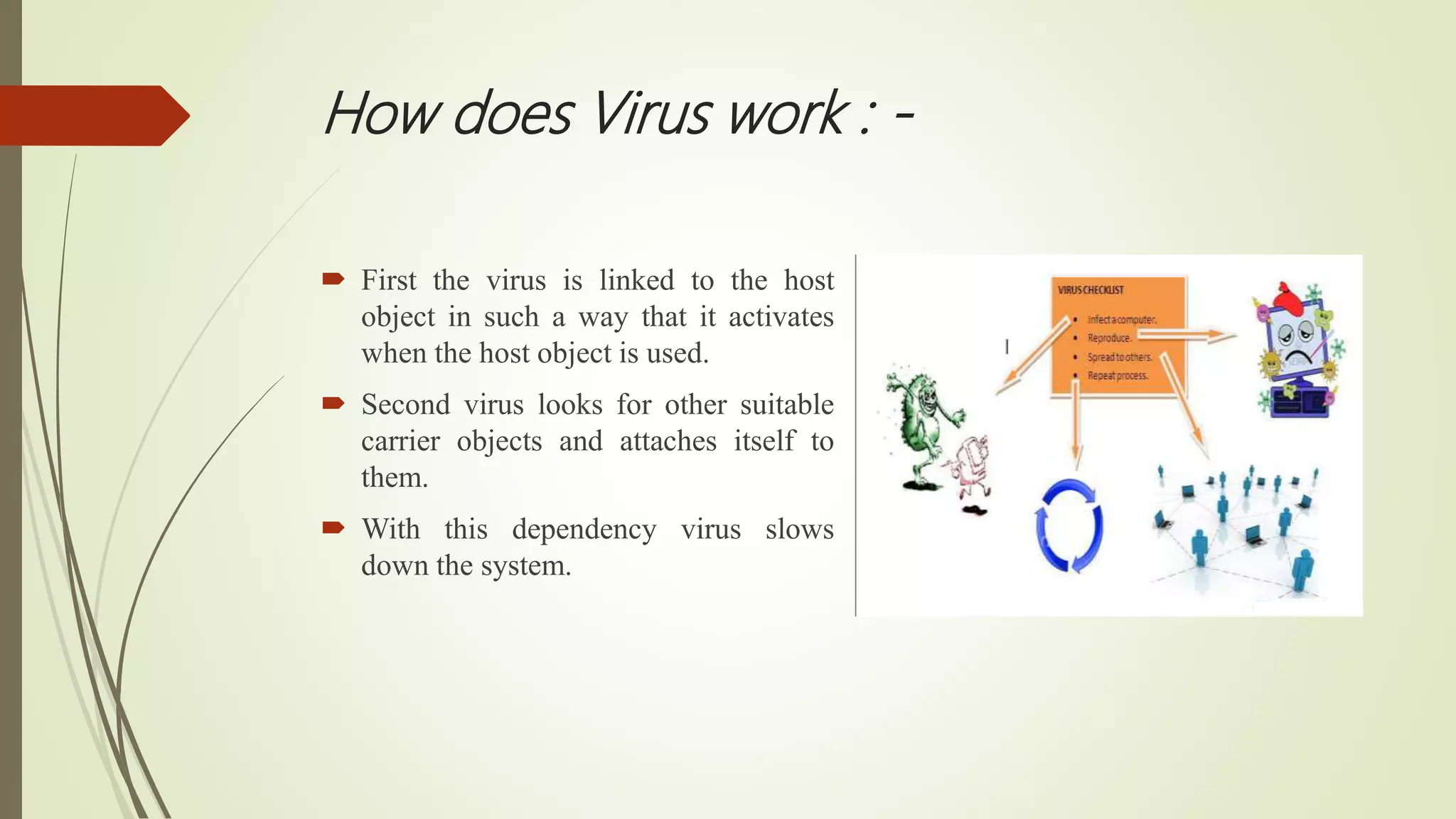
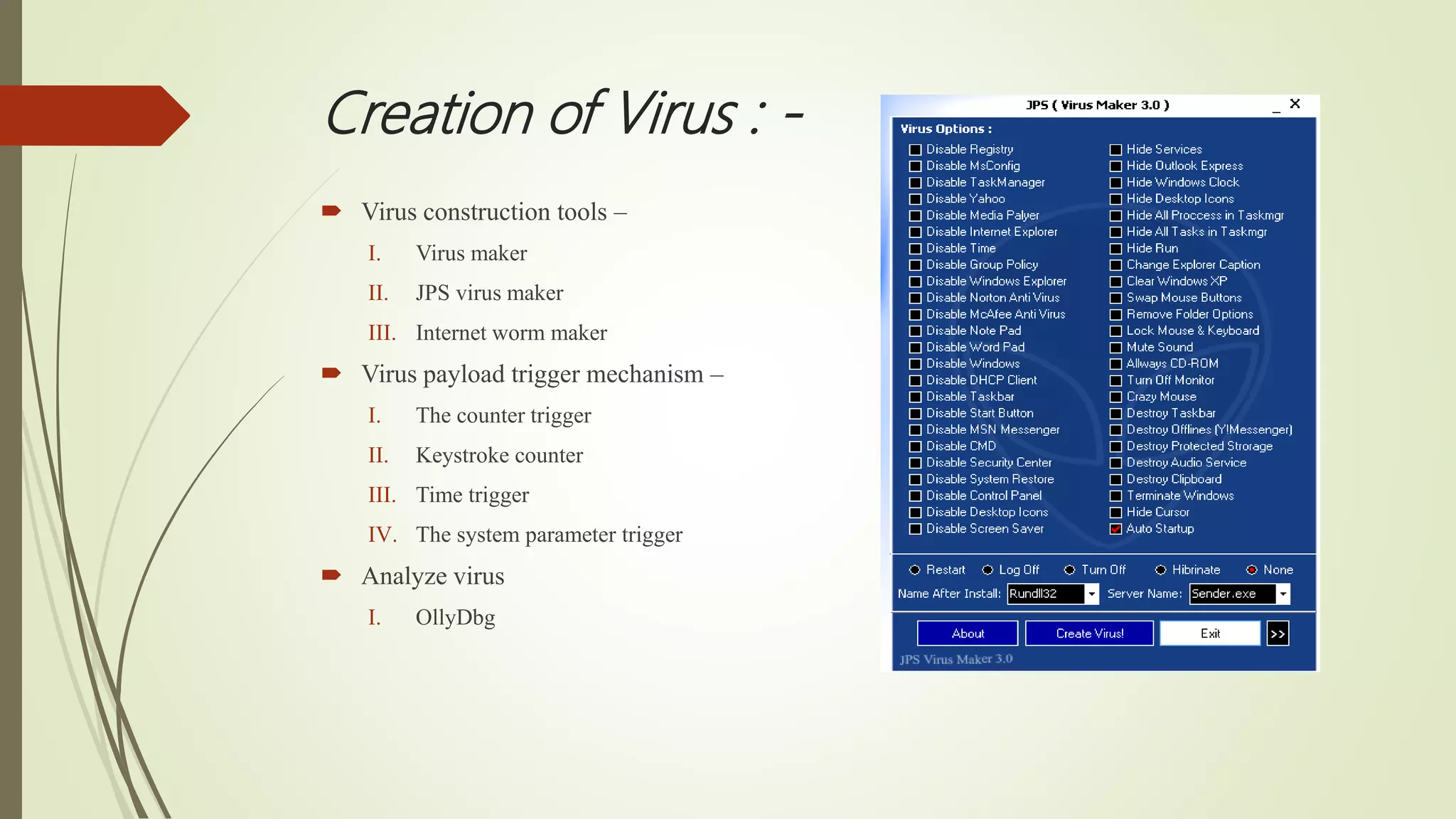
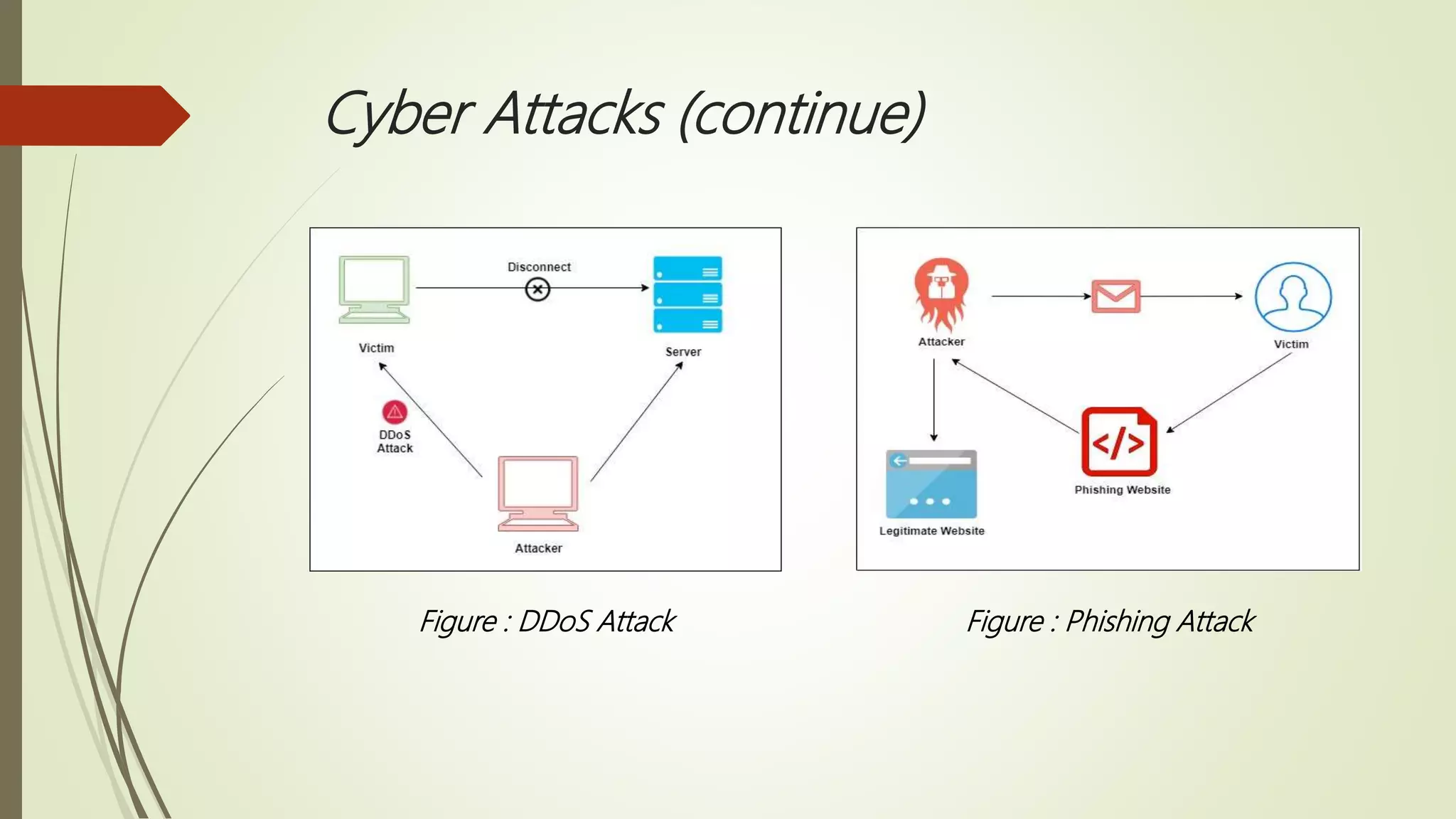
This document summarizes a seminar presentation on computer viruses and cyber attacks. The presentation covered the introduction and history of viruses, how viruses work and are created, types of viruses including boot sector, web scripting, and polymorphic viruses. It also discussed cyber attacks like DDoS, phishing, and man-in-the-middle attacks. The presentation explained how anti-virus software detects viruses using signature-based, heuristic-based, and behavioral-based techniques and outlines prevention methods like using firewalls and updating software.