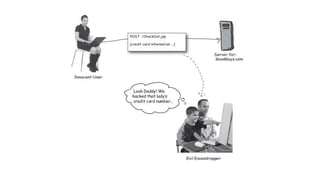
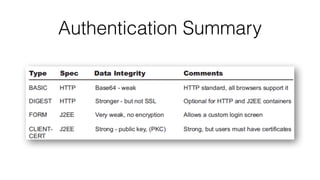
This document discusses security topics related to application programming interfaces (APIs), including authentication, authorization, and protecting data. It covers basic types of authentication like declarative, programmatic, and informative authentication. It also discusses defining roles and resource constraints for authentication and authorization. The document stresses the importance of securing code and concentrating on authentication. It provides examples of container-specific authentication and discusses protecting requested data by using HTTPS.