This document describes a MIPS encryption program that uses three arrays: array1 stores the input string, array2 stores the encoded/decoded output, and array3 stores an encryption key. It works by reading each character from array1, determining if it is a letter or number, and then encoding/decoding it based on the encryption key stored in array3 before writing it to array2. If a user inputs 'Y' or 'y' they are asked if they want to terminate the program, otherwise it loops back to the beginning to encode another string. Screenshots of it encoding and decoding messages are also included.
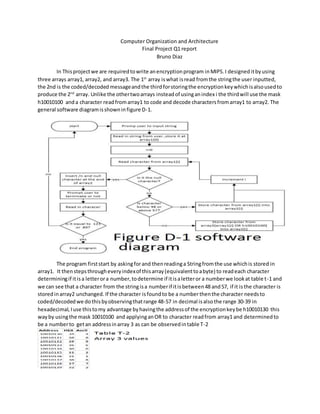

![li $s3,0x10010130 #load the base adressof array3(encryptioncode)
li $t0,0x35393634 #store the encryptioncode
sw $t0,0($s3)
li $t0,0x38313330
sw $t0,4($s3)
li $t0,0x00003237
sw $t0,8($s3)
addi $s4,$0,48 #lowerlimitfornumber
addi $s5,$0,57 #upperlimitfornumber
addi $s6,$0,89 #Y and
addi $s7,$0,121 #y
LOOP1:
li $v0,4 #print start
la $a0,start
syscall
li $v0, 8 # read string byusingsyscall
add $a0, $0,$s1 # loadfirstarray addressinto$a0
addi $a1, $0,29 #load the character limit
syscall
li $v0,4 #make newline
la $a0,new_line
syscall
addi $t2,$0,0 #offseti
LOOP2:
add $t3,$t2,$s1 #current adressinrespectto array1
add $t4,$t2,$s2 #current adressinrespectto array2
lb $t5,0($t3) #loadelementfromarray1[i]
beq$0,$t5,done #jumpto done if null character ispulledfromarray
slt$t6,$t5,$s4 #is it lessthan48?
bne $t6,$0,continue
slt$t6,$s5,$t5 #is it greaterthan57?
bne $t6,$0,continue
or $t7,$s0,$t5 #decrypt byreadingadressinrespectto the numberoredwiththe maskin array3
lb$t5,0($t7)
continue:
sb $t5,0($t4) #store intoarray 2[i]
addi $t2,$t2,1 #incrementi
j,LOOP2
done:
li $t5,0x5C6D0000 #store n and null chatacterintoendof array
addi $t4,$t4,1
sb $t5,0($t4)
li $v0,4 #printresult
or $a0,$s2,$0](https://image.slidesharecdn.com/fcf4ae8d-886f-47c9-8ab0-e01f075f68cd-150513193450-lva1-app6892/85/compuorg-final-3-320.jpg)
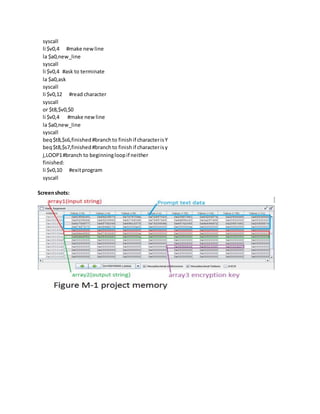
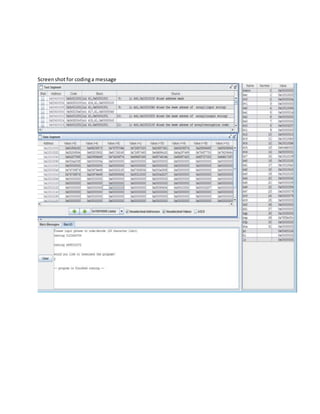
![Screenshotfor decodingamessage
Conclusion:
I was able tocome upwitha MIPS designthatavoidedhavingtouse 10 differentbranchesto
decode numbersbyutilizingakeystoredinmemoryandusinga trick withthe addressandthe ASCII
valuesof numberspointtothe positioninthe keyforthe value itneededtobe turnedintoto. By doing
thisI alsohad the befitof beingable toeasilymodifythe type of encryptionshouldIneedto.Ialso
avoidedhavingtouse a for loopforthe iterationneededforthe characterread byusinga while loop
that keptreadingtill itfoundanull character essentiallyturningfor(i=0;i++;i<29) towhile(array[i]!=00)
thisgivesthe benefitof beingable tomodifythe size of the inputtedstringshouldone needto.Soin
conclusionIcame up witha compact design(77 lineslong) foraMIPS encryptedthatiseasily
modifiable.](https://image.slidesharecdn.com/fcf4ae8d-886f-47c9-8ab0-e01f075f68cd-150513193450-lva1-app6892/85/compuorg-final-6-320.jpg)