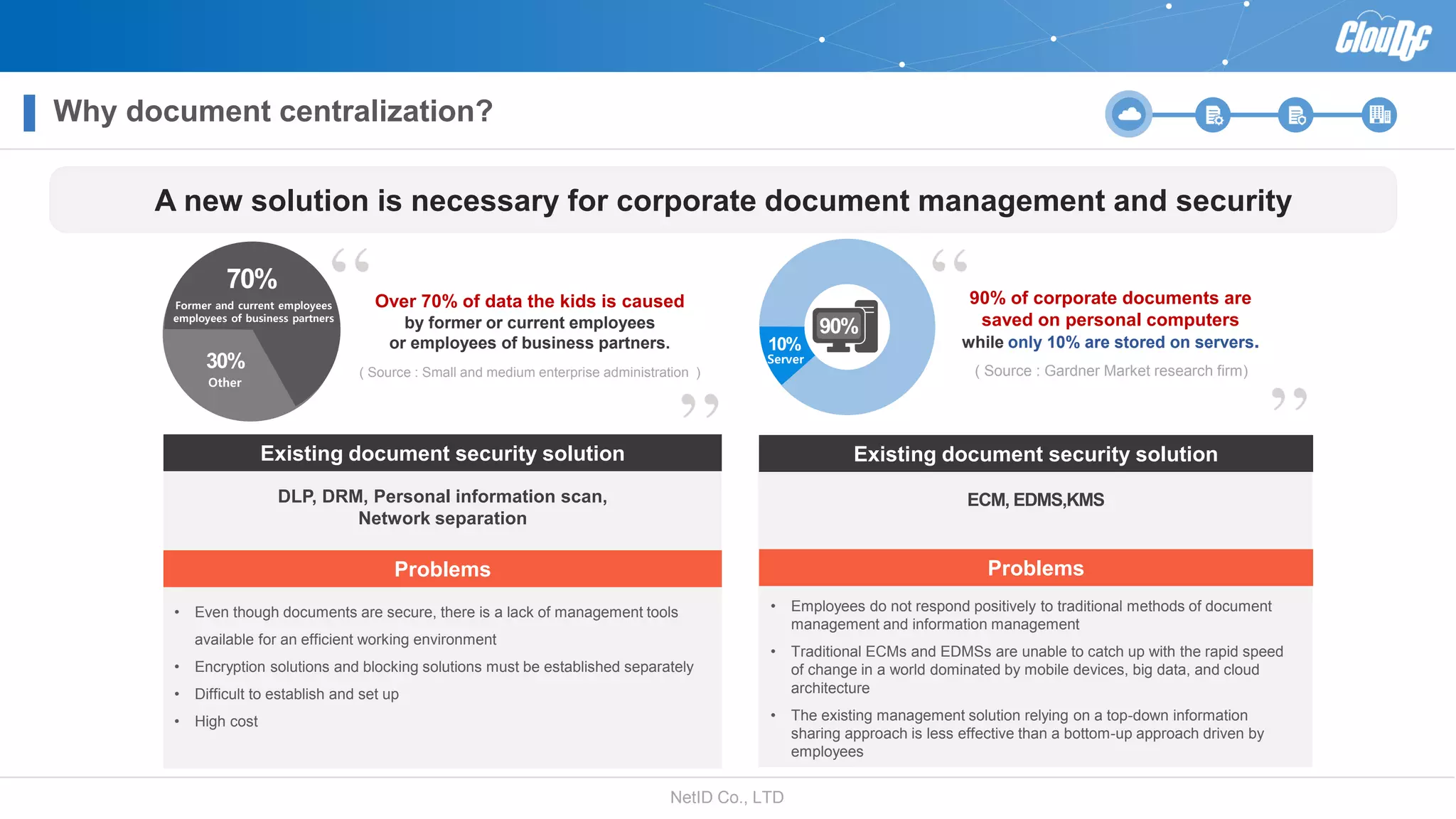
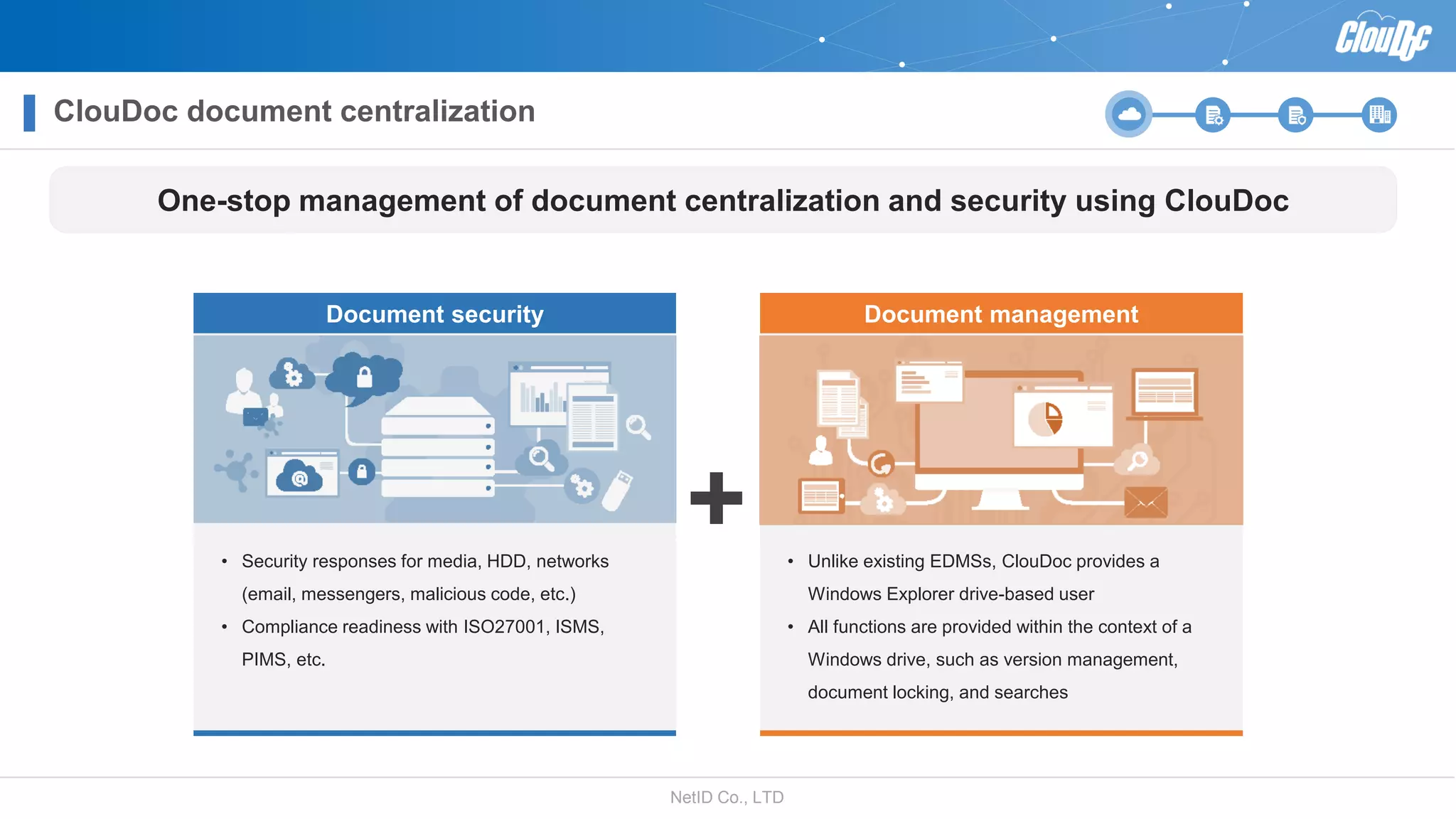
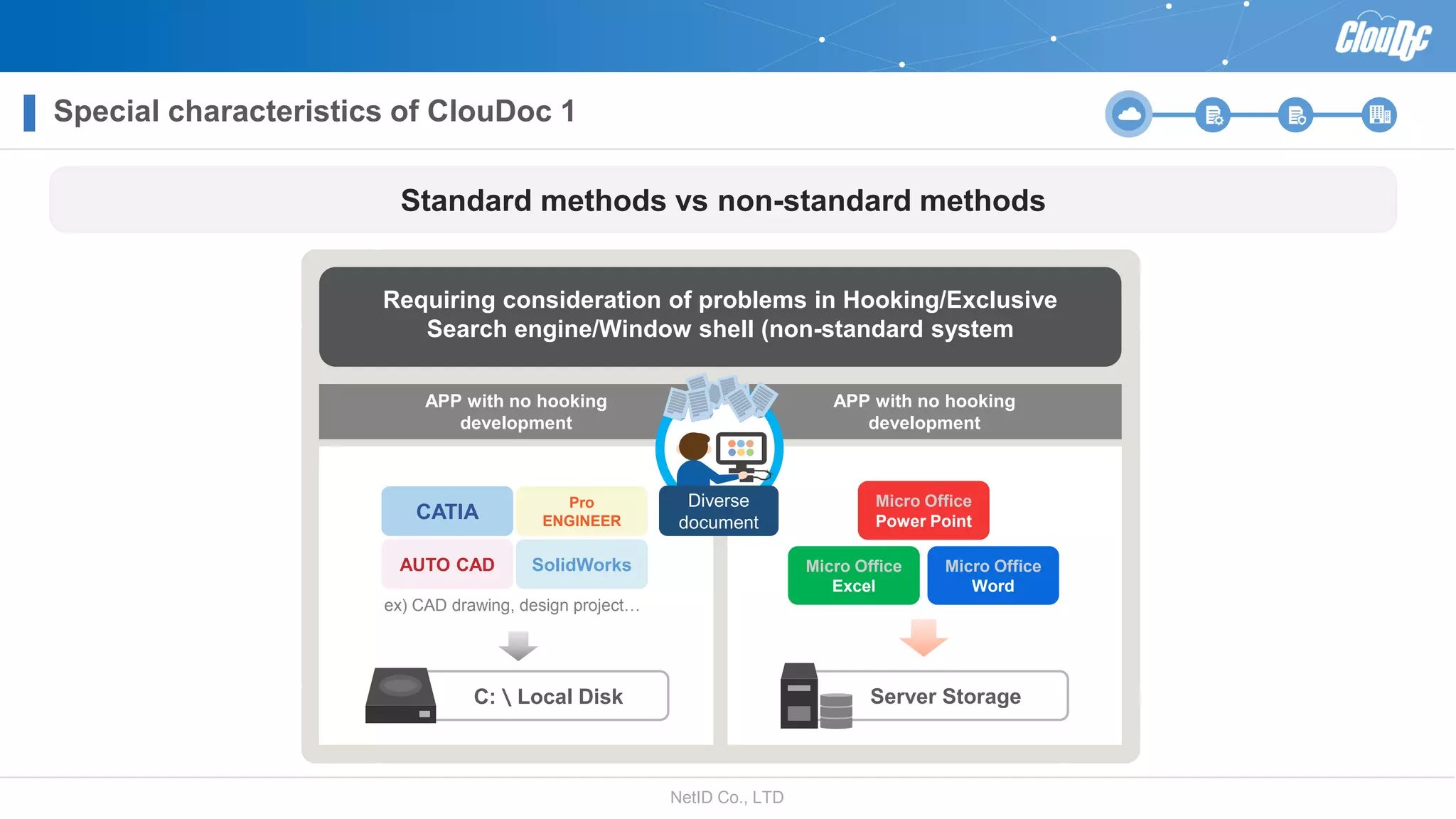
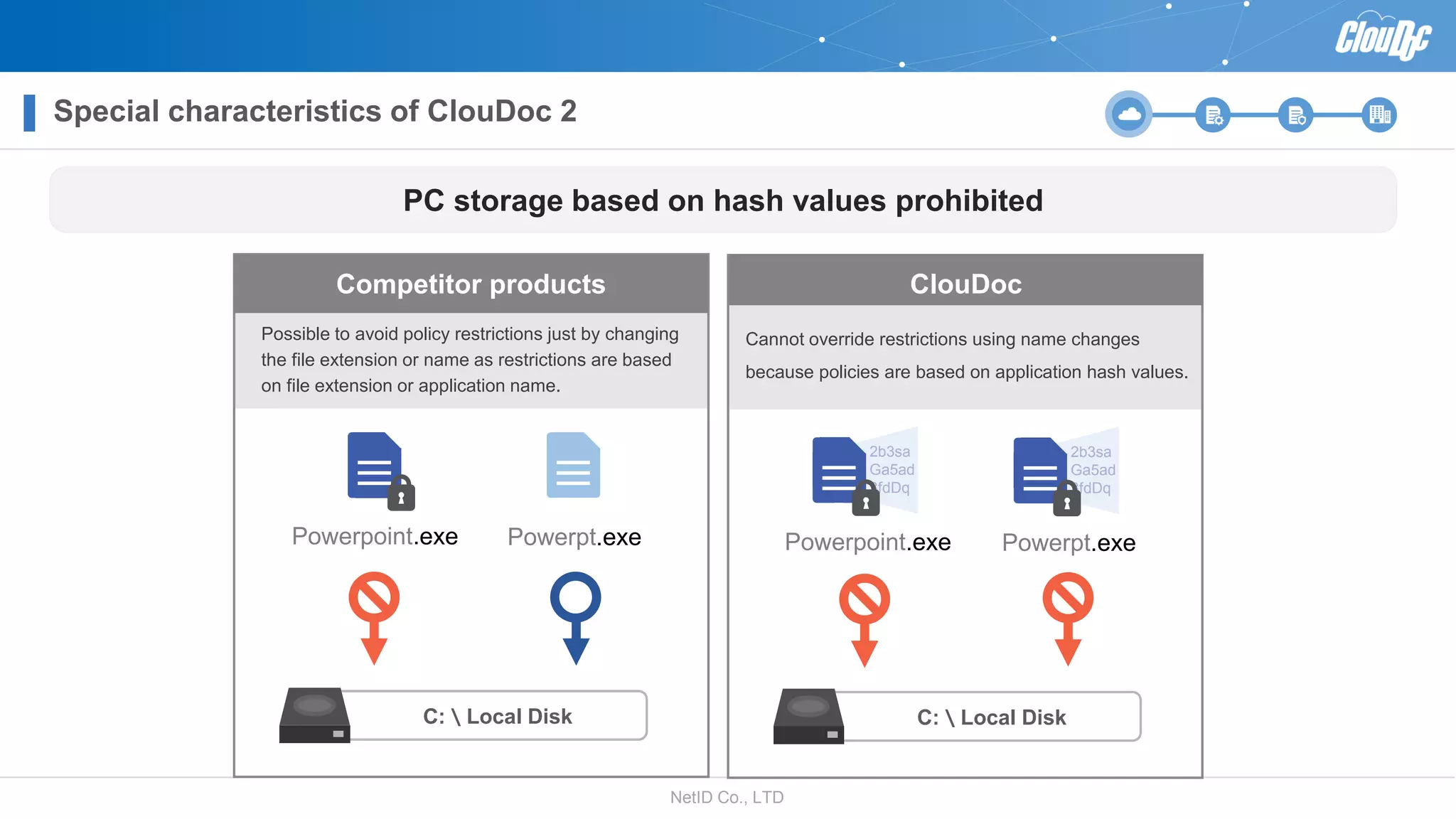
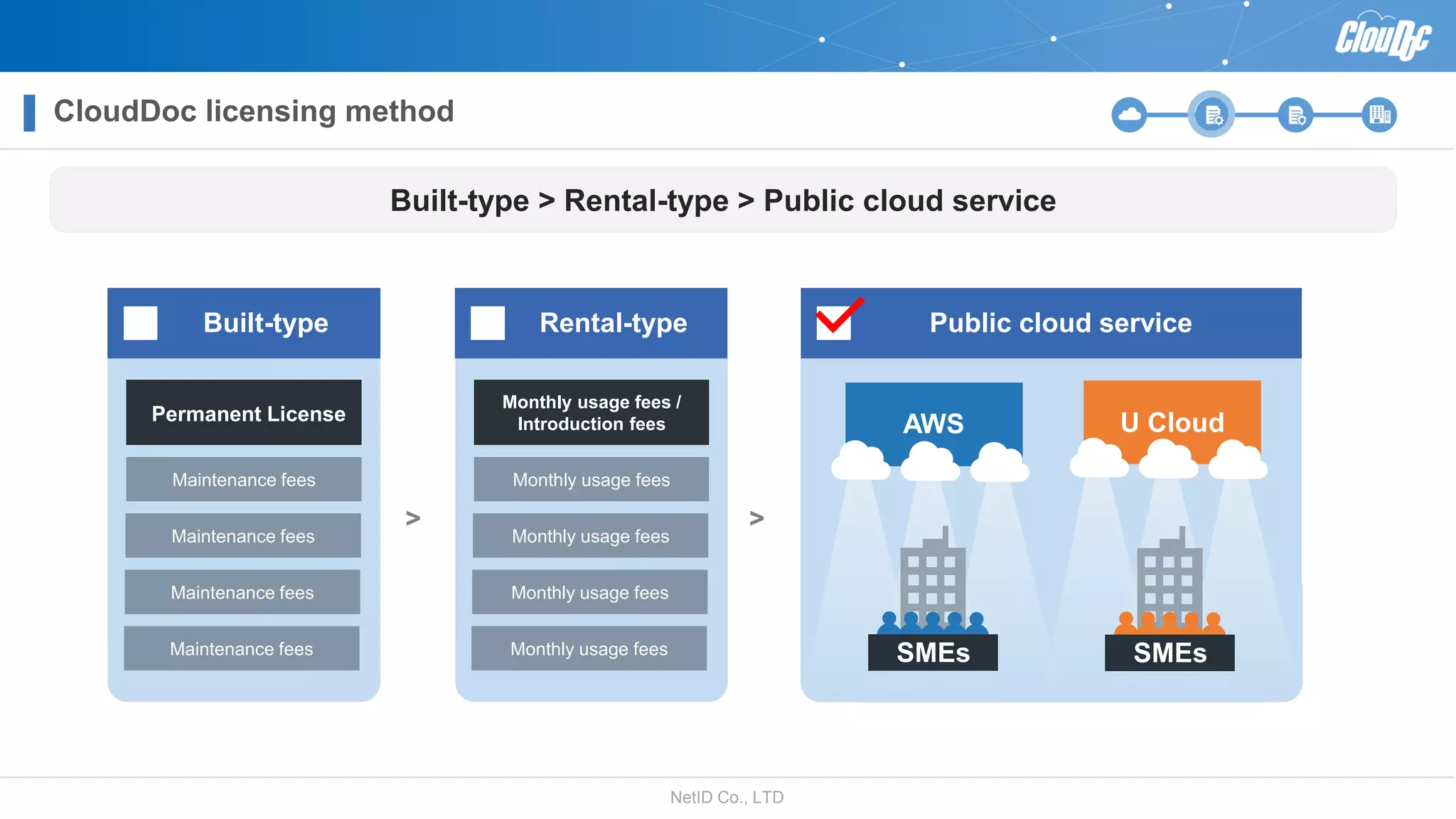
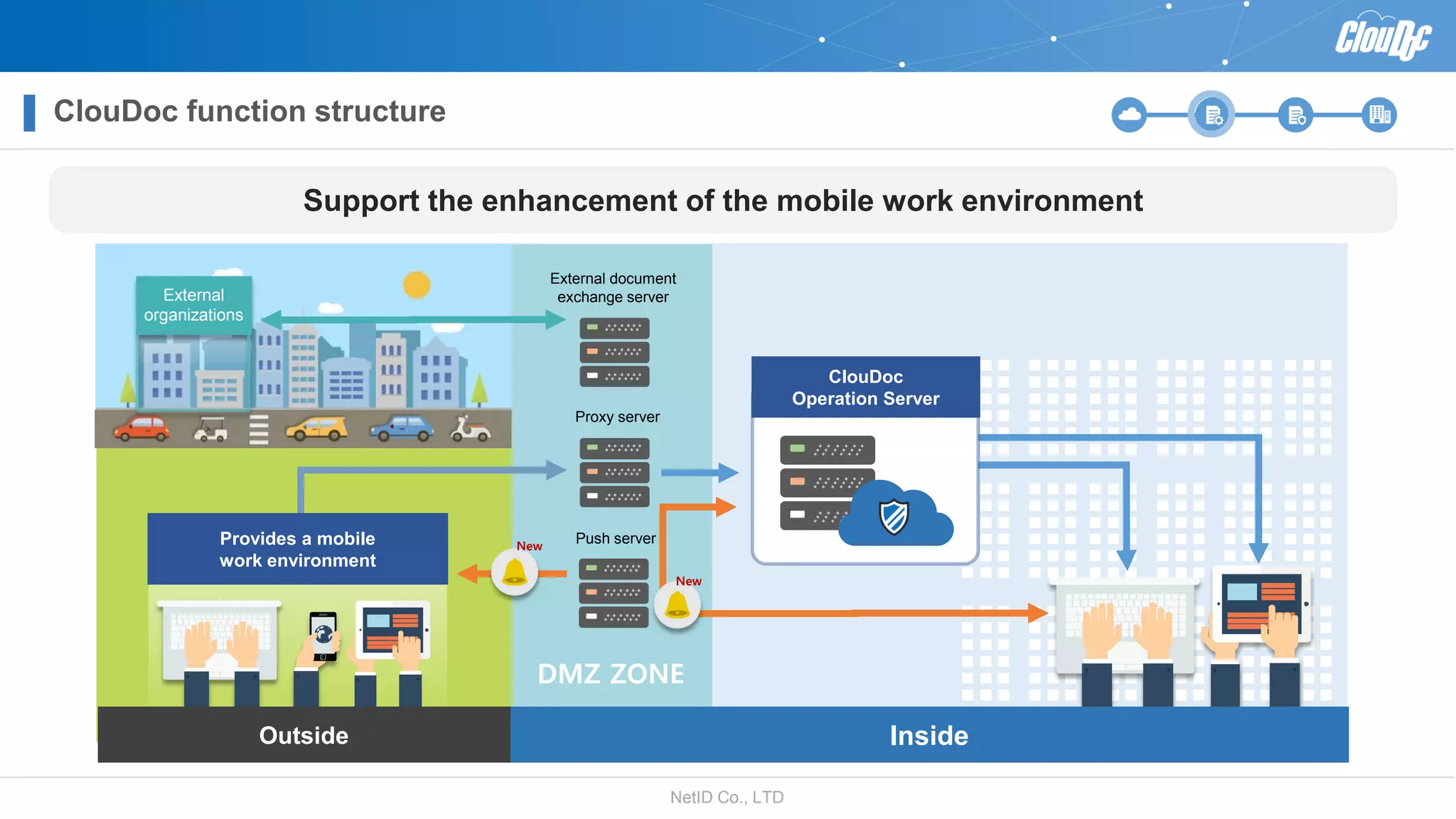
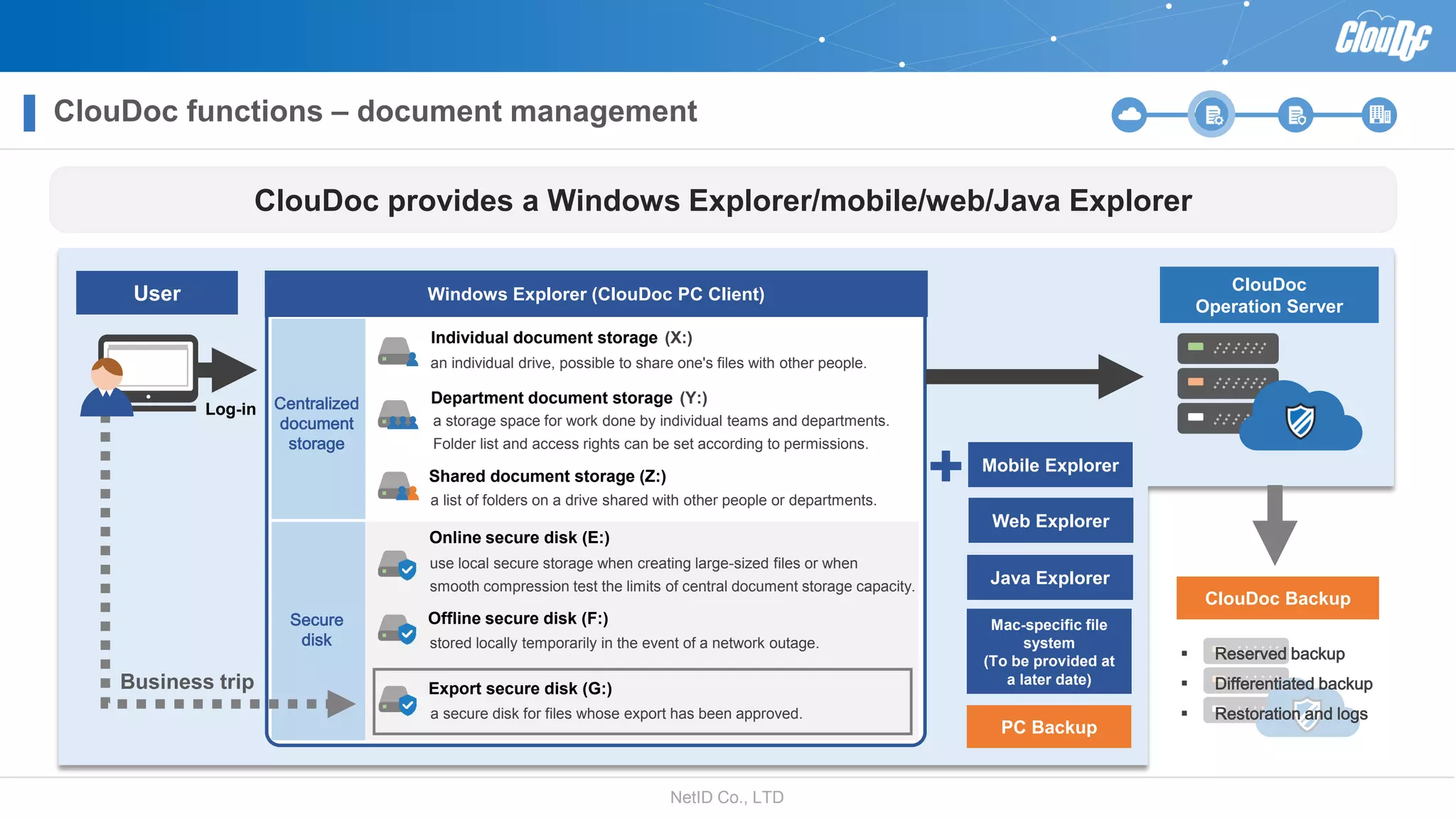
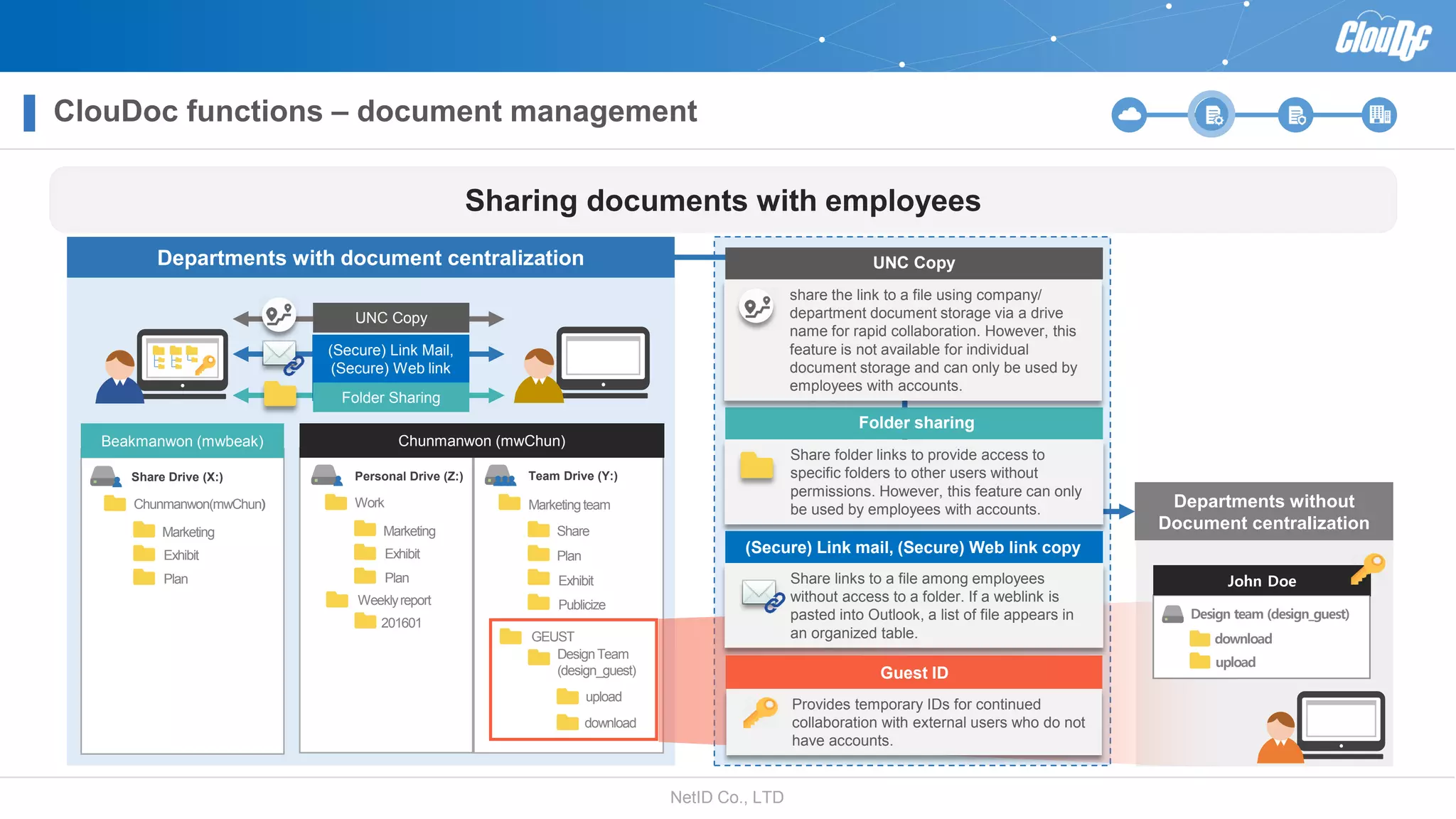
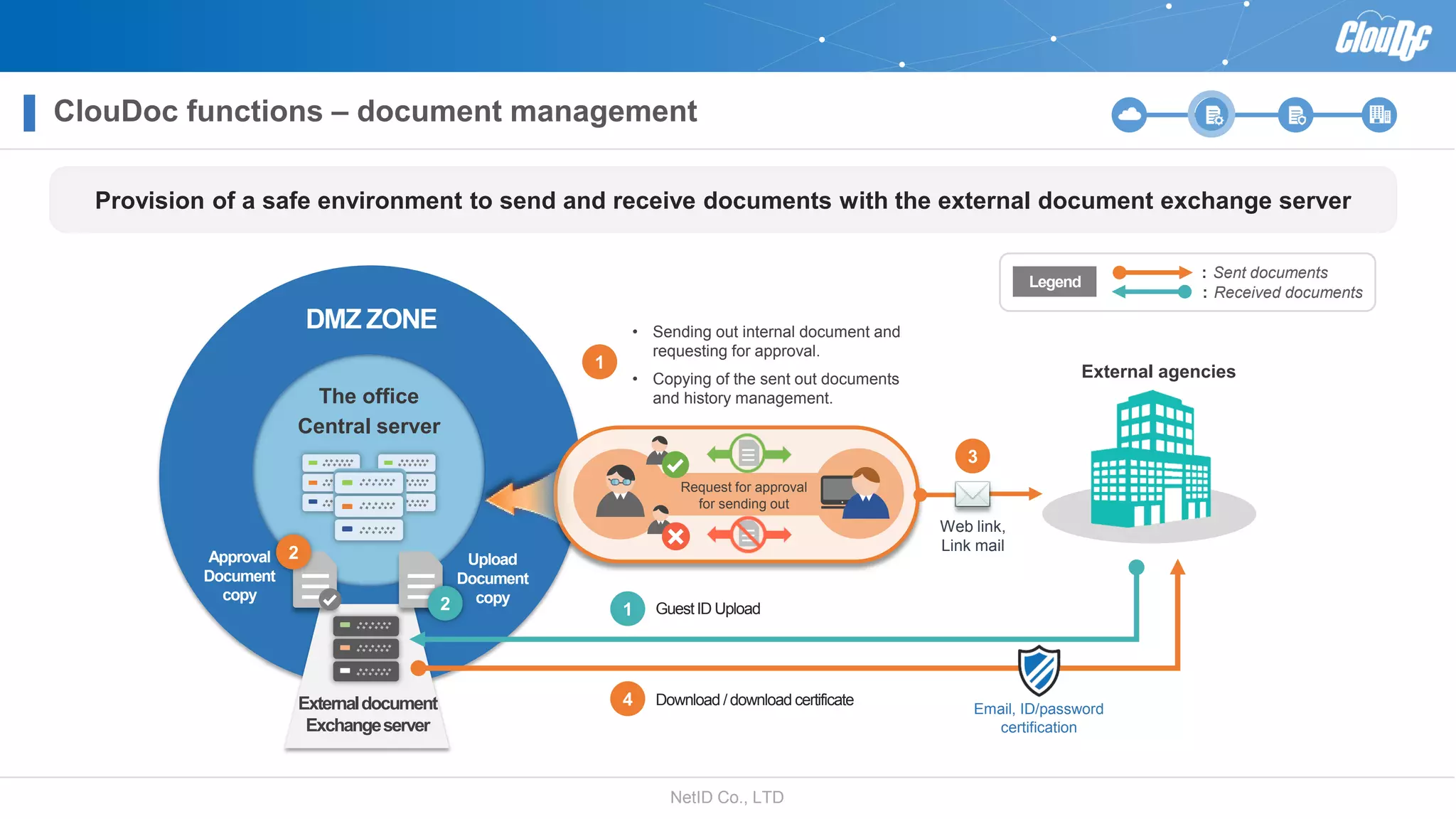
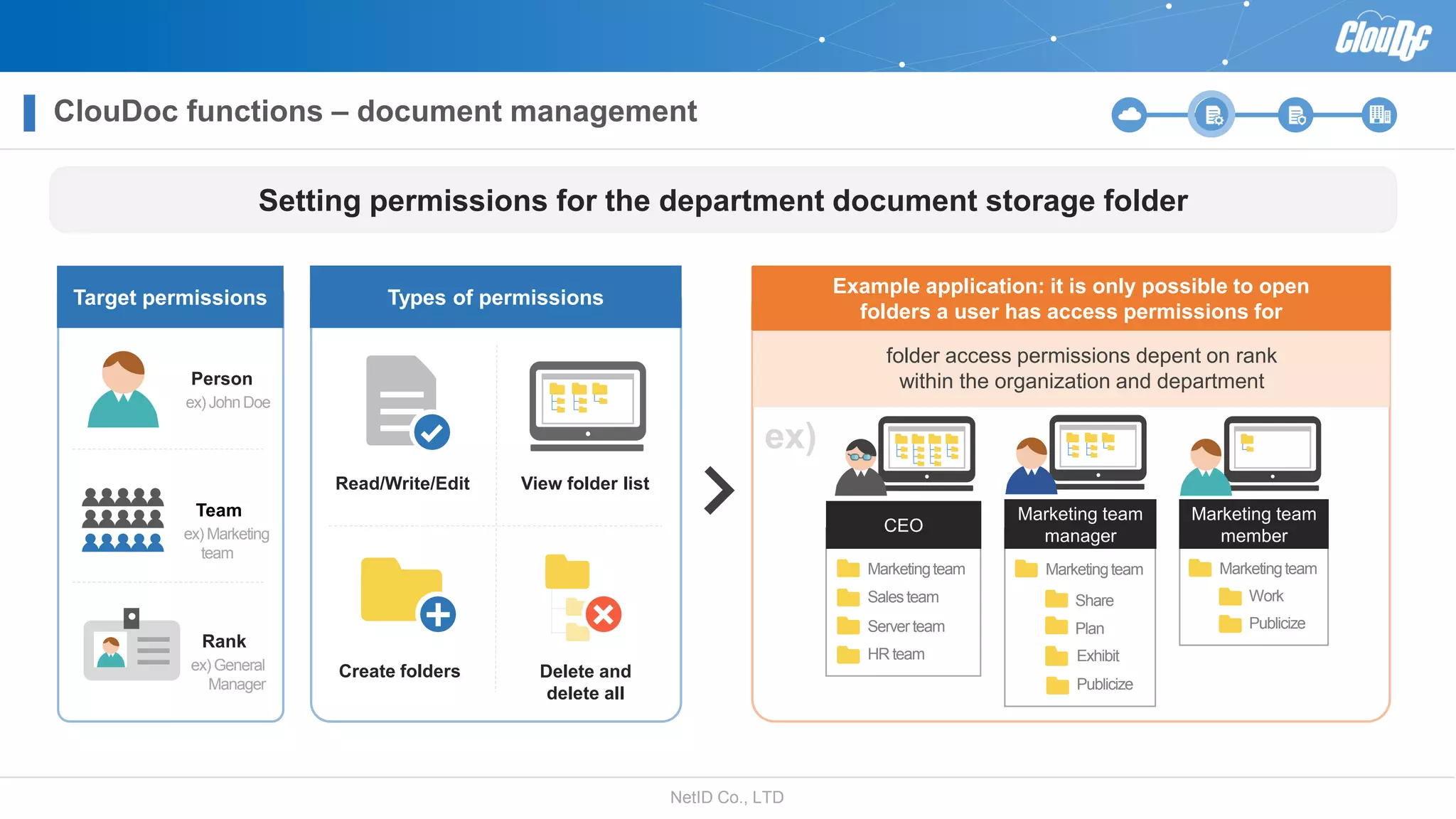
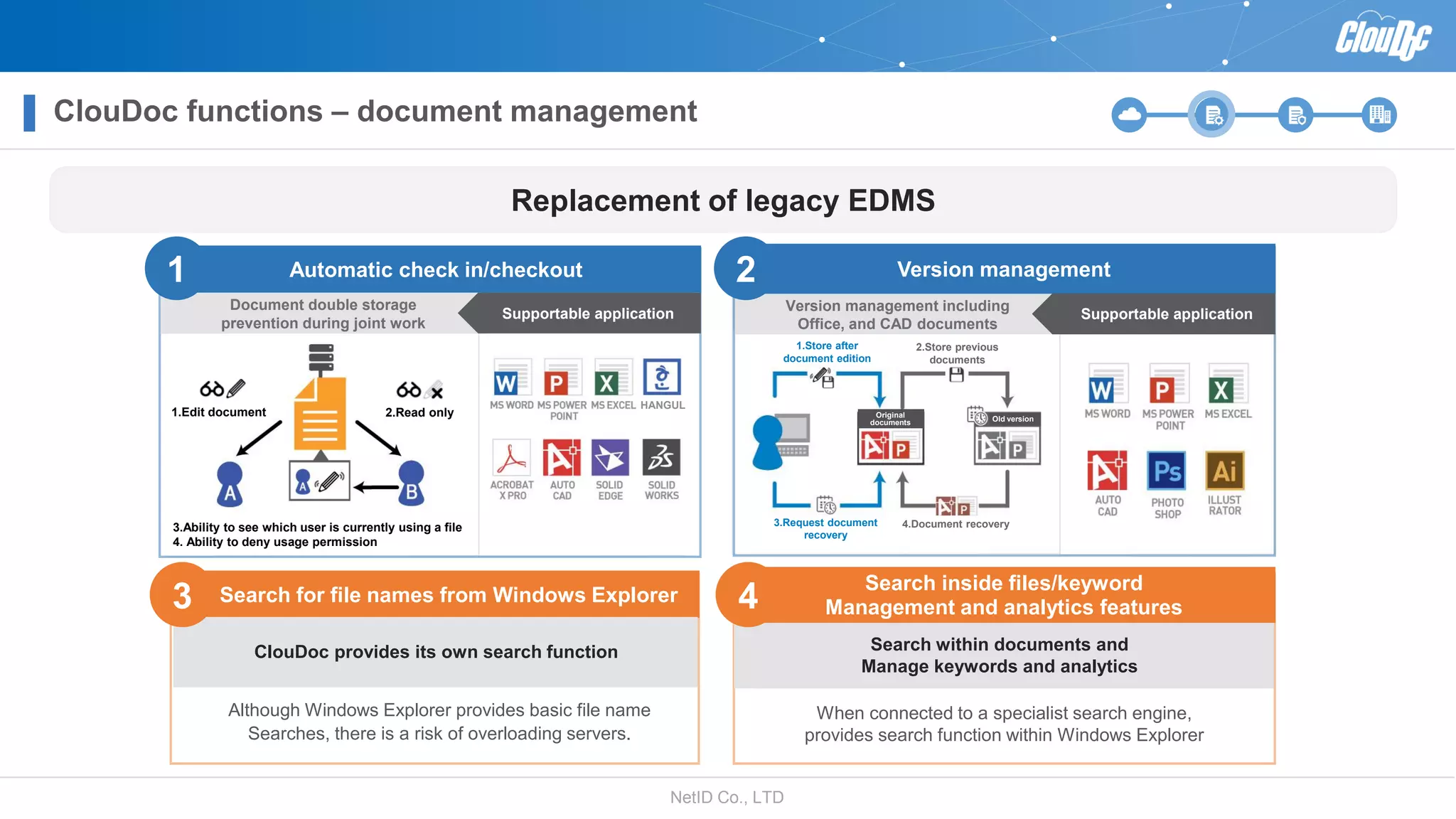
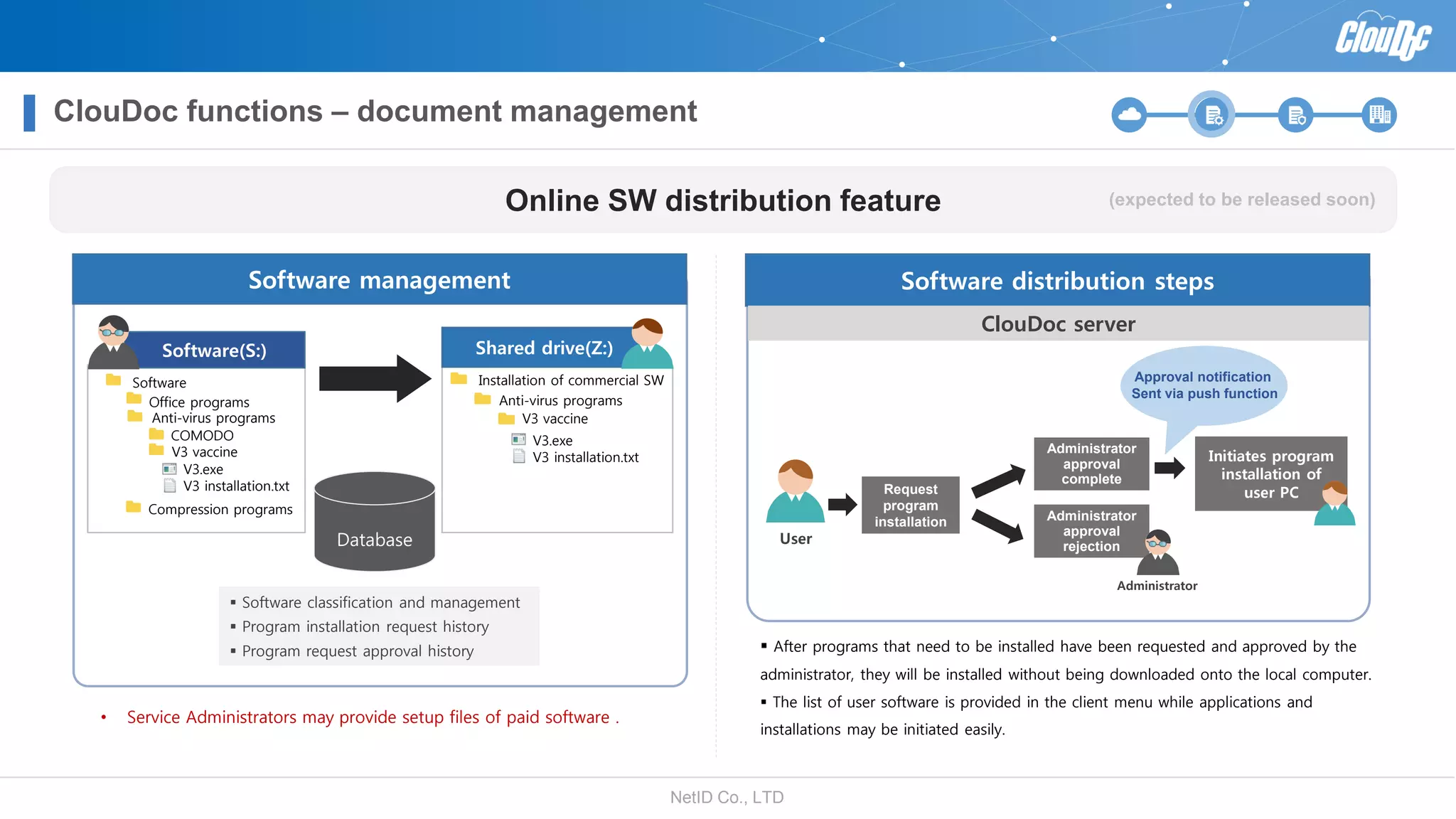
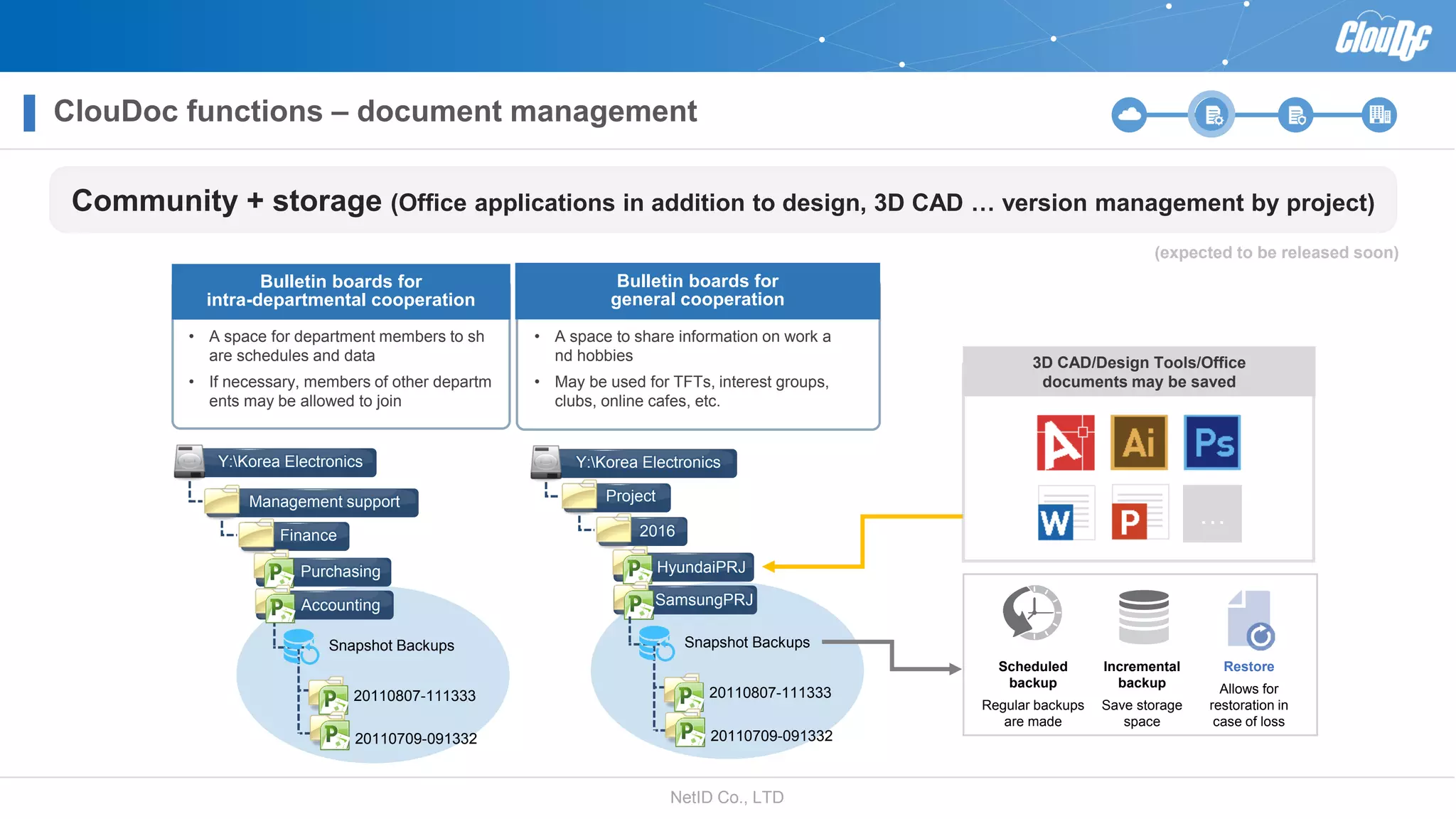
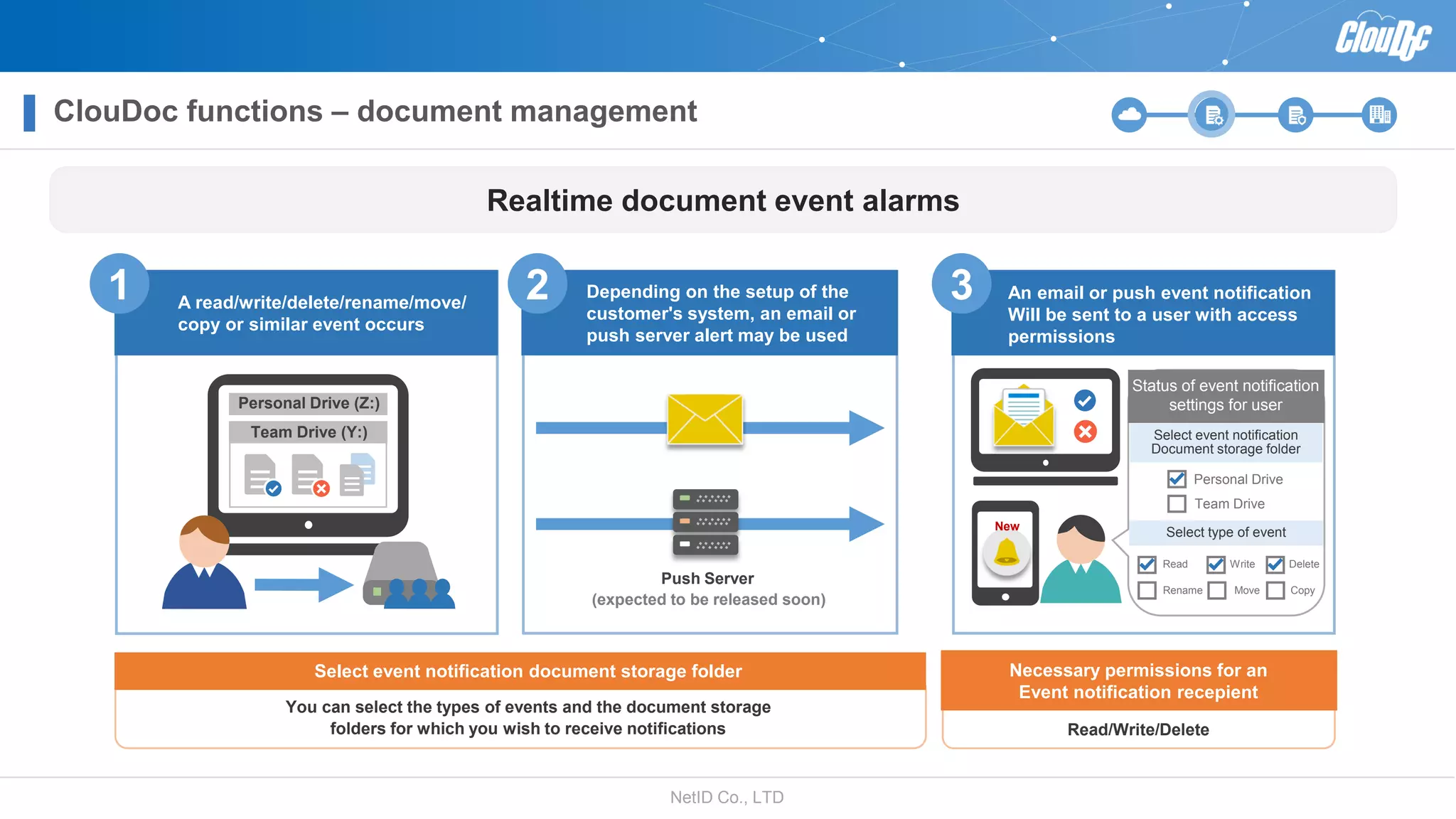
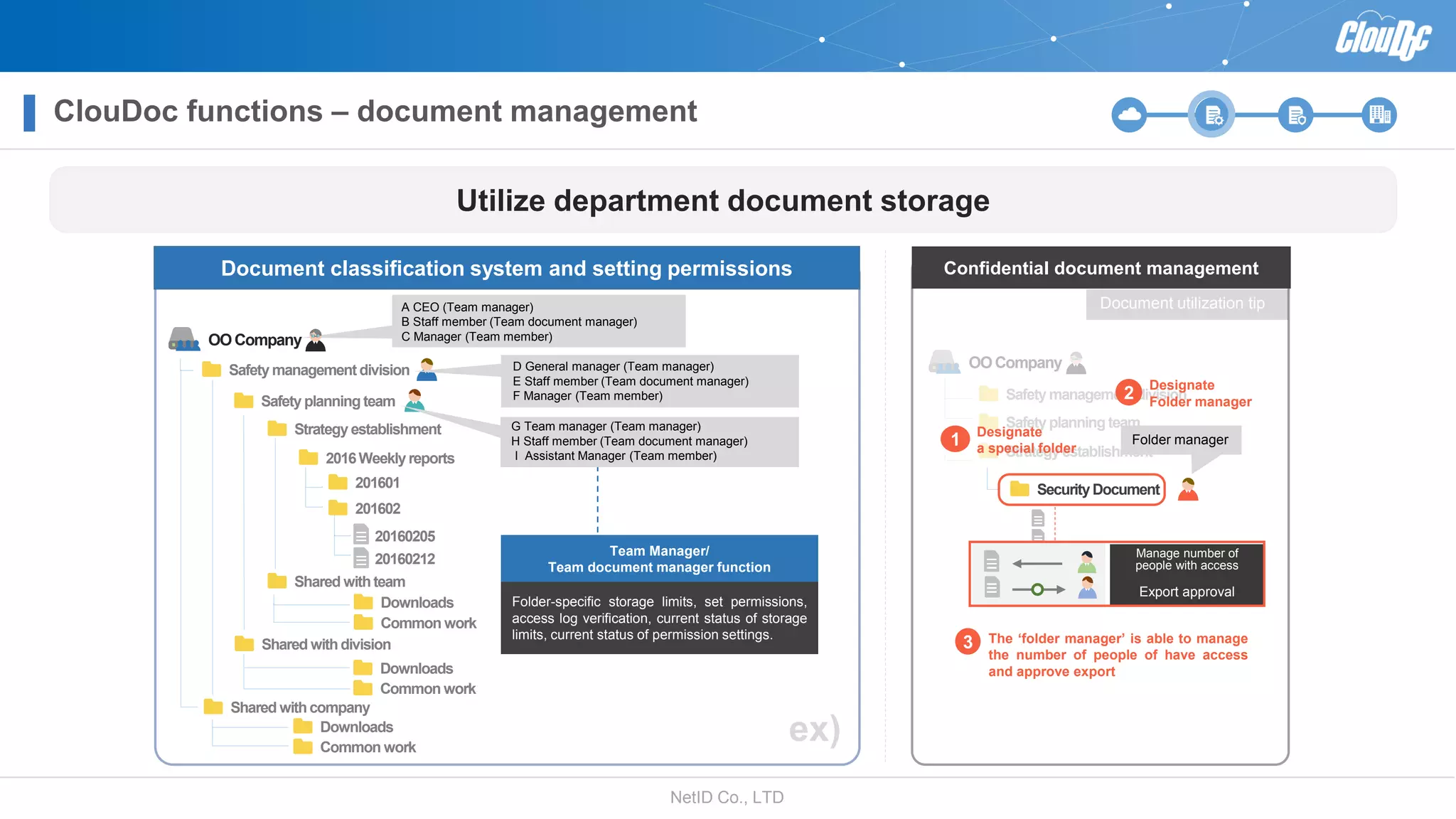
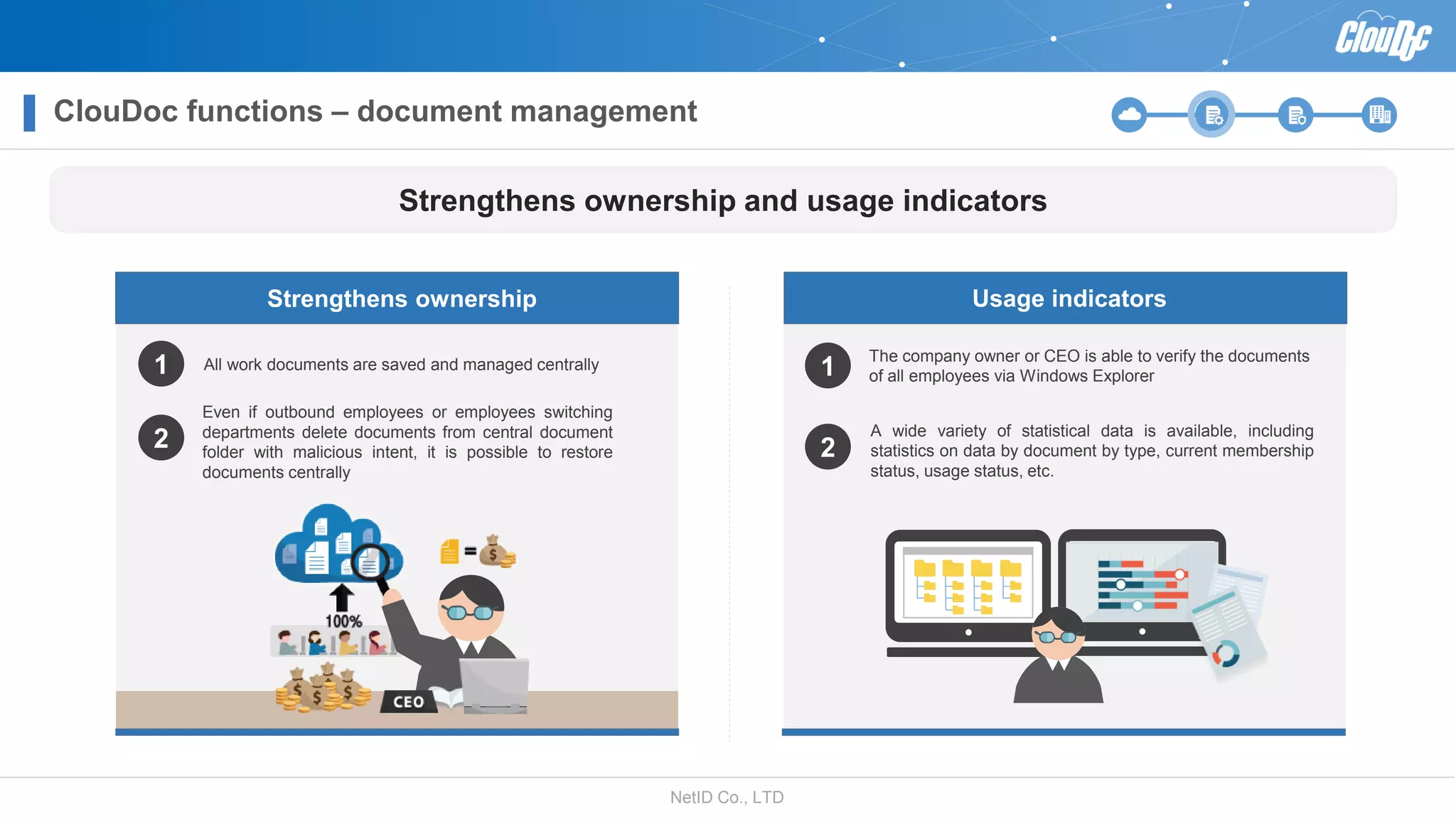
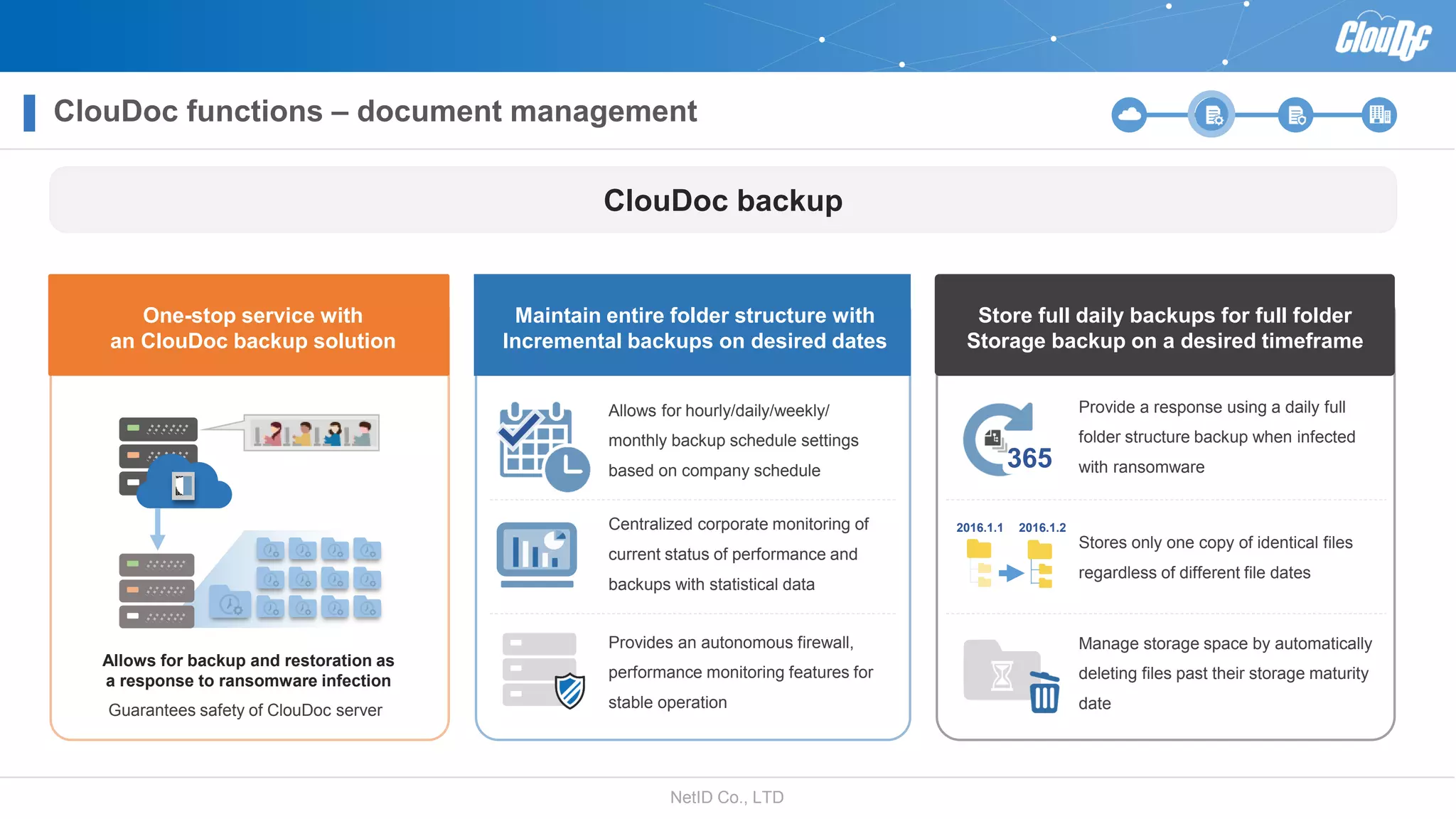
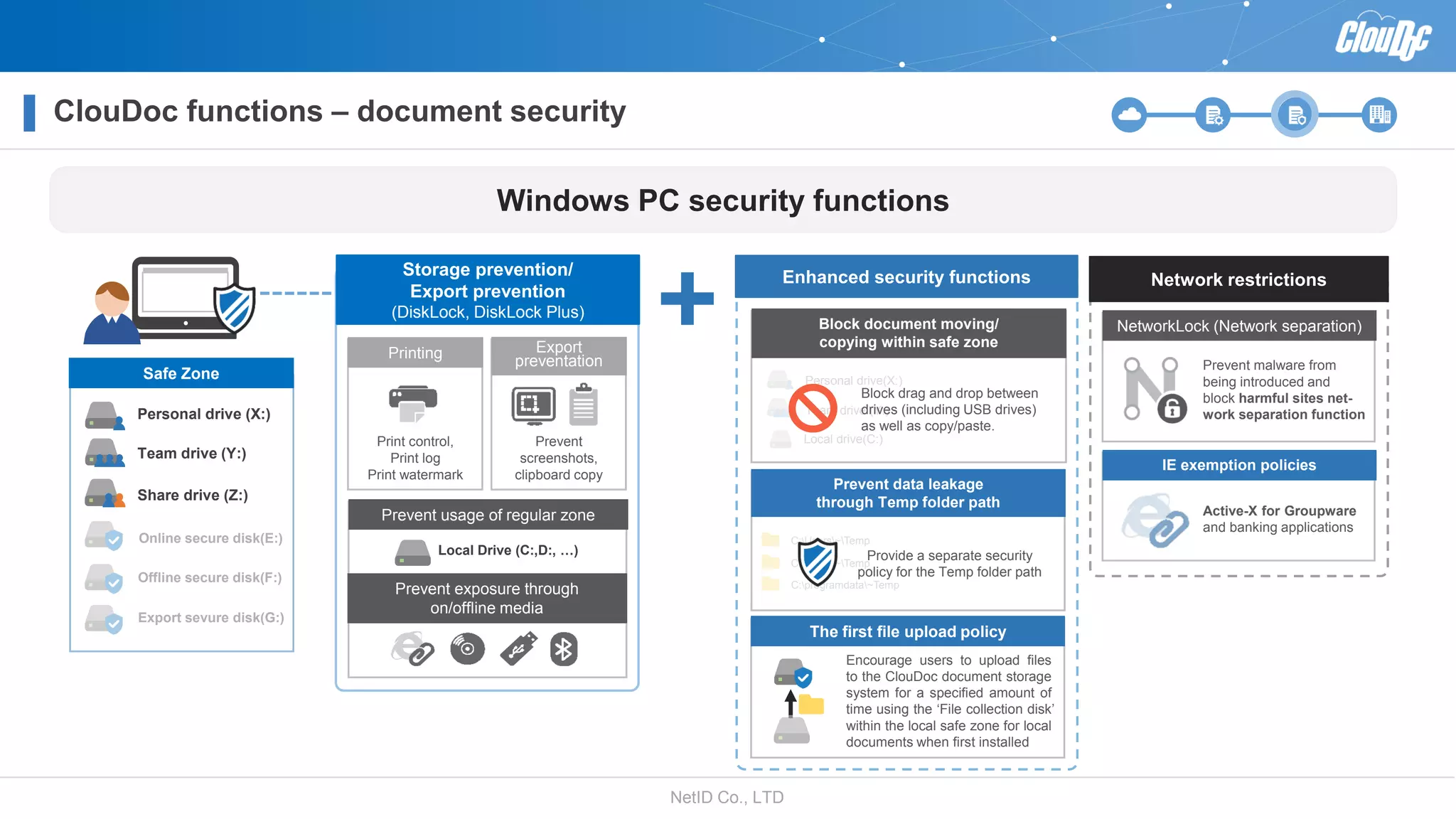
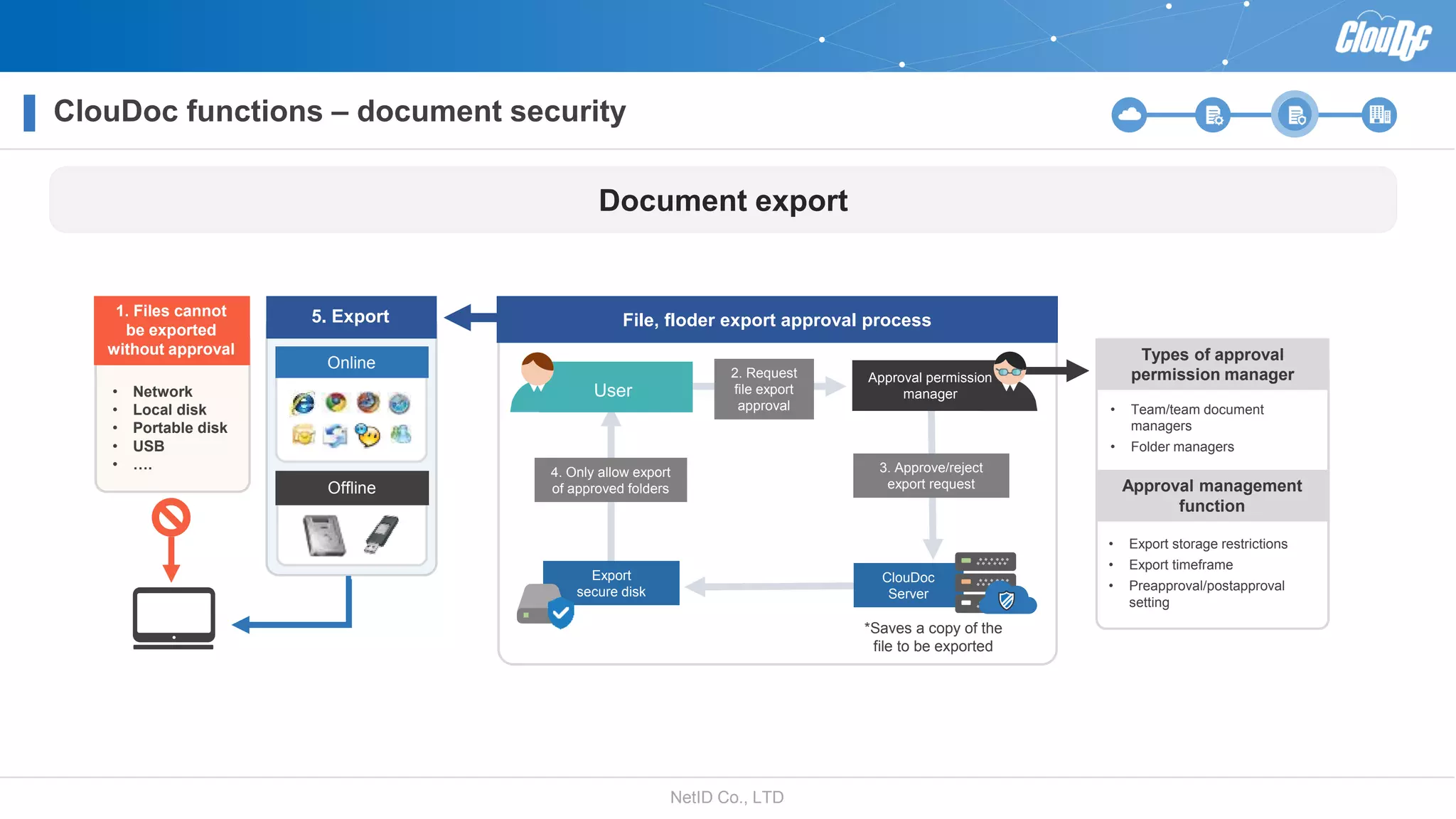
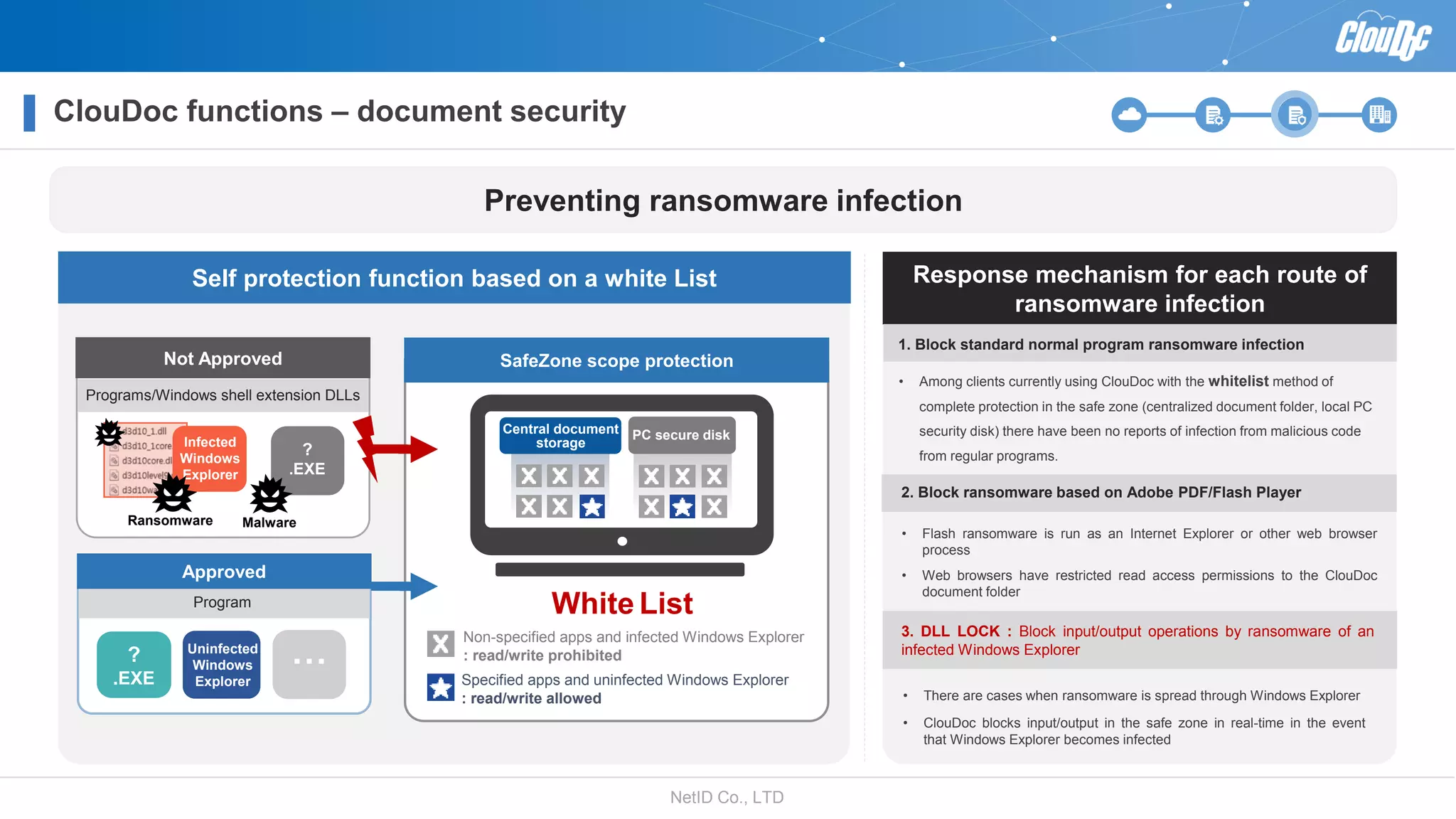
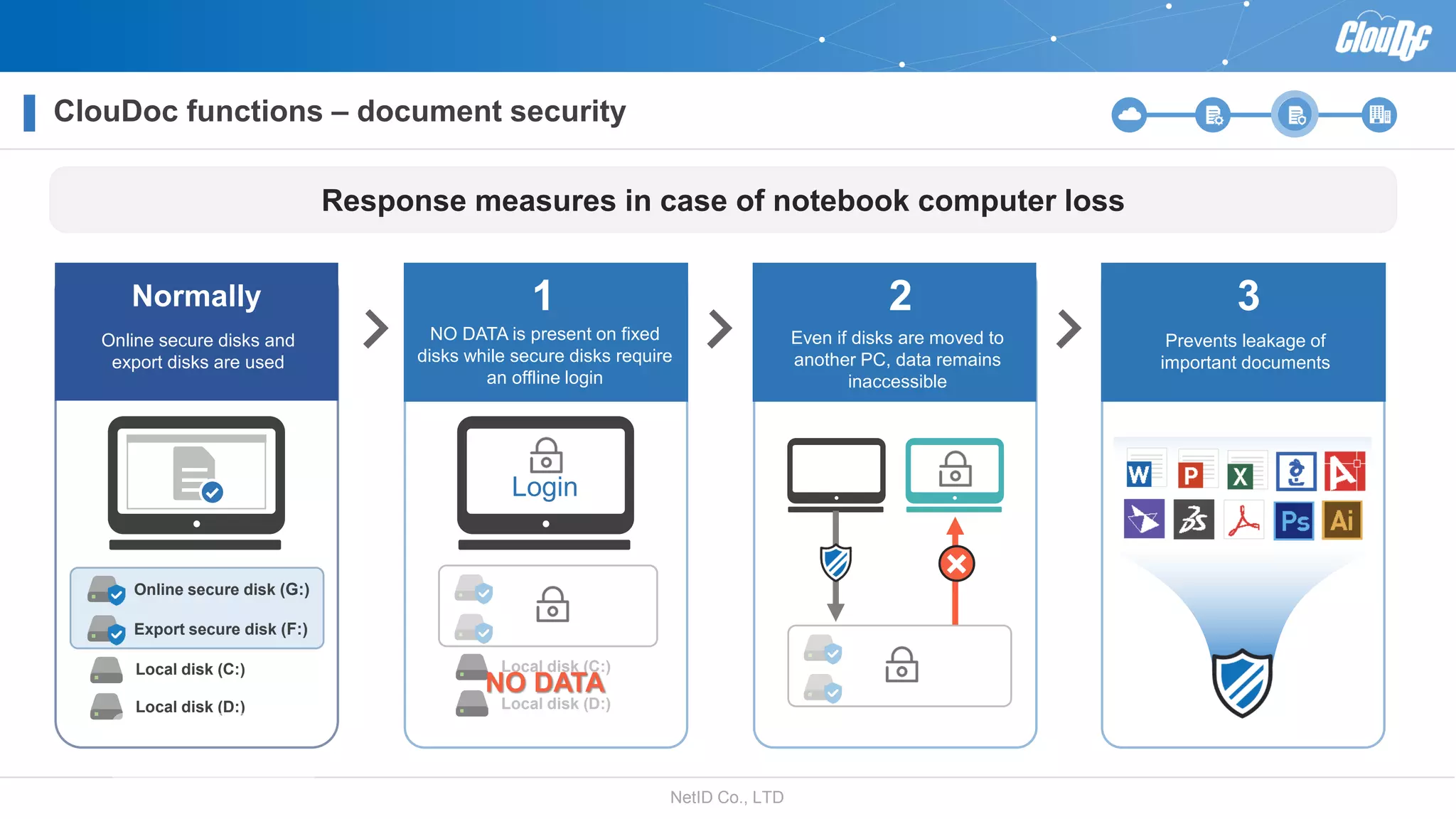
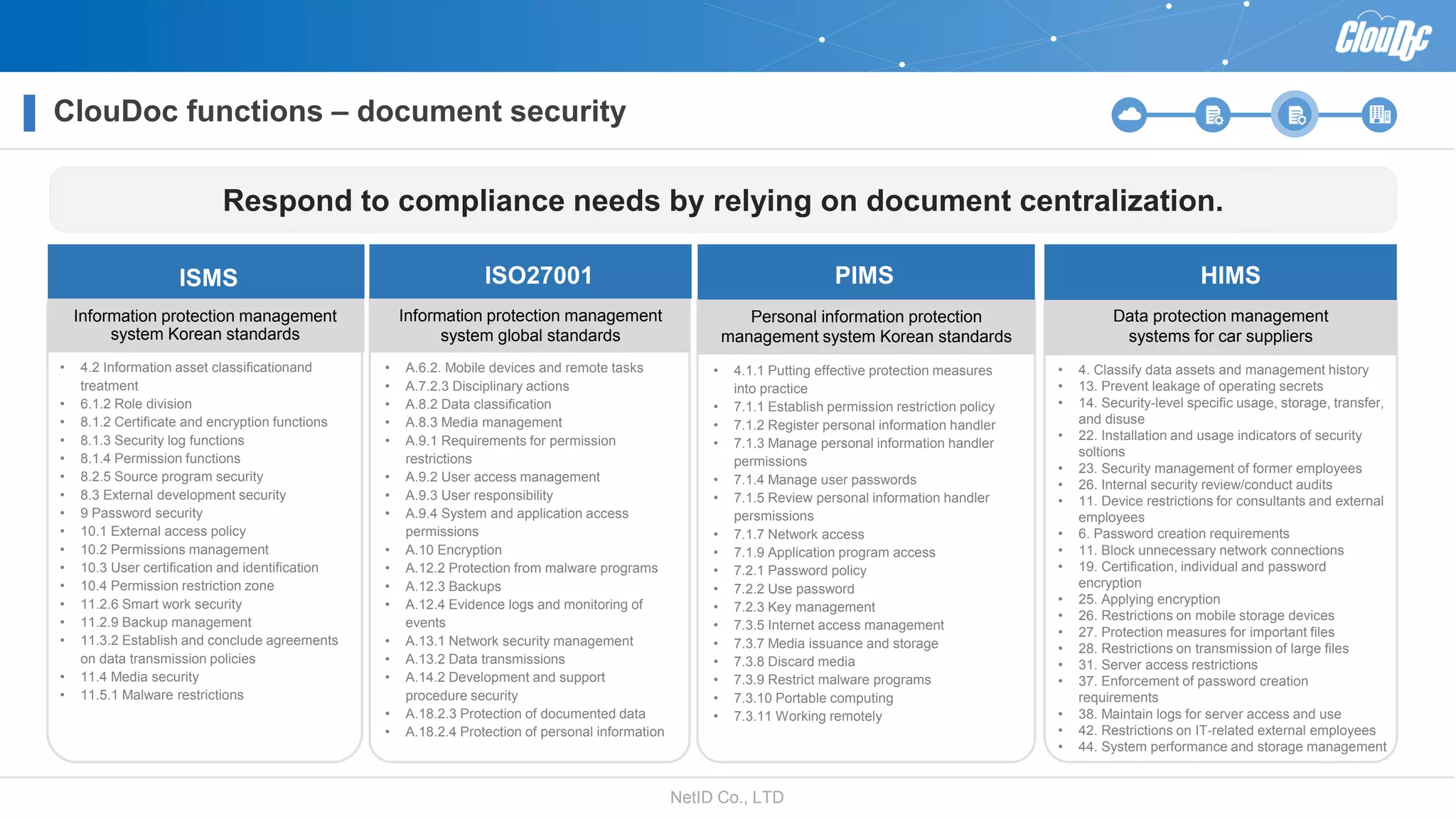
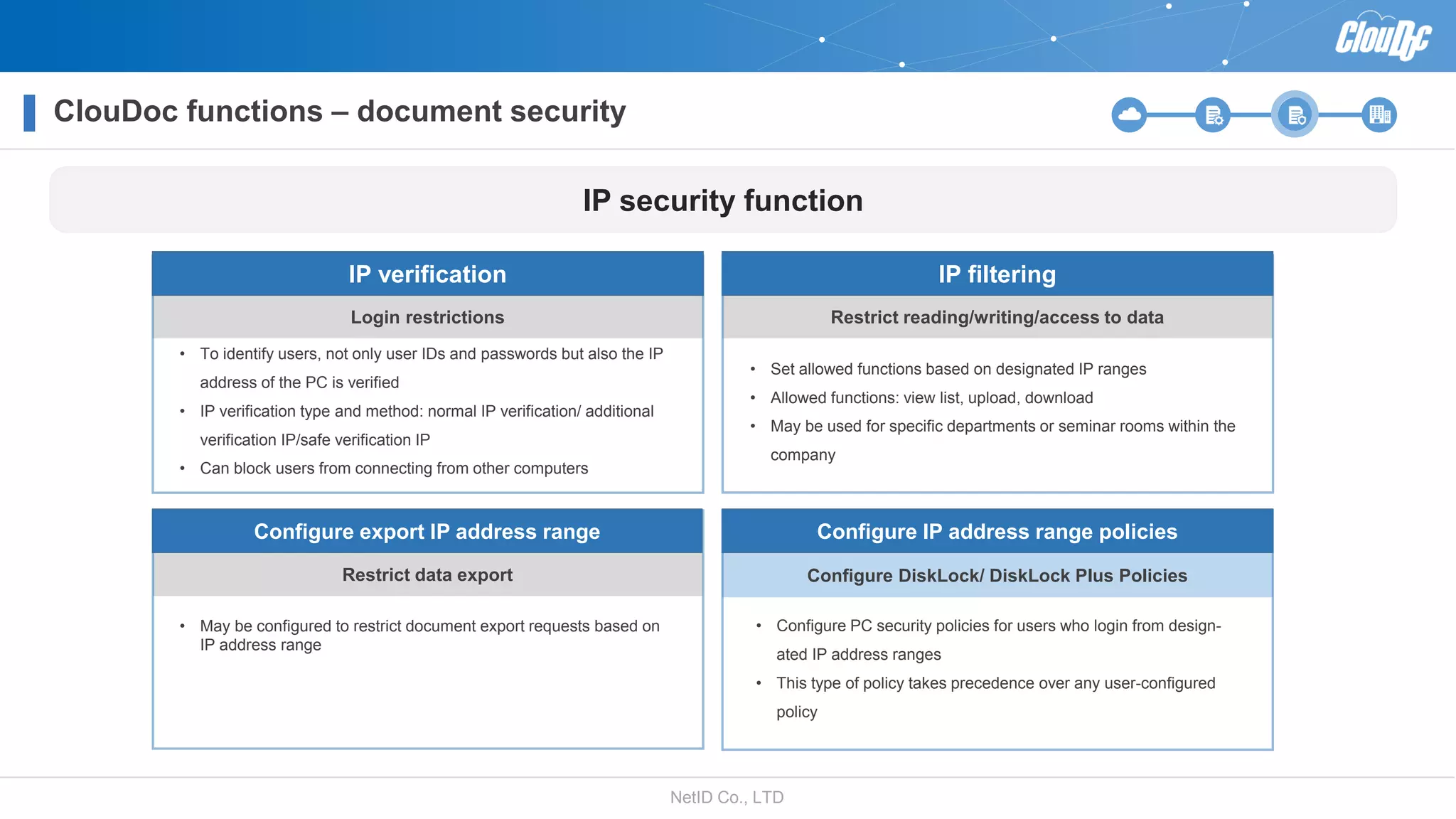
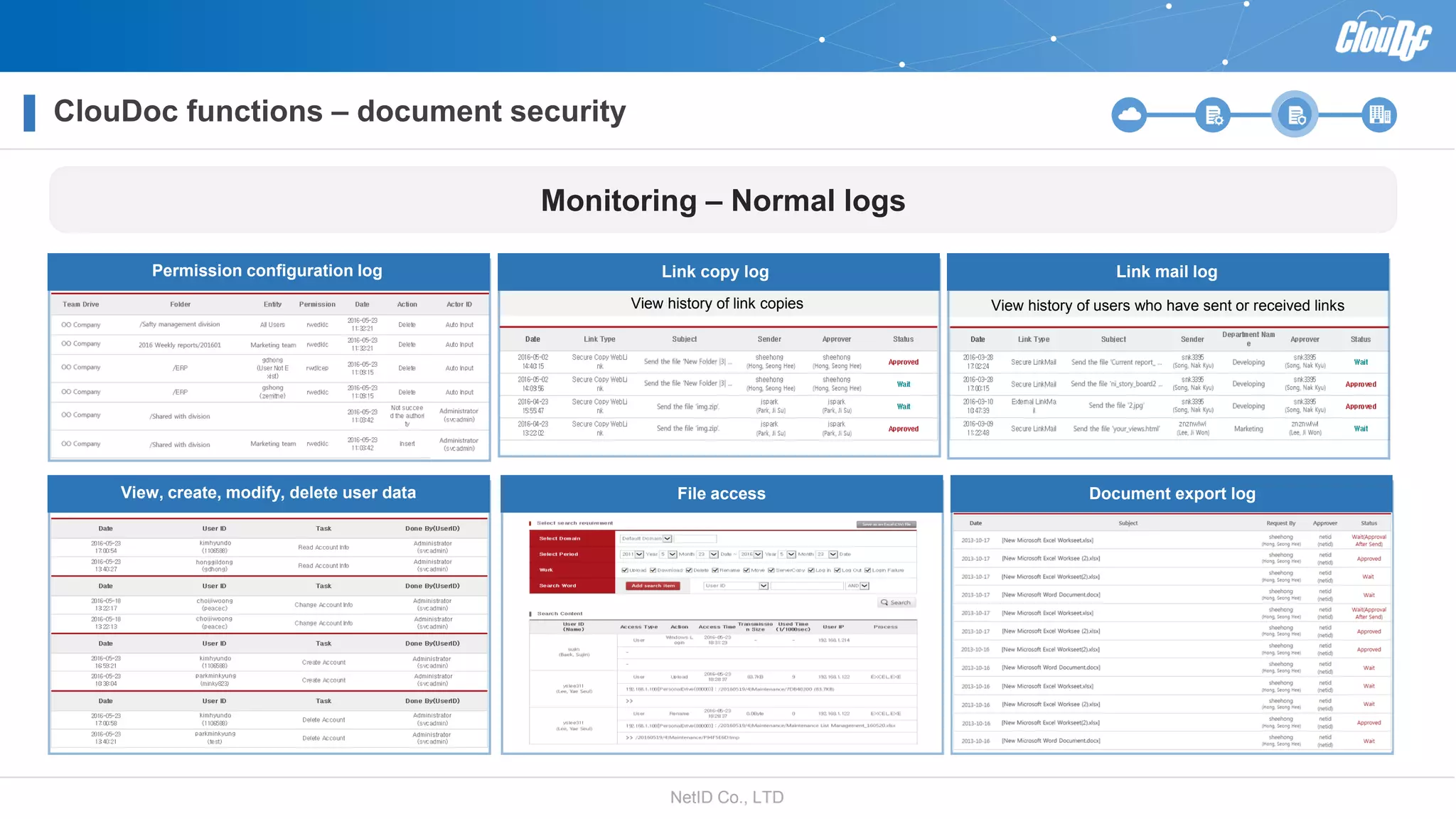
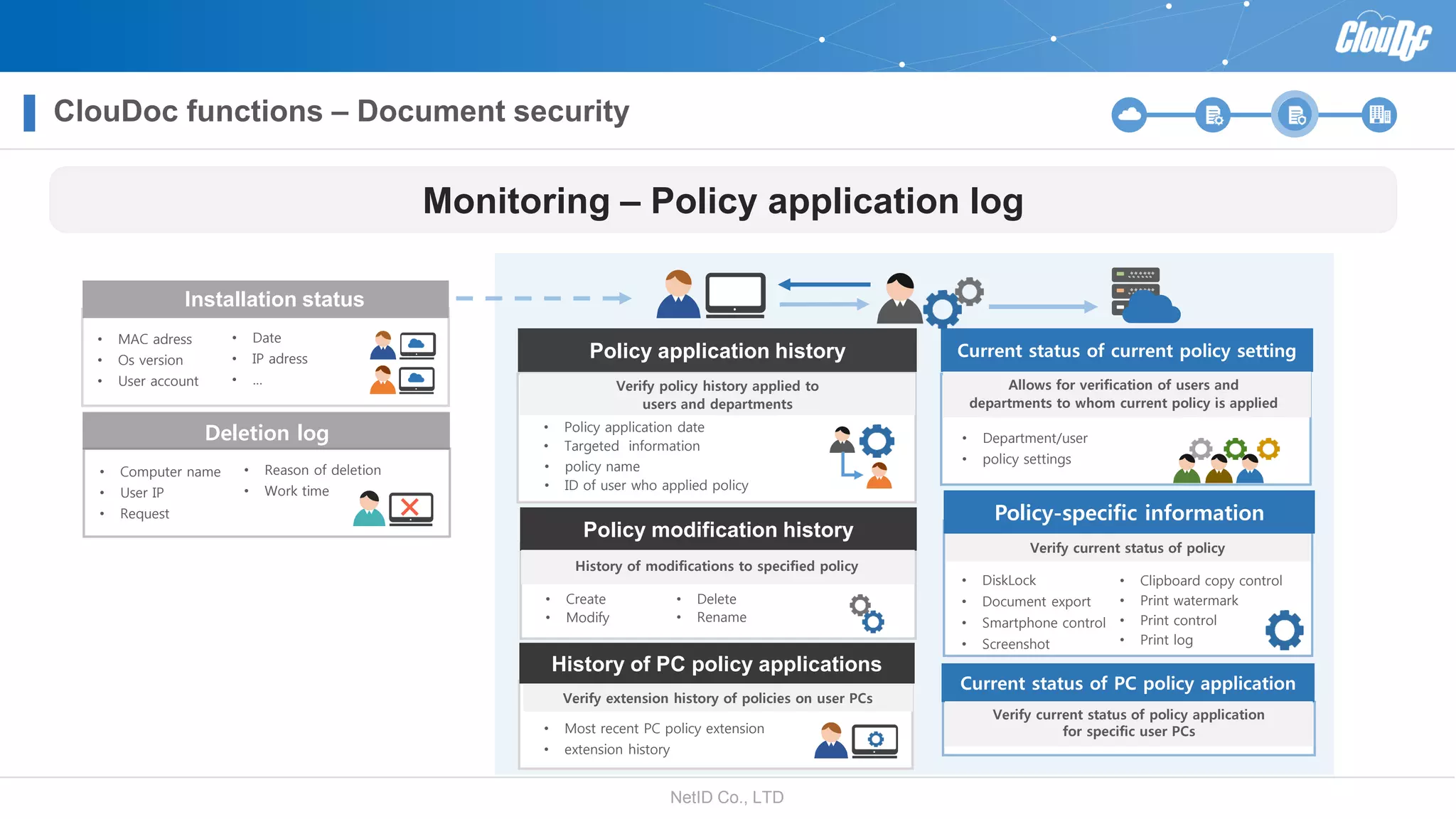
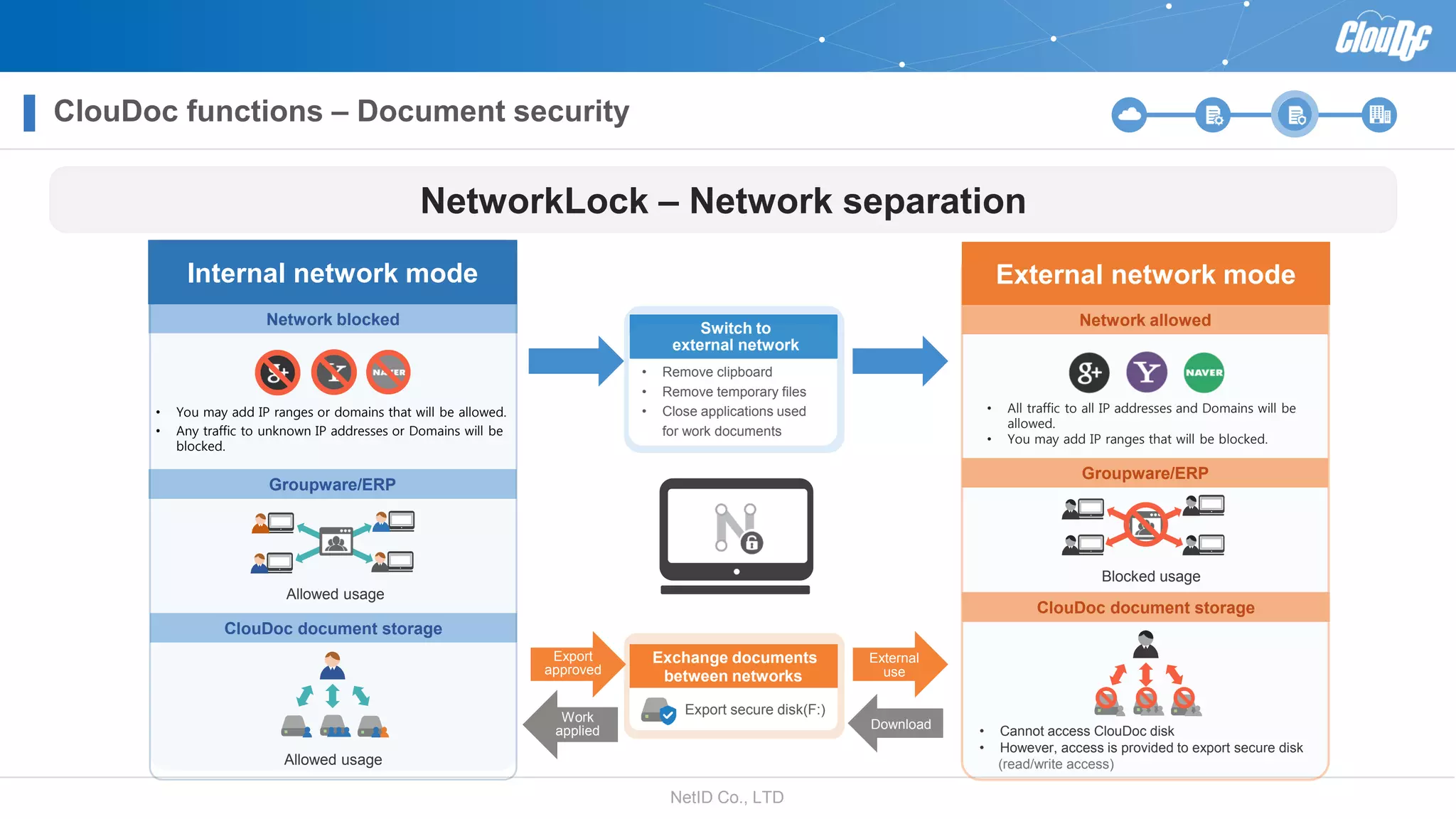
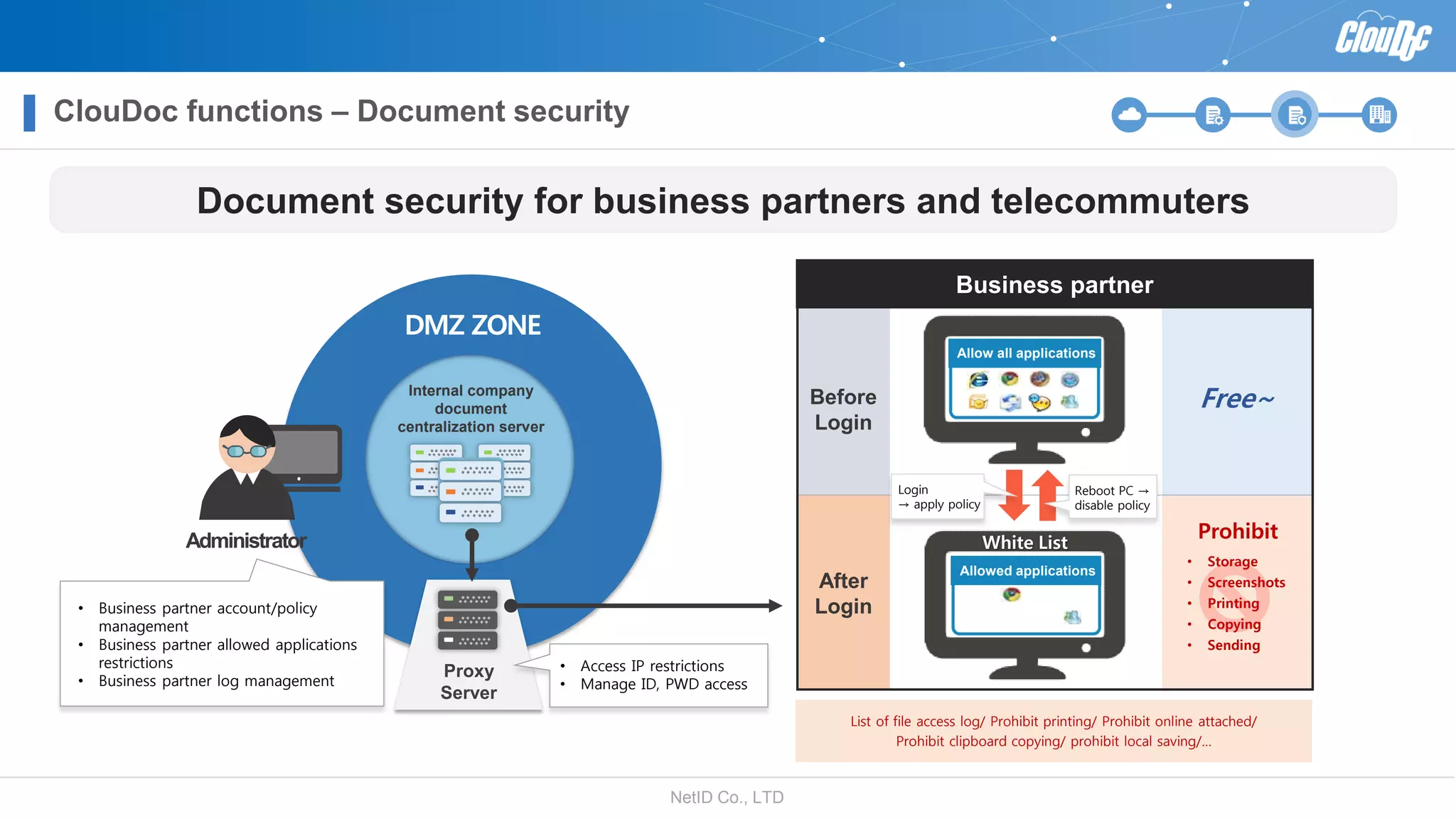
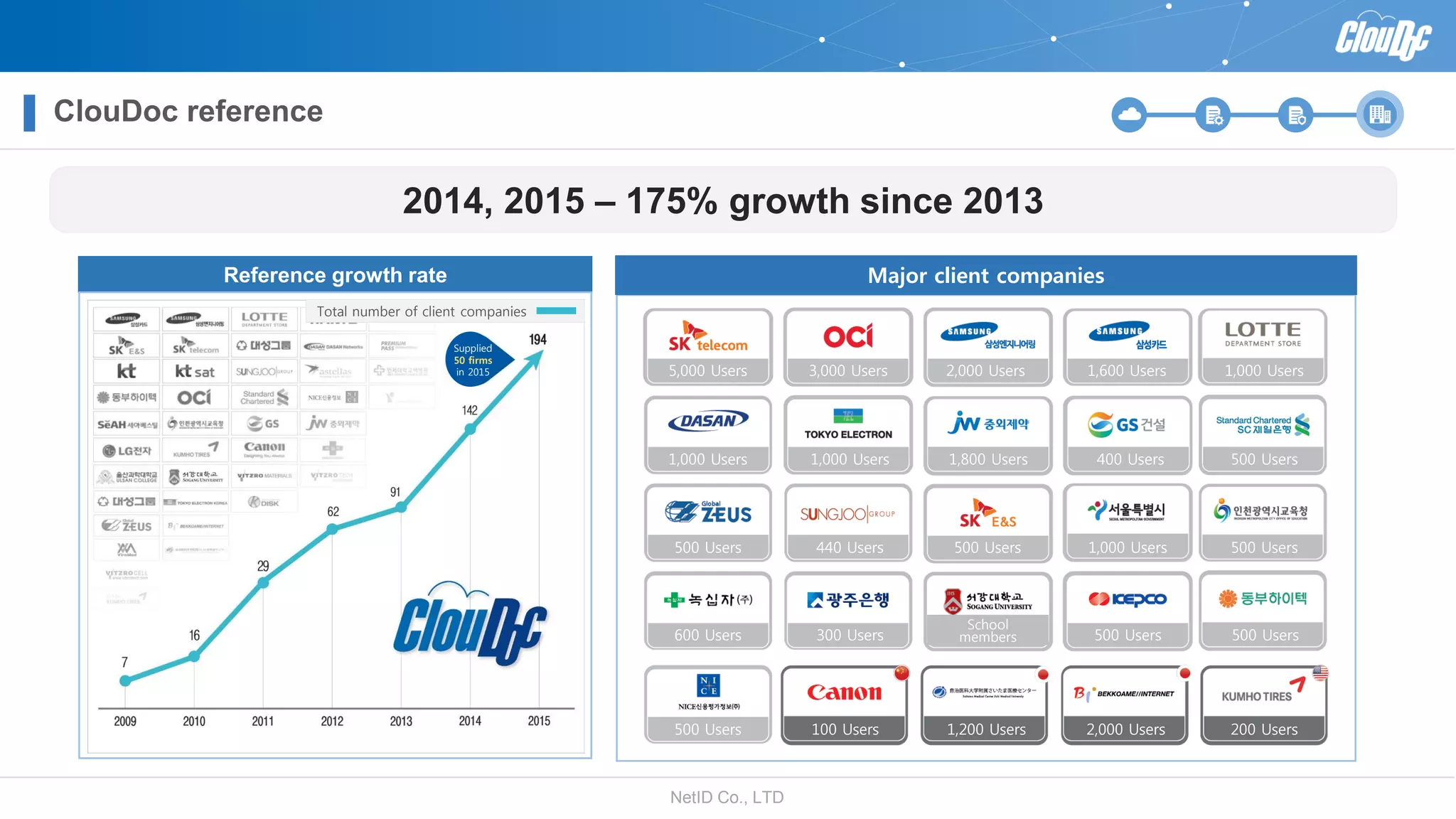
NetID Co. Ltd. presents its document centralization solution, Cloudoc, aimed at addressing shortcomings in traditional document management and security systems suited for the cloud/mobile era. The solution provides tools for effective document management, compliance readiness, and enhanced security features tailored to contemporary workplace needs. Key functionalities include version management, user access controls, and a secure platform for efficient document sharing and storage.