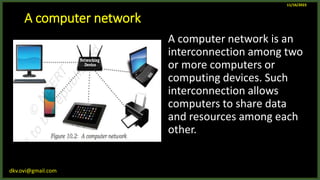
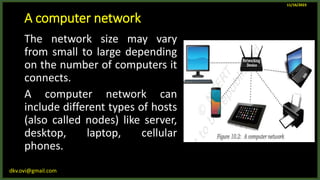
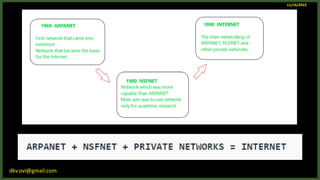
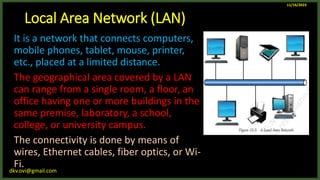
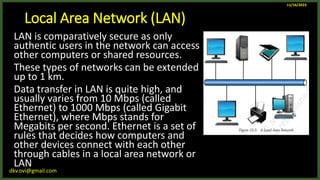
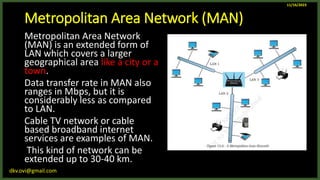
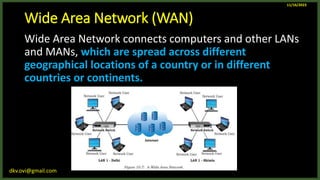
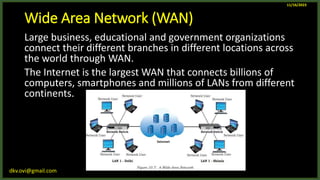
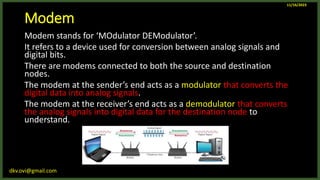
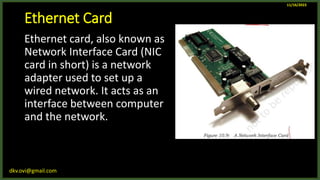
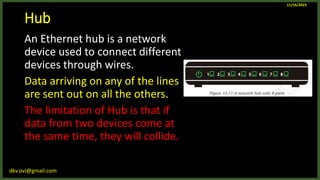
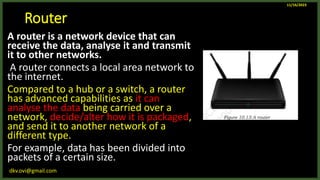
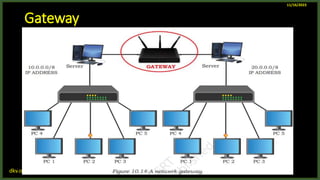
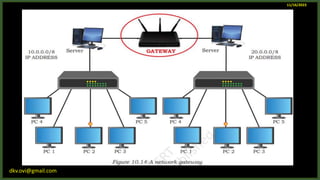
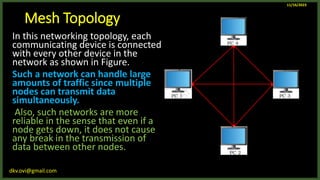
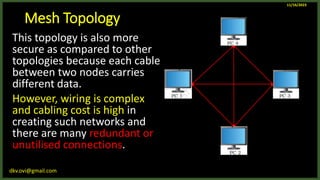
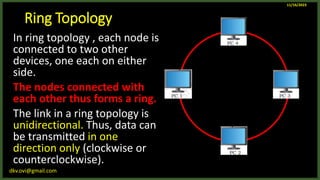
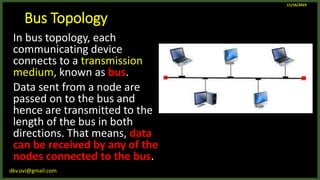
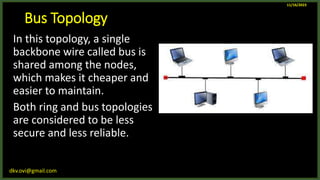
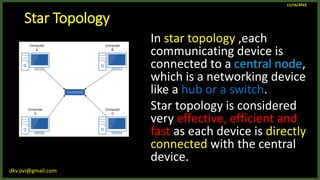
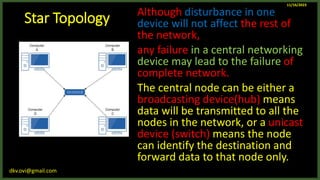
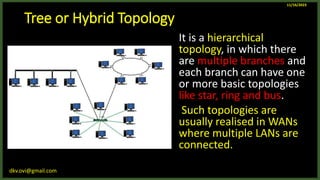
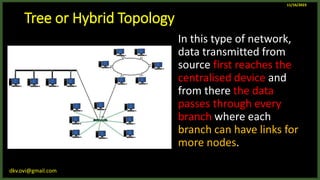
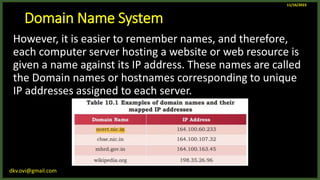
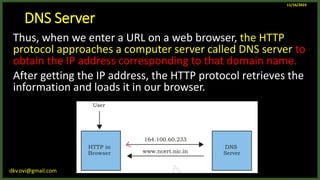
The document provides an overview of computer networks, including definitions and examples of different types of networks. It discusses what a computer network is and how it allows devices to share resources. It also describes the evolution of networks from ARPANET to the modern Internet. Various networking devices like routers, switches, hubs and gateways are defined. Finally, the document outlines common network topologies and how nodes are identified on a network using MAC addresses and IP addresses.