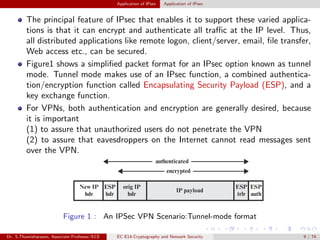
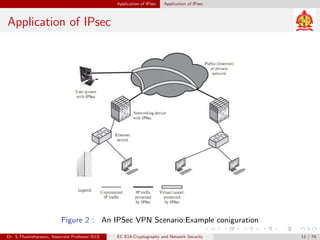
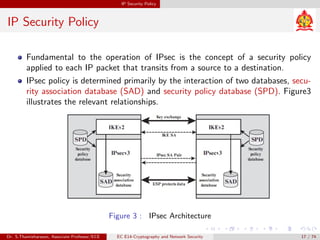
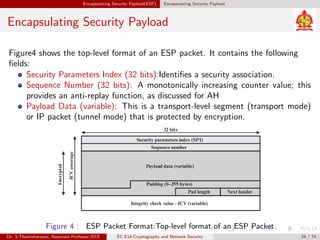
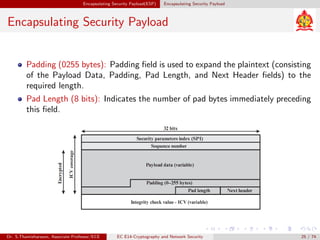
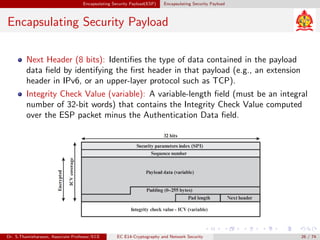
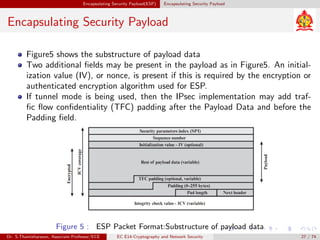
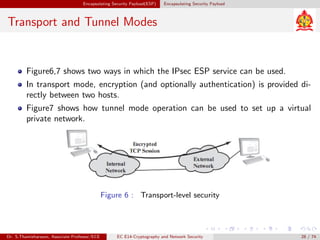
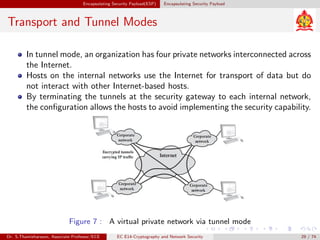
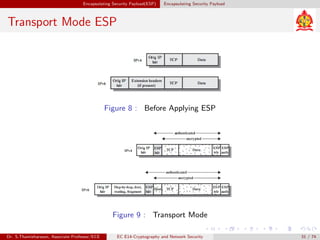
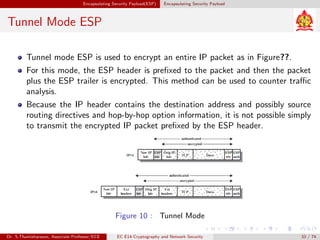
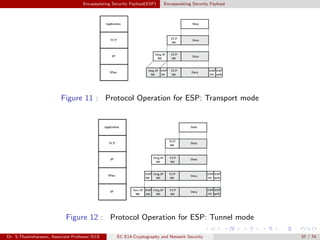
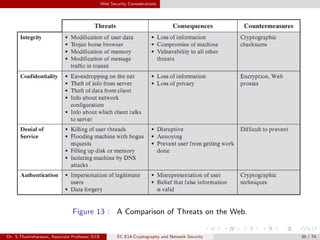
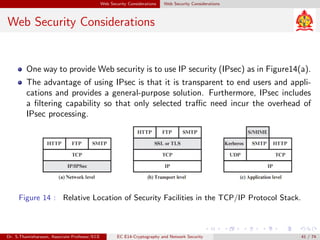
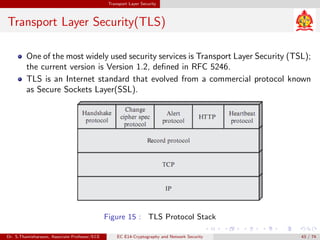
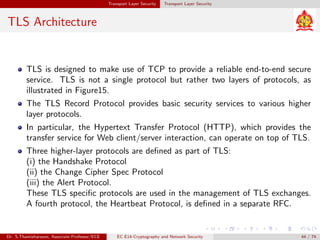
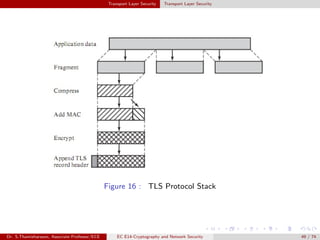
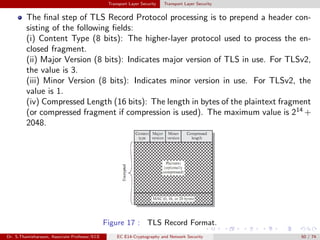
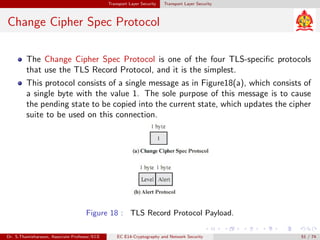
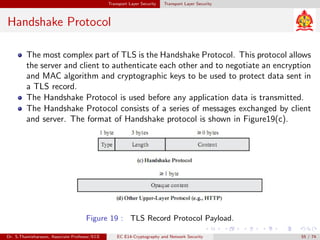
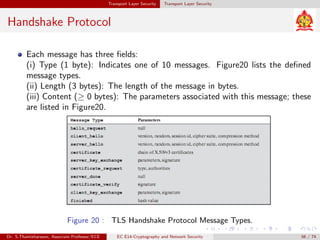
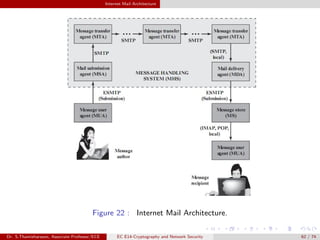
The document discusses IP security (IPsec) and its various components. It covers IPsec overview, applications of IPsec like VPNs, benefits of IPsec, IPsec documents that define its architecture and protocols, IPsec services for authentication, encryption, anti-replay etc. It also describes security associations, security policy database, encapsulating security payload (ESP) protocol and how IPsec provides security at the network layer.