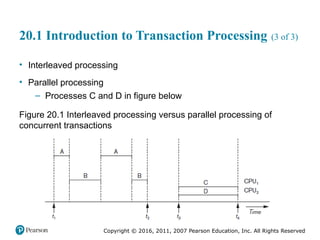
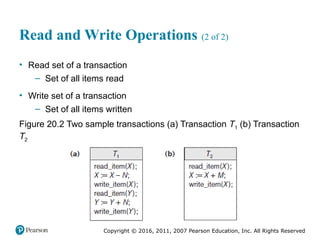
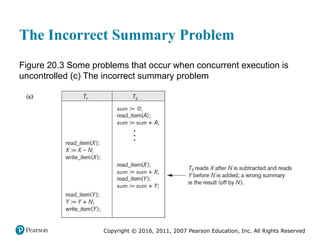
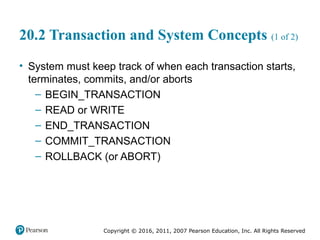
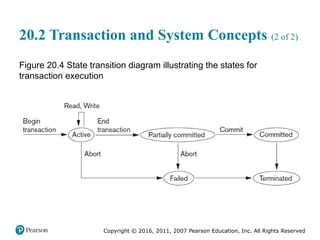
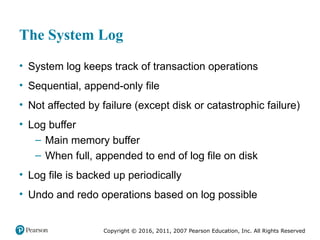
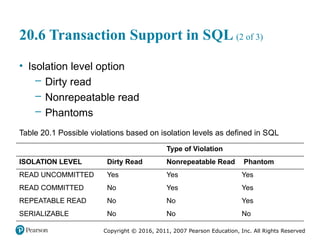
Chapter 20 of 'Fundamentals of Database Systems' explores transaction processing concepts essential for managing large databases with concurrent users. It covers transaction characteristics, concurrency control methods, and the need for reliable recovery mechanisms. Additionally, the chapter discusses ACID properties, different scheduling and isolation levels, and SQL transaction support.