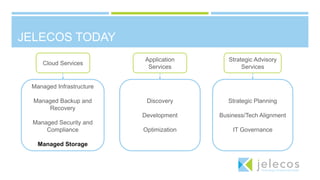
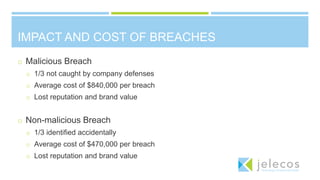
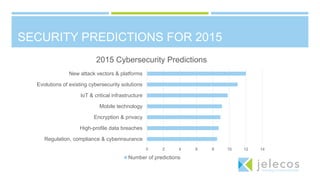
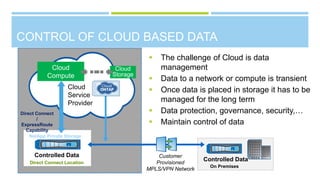
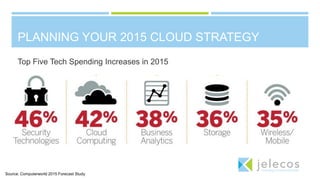
The document summarizes a CIO forum on security, compliance, and cloud computing. It discusses Jelecos cloud and managed services, changing compliance landscapes like PCI DSS 3.0, and the evolution of hybrid clouds and compliance. It also covers topics like data breaches, security predictions for 2015, planning cloud strategies, and ensuring data protection and compliance in hybrid clouds and with emerging technologies like IoT.