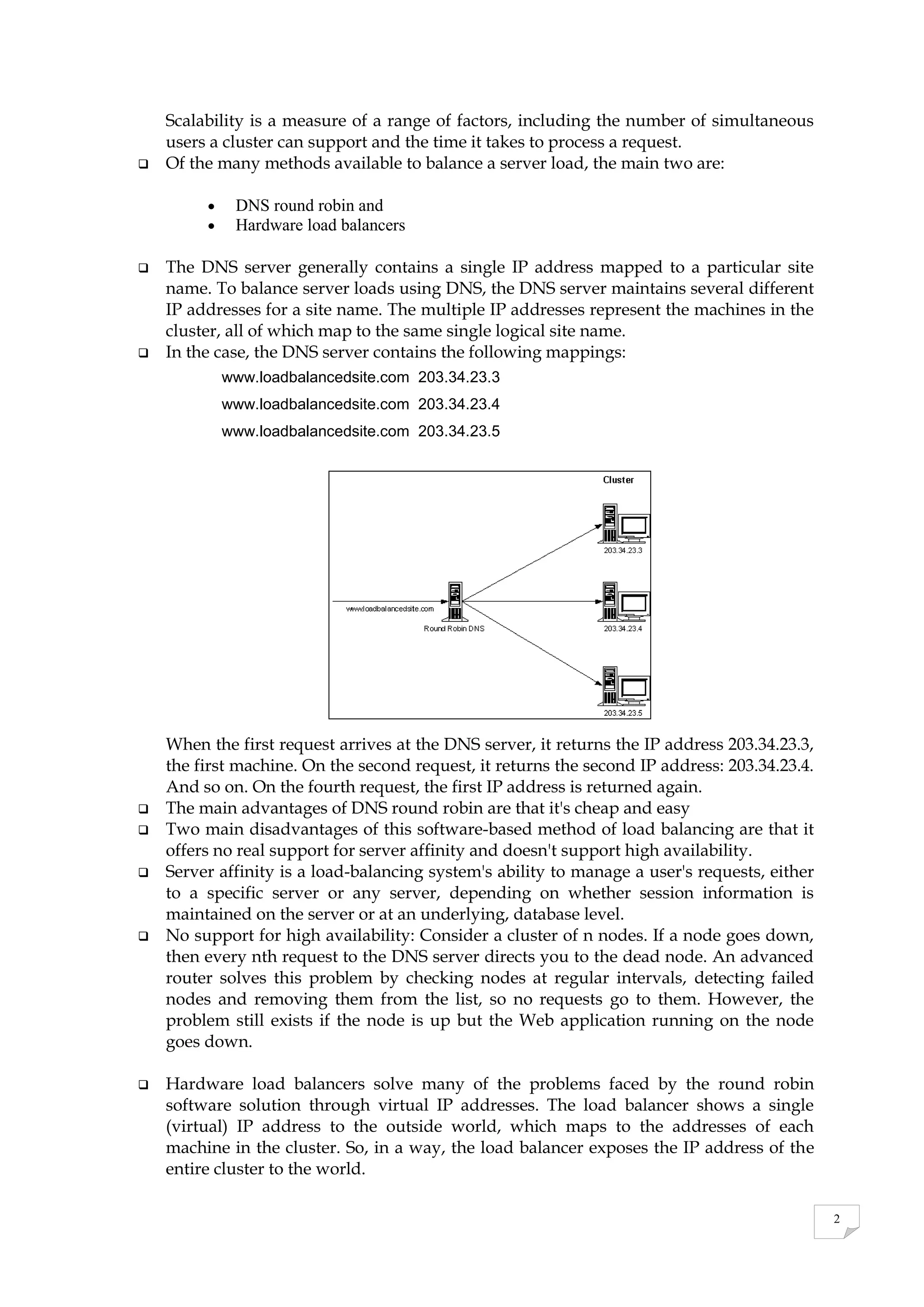
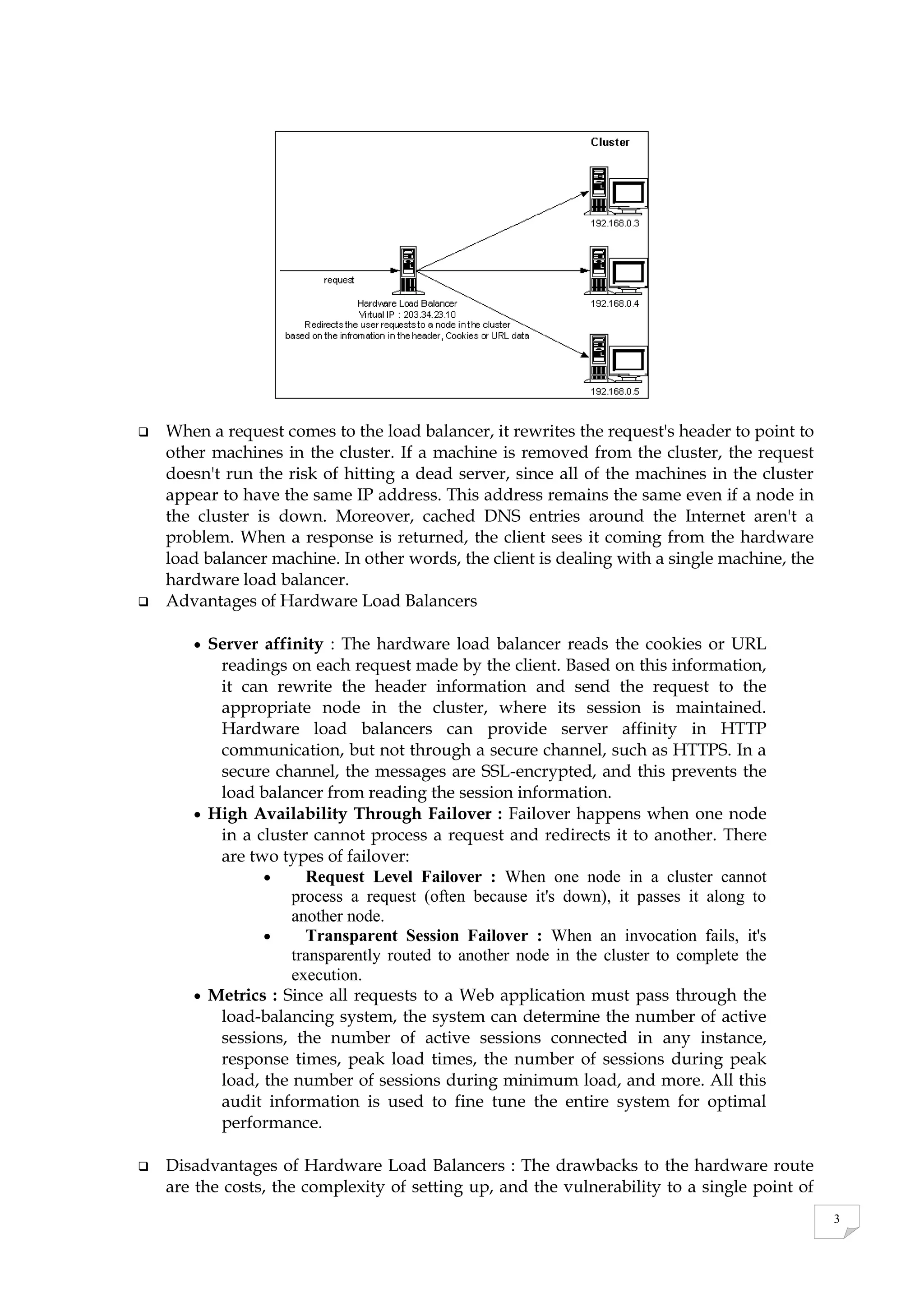
A cluster is a group of machines that work together to provide services like load balancing. Clusters can include load balancers, web servers, routers, switches, firewalls, and databases. Load balancing distributes requests across servers in a cluster to optimize performance and availability. Common load balancing methods are DNS round robin, which distributes IP addresses, and hardware load balancers, which provide a single virtual IP address for the cluster. Hardware load balancers offer high availability and can maintain sessions across servers.