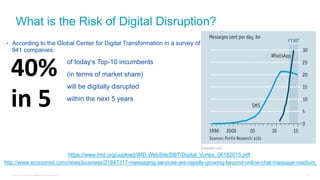
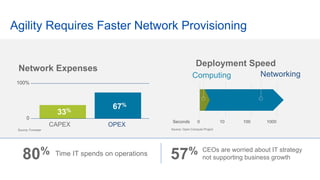
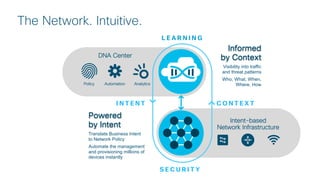
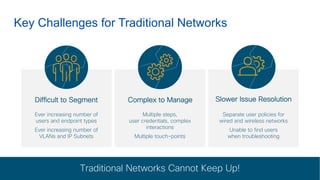
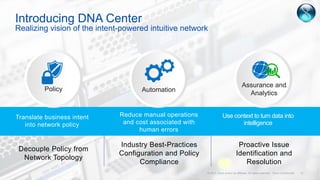
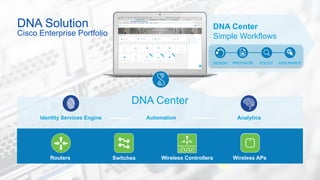
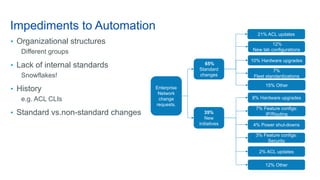
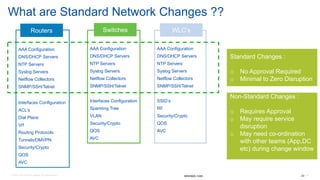
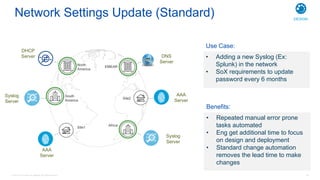
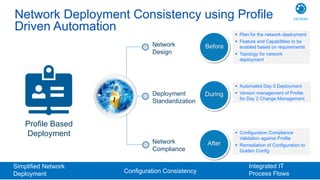
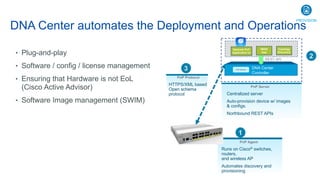
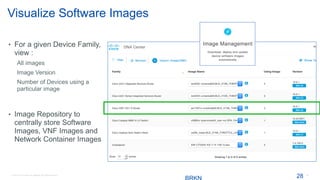
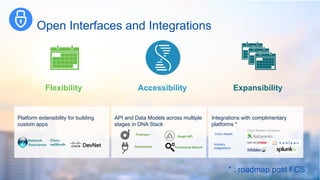
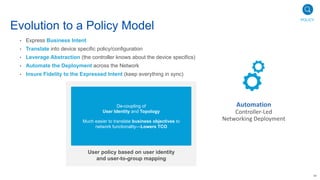
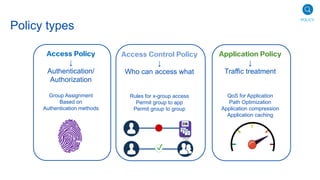
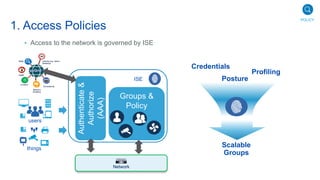
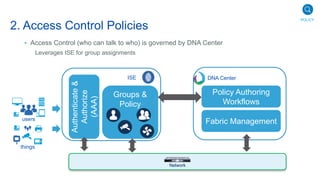
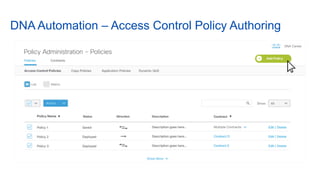
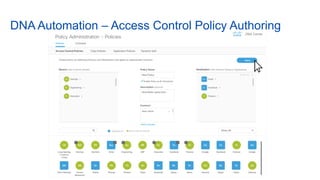
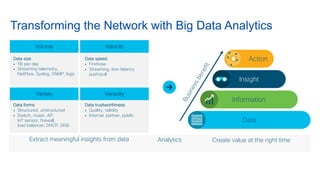
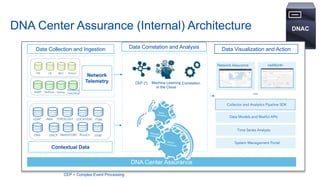
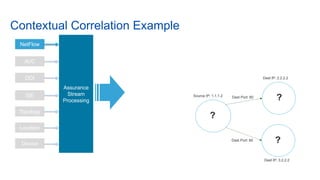
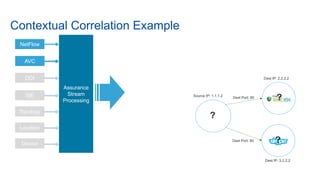
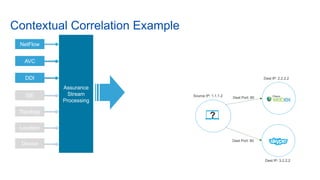
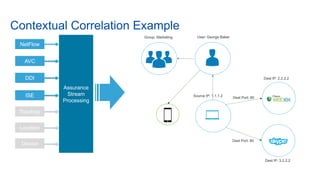
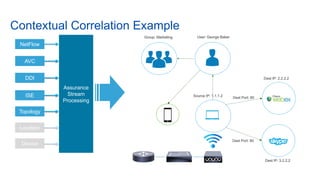
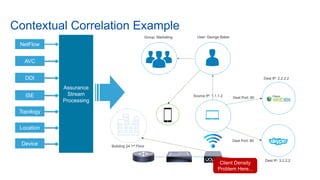
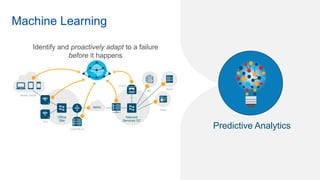
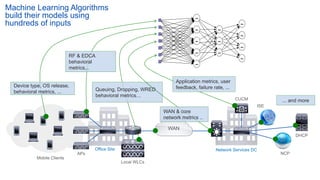
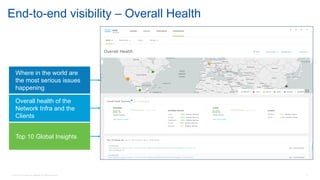
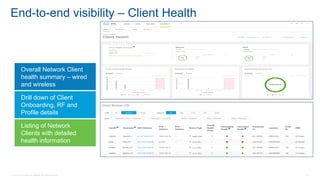
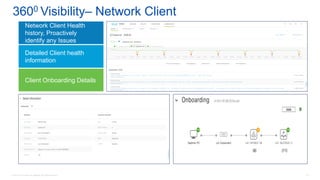
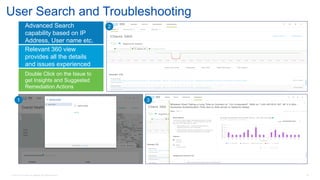
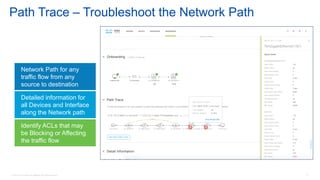
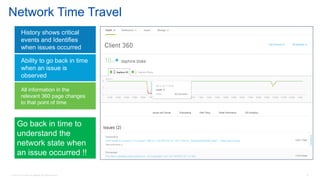
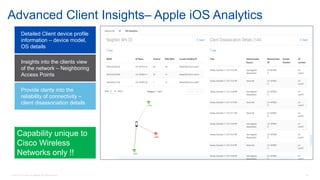
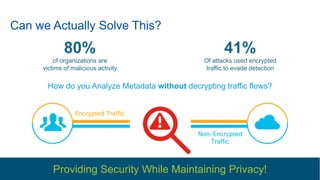
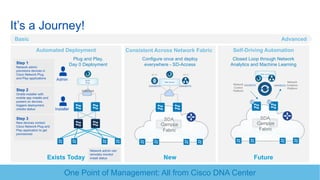
Cisco's Digital Network Architecture (DNA) offers a new holistic approach to meet the requirements of the digitized enterprise. DNA Center provides new automation, analytics, and assurance capabilities including a GUI, automated workflows, and insights to simplify operations. The session introduces DNA's approach to translating business intent into network policies through automation and using context to gain intelligence from network data.