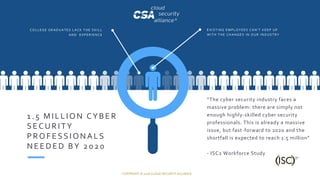
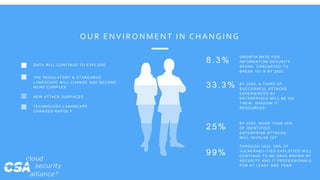
The document discusses the Cloud Security Alliance's (CSA) research activities. It notes that CSA has produced over 165 research artifacts through 34 active working groups. It highlights some of CSA's 2018 research releases and lists CSA's active and dormant working groups. The document promotes connecting with CSA and learning more about their research through various online resources.