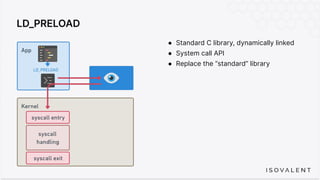
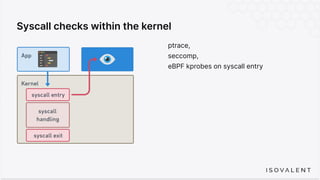
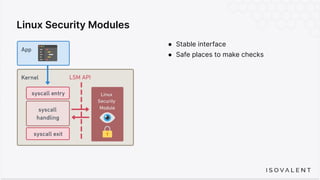
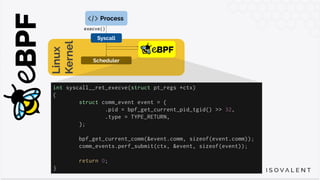
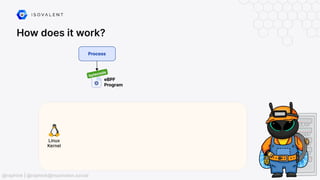
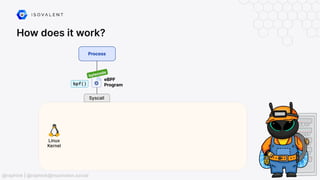
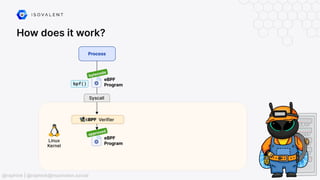
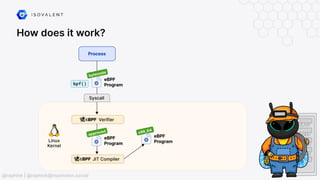
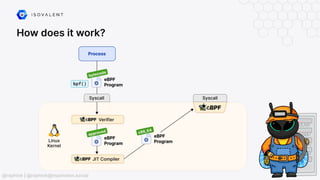
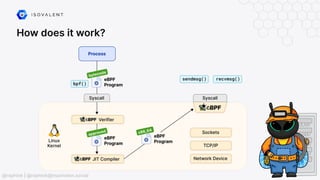
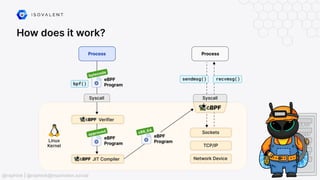
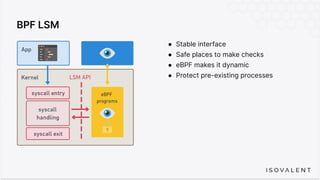
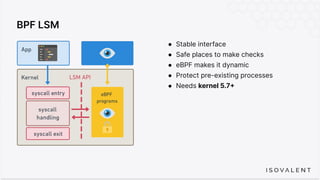
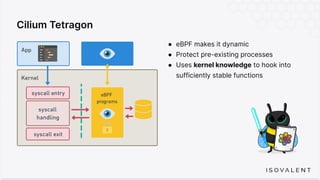
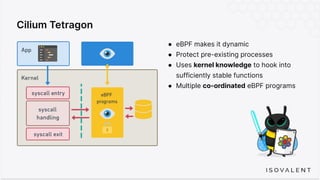
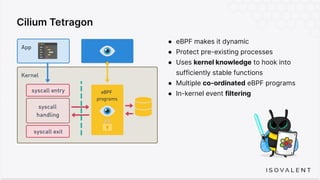
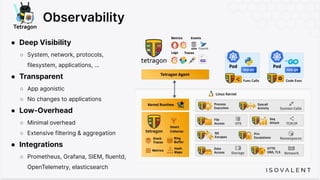
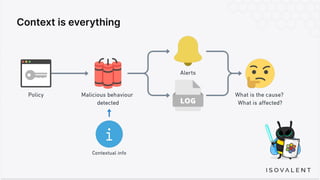
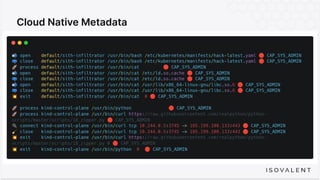
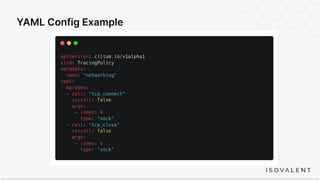
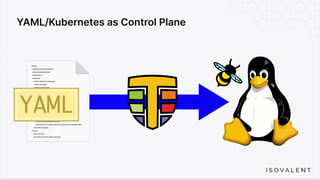
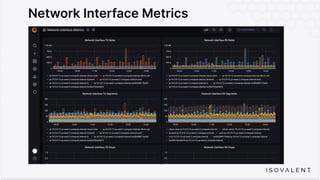
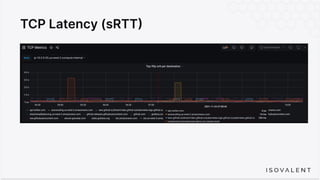
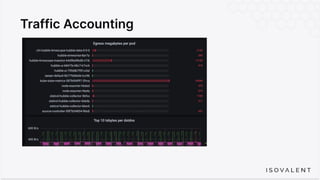
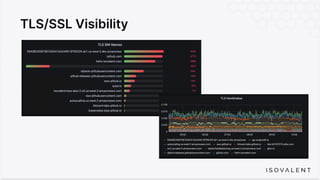
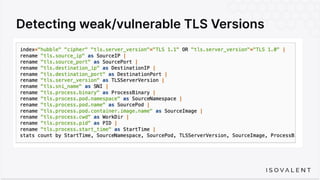
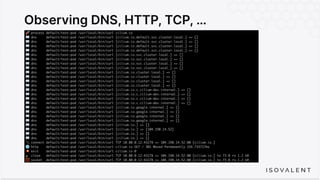
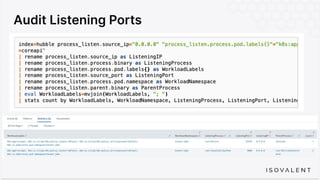
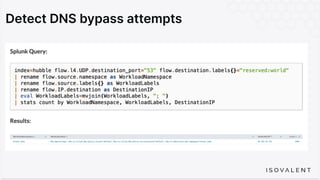
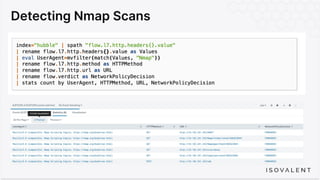
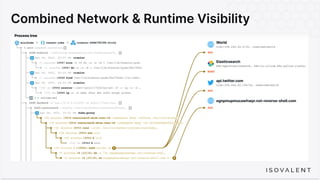
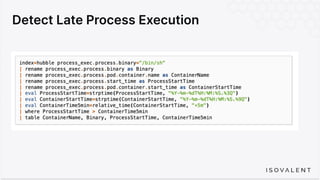
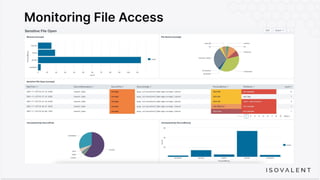
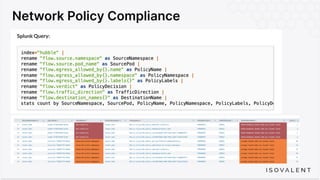
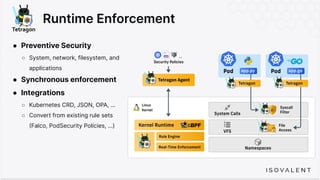
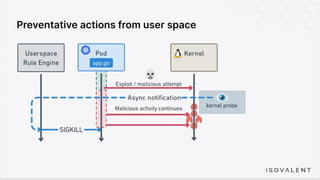
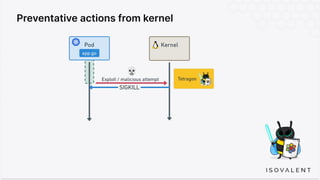
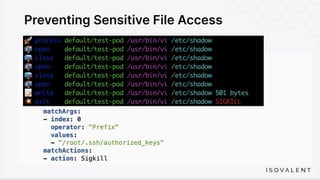
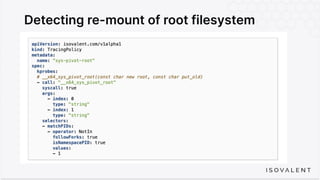
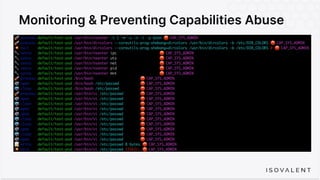
The document discusses eBPF-based security observability and runtime enforcement using Cilium Tetragon, focusing on real-time detection and prevention of malicious activities in cloud-native environments. It outlines various technical techniques and integrations for monitoring system calls, network traffic, and file access while ensuring minimal overhead and high visibility. Additionally, it emphasizes the dynamic and preventive nature of security measures that can be implemented using Cilium Tetragon in Kubernetes and other platforms.