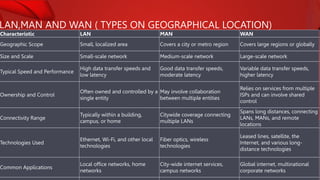
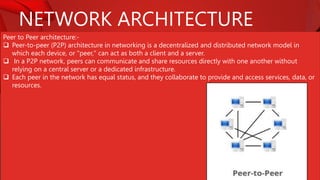
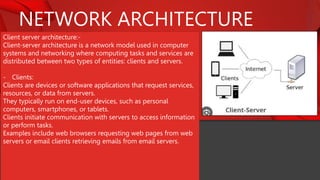
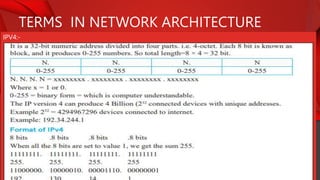
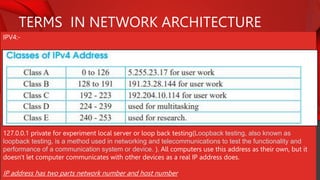
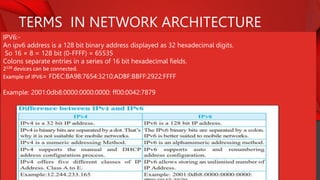
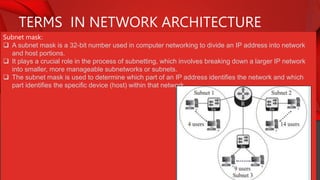
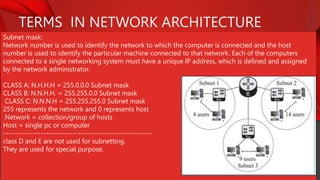
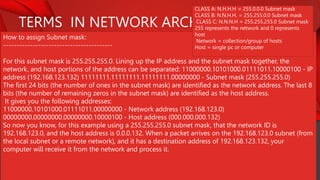
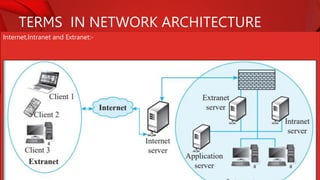
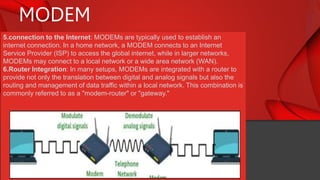
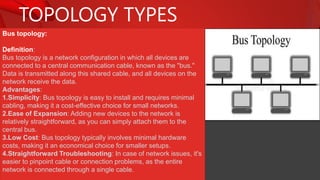
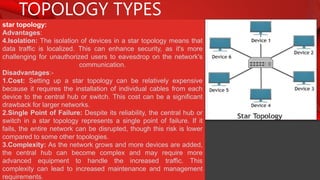
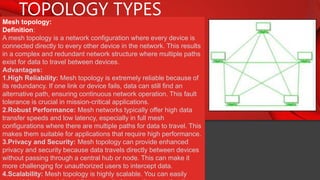
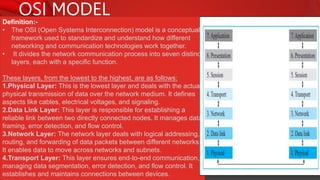
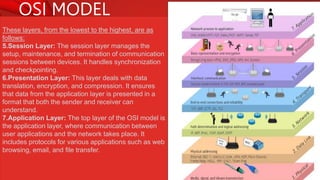
The document describes the components and functions of a communication system, including information sources, encoders, transmitters, channels, receivers, and destinations. It explains different communication modes: simplex, half-duplex, and full-duplex, as well as types of networks like LAN, MAN, and WAN. Additionally, it covers transmission media (wired and wireless), impairments affecting transmission quality, and network architectures such as peer-to-peer and client-server models.