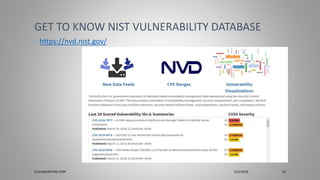
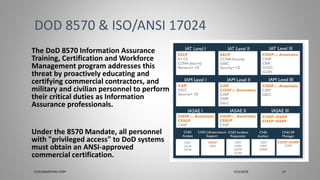
Joseph Holbrook, a cloud consulting architect and CompTIA subject matter expert, discusses the CompTIA PenTest+ certification, aimed at intermediate cybersecurity professionals focusing on penetration testing. The document outlines exam objectives, format, key frameworks, and areas to study for the certification. Additionally, it includes observations and recommendations based on past exam experiences and suggests upcoming training courses.