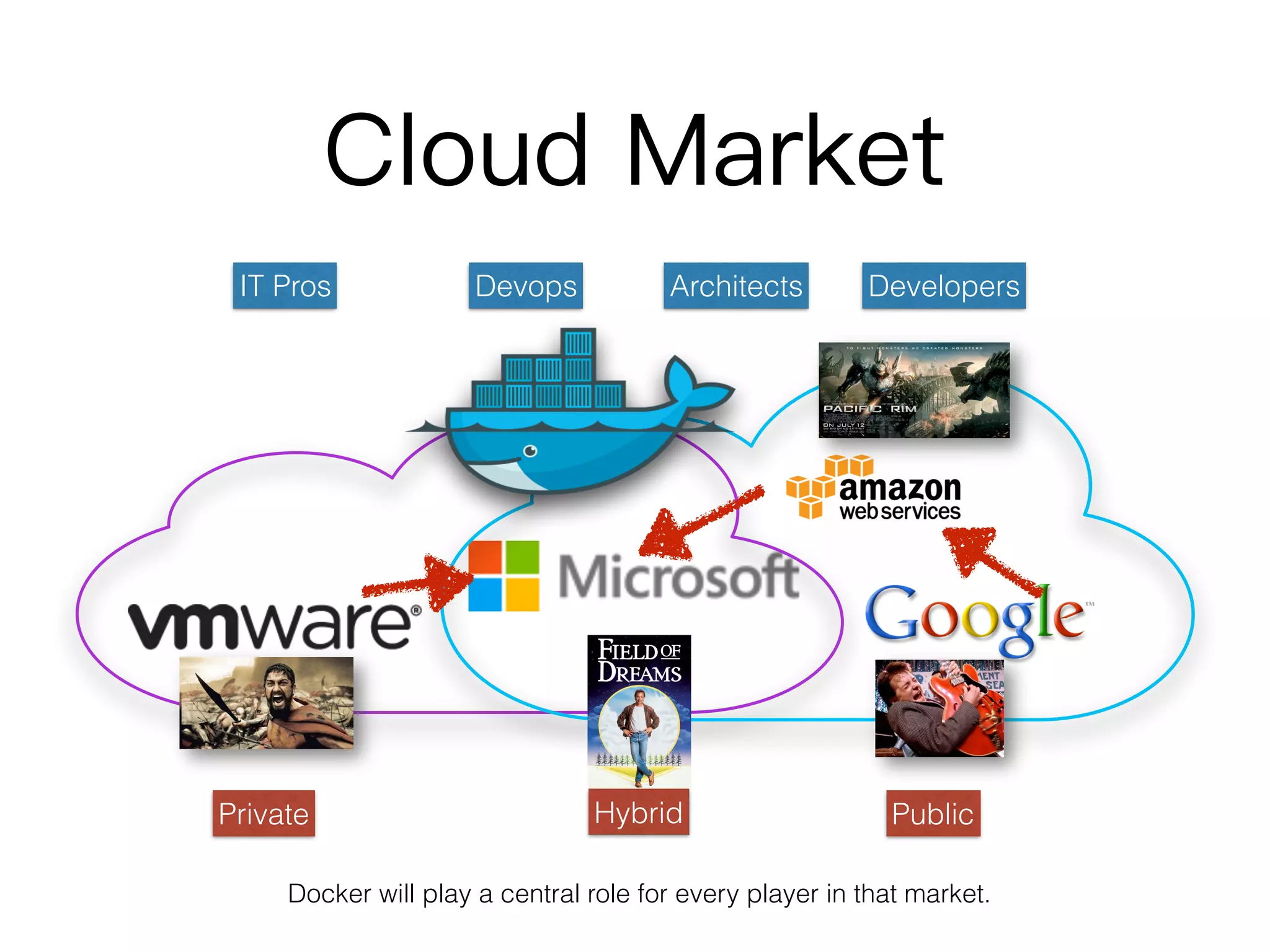
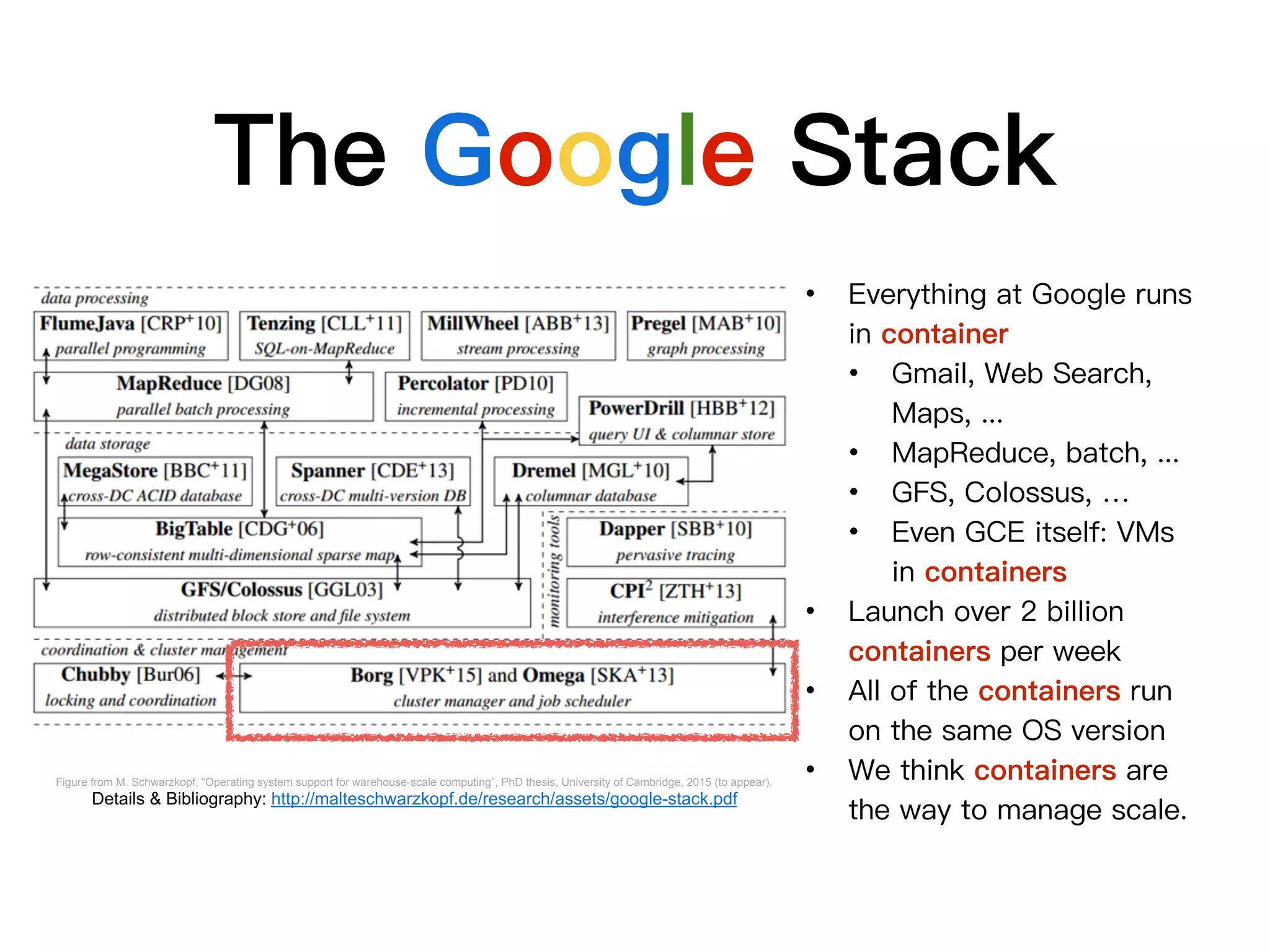
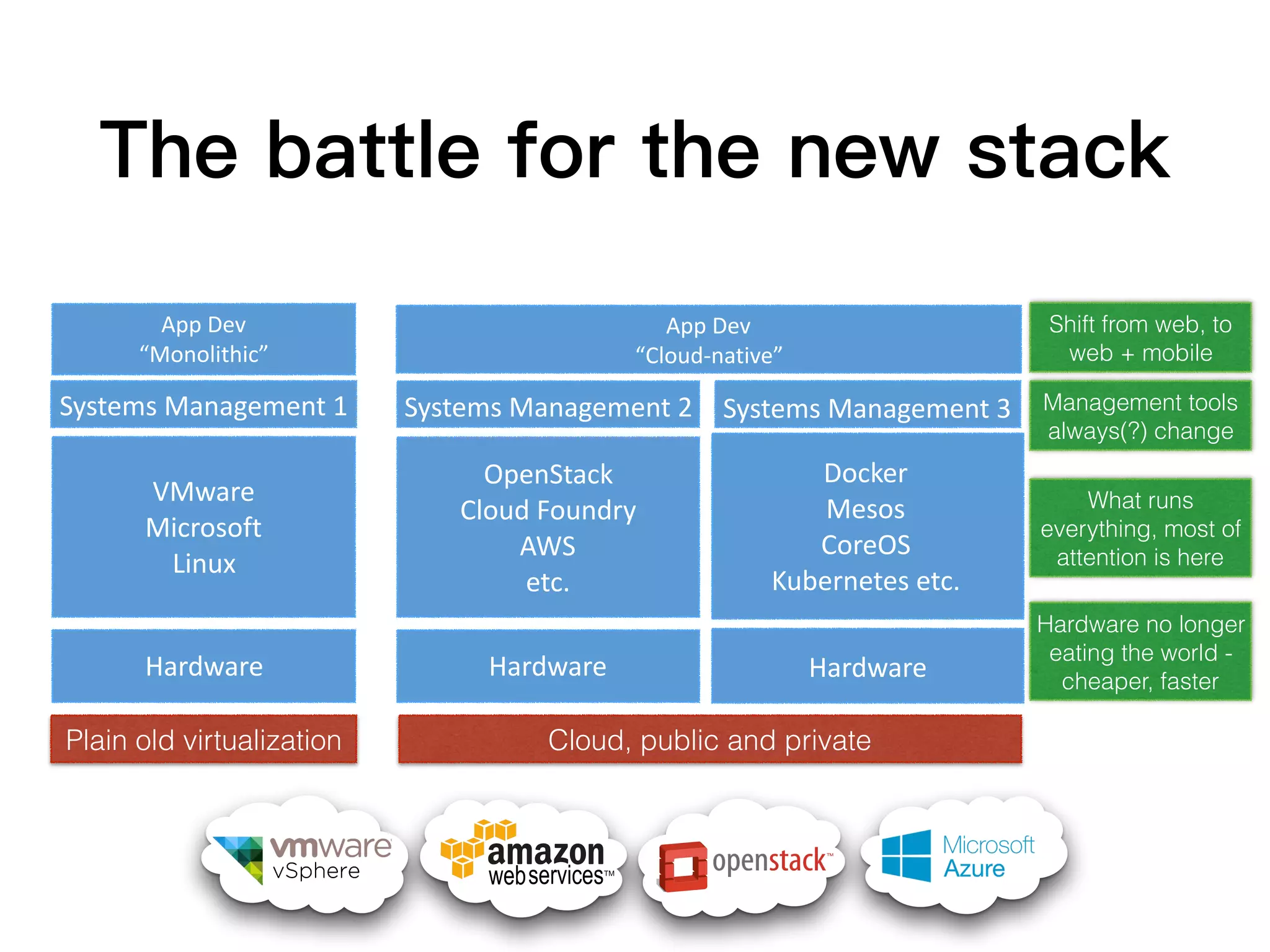
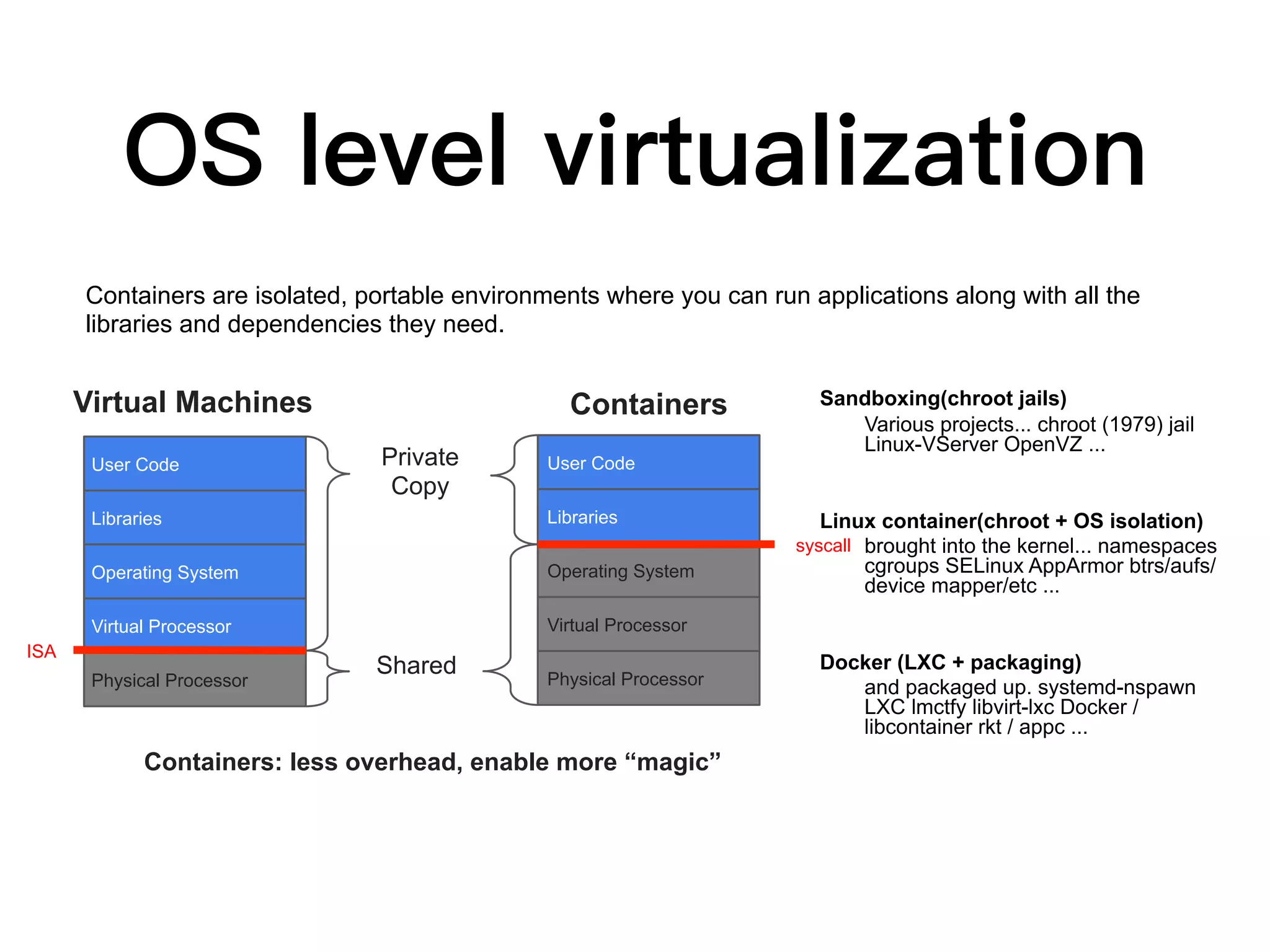
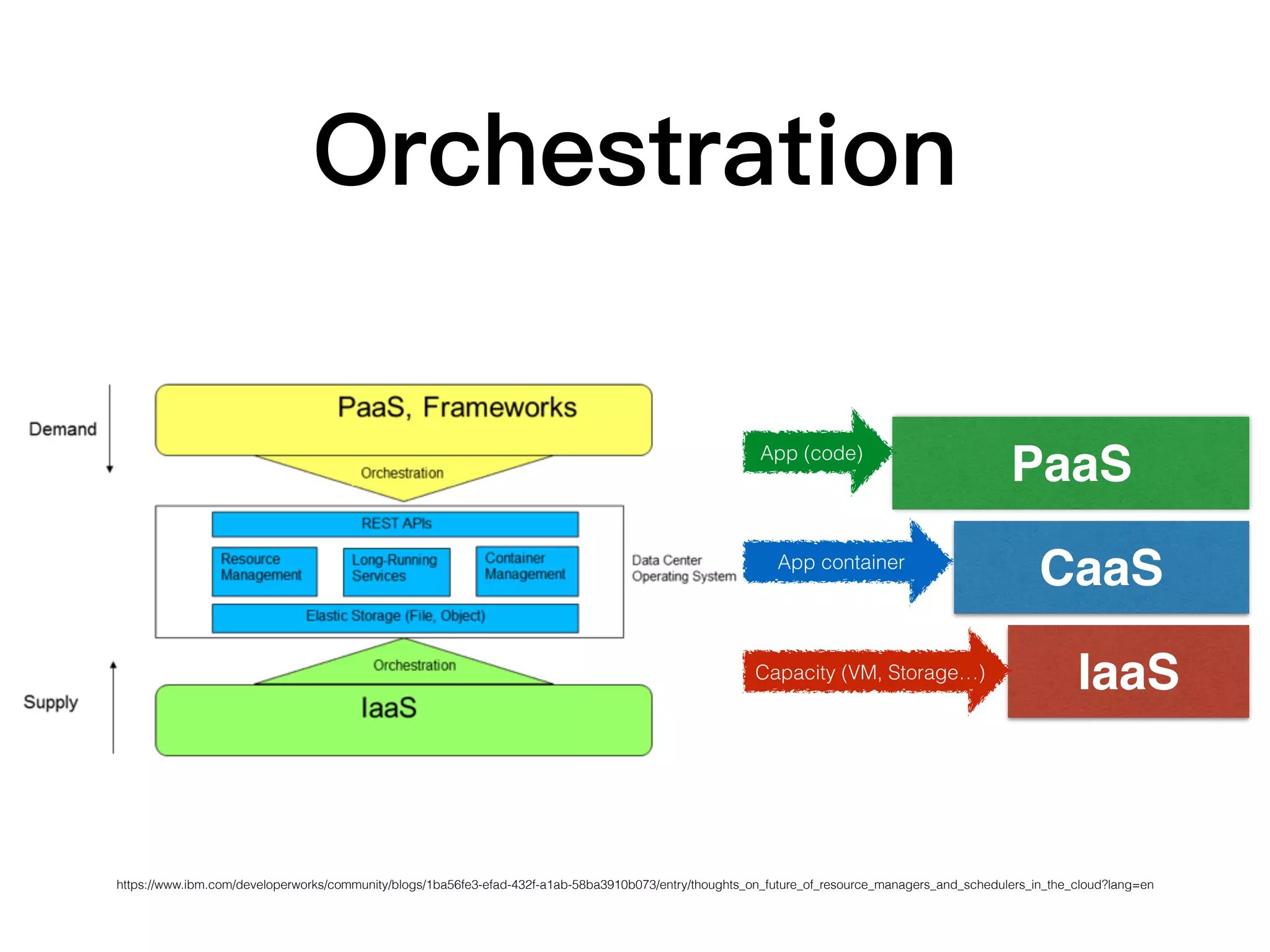
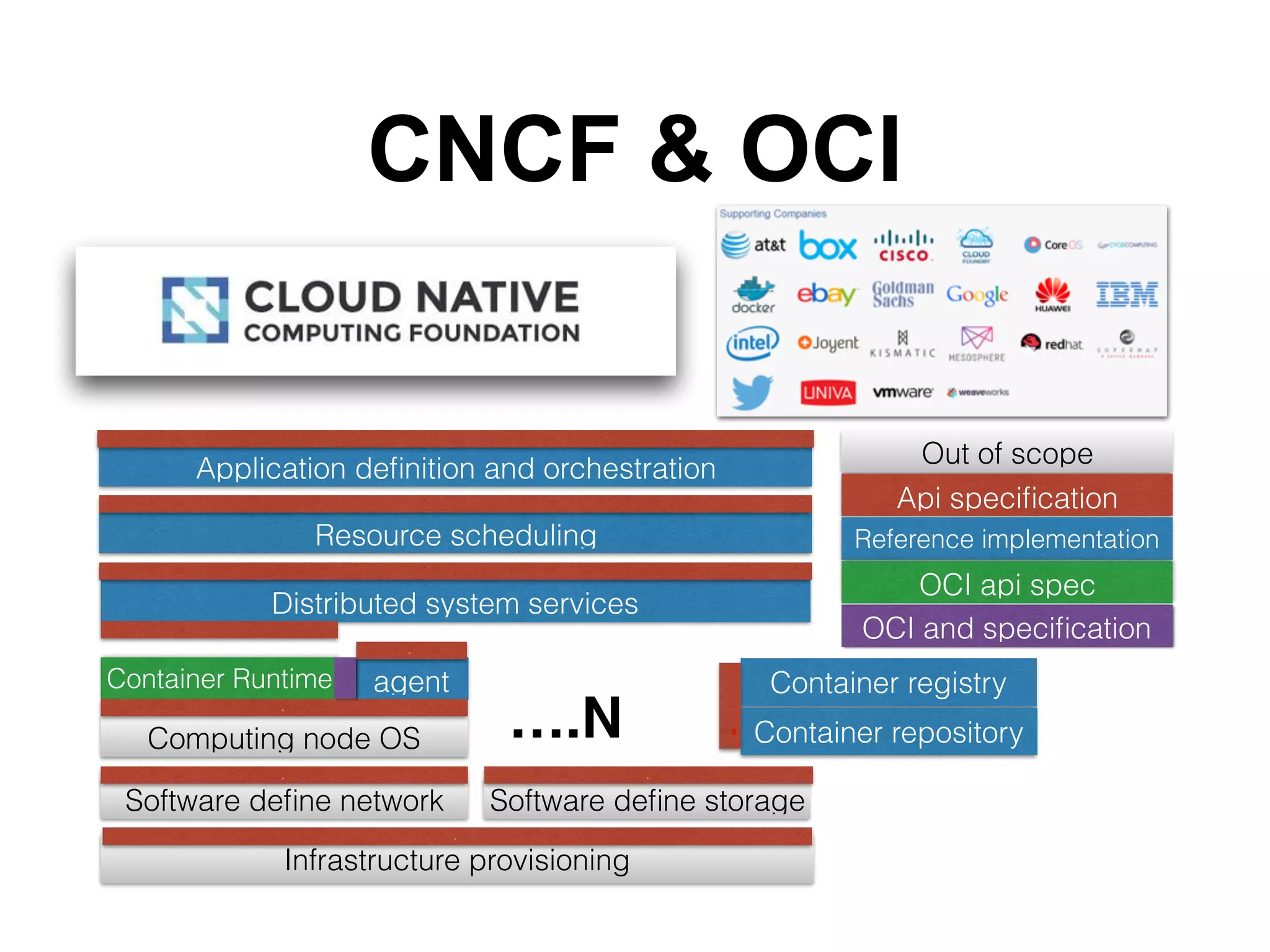
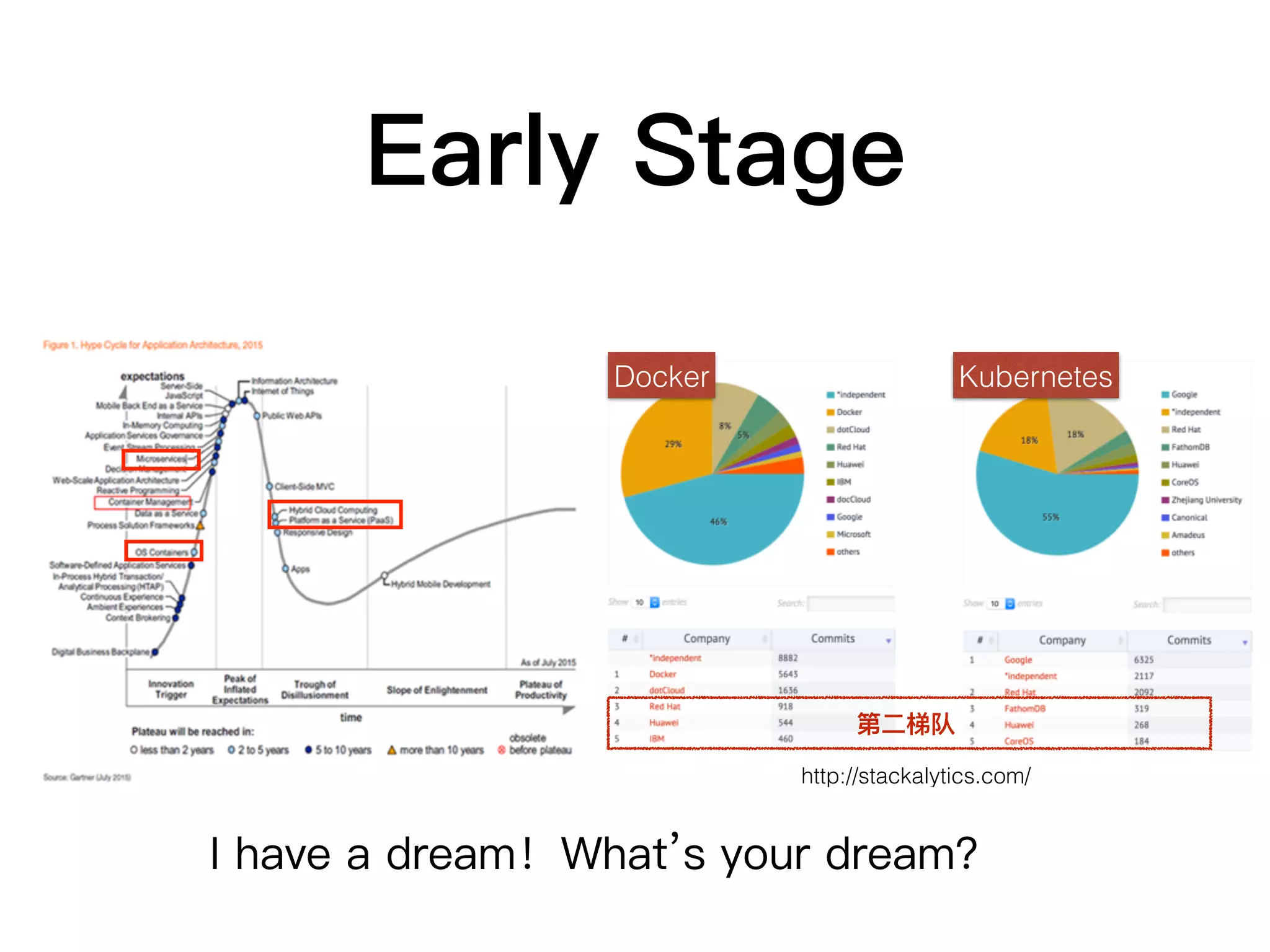
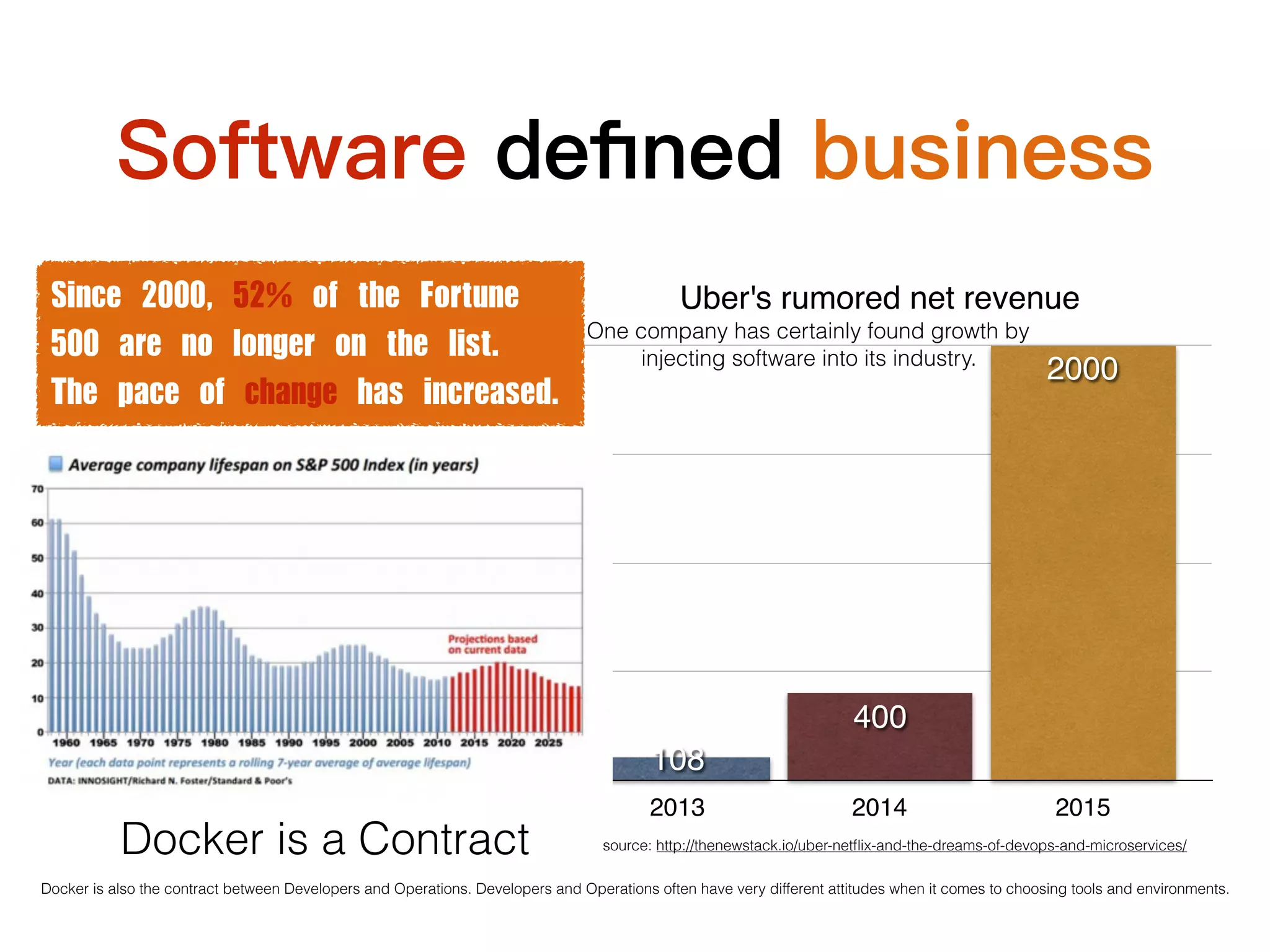
This document discusses containers and related technologies:
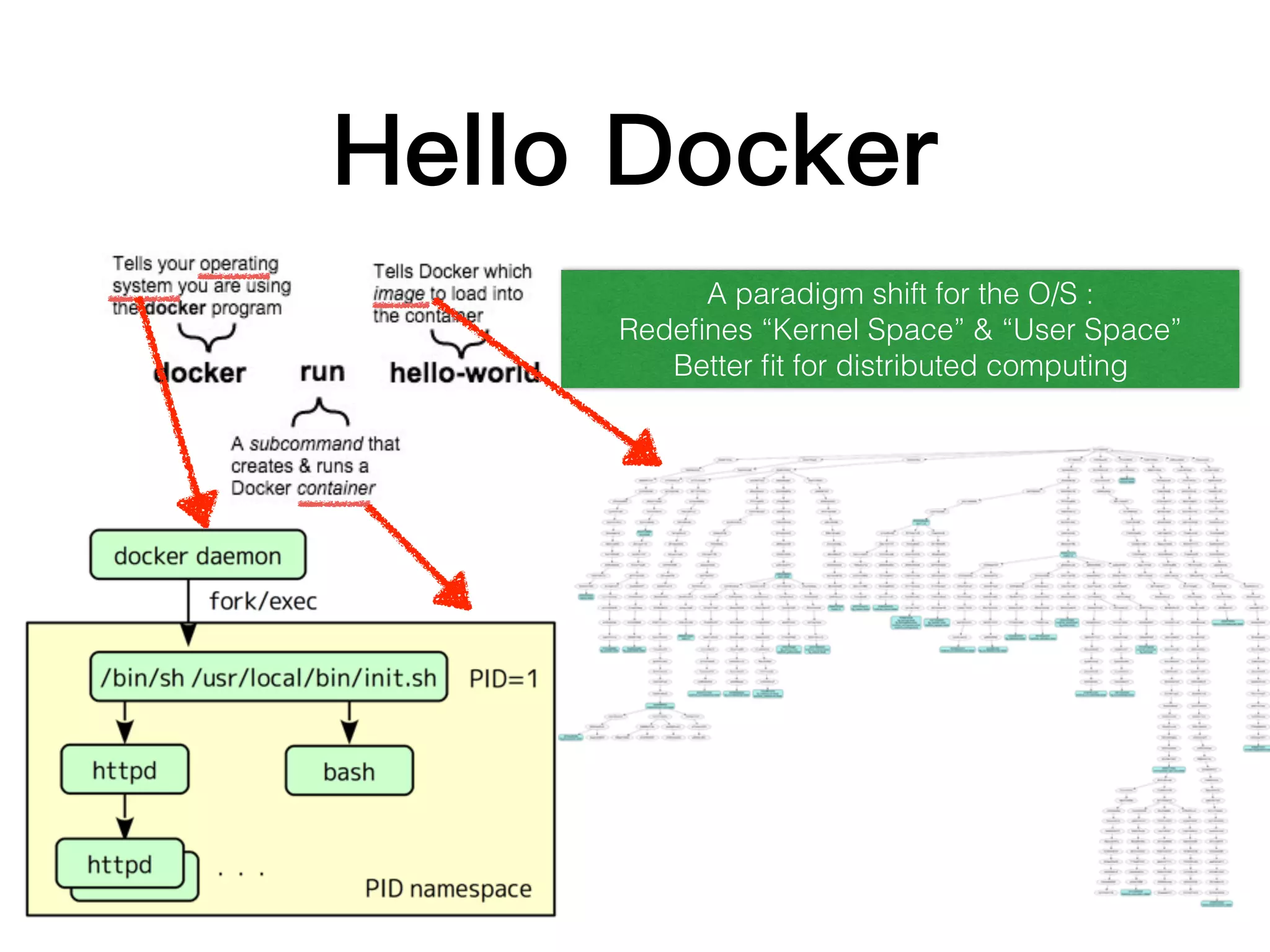
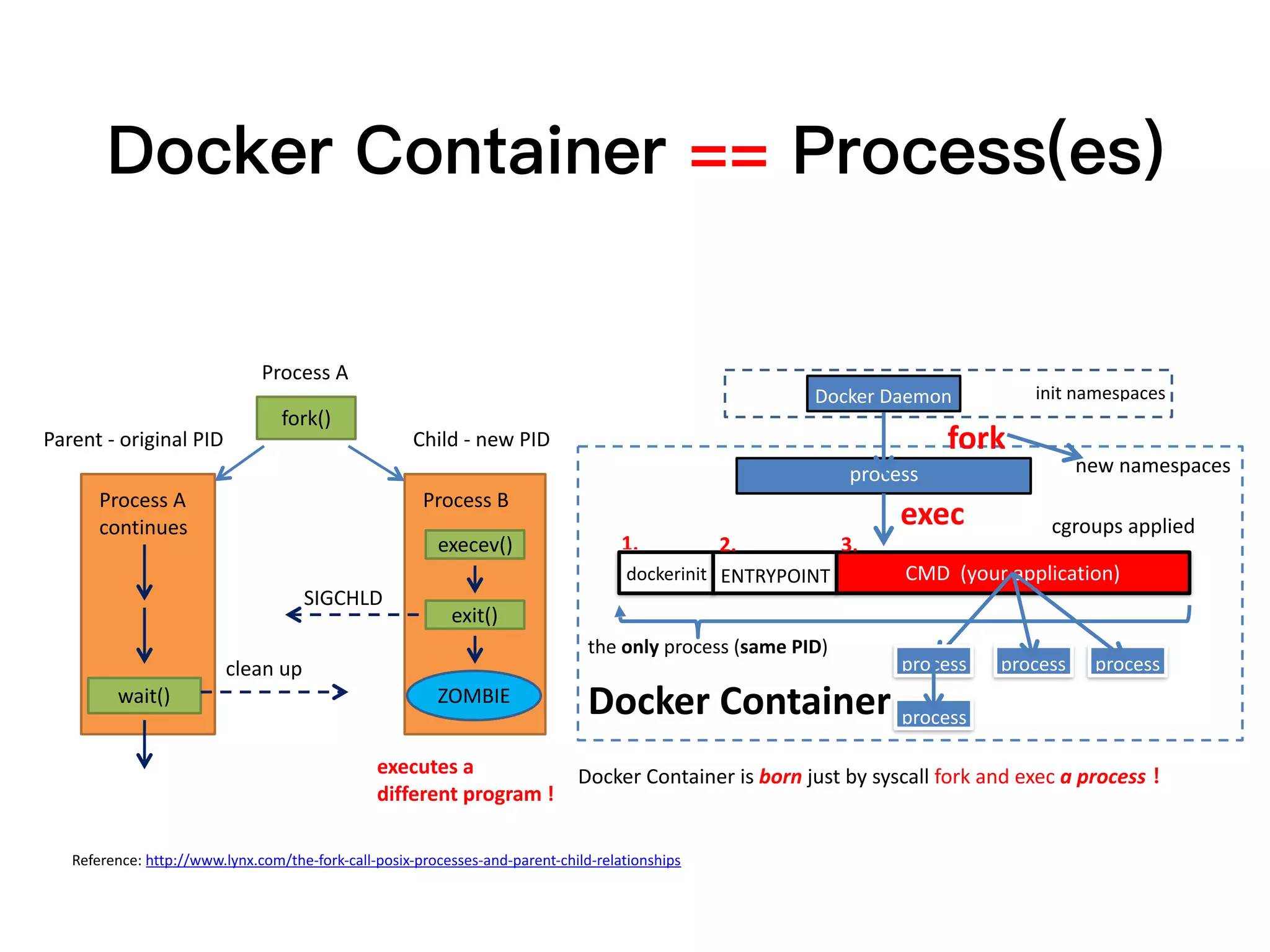
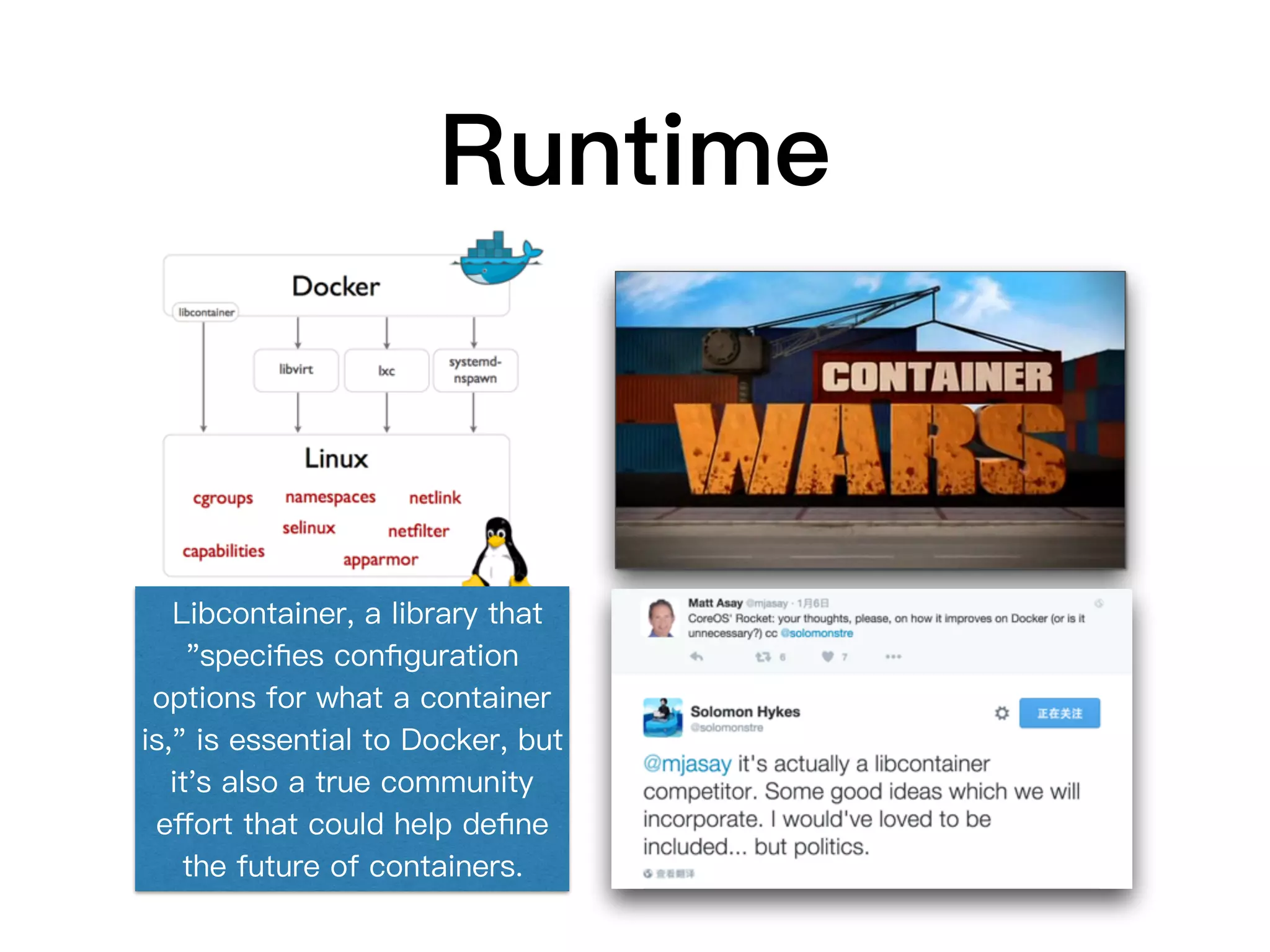
1. Containers provide isolated, portable environments for running applications and their dependencies. Docker is a popular container platform that packages applications into containers using Linux kernel features like namespaces and cgroups.
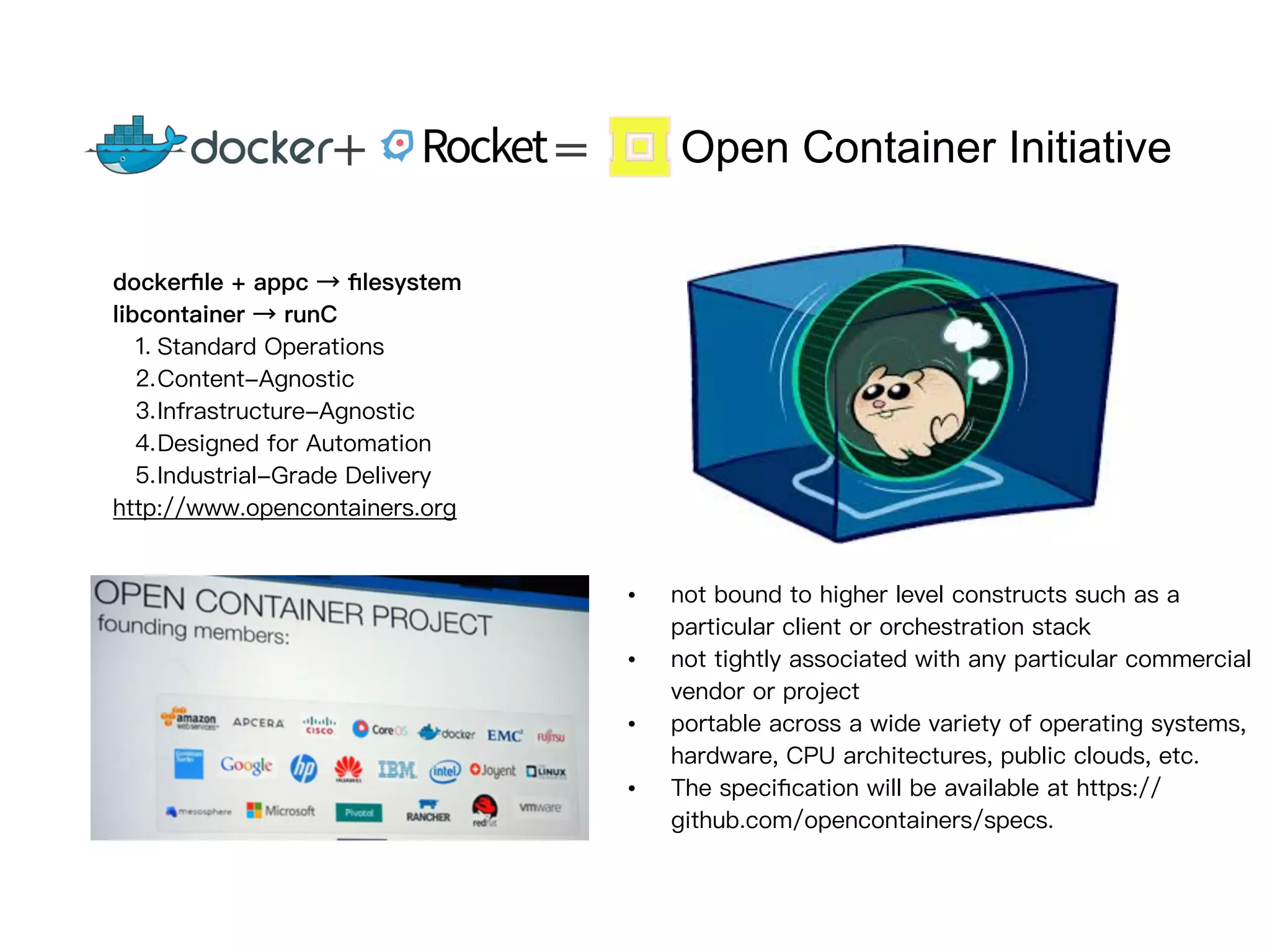
2. The Open Container Initiative (OCI) aims to develop standards around container formats and runtime. Technologies like Docker, rkt, and AppC implement the OCI specifications.
3. Container orchestration systems like Kubernetes and Mesos manage the deployment and lifecycles of containers at scale across clusters of hosts.