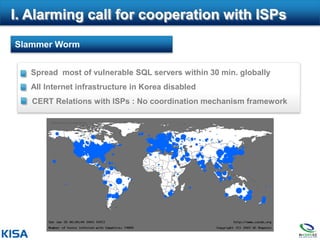
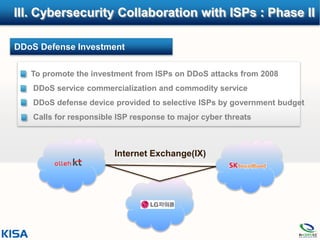
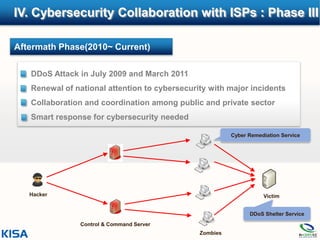
1. The document outlines Korea's efforts to enhance cybersecurity collaboration with ISPs over four phases from 2003 to the present.
2. In the initial phase, laws were amended and mechanisms for threat information sharing and emergency response were established between KrCERT/CC and ISPs.
3. Subsequent phases focused on stabilizing collaboration, implementing botnet response actions, and investing in DDoS defense.
4. Recent efforts have included a DDoS shelter service, joint voluntary projects, and high-level attention to cybersecurity issues.