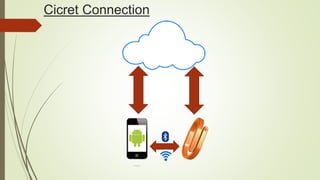
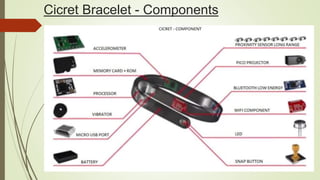
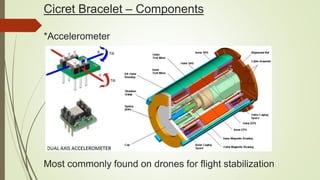
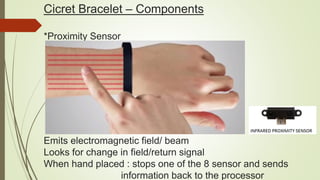
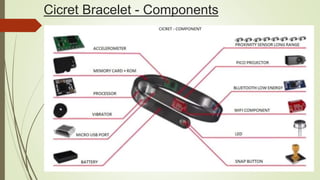
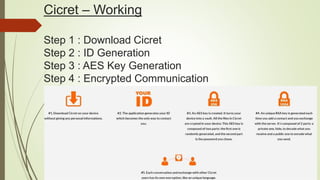
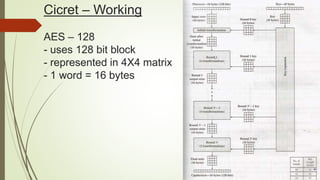
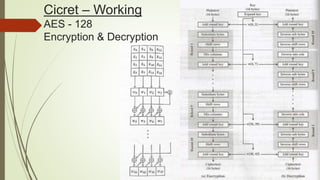
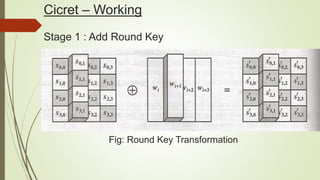
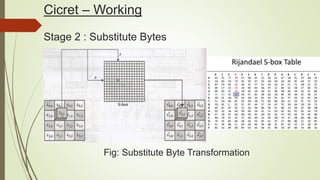
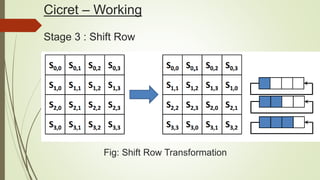
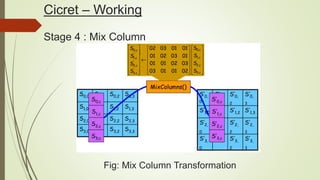
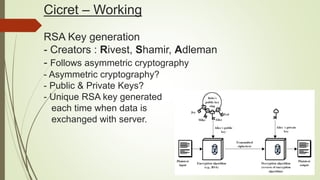
Cicret is an innovative product combining a mobile app and a bracelet that transforms the skin into a touchscreen, enabling features like messaging, music playback, and call answering. It employs advanced AES-256 encryption for secure communications and incorporates components such as an accelerometer, micro USB port, proximity sensor, and pico projector. This project, developed by Pranav Misra, aims to enhance user control and data privacy.










![[ Links ]
www.cicret.com
https://www.youtube.com/watch?v=9J7GpVQCfms](https://image.slidesharecdn.com/cicret-ppt-151121040934-lva1-app6892/85/Cicret-PPT-25-320.jpg)
