This document discusses the need for comprehensive risk management and automation for cyber security. It makes three key points:
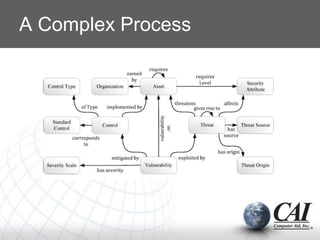
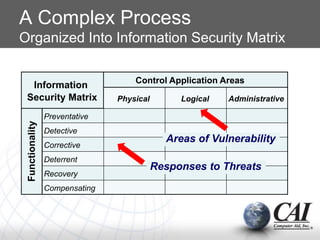
1. Security is a process that requires monitoring across physical, technical and administrative controls to be effective. Comprehensive monitoring of vulnerabilities and threats is needed.
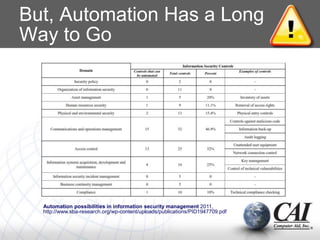
2. Automation is key to continuously monitoring for vulnerabilities and threats, and to modifying security behaviors through persistent enforcement and reinforcement of practices.
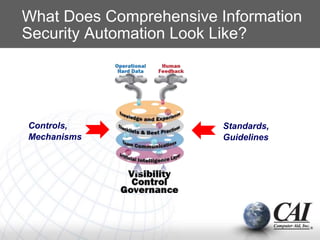
3. An effective approach is to automate information security "ensurance" through a system that incorporates both technical ("hard") data from security systems and human ("soft") feedback to provide comprehensive security assessment and reinforcement of policies to change behaviors.