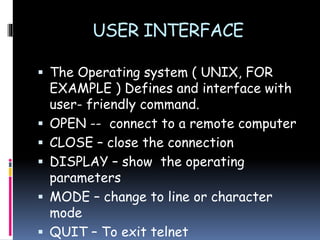
This document provides an overview of email and telnet. It defines email as allowing users to exchange messages through a user agent program. It describes the basic components and processes for sending, receiving, and addressing emails. It also discusses email security protocols and mailing lists. For telnet, the document explains that it allows remote logging into another computer through a network virtual terminal. It compares local versus remote logging and describes basic telnet user commands.