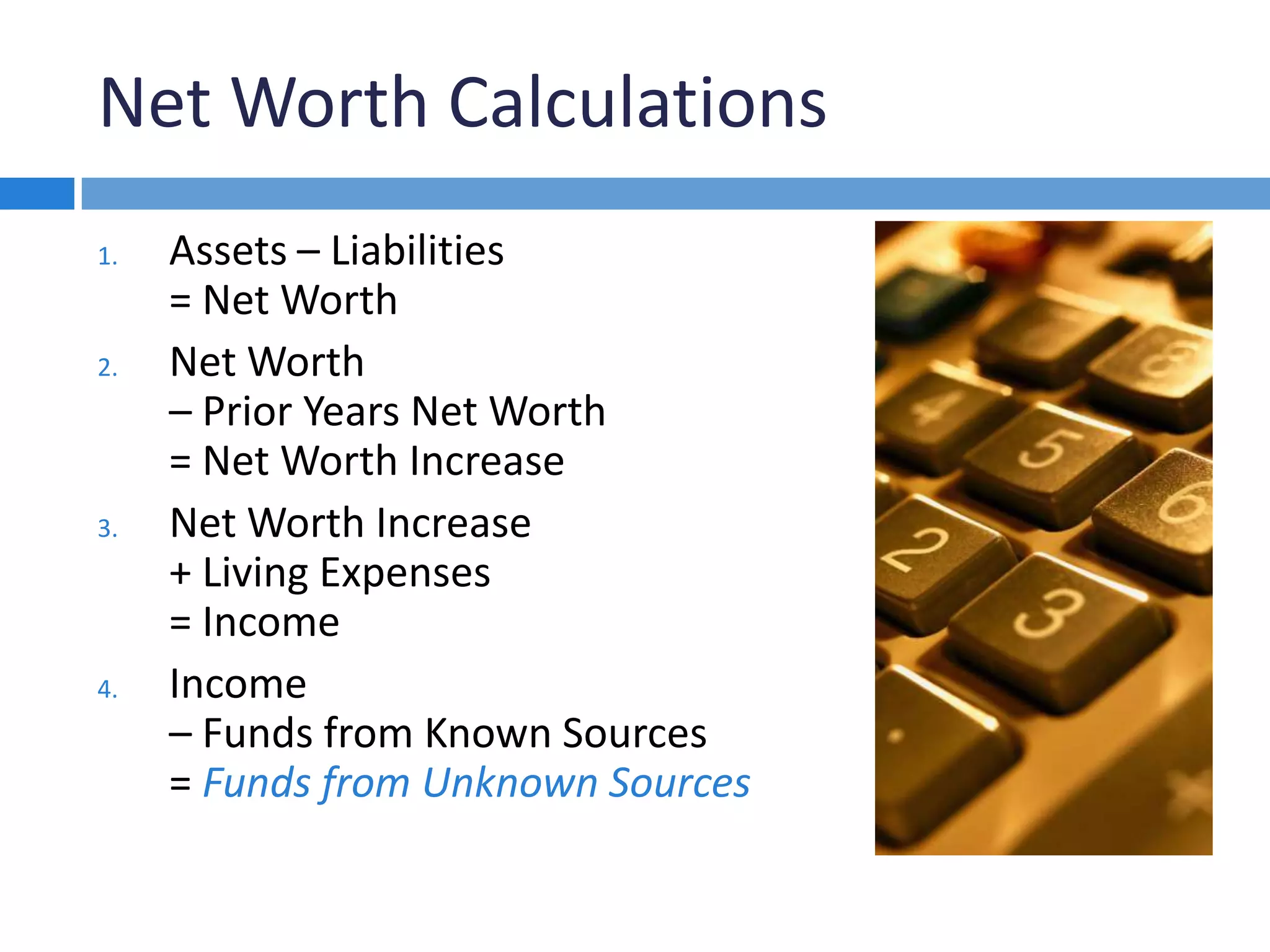
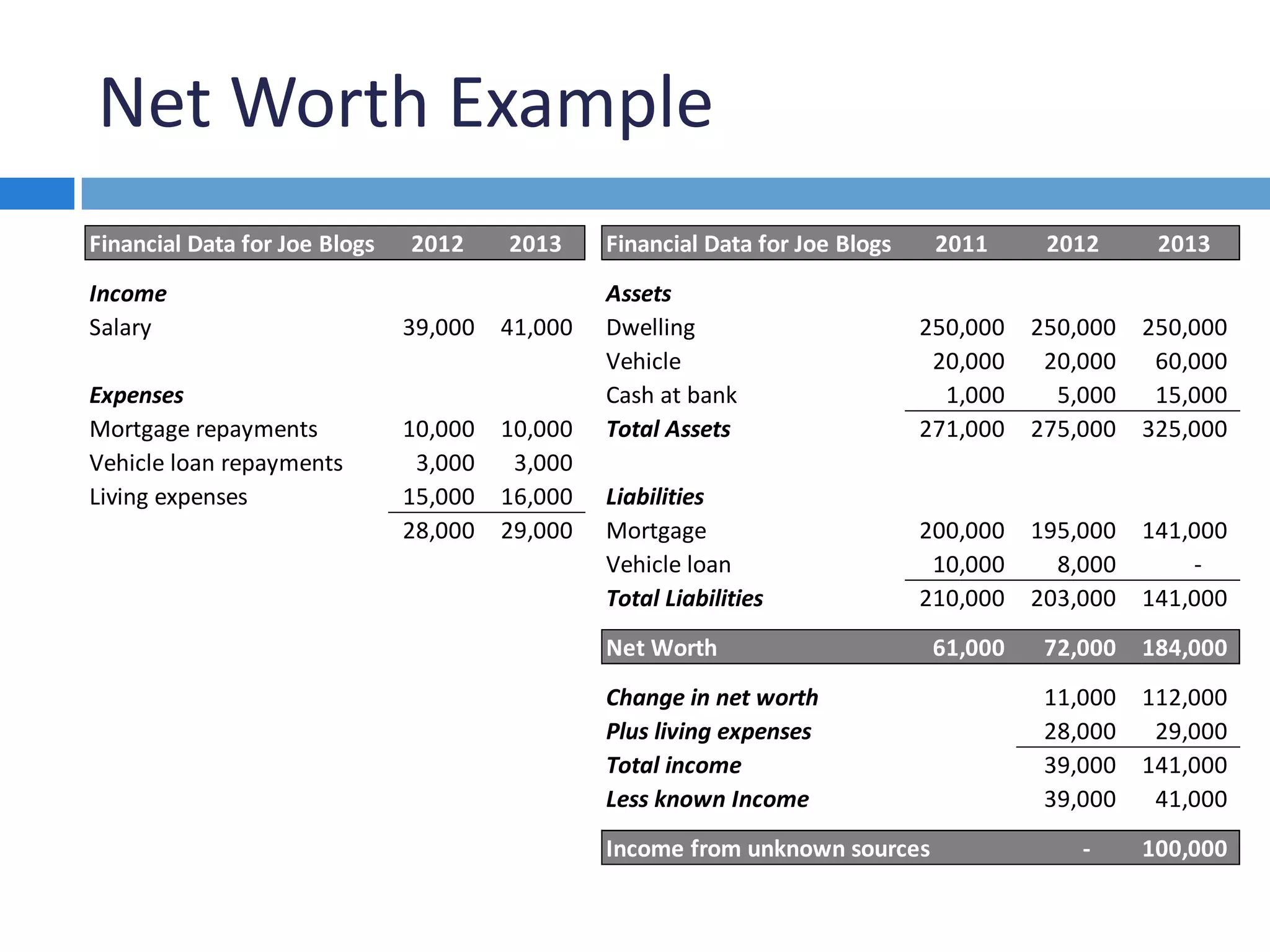
This document discusses methods for investigating how perpetrators convert and spend stolen funds during a fraud examination. It explains that conversion searches are important to determine the extent of embezzlement and gather evidence that can be used to obtain confessions. Public records, private sources, online databases, and internet searches can be used to find information about suspects' lifestyles and expenditures. Net worth calculations compare suspects' assets and income over time and can reveal funds from unknown sources.