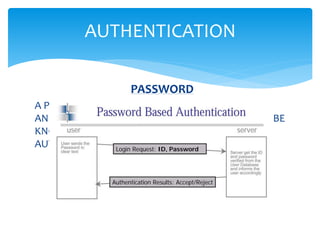
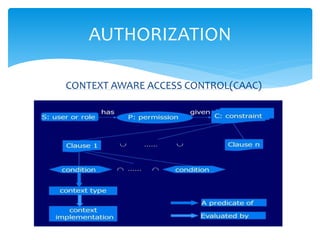
This document contains information about Sourodeep Chakraborty, a student in the 5th semester with ID BGC201120. It discusses cloud computing security topics like authentication, authorization, auditing, and accountability. Authentication verifies a user's identity using credentials like usernames and passwords. Authorization controls user privileges and access to resources. Auditing monitors systems and user activity for compliance. Accountability develops a holistic approach to security involving legal, regulatory, and technical mechanisms. The document also covers challenges of cloud security like lack of network supervision and potential for misconfiguration or human errors.