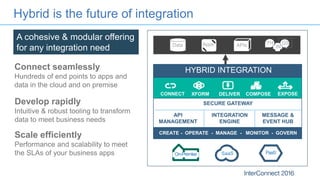
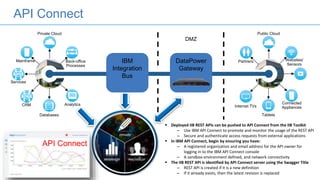
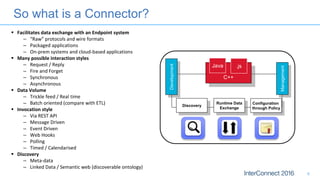
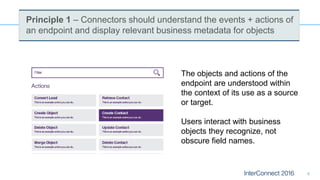
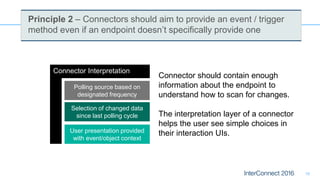
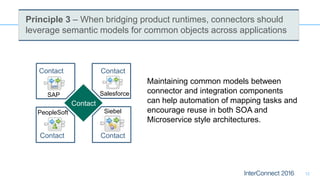
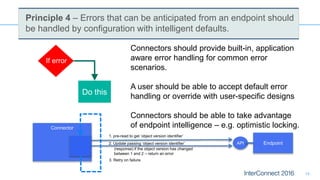
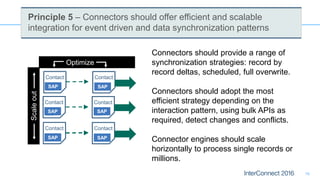
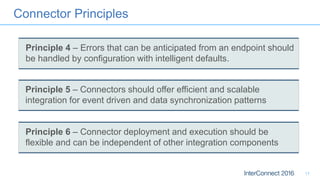
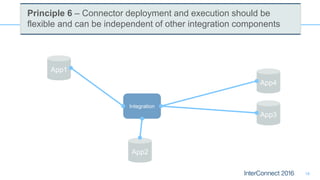
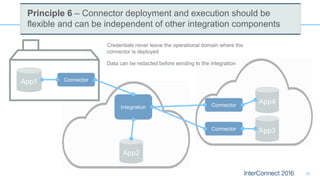
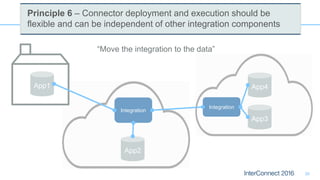
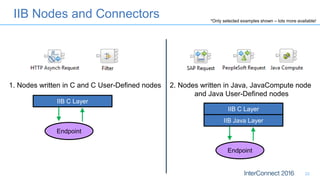
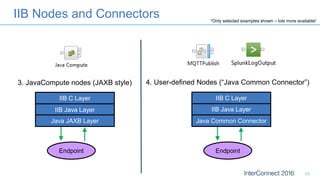
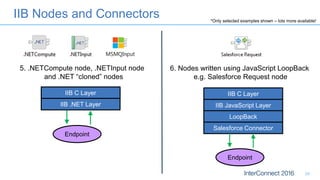
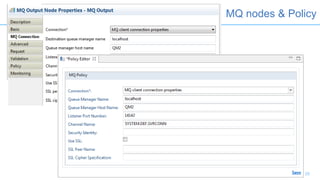
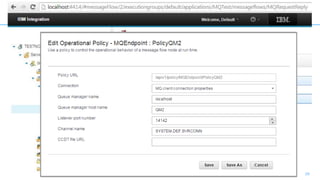
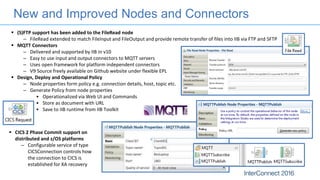
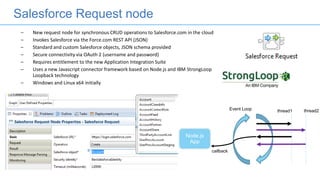
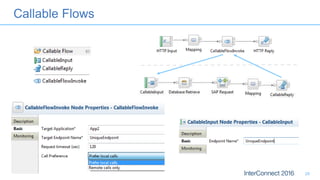
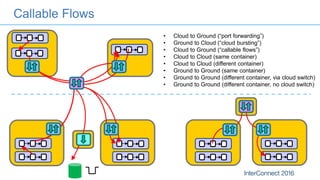
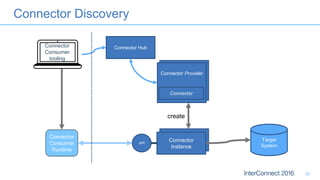
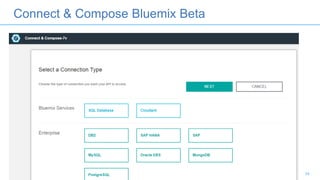
Connectors for Integration provide ways to connect IBM Integration Bus to various endpoints and applications. They handle data exchange with external systems and applications, supporting various interaction styles and data volumes. Well-designed connectors understand the business objects and events of an endpoint, can provide event-driven access even if one is not directly available, leverage semantic data models, and have built-in error handling. Connectors also aim to offer efficient, scalable integration for event-driven and data synchronization scenarios, and have flexible deployment that is independent of other integration components.