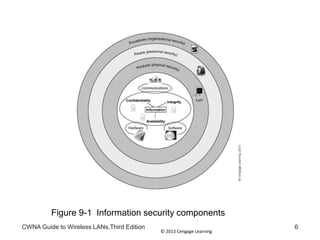
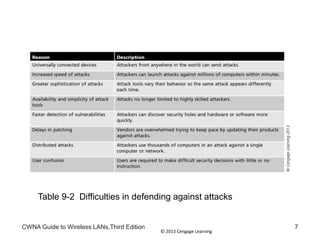
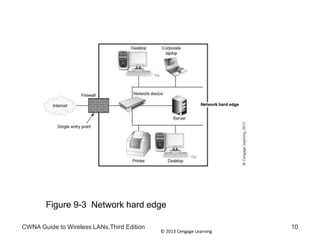
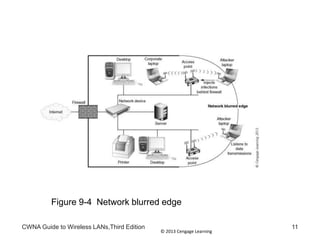
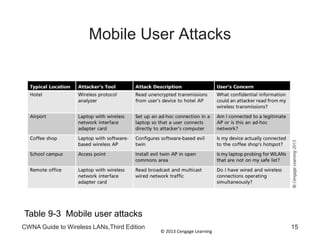
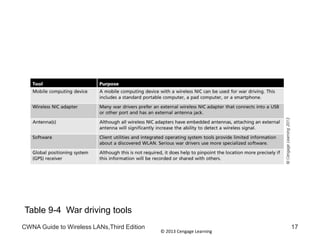
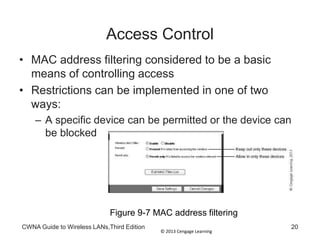
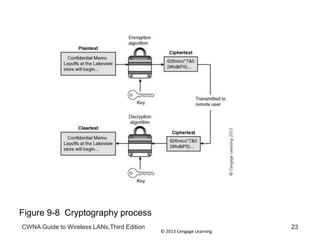
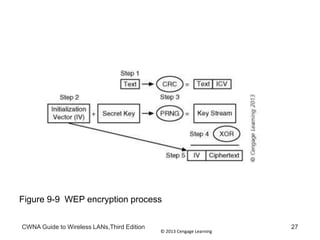
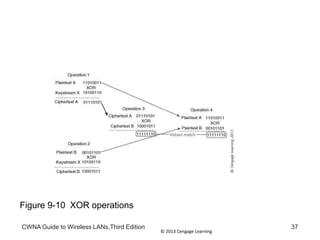
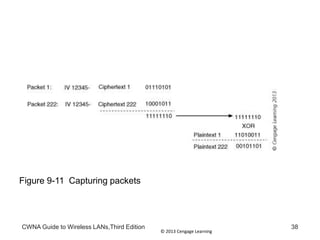
The document discusses security vulnerabilities in wireless LANs. It describes how wireless LANs blur the defined network edge and introduce new attack vectors. It also summarizes different types of wireless attacks against enterprises, mobile users, and home networks. Finally, it discusses vulnerabilities in the legacy IEEE 802.11 security protections including weaknesses in authentication, address filtering, and the Wired Equivalent Privacy (WEP) encryption protocol.