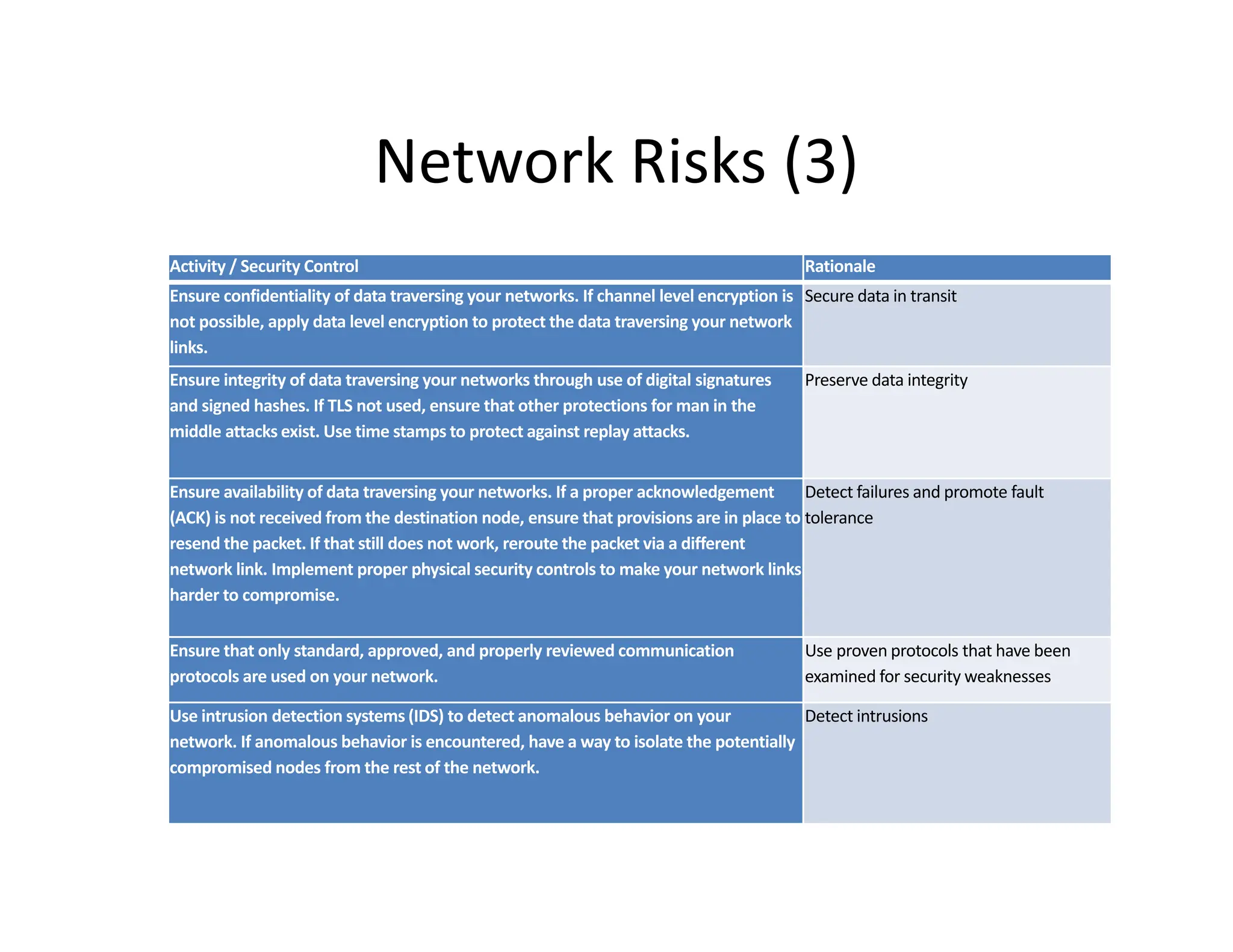
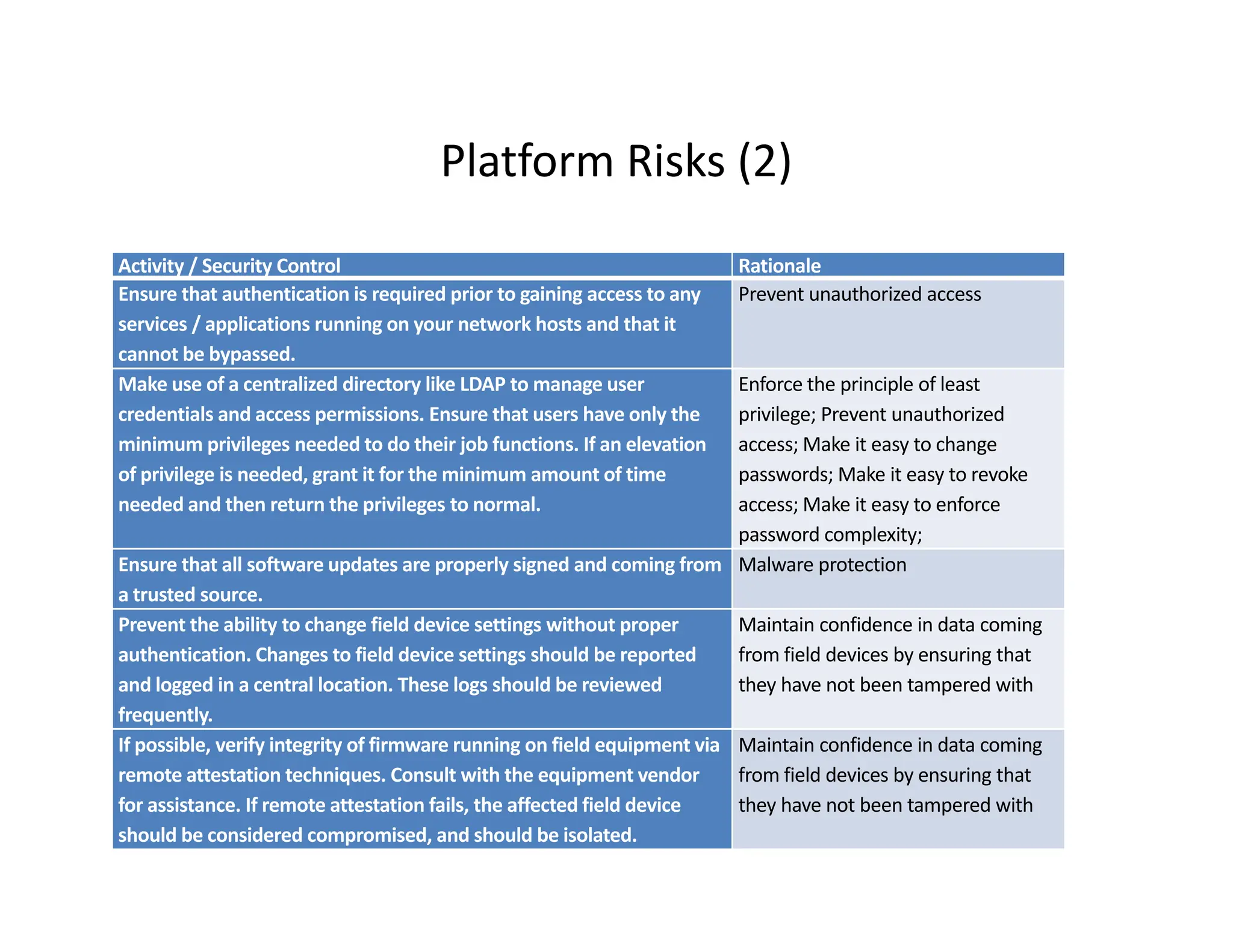
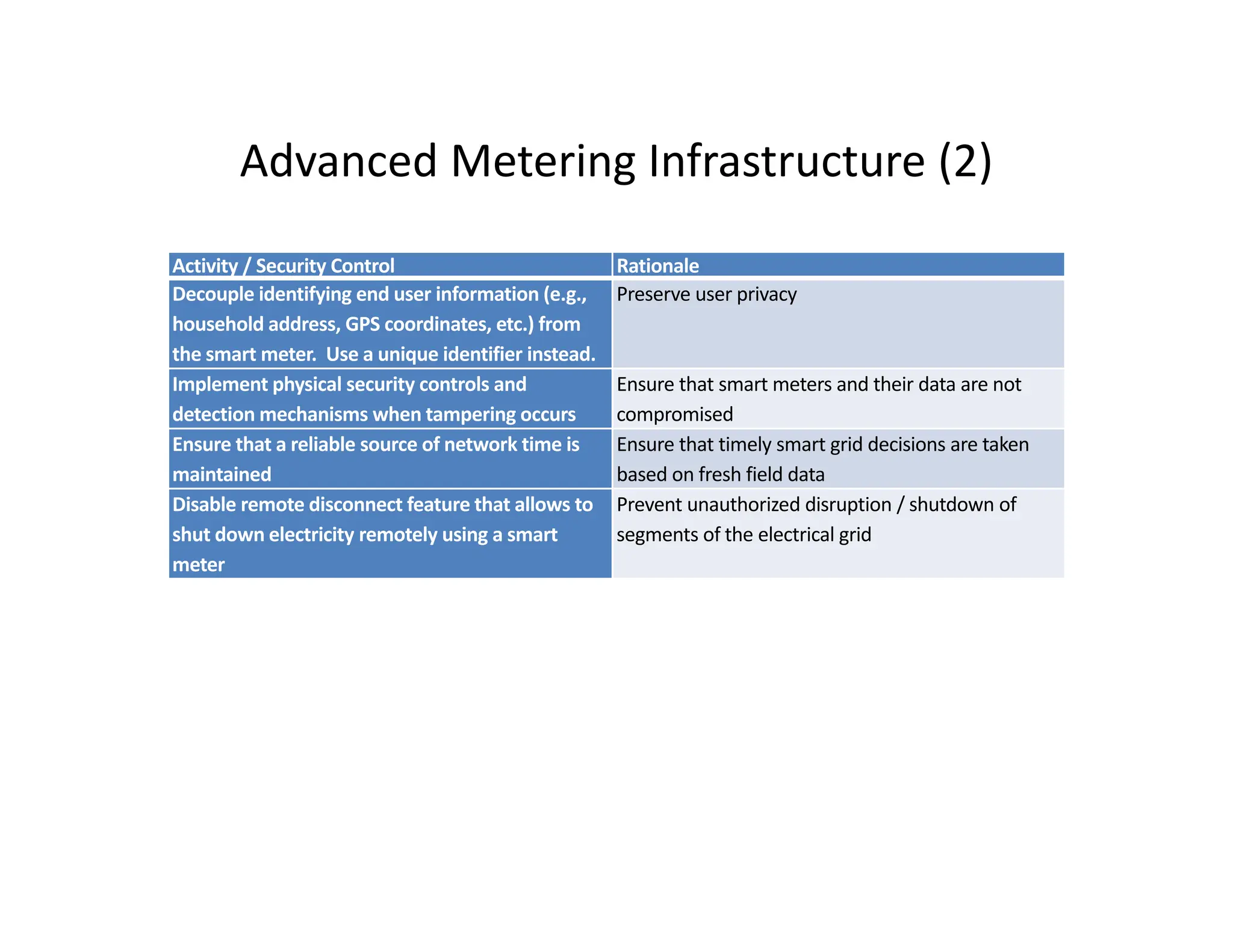
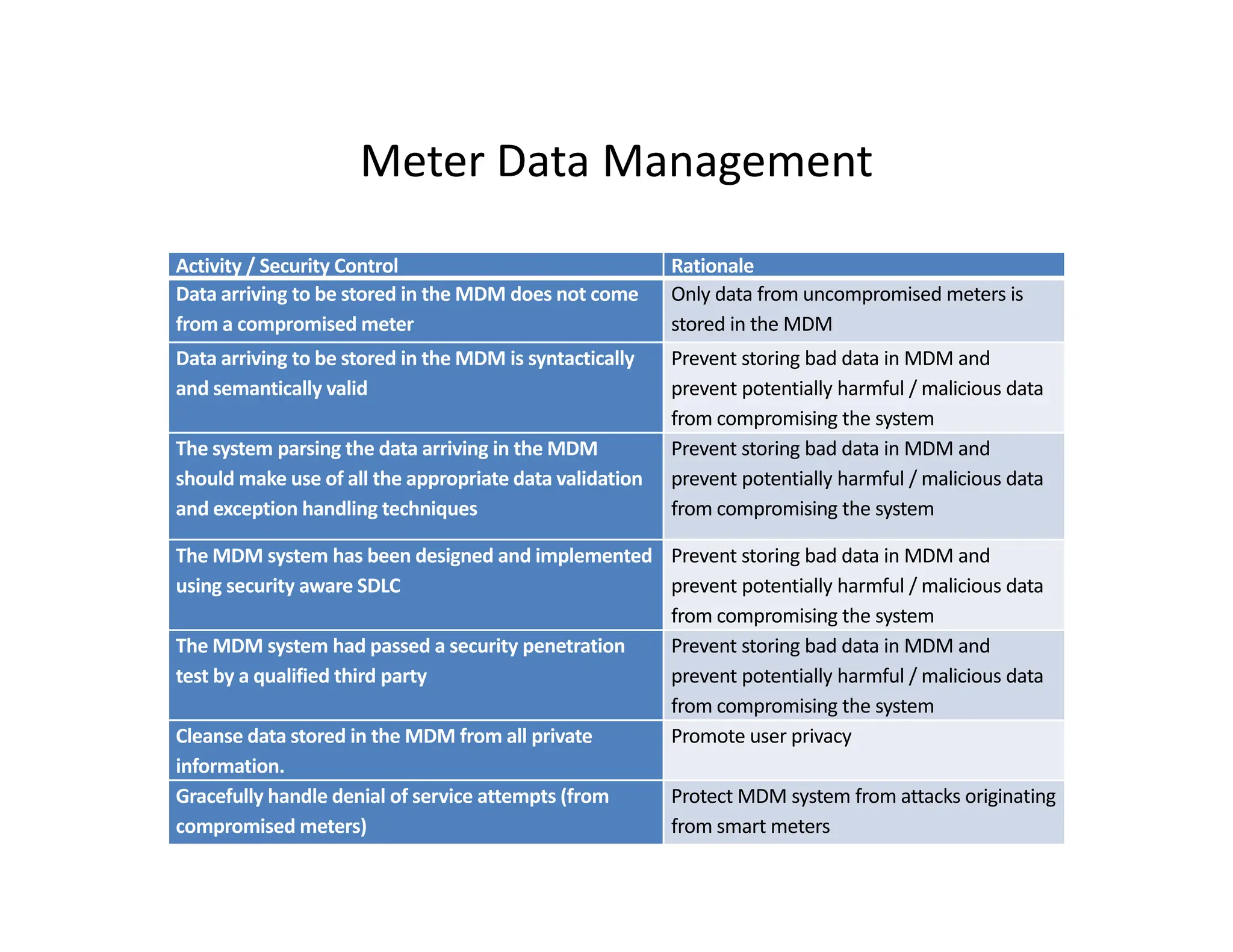
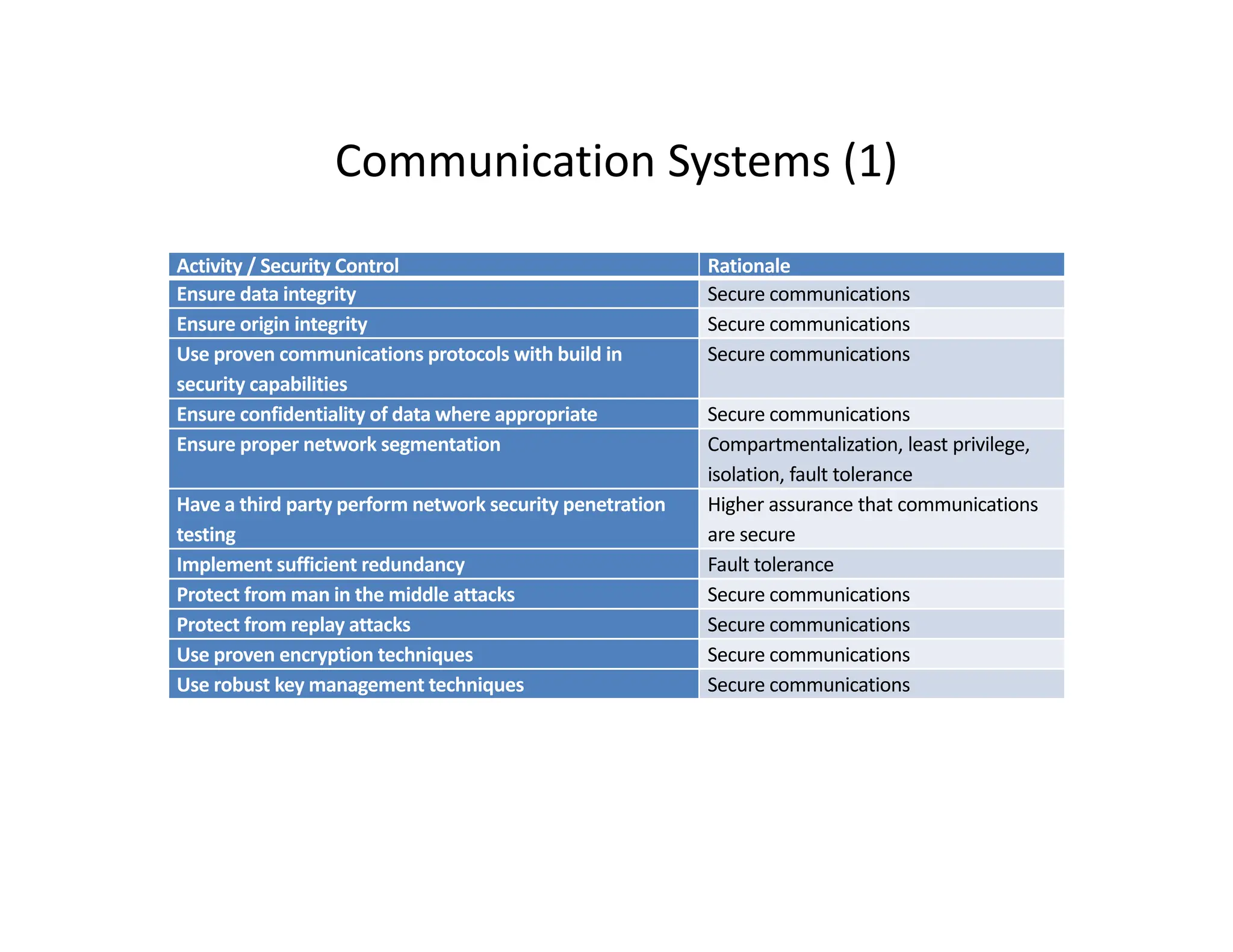
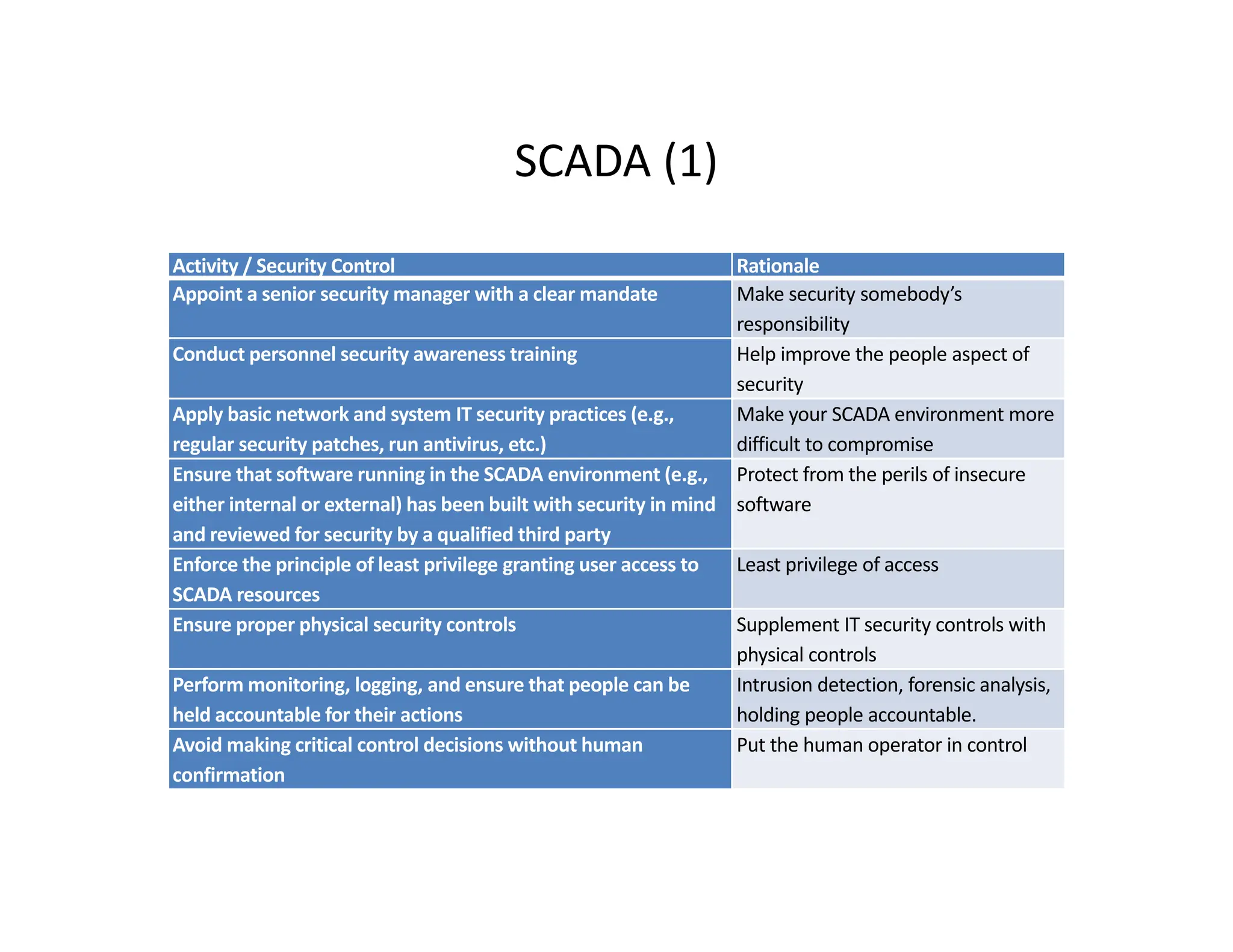
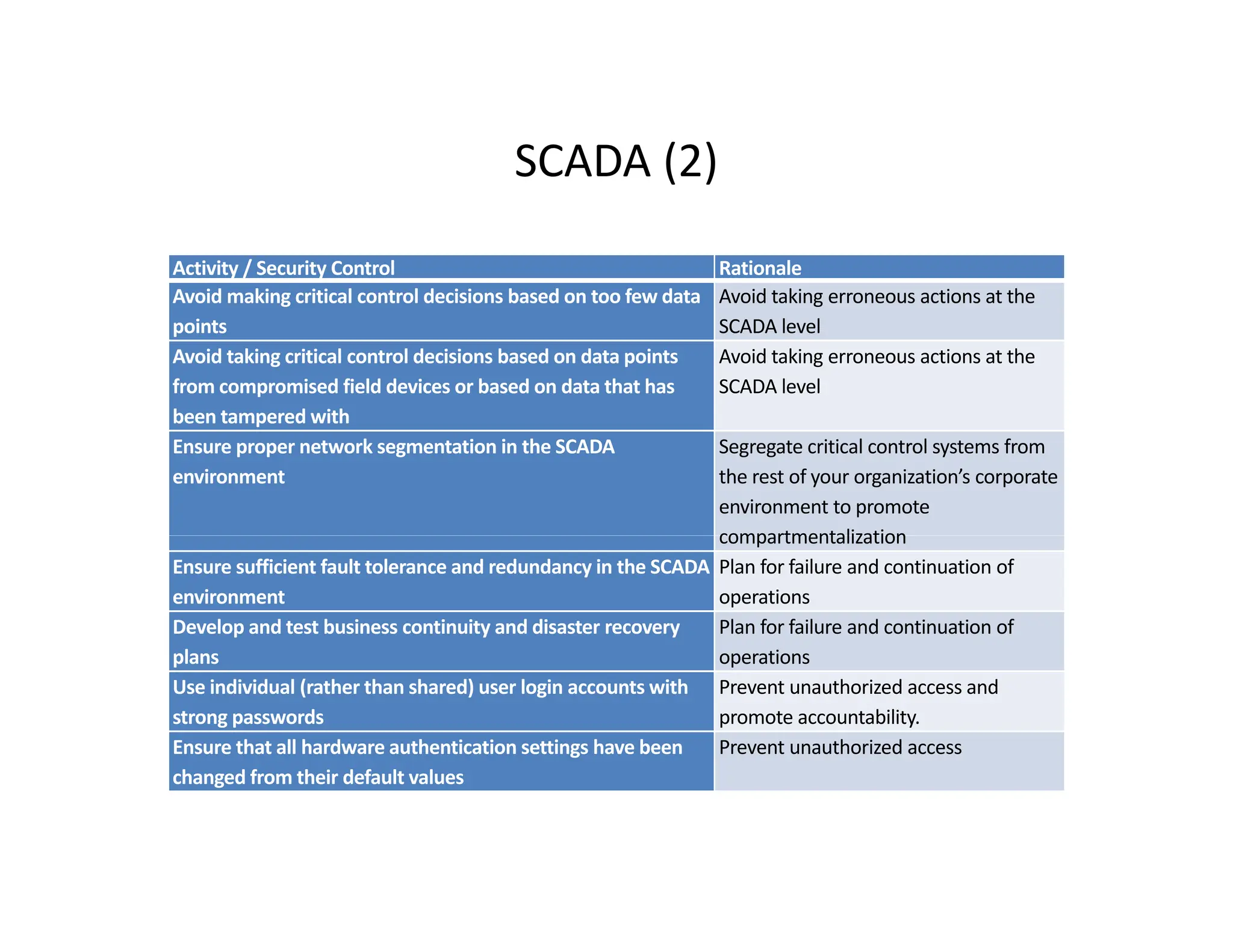
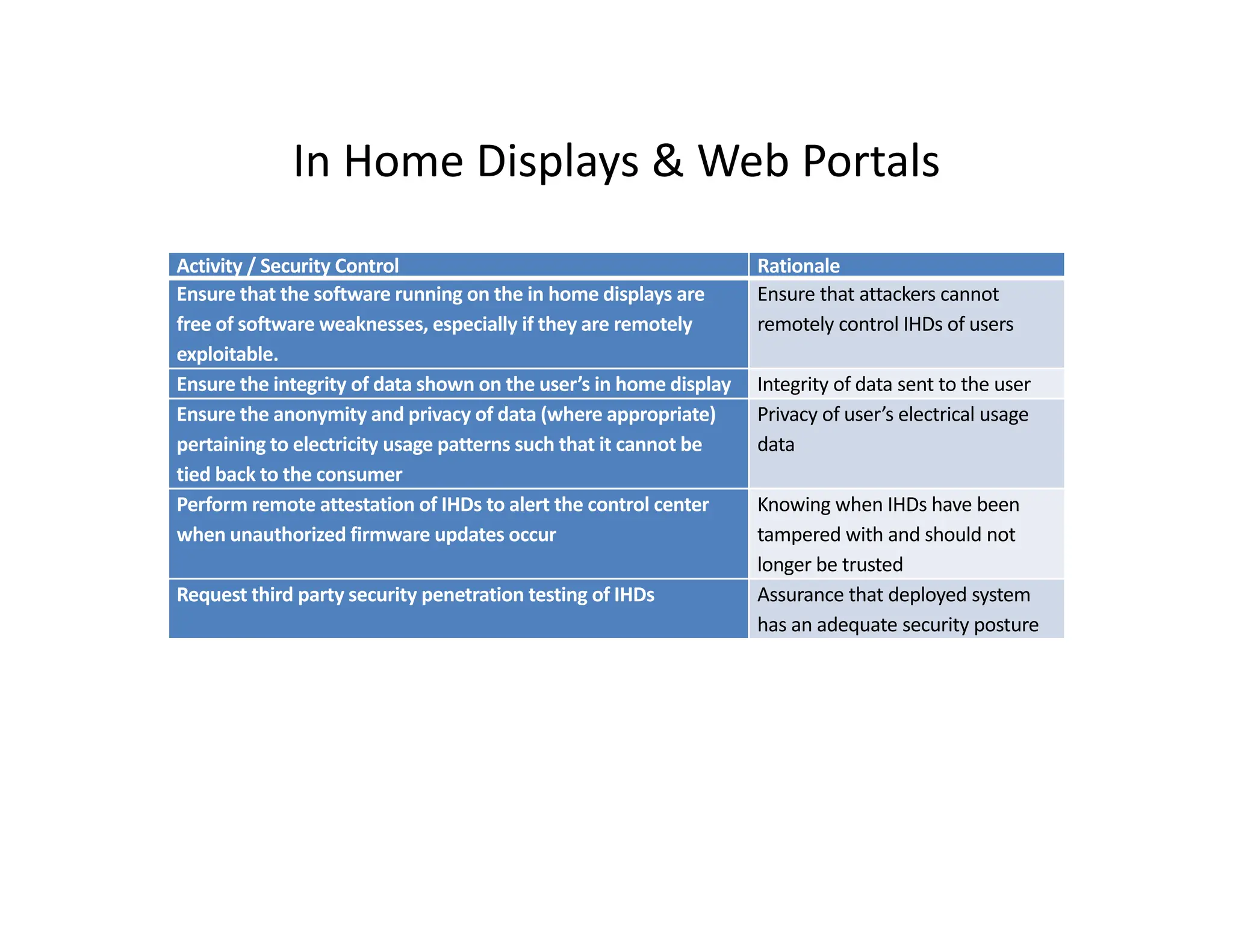
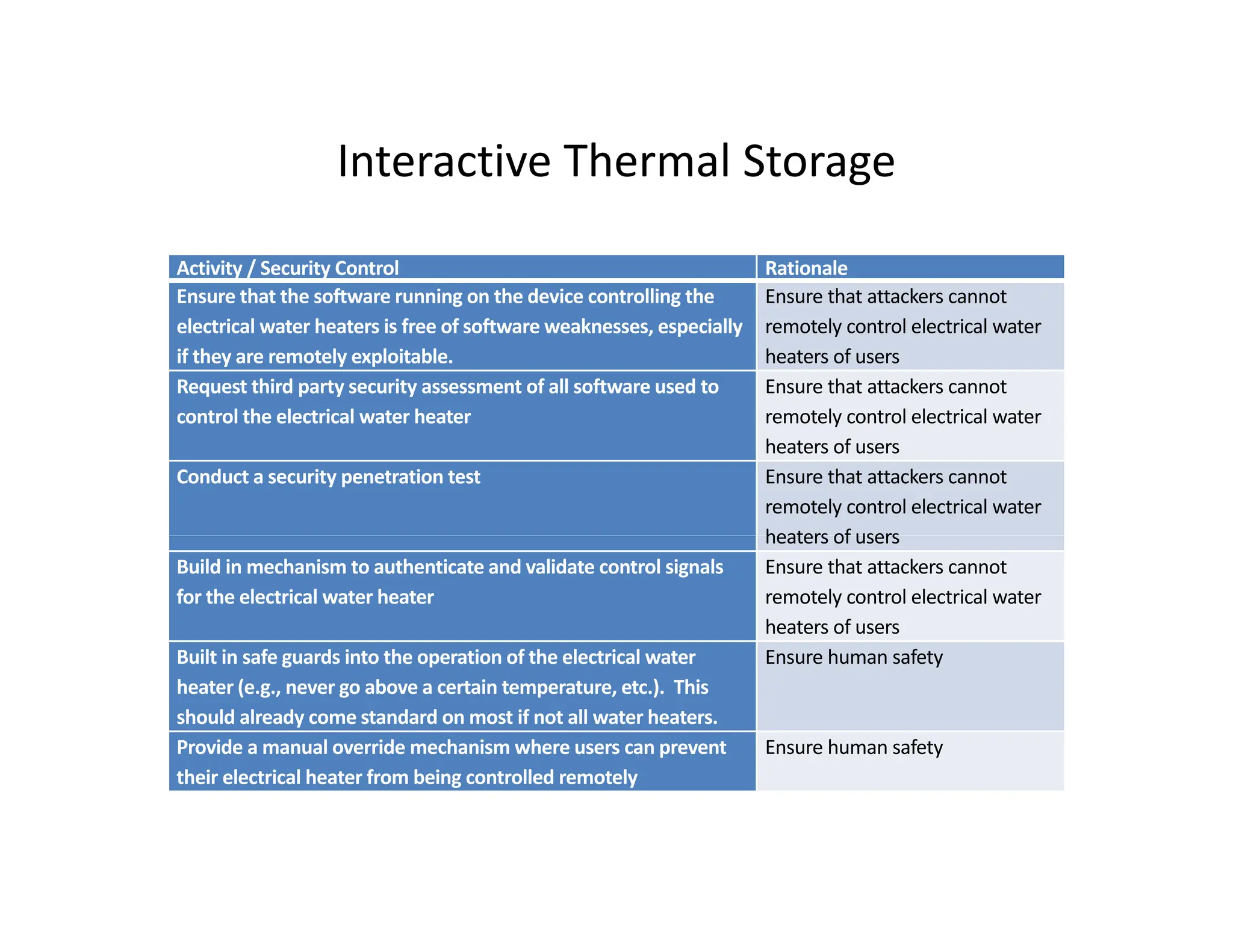
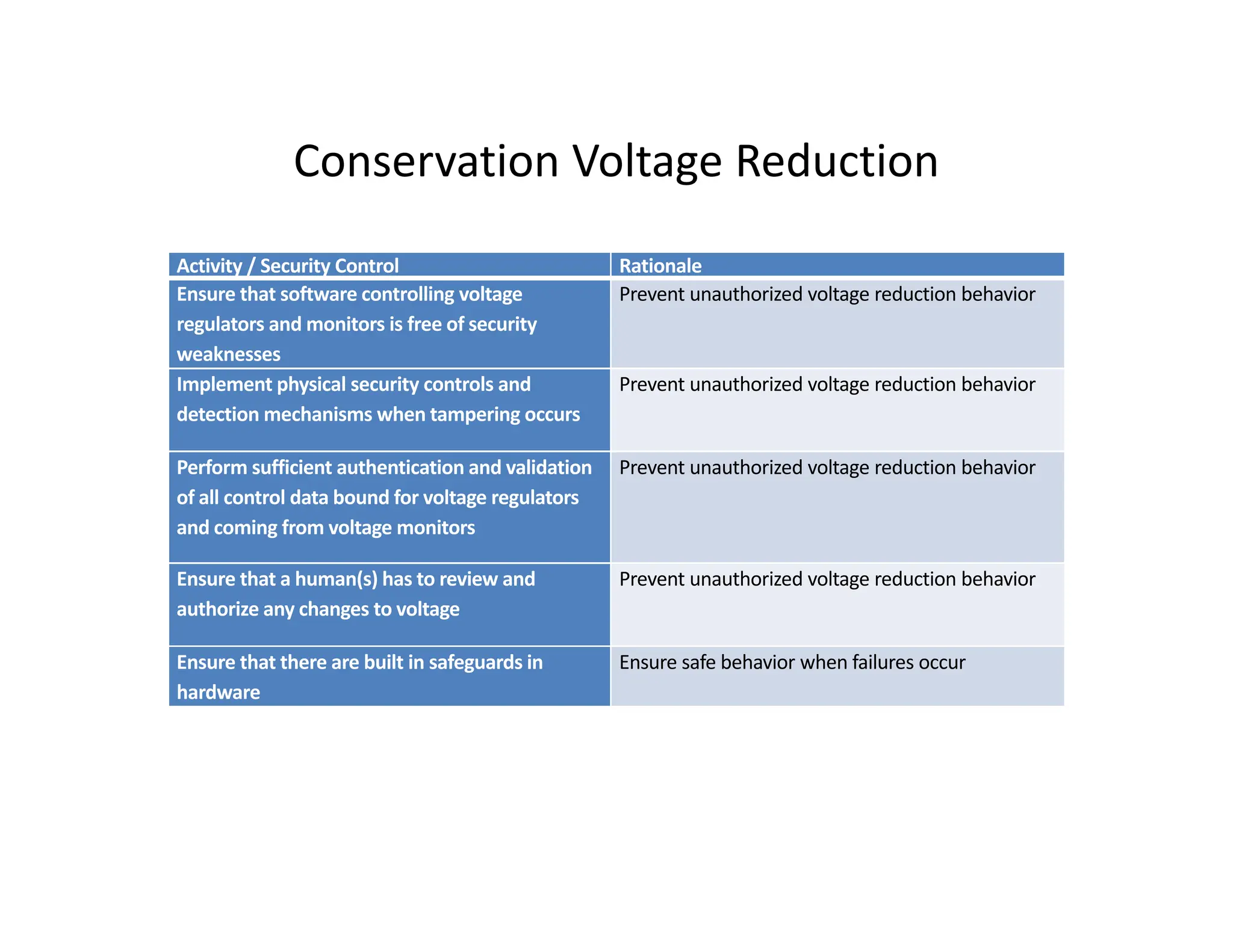
The document outlines a comprehensive cybersecurity risk mitigation checklist that includes building a risk management program, establishing cybersecurity policies, training personnel, and addressing operational, SDLC, physical, relationship, and network risks. Key actions include assigning responsibilities, performing vulnerability assessments, implementing controls, and ensuring proactive monitoring and response strategies. The goal is to ensure adequate protection of critical assets and maintain effective security processes across the organization.