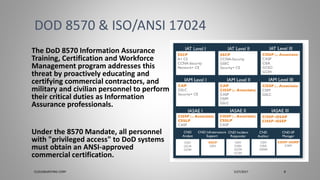
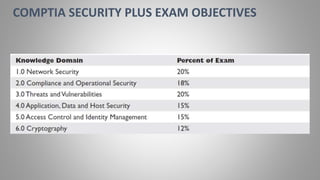
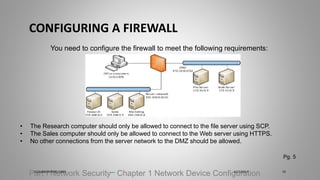
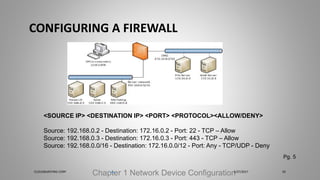
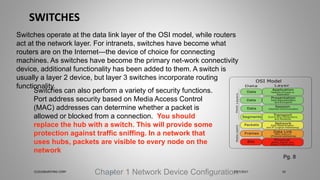
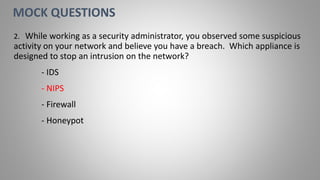
Joseph Holbrook is a cloud consulting architect and technical trainer with over 15 years of experience in cloud computing, data security, and government consulting. The document provides an overview of the CompTIA Security+ certification, its importance for IT professionals, particularly in military and government roles, and outlines the requirements under the DoD 8570 directive. It also includes training options, exam objectives, and key networking concepts related to security certifications.