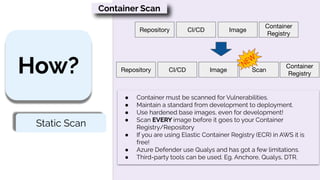
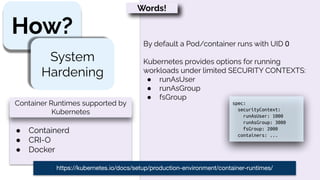
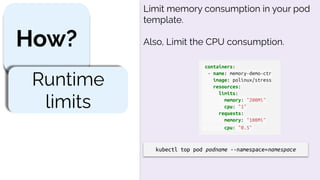
This document provides an overview of container security best practices. It recommends scanning containers for vulnerabilities before deployment, running containers with limited privileges using security contexts, and limiting container resources consumption using limits and requests. The document also discusses container runtimes like Docker, Containerd and CRI-O, and how containers isolate processes using namespaces and cgroups.




![Jargon
Static Scan
CVE : Common Vulnerabilities and
Exposures
MITRE. [Non-Profit Organization]
NVD [National Vulnerability Database]
Words!
First container CVE : CVE-2019-5736 https://seclists.org/oss-sec/2019/q1/119](https://image.slidesharecdn.com/containersecurity-210228105818/85/Container-Security-5-320.jpg)

![In-Depth!
Docker container are isolated using Namespaces:
● IPC namespace
● Mount namespace
● Network namespace
● Process (PID) namespace
● User namespace
● UTS [Unix Time Sharing]
Namespace 2
Container
C
Namespace 1
Container
A
Container
B
Container
D
Docker containers use Control Groups to control or limit
access to system resources.
Also known as cgroups.
CGroups are hierarchical policies.
CGroups are formed using multiple nodes.
A Node is a collection of process.
Types:
● Memory
● TLB
● CPU
● Bulk IO
● Net
● Device (/dev/)
CGROUPS](https://image.slidesharecdn.com/containersecurity-210228105818/85/Container-Security-8-320.jpg)