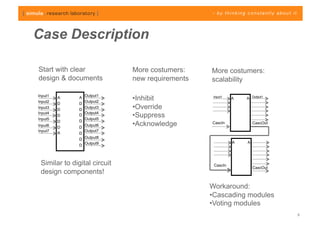
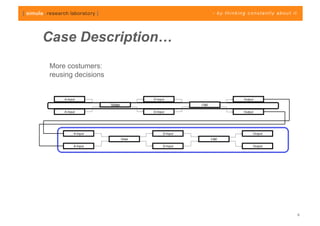
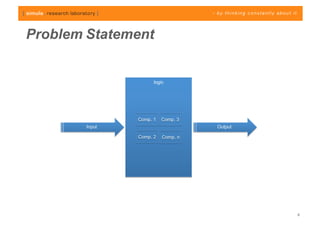
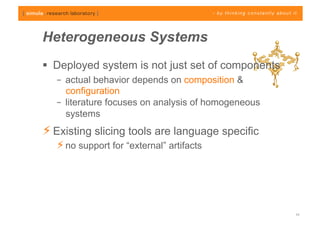
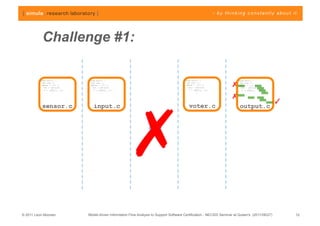
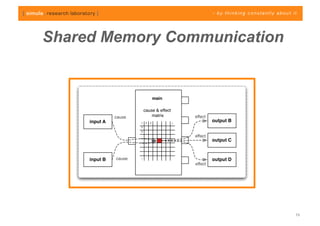
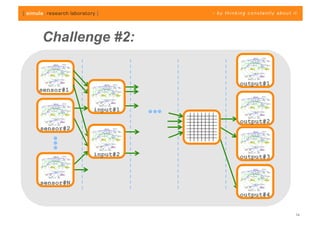
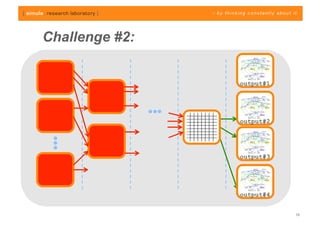
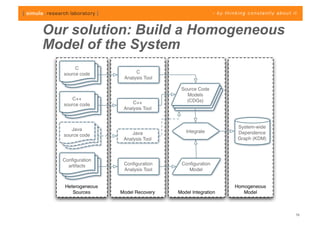
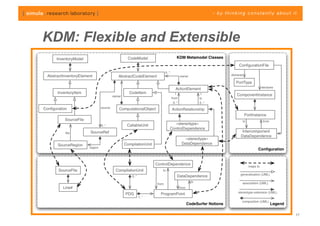
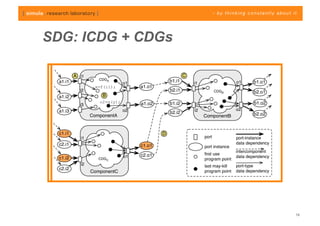
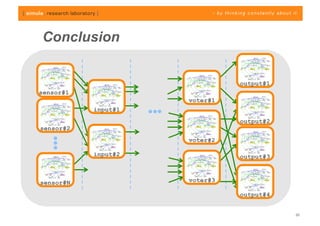
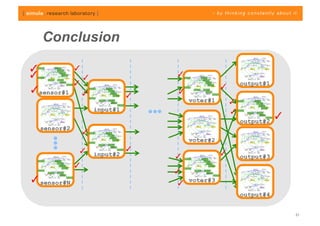
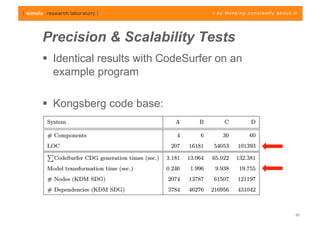
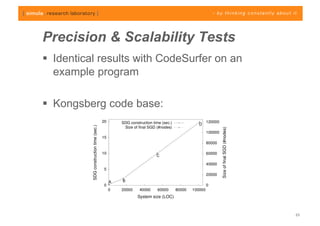
The document discusses challenges in analyzing heterogeneous component-based software systems, focusing on safety monitoring and control systems. It emphasizes the need for a model-driven information flow analysis approach to ensure that sensor signals reach the correct actuators for certification purposes and proposes building a homogeneous model of the system. Limitations are noted, including issues with bit manipulation and the need for improvements in abstraction and visualization for comprehensibility.