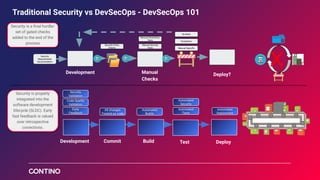
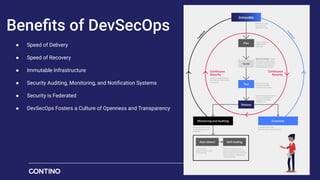
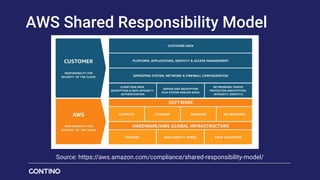
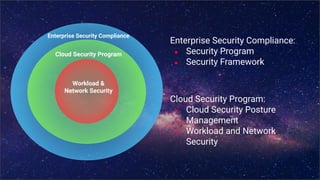
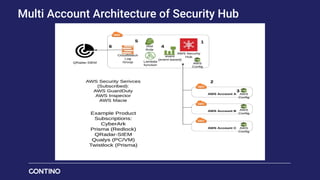
The document outlines Contino's approach to AWS cloud governance and security through automation, emphasizing the importance of integrating security within the DevSecOps practice. It highlights key outcomes achieved for clients, such as significant reductions in manual effort and improved compliance ratings through automated solutions. Additionally, it offers insights into security frameworks, practices, and tools necessary for ensuring compliance and effective security management in cloud environments.