This document is a Persian translation of a CCNA lab manual. It contains an introduction chapter about familiarizing with CCNA labs. It then has several chapters on basic router and switch management, and basic security configurations on Cisco devices. Each chapter contains multiple lab exercises with step-by-step instructions on topics like password recovery, IOS upgrades, interface configurations, access lists, AAA authentication, SSH, syslog server connections, and more.









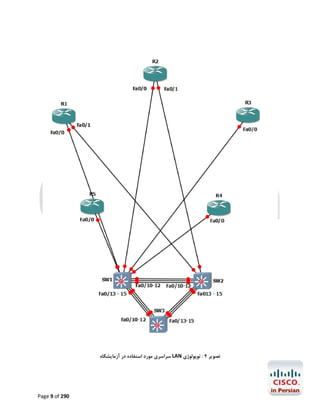




















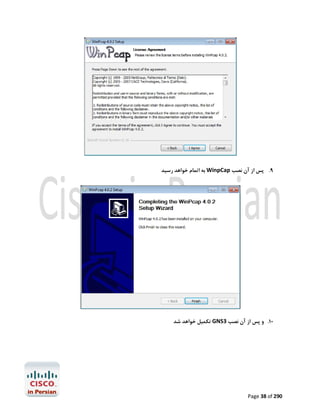
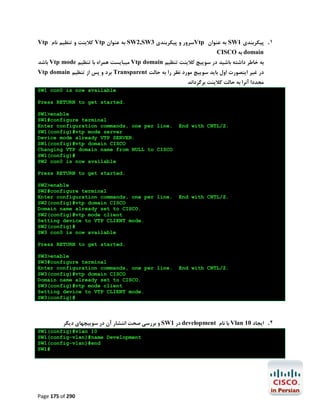
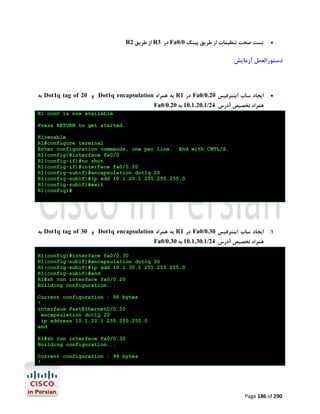
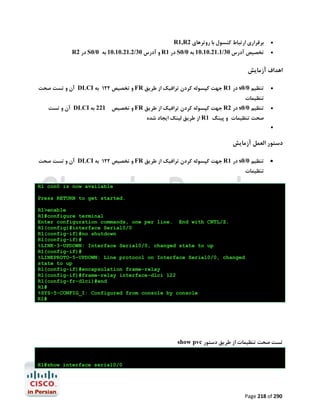
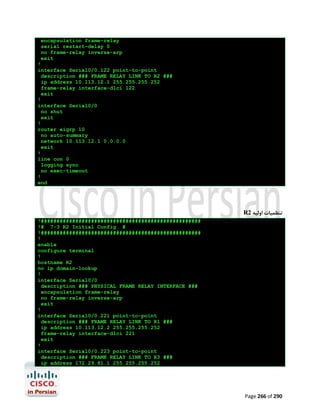
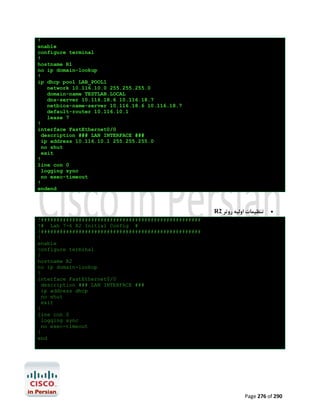
![ ﺑﻪ اﮐﺴﺲ ﺳﺮورHostname ﺗﺨﺼﯿﺺ
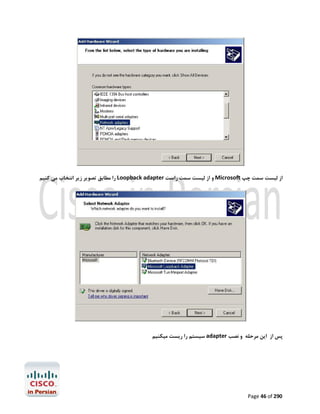
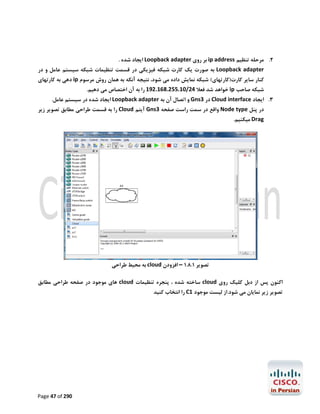
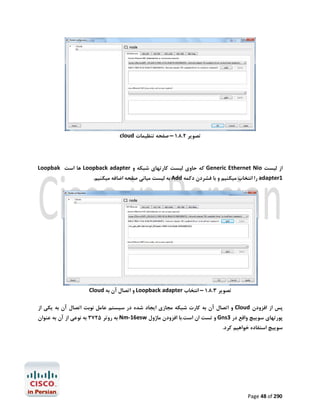
Router>enable
Router#configure terminal
Enter configuration commands, one per
line.
End with CNTL/Z
Router(config)#hostname Access_Server
Access_Server(config)#
از ﺳﻤﺖ آن ﺑﻪ ﺳﺎﯾﺮ ادواتTelnet اﯾﺠﺎد ﯾﮏ ﻟﻮپ ﺑﮏ اﯾﻨﺘﺮﻓﯿﺲ ﺟﻬﺖ ﺑﺮﻗﺮاري
Access_Server(config)#interface loopback 0
Access_Server(config-if)#ip address 10.10.10.10 255.255.255.255
Access_Server(config-if)#exit
Access_Server(config)#
Async ﻣﻌﮑﻮس روي ﺧﻄﻮطTelnet ﺟﻬﺖ ﺑﺮﻗﺮاري ارﺗﺒﺎط ﻫﺎيIP Host ﺗﻨﻈﯿﻢ ﺟﺪول
Access_Server(config)#ip
Access_Server(config)#ip
Access_Server(config)#ip
Access_Server(config)#ip
Access_Server(config)#ip
Access_Server(config)#ip
Access_Server(config)#ip
Access_Server(config)#ip
Access_Server(config)#ip
host
host
host
host
host
host
host
host
host
r1 2001 10.10.10.10
r2 2002 10.10.10.10
r3 2003 10.10.10.10
r4 2004 10.10.10.10
r5 2005 10.10.10.10
r6 2006 10.10.10.10
sw1 2007 10.10.10.10
sw2 2008 10.10.10.10
sw3 2009 10.10.10.10
ﺑﺎ اﮐﺴﺲ ﺳﺮورExec session ﺑﻬﻢ ﻣﻨﻈﻮر ﺟﻠﻮﮔﯿﺮي از اﯾﺠﺎدAsync ﺗﻨﻈﯿﻢ ﺧﻄﻮط
Access_Server(config)#line 1 16
Access_Server(config-line)#no exec
async روي ﺧﻄﻮطTelnet ﻓﻌﺎل ﮐﺮدن ﻗﺎﺑﻠﯿﺖ
Access_Server(config-line)#transport input telnet
ﭘﺲ از ﮐﺎﻧﻔﯿﮓ دﺳﺘﮕﺎه ﺗﮏ ﺗﮏ ﺧﻄﻮط اﻧﺮا ﺟﻬﺖ ﺣﺼﻮل اﻃﻤﯿﻨﺎن از ﺻﺤﺖ اﻣﮑﺎن ﺑﺮﻗﺮاري ﺗﻤﺎس آن ﺑﺎ ادوات ﻣﺘﻨﺎﻇﺮ
.ﺗﺴﺖ ﻣﯿﮑﻨﯿﻢ
Access_Server#r1
Trying r1 (10.10.10.10, 2037)… Open
% Please answer ‘yes’ or ‘no’.
Would you like to enter the initial configuration dialog? [yes/no]:
Page 32 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-33-320.jpg)















![روﺗﺮ را روﺷﻦ ﻣﯿﮑﻨﯿﻢ ﺗﺎ ﻓﺮاﯾﻨﺪ ﺑﻮت آﻏﺎز ﺷﻮد ، در اﯾﻦ ﺣﯿﻦ ﻧﯿﺎز اﺳﺖ ﺗﺎ ﻓﺮاﯾﻨﺪ ﺑﻮت ﺑﻪ ﺻﻮرت ﻧﺮﻣﺎل ﻣﺘﻮﻗﻒ
.1
اﻧﺠﺎم ﻣﯽ دﻫﯿﻢ ﺗﺎ ﺑﻪCtrl+Puse Breake ﺑﺎﻻ ﺑﯿﺎﯾﺪ ، اﯾﻨﮑﺎر را ﻓﺸﺮدن ﻣﮑﺮرbootrom ﺷﻮد و روﺗﺮ ﺑﺎ
. وارد ﺷﻮﯾﻢbootrom ﻣﺤﯿﻂ
System Bootstrap, Version 11.0(10c), SOFTWARE
Copyright (c) 1986-1996 by cisco Systems
2500 processor with 14336 Kbytes of main memory
Abort at 0x10B1F3C (PC)
>
را ﺑﻪ 2412×0 ﺗﻐﯿﯿﺮ ﻣﯽ دﻫﯿﻢ ﺗﺎ در ﺑﻮت ﺑﻌﺪي روﺗﺮ از ﻃﺮﯾﻖconfiguration register 2. اﮐﻨﻮن ﻣﺤﺘﻮاي
. ﻣﻮرد ﭘﺮدازش ﻗﺮار ﻧﮕﯿﺮدNvram ﺑﻮت ﺷﻮد و ﻣﺤﺘﻮايIOS
>o/r 0x2142
>i
privileged 3. راه اول:ﭘﺲ از ﺑﻮت ﺷﺪن روﺗﺮ ﺑﺎ ﺻﻔﺤﻪ ﺗﻨﻈﯿﻤﺎت اوﻟﯿﻪ روﺗﺮ روﺑﺮو ﻣﯿﺸﻮد ، ﺑﺎ ورود ﺑﻪ ﻣﺤﯿﻂ
running configuration را ﺑﻪstartup configuration ، ﻣﺤﺘﻮايen از ﻃﺮﯾﻖ ﺗﺎﯾﭗ ﮐﺮدنmode
از ﻃﺮﯾﻖNvram ﮐﭙﯽ ﻣﯿﮑﻨﯿﻢ و ﭘﺲ از ان ﭘﺴﻮردﻫﺎ را ﺗﻐﯿﯿﺮ ﻣﯽ دﻫﯿﻢ در ﻧﻬﺎﯾﺖ ﻫﻢ ذﺧﯿﺮه ﺗﻐﯿﯿﺮات در
. اﻧﺠﺎم ﻣﯿﮕﯿﺮدcopy run start
--- System Configuration Dialog --Would you like to enter the initial configuration dialog? [yes/no]: n
Press RETURN to get started!
Router>enable
Router#copy start run
Destination filename [running-config]?
506 bytes copied in 3.868 secs (168 bytes/sec)
ARCVRSR01#configure terminal
ARCVRSR01(config)#enable secret NEWENABLEPASSWORD
ARCVRSR01(config)#line con 0
ARCVRSR01(config-if)#password NEWPASSWORD
ARCVRSR01(config-if)#end
ARCVRSR01#copy run start
Destination filename [startup-config]?
Building configuration...
[OK]
ARCVRSR01#
وارد ﻣﯽ ﺷﻮﯾﻢ اﻣﺎprivileged mode ﺑﻪ ﻣﺤﯿﻂIOS 4. راه دوم : ﻫﻤﺎﻧﻨﺪ روش ﻗﺒﻠﯽ ﭘﺲ از ﺑﻮت از ﻃﺮﯾﻖ
را ﭘﺎك ﻣﯿﮑﻨﯿﻢNvram اﯾﻨﺒﺎر ﻣﺤﺘﻮاي
--- System Configuration Dialog ---
Page 53 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-54-320.jpg)
![Would you like to enter the initial configuration dialog? [yes/no]: n
Press RETURN to get started!
Router>enable
Router#write erase
Erasing the nvram filesystem will remove all files! Continue? [confirm]
[OK]
Erase of nvram: complete
Router#
را ﺑﻪconfiguration register ﻣﺤﺘﻮايNvram 5. در ﻫﺮ دو ﺣﺎﻟﺖ ﭘﺲ از رﯾﺴﺖ ﮐﺮدن ﭘﺴﻮرد ﯾﺎ ﭘﺎك ﮐﺮدن
. ﺑﻮت ﺧﻮاﻫﺪ ﺷﺪNvram 2012×0 ﺑﺮ ﻣﯿﮕﺮداﻧﯿﻢ ﺑﺎ رﯾﺒﻮت ﺑﻌﺪي ﺳﯿﺴﺘﻢ از ﻃﺮﯾﻖ ﺧﻮاﻧﺪن ﻣﺤﺘﻮاي
Router#configure terminal
Router(config)#config-register 0x2102
Router(config)#end
Page 54 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-55-320.jpg)

![روﺗﺮ را روﺷﻦ ﻣﯿﮑﻨﯿﻢ ﺗﺎ ﻓﺮاﯾﻨﺪ ﺑﻮت آﻏﺎز ﺷﻮد ، در اﯾﻦ ﺣﯿﻦ ﻧﯿﺎز اﺳﺖ ﺗﺎ ﻓﺮاﯾﻨﺪ ﺑﻮت ﺑﻪ ﺻﻮرت ﻧﺮﻣﺎل ﻣﺘﻮﻗﻒ
.1
اﻧﺠﺎم ﻣﯽ دﻫﯿﻢ ﺗﺎ ﺑﻪCtrl+Puse Breake ﺑﺎﻻ ﺑﯿﺎﯾﺪ ، اﯾﻨﮑﺎر را ﻓﺸﺮدن ﻣﮑﺮرbootrom ﺷﻮد و روﺗﺮ ﺑﺎ
. وارد ﺷﻮﯾﻢbootrom ﻣﺤﯿﻂ
System Bootstrap, Version 12.2(8r) [cmong 8r], RELEASE SOFTWARE (fc1)
Copyright (c) 2003 by cisco Systems, Inc.
C2600 platform with 262144 Kbytes of main memory
monitor: command "boot" aborted due to user interrupt
rommon 1 >
را ﺑﻪ 2412×0 ﺗﻐﯿﯿﺮ ﻣﯽ دﻫﯿﻢ ﺗﺎ در ﺑﻮت ﺑﻌﺪي روﺗﺮ از ﻃﺮﯾﻖconfiguration register 2. اﮐﻨﻮن ﻣﺤﺘﻮاي
ﻣﻮرد ﭘﺮدازش ﻗﺮار ﻧﮕﯿﺮدNvram ﺑﻮت ﺷﻮد و ﻣﺤﺘﻮايIOS
rommon 1 >confreg 0x2142
rommon 2 >reset
privileged 3. راه اول:ﭘﺲ از ﺑﻮت ﺷﺪن روﺗﺮ ﺑﺎ ﺻﻔﺤﻪ ﺗﻨﻈﯿﻤﺎت اوﻟﯿﻪ روﺗﺮ روﺑﺮو ﻣﯿﺸﻮد ، ﺑﺎ ورود ﺑﻪ ﻣﺤﯿﻂ
ﮐﭙﯽrunning configuration ﺑﻪstartup configuration ، ﻣﺤﺘﻮايen از ﻃﺮﯾﻖ ﺗﺎﯾﭗ ﮐﺮدنmode
copy از ﻃﺮﯾﻖNvram ﻣﯿﮑﻨﯿﻢ و ﭘﺲ از ان ﭘﺴﻮردﻫﺎ را ﺗﻐﯿﯿﺮ ﻣﯽ دﻫﯿﻢ در ﻧﻬﺎﯾﺖ ﻫﻢ ذﺧﯿﺮه ﺗﻐﯿﯿﺮات در
run start
--- System Configuration Dialog ---
Would you like to enter the initial configuration dialog? [yes/no]: n
Press RETURN to get started!
Router>enable
Router#copy start run
Destination filename [running-config]?
506 bytes copied in 3.868 secs (168 bytes/sec)
IMAROUTER#configure terminal
IMAROUTER(config)#enable secret NEWENABLEPASSWORD
IMAROUTER(config)#line con 0
IMAROUTER(config-if)#password NEWPASSWORD
IMAROUTER(config-if)#end
IMAROUTER#copy run start
Destination filename [startup-config]?
Building configuration...
[OK]
IMAROUTER#
Page 56 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-57-320.jpg)
![ وارد ﻣﯽ ﺷﻮﯾﻢ اﻣﺎprivileged mode ﺑﻪ ﻣﺤﯿﻂIOS 4. راه دوم : ﻫﻤﺎﻧﻨﺪ روش ﻗﺒﻠﯽ ﭘﺲ از ﺑﻮت از ﻃﺮﯾﻖ
را ﭘﺎك ﻣﯿﮑﻨﯿﻢNvram اﯾﻨﺒﺎر ﻣﺤﺘﻮاي
--- System Configuration Dialog --Would you like to enter the initial configuration dialog? [yes/no]: n
Press RETURN to get started!
Router>enable
Router#write erase
Erasing the nvram filesystem will remove all files! Continue? [confirm]
[OK]
Erase of nvram: complete
Router#
را ﺑﻪconfiguration register ﻣﺤﺘﻮايNvram 5. در ﻫﺮ دو ﺣﺎﻟﺖ ﭘﺲ از رﯾﺴﺖ ﮐﺮدن ﭘﺴﻮرد ﯾﺎ ﭘﺎك ﮐﺮدن
. ﺑﻮت ﺧﻮاﻫﺪ ﺷﺪNvram 2012×0 ﺑﺮ ﻣﯿﮕﺮداﻧﯿﻢ ﺑﺎ رﯾﺒﻮت ﺑﻌﺪي ﺳﯿﺴﺘﻢ از ﻃﺮﯾﻖ ﺧﻮاﻧﺪن ﻣﺤﺘﻮاي
Router#configure terminal
Router(config)#config-register 0x2102
Router(config)#end
Page 57 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-58-320.jpg)

![MODE ﻫﺎ و ﻣﺪت زﻣﺎن ﻻزم ﺟﻬﺖ ﭘﺎﯾﯿﻦ ﻧﮕﻪ داﺷﺘﻦ دﮐﻤﻪLed رﻓﺘﺎر
ﻧﻮع ﺳﻮﯾﯿﭻ
ﺧﺎﻣﻮش ﻧﺸﺪه ﭘﺎﯾﻦ ﻧﮕﻪ داﺷﺘﻪ ﺷﻮدFA0/1 ﭘﻮرتLED ﺗﺎ زﻣﺎﻧﯽ ﮐﻪ
2900XL, 3500XL,
3550
زرد ﭼﺸﻤﮏSyst LED ﺧﺎﻣﻮش ﺷﺪ آﻧﺮا رﻫﺎ ﮐﻨﯿﺪ.ﭘﺲ از رﻫﺎ ﮐﺮدن آنStat LED ﺣﺪودا ﭘﺲ از 5 ﺛﺎﻧﯿﻪ و زﻣﺎﻧﯽ ﮐﻪ
زن ﺧﻮاﻫﺪ ﺷﺪ
2940, 2950
Mode زرد ﭼﺸﻤﮏ زن ﺷﺪ و ﺑﻌﺪ از آن ﮐﺎﻣﻼ ﺳﺒﺰ ﺷﺪ دﮐﻤﻪ را رﻫﺎ ﮐﻨﯿﺪ.ﭘﺲ از رﻫﺎ ﮐﺮدنSYST LED ﭘﺲ از اﯾﻨﮑﻪ
. ﺳﺒﺰ ﭼﺸﻤﮏ زن ﺧﻮاﻫﺪ ﺷﺪSYST LED ﺣﺎﻟﺖ
2960, 2970
ﺳﺒﺰSYST LED را رﻫﺎ ﮐﻨﯿﺪ.ﭘﺲ از رﻫﺎ ﮐﺮدن آنMode دﮐﻤﻪSYST LED ﺑﻌﺪ از ﺣﺪود 51 ﺛﺎﻧﯿﻪ و ﺳﺒﺰ ﺷﺪن
ﭼﺸﻤﮏ زن ﺧﻮاﻫﺪ ﺷﺪ
3560, 3750
ﺑﺎ ﻋﺒﺎرت ﻫﺎي زﯾﺮ ﻣﻮاﺟﻪ ﺧﻮاﻫﯿﻢ ﺷﺪSWITCH ROM 2. ﭘﺲ از ورود ﻣﻮﻓﻘﯿﺖ آﻣﯿﺰ ﺑﻪ ﻣﺤﯿﻂ
Boot Sector Filesystem (bs) installed, fsid: 2
Base ethernet MAC Address: 00:14:f2:d2:41:80
Xmodem file system is available.
The password-recovery mechanism is enabled.
The system has been interrupted prior to initializing the
flash filesystem. The following commands will initialize
the flash filesystem, and finish loading the operating
system software:
flash_init
boot
switch:
flash_init ﺷﺪن دارد ﺑﺎ ﺗﺎﯾﭗ دﺳﺘﻮرinitialize ﻧﯿﺎز ﺑﻪflash 3. در اﯾﻦ ﻣﺮﺣﻠﻪ
switch:flash_init
Initializing Flash...
flashfs[0]: 5 files, 1 directories
flashfs[0]: 0 orphaned files, 0 orphaned directories
flashfs[0]: Total bytes: 15998976
flashfs[0]: Bytes used: 12282368
flashfs[0]: Bytes available: 3716608
flashfs[0]: flashfs fsck took 10 seconds.
...done Initializing Flash.
switch:
Page 59 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-60-320.jpg)
![ ﺑﻪ ﻣﻨﻈﻮر ﭘﯿﺪا ﮐﺮدن ﻓﺎﯾﻞ ﮐﺎﻧﻔﯿﮓ اﺻﻠﯽ ﻟﯿﺴﺖ ﻣﯽ ﮔﯿﺮﯾﻢ.اﯾﻦ ﻓﺎﯾﻞ ﺑﻪ ﻃﻮر ﭘﯿﺶflash 4. از ﻓﺎﯾﻠﻬﺎي ﻣﻮﺟﻮد در
. ﻧﺎم داردconfig.text ﻓﺮض
switch:dir flash:
Directory of flash:/
1 -rwx 10573494
2 -rwx 684
3 -rwx 1938
4 -rwx 1654
5 -rwx 3096
c3560-advipservicesk9-mz.122-44.SE6.bin
vlan.dat
private-config.text
config.text
multiple-fs
3716608 bytes available (10508886 bytes used)
switch:
ﺗﻐﯿﯿﺮ ﻧﺎم ﻣﯽ دﻫﯿﻢconfig.old 5. ﻓﺎﯾﻞ ﮐﺎﻧﻔﯿﮓ را ﺑﻪ
switch:rename flash:config.text flash:config.old
ﭘﺎك ﮐﺮدdelete flash:config.text ﻫﻤﯿﻨﻄﻮر ﻣﯿﺘﻮان آﻧﺮا ﺑﺎ دﺳﺘﻮر
6. ﭘﺲ از ﺣﺼﻮل اﻃﻤﯿﻨﺎن از ﺗﻐﯿﯿﺮ ﻧﺎم ﻓﺎﯾﻞ ﮐﺎﻧﻔﯿﮓ ﺳﻮﯾﯿﭻ را ﻣﺠﺪدا ﺑﻮت ﻣﯿﮑﻨﯿﻢ.و وارد ﻣﺤﯿﻂ ﺗﻨﻈﯿﻤﺎت اوﻟﯿﻪ
.ﺳﻮﯾﯿﭻ ﻣﯿﺸﻮﯾﻢ
--- System Configuration Dialog --Would you like to enter the initial configuration dialog? [yes/no]: n
Switch>
. ﮐﭙﯽ ﻣﯿﮑﻨﯿﻢrunnin config ﮐﺎﻧﻔﯿﮓ ﻗﺪﯾﻤﯽ را ﺑﻪstart-up ﻣﺤﺘﻮايprivileged mode 7. ﭘﺲ از ورود ﺑﻪ
Switch>enable
Switch#copy flash:config.old run
Destination filename [running-config]?
1654 bytes copied in 9.647 secs (171 bytes/sec)
ARSCORESW1#
. اﻣﮑﺎن ﺗﻐﯿﯿﺮ ﭘﺴﻮردﻫﺎ ﺳﻮﯾﯿﭻ را ﺧﻮاﻫﯿﻢ داﺷﺖrunning config 8. ﭘﺲ از ﮐﭙﯽ ﺗﻨﻈﯿﻤﺎت ﻗﺪﯾﻤﯽ ﺳﻮﯾﯿﭻ ﺑﻪ
Switch#configure terminal
Switch(config)#enable password NEWENABLEPASSWORD
Switch(config)#line con0
Switch(config-line)#password NEWCONSOLELINEPASSWORD
Switch(config-line)#end
Switch#copy run start
Destination filename [startup-config]?
Building configuration...
[OK]
0 bytes copied in 1.309 secs (0 bytes/sec)
Switch#
Page 60 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-61-320.jpg)
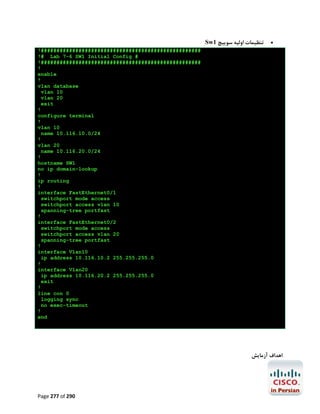
![آزﻣﺎﯾﺶ 4.2-آﺷﻨﺎﯾﯽ ﺑﺎ ﺻﻔﺤﻪ اوﻟﯿﻪ ﺗﻨﻈﯿﻤﺎت ﺳﻮﯾﯿﭻ
در اﯾﻦ آزﻣﺎﯾﺶ ﺑﺎ ﭼﮕﻮﻧﮕﯽ ﺗﻈﯿﻤﺎت ﭘﺎﯾﻪ ﺳﻮﯾﯿﭻ ﻣﺎﻧﻨﺪ IP address,Hostnameو ﺗﻌﺪادي دﯾﮕﺮ از ﻃﺮﯾﻖ ﺻﻔﺤﻪ
اوﻟﯿﻪ ﺗﻨﻈﯿﻤﺎت ﺳﻮﯾﯿﭻ/روﺗﺮ آﺷﻨﺎ ﺧﻮاﻫﯿﻢ ﺷﺪ.
ﮐﺎرﺑﺮد ﻋﻤﻠﯽ
ﺻﻔﺤﻪ ﺗﻨﻈﯿﻤﺎت اوﻟﯿﻪ ﺳﻮﯾﯿﭻ/روﺗﺮ و ﭘﯿﺎﻣﻬﺎ و ﺳﻮاﻻت آن از ﺟﻤﻠﻪ ﺻﻔﺤﺎت آذار دﻫﻨﺪه ﻣﺘﺨﺼﺼﯿﻦ ﺷﺒﮑﻪ اﺳﺖ ﭼﻮن
ﻋﻤﻮم ﻣﺘﺨﺼﺼﯿﻦ ﺗﻤﺎﯾﻠﯽ ﺑﻪ ﮐﺎﻧﻔﯿﮓ ادوات ﺧﻮد ﺑﺎ اﺳﺘﻔﺎده از ﯾﮏ وﯾﺰارد ﻣﺘﻨﯽ ﻣﺤﺪود ﻧﺪارﻧﺪ. اﻣﺎ ﺑﻪ ﻫﺮ ﺣﺎل ﺟﻬﺖ
آزﻣﻮن ccnaآﺷﻨﺎﯾﯽ ﺑﺎ آن اﻟﺰاﻣﯽ اﺳﺖ.ﻗﻄﻌﺎ در آﯾﻨﺪه ﻧﺰدﯾﮏ و ﭘﺲ از ﺗﺴﻠﻂ ﺑﻪ دﺳﺘﻮرات ﻣﺮﺑﻮﻃﻪ ﻫﯿﭻ وﻗﺖ از اﯾﻦ
ﻣﺤﯿﻂ اﺳﺘﻔﺎده ﻧﺨﻮاﻫﯿﺪ ﮐﺮد.
ﭘﯿﺶ ﻧﯿﺎزﻫﺎي آزﻣﺎﯾﺶ
راه اﻧﺪازي ﯾﮏ روﺗﺮ در ﻣﺤﯿﻂ 3 Gnsو ﺑﺮﻗﺮاري اﺗﺼﺎل ﮐﻨﺴﻮل ﺑﻪ آن
اﻫﺪاف آزﻣﺎﯾﺶ
آﺷﻨﺎي ﺑﺎ ﺻﻔﺤﻪ ﺗﻨﻈﯿﻤﺎت اوﻟﯿﻪ روﺗﺮ/ﺳﻮﯾﯿﭻ
دﺳﺘﻮراﻟﻌﻤﻞ آزﻣﺎﯾﺶ
ﭘﺲ از ﺧﺮﯾﺪاري و روﺷﻦ ﮐﺮدن ﯾﮏ دﺳﺘﮕﺎه ﺳﻮﯾﯿﭻ/روﺗﺮ ﺳﯿﺴﮑﻮ اوﻟﯿﻦ ﺻﻔﺤﻪ اي ﮐﻪ ﻧﻤﺎﯾﺎن ﻣﯽ ﺷﻮد ﺻﻔﺤﻪ ﺗﻨﻈﯿﻤﺎت
اوﻟﯿﻪ دﺳﺘﮕﺎه اﺳﺖ.اﯾﻦ ﺻﻔﺤﻪ ﻫﻤﯿﻨﻄﻮر ﻫﻨﮕﺎم ﺑﻮت دﺳﺘﮕﺎه ﭘﺲ از اﺟﺮاي دﺳﺘﻮر eraseﮐﻪ ﺑﺎﻋﺚ ﭘﺎك ﺷﺪن Nvram
ﻣﯿﺸﻮد ﻧﻤﺎﯾﺎن ﻣﯽ ﺷﻮد.
در ﮐﺪ زﯾﺮ ﻣﺤﺘﻮاي اﯾﻦ ﺻﻔﺤﻪ را در ﺑﻮت اوﻟﯿﻪ دﺳﺘﮕﺎه ﻣﺸﺎﻫﺪه ﻣﯿﮑﻨﯿﺪ.
-- --- System Configuration DialogWould you like to enter the initial configuration dialog? [yes/no]: yes
ﭘﺲ از اﻧﺘﺨﺎب yesوﻧﻤﺎﯾﺶ ﻣﺤﯿﻂ ﺗﻨﻈﯿﻤﺎت اوﻟﯿﻪ ، ﻣﺮاﺣﻞ ﺗﻨﻈﯿﻢ ﺑﻪ ﺻﻮرت ﺳﻮال و ﺟﻮاﺑﻬﺎي ﻣﺘﻮاﻟﯽ ﺑﺎ ﺗﻮﺿﯿﺤﺎت
ﻣﺨﺘﺼﺮي ﻧﻤﺎﯾﺎن ﻣﯽ ﺷﻮد.
.At any point you may enter a question mark '?' for help
.Use ctrl-c to abort configuration dialog at any prompt
.'][' Default settings are in square brackets
092 Page 61 of](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-62-320.jpg)
![Basic management setup configures only enough connectivity
for management of the system, extended setup will ask you
to configure each interface on the system
Would you like to enter basic management setup? [yes/no]: yes
را از ﻣﺎTerminal password وEnable secret وHostname اﻃﻼﻋﺎت ﻻزم ﺟﻬﺖ ﺗﻨﻈﻤﯿﺎتyes ﭘﺲ از اﻧﺘﺨﺎب
اﺧﺬ ﺧﻮاﻫﺪ ﮐﺮد
Configuring global parameters:
Enter host name [Router]: R1
The enable secret is a password used to protect access to
privileged EXEC and configuration modes. This password, after
entered, becomes encrypted in the configuration.
Enter enable secret: CISCO
The enable password is used when you do not specify an
enable secret password, with some older software versions, and
some boot images.
Enter enable password: cisco
The virtual terminal password is used to protect
access to the router over a network interface.
Enter virtual terminal password: cisco
ﭘﺮوﺗﮑﻞ اﺳﺘﺎﻧﺪاري اﺳﺖ ﮐﻪ ادوات ﻓﻌﺎل درSNMP . ﻣﻮاﺟﻪ ﺧﻮاﻫﯿﻢ ﺷﺪSNMP ﺑﻌﺪ از ﺗﻈﯿﻤﺎت ﻓﻮق ﺑﺎ ﭘﯿﻐﺎم ﻓﻌﺎل ﺳﺎزي
.ﺷﺒﮑﻪ ﺑﻪ واﺳﻄﻪ آن ﻣﺎﻧﯿﺘﻮ و ﯾﺎ ﭘﯿﮑﺮ ﺑﻨﺪي ﻣﯿﺸﻮﻧﺪ
Configure SNMP Network Management? [no]: yes
Community string [public]: COMMUNITYSTRINGGOESHERE
واﻗﻊManagement network دﻫﯽ ﺑﻪ ﯾﮑﯽ از اﯾﻨﺘﺮﻓﯿﺴﻬﺎي دﺳﺘﮕﺎه ﮐﻪ درIP ﻧﻮﺑﺖ ﺑﻪSNMP ﭘﺲ از ﭘﯿﮑﺮﺑﻨﺪي
ﺷﺪه)در آن رﻧﺞ ﻗﺮار دارد( ﻣﯿﮑﻨﯿﻢ.در ﻧﻈﺮ داﺷﺘﻪ ﺑﺎﺷﯿﺪ ﮐﻪ ﺑﺎﯾﺪ ﻧﺎم اﯾﻨﺘﺮﻓﯿﺲ ﺑﻪ ﻃﻮر ﮐﺎﻣﻞ ﻧﻮﺷﺘﻪ ﺷﻮد
Current interface summary
Any interface listed with OK? value "NO" does not have a valid configuration
Interface
Interface
FastEthernet0/0
FastEthernet0/1
Serial1/0
Serial1/1
Serial1/2
Serial1/3
IP-Address
IP-Address
unassigned
unassigned
unassigned
unassigned
unassigned
unassigned
OK?
OK?
NO
NO
NO
NO
NO
NO
Method
Method
unset
unset
unset
unset
unset
unset
Status
Status
up
up
up
up
up
up
Protocol
Protocol
up
up
down
down
down
down
Page 62 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-63-320.jpg)
![Enter interface name used to connect to the
management network from the above interface summary: FastEthernet0/0
. ﻣﯽ رﺳﺪIP ﺑﻪ ﻣﺤﺾ اﯾﻨﮑﻪ اﯾﻨﺘﺮﻓﯿﺲ ﻣﺮﺑﻮط ﺑﻪ ﻣﺪﯾﺮﯾﺖ دﺳﺘﮕﺎه را اﻧﺘﺨﺎب ﮐﺮدﯾﻢ ﻧﻮﺑﺖ ﺑﻪ ﺗﻨﻈﯿﻢ ﭘﺎراﻣﺘﺮﻫﺎي
Configuring interface FastEthernet0/0:
Operate in full-duplex mode? [no]:
Configure IP on this interface? [yes]:
IP address for this interface: 10.1.1.1
Subnet mask for this interface [255.0.0.0] : 255.255.255.0
Class A network is 10.0.0.0, 24 subnet bits; mask is /24
Running ﺧﻮب،ﭘﺲ از اﺗﻤﺎم ﻣﺮاﺣﻞ ﺑﺎﻻ روﺗﺮ/ﺳﻮﯾﯿﭻ ﮐﺪ ﮐﺎﻧﻔﯿﮓ ﻫﺎي اﻧﺠﺎم ﺷﺪه روي دﺳﺘﮕﺎه ﯾﺎ ﺑﻪ ﺑﯿﺎن دﯾﮕﺮ
: را ﺑﻪ ﻣﺎ ﻧﻤﺎﯾﺶ ﻣﯽ دﻫﺪ ﺑﻪ ﻗﺮار زﯾﺮconfig
The following configuration command script was created:
hostname R1
enable secret 5 $1$kGQ2$tr6bd7mW9zjqzfkUHhnCE0
enable password cisco
line vty 0 4
password cisco
no snmp-server
!
no ip routing
!
interface FastEthernet0/0
no shutdown
half-duplex
ip address 10.1.1.1 255.255.255.0
no mop enabled
!
interface FastEthernet0/1
shutdown
no ip address
!
interface Serial1/0
shutdown
no ip address
!
interface Serial1/1
shutdown
no ip address
!
interface Serial1/2
shutdown
no ip address
!
interface Serial1/3
shutdown
no ip address
!
Page 63 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-64-320.jpg)
![end
ﭘﺲ از ﻣﺮﺣﻠﻪ ﺑﺎﻻ ﺳﯿﺴﺘﻢ در ﺧﺼﻮص ذﺧﯿﺮه ﺗﻨﻈﯿﻤﺎت ﺻﻮرت ﮔﺮﻓﺘﻪ ﺳﻮال ﺧﻮاﻫﺪ ﭘﺮﺳﯿﺪ. ﻋﺪد 2 را ﺟﻬﺖ ذﺧﯿﺮه
اﻧﺘﺨﺎب ﻣﯿﮑﻨﯿﻢstartup config ﺗﻨﻈﯿﻤﺎت در
[0] Go to the IOS command prompt without saving this config.
[1] Return back to the setup without saving this config.
[2] Save this configuration to nvram and exit.
Enter your selection [2]: 2
The enable password you have chosen is the same as your enable secret.
This is not recommended. Re-enter the enable password.
Building configuration...
Use the enabled mode 'configure' command to modify this configuration.
% Crashinfo may not be recovered at bootflash:crashinfo
% This file system device reports an error
Press RETURN to get started!
R1>
Page 64 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-65-320.jpg)


![Router>enable
Password:
Router#
در اﯾﻦ ﻣﻮد دﺳﺘﻮرات ﻣﺪﯾﺮﯾﺘﯽ ﺟﻬﺖ ﻧﮕﻬﺪاري ﺳﯿﺴﺘﻢ اﺟﺮا ﻣﯿﺸﻮﻧﺪ ﻣﺎﻧﻨﺪ ﻣﻮرد زﯾﺮ
Router#copy running-config startup-config
Destination filename [startup-config]?
Building configuration...
[OK]
Router#
وارد ﻣﺤﯿﻂ ﭘﯿﮑﺮﺑﻨﺪي وconfigure terminal ﻫﺴﺘﯿﻢ ﺑﺎ وادر ﮐﺮدن دﺳﺘﻮرPriviledge mode ﻫﻨﮕﺎﻣﯽ ﮐﻪ در
Acess ﻧﺎم دارد.ﻻزم ﺑﻪ ذﮐﺮ اﺳﺖ اﯾﻦ ﻣﻮد درglobal configuration mode ﺗﻨﻈﯿﻤﺎت ﺳﯿﺴﺘﻢ ﻣﯿﺸﻮﯾﻢ ﮐﻪ
. ﻫﺎي ﺳﯿﺴﮑﻮ وﺟﻮد ﻧﺪارد و ﺑﻪ ﻣﺤﺾ ورود ﺑﻪ اﯾﻦ دﺳﺘﮕﺎه ﮐﻠﯿﻪ ﻓﺮاﻣﯿﻦ ﺑﻪ ﻃﻮر ﻣﺴﺘﻘﯿﻢ اﺟﺮا ﺧﻮاﻫﻨﺪ ﺷﺪserver
Router#configure terminal
Enter configuration commands, one per line.
Router(config)#
End with CNTL/Z.
ﺑﻪ ﺳﻄﺢ ﻣﺘﻔﺎوﺗﯽ از دﺳﺘﻮرات ﭘﯿﮑﺮﺑﻨﺪي دﺳﺘﺮﺳﯽ ﺧﻮاﻫﯿﻢ داﺷﺖglobal configuration mode ﭘﺲ از ورود ﺑﻪ
و ﻣﻮارد ﺑﺴﯿﺎري دﯾﮕﺮAccess list ، Vlan، ﻫﻤﭽﻮن ﺗﻨﻈﯿﻤﺎت اﯾﻨﺘﺮﻓﯿﺲ ﻫﺎ
Router(config)#interface f0/0
Router(config-if)#router eigrp 1
Router(config-router)#ip access-list extended example_acl_name
Router(config-ext-nacl)#line con 0
Router(config-line)#
اﺳﺘﻔﺎدهExit از دﺳﺘﻮرuser mode ﺑﻪPrivileged ﺑﺮاي ﺧﺮوج از ﻣﻮد ﺟﺎري و ﺑﺎزﮔﺸﺖ ﺑﻪ ﻣﻮد ﻗﺒﻠﯽ ﻓﺮﺿﺎ از
.ﻣﯿﮑﻨﯿﻢ
ﻋﻼوه ﺑﺮ دﺳﺘﻮرات ﻣﺨﺘﺺ ﻫﺮ ﻣﻮد ، ﺗﻌﺪادي دﺳﺘﻮر ﺗﺮﮐﯿﺒﯽ ﺑﻪ ﻣﻨﻈﻮر اﯾﺠﺎد ﺗﺴﻬﯿﻞ اﻣﻮر در ﻣﺤﯿﻂ ﻣﺘﻨﯽ ﺗﺎﯾﭗ
.دﺳﺘﻮرات وﺟﻮد دارﻧﺪ ﮐﻪ ﺟﺪول آﻧﻬﺎ را در زﯾﺮ ﻣﺸﺎﻫﺪه ﻣﯿﮑﻨﯿﺪ
Key
ESC + F
ESC + B
ESC + DEL
ESC + D
ESC + C
Page 67 of 290
Result
Move insertion point to the beginning of the next word.
Move insertion point to the beginning of the current word.
Erase previous word.
Erase word, or section of a word, following the insertion point.
Capitalize letter following the insertion point.](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-68-320.jpg)










![Router con0 is now available
Press RETURN to get started.
Router>enable
Password:
Router#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#interface fastethernet 0/0
Router(config-if)#ip address 10.1.1.2 255.255.255.0
Router(config-if)#no shutdown
Router(config-if)#end
Router#
ﺑﻪ ﺷﮑﻞ زﯾﺮ اﺳﺘﻔﺎده ﻣﯿﮑﻨﯿﻢping 2. ﺑﺮاي اﻃﻤﯿﻨﺎن از ﺻﺤﺖ ﺗﻨﻈﯿﻤﺎت و ﺑﺮﻗﺮاري اﺗﺼﺎل ﻓﯿﺰﯾﮑﯽ از دﺳﺘﻮر
Router#ping 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
Router#
ﺟﺪﯾﺪ ﺑﻪ ﻓﻠﺶ ﻣﻤﻮري روﺗﺮ ﻣﯿﺮﺳﺪ.ﺑﺎimage و روﺗﺮ ﻧﻮﺑﺖ ﺑﻪ ﮐﭙﯽPC ﭘﺲ از ﺣﺼﻮل اﻃﻤﯿﻨﺎن از ﺑﺮﻗﺮاري اﺗﺼﺎل ﻣﺎﺑﯿﻦ
ﻓﺎﯾﻞ روﺑﺮو ﺧﻮاﻫﯿﻢimage ﺳﺮور و ﻧﺎمTftp ﺑﺎ ﭘﯿﺎﻣﯽ ﻣﺒﻨﯽ ﺑﺮ ﻣﺸﺨﺺ ﮐﺮدن آدرسcopy tftp flash اﺟﺮاي دﺳﺘﻮر
ﺷﺪ
Router#copy tftp flash
Address or name of remote host []? 10.1.1.1
Source filename []? c2600-adventerprisek9-mz.124-15.T11.bin
Destination filename [c2600-adventerprisek9-mz.124-15.T11.bin]?
Accessing tftp://10.1.1.1/c2600-adventerprisek9-mz.124-15.T11.bin...
Erase flash: before copying? [confirm]
Erasing the flash filesystem will remove all files! Continue? [confirm]
Erasing device... eeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee ...erased
Erase of flash: complete
Loading
c2600-adventerprisek9-mz.124-15.T11.bin
from
10.1.1.1
(via
FastEthernet0/0):
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
[OK - 34634180 bytes]
Verifying checksum... CCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCC OK (0x8E89)
34634180 bytes copied in 486.894 secs (71133 bytes/sec)
Router#
Page 80 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-81-320.jpg)
![ در ﻓﺮاﯾﻨﺪ ﺑﻮت دﭼﺎر ﻣﺸﮑﻞ ﺷﺪ وIOS ﻓﺎﯾﻞ ﺟﺪﯾﺪ روﺗﺮ را رﯾﺴﺖ ﻣﯿﮑﻨﯿﻢ ، در ﺻﻮرﺗﯿﮑﻪimage ﭘﺲ از ﮐﭙﯽ ﺷﺪن
.ﺳﯿﺴﺘﻢ ﺑﻮت ﻧﺸﺪ از ﻓﺮاﯾﻨﺪ رﯾﮑﺎوري درس ﺑﻌﺪي اﺳﺘﻔﺎده ﺧﻮاﻫﯿﻢ ﮐﺮد
Router#reload
System configuration has been modified. Save? [yes/no]: no
Proceed with reload? [confirm]
%SYS-5-RELOAD: Reload requested
by console. Reload Reason: Reload Command.
System Bootstrap, Version 12.2(8r) [cmong 8r], RELEASE SOFTWARE (fc1)
Copyright (c) 2003 by cisco Systems, Inc.
C2600 platform with 262144 Kbytes of main memory
program load complete, entry point: 0x80008000, size: 0x2107824
Self
decompressing
the
image
:
#################################################
#############################################################################
###
#############################################################################
###
#############################################################################
###
################################### [OK]
Smart Init is enabled
smart init is sizing iomem
ID
MEMORY_REQ
00036F
0X00103980
000065
0X00031500
0X00098670
0X00211000
TOTAL:
0X003DE4F0
TYPE
C2651XM Dual Fast Ethernet
Four port Voice PM
public buffer pools
public particle pools
If any of the above Memory Requirements are
"UNKNOWN", you may be using an unsupported
configuration or there is a software problem and
system operation may be compromised.
Rounded IOMEM up to: 3Mb.
Using 1 percent iomem. [3Mb/256Mb]
Increasing IOMEM up to: 8Mb
Restricted Rights Legend
Use, duplication, or disclosure by the Government is
subject to restrictions as set forth in subparagraph
(c) of the Commercial Computer Software - Restricted
Rights clause at FAR sec. 52.227-19 and subparagraph
(c) (1) (ii) of the Rights in Technical Data and Computer
Software clause at DFARS sec. 252.227-7013.
cisco Systems, Inc.
170 West Tasman Drive
San Jose, California 95134-1706
Page 81 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-82-320.jpg)


![Copyright (c) 1986-1996 by cisco Systems
2500 processor with 14336 Kbytes of main memory
Abort at 0x10CFA0A (PC)
>
ﺑﻪRom boot image را ﺑﻪ ﻣﻨﻈﻮر ﺑﻮت ﺷﺪن ﺑﻌﺪي از ﻃﺮﯾﻖconfiguration register 2. ﻣﺤﺘﻮاي
1412×0 ﺗﻐﯿﯿﺮ ﻣﯽ دﻫﯿﻢ
>o/r 0x2141
. ﻣﯽ ﺷﻮدInitialize روﺗﺮ وارد ﭘﺮوﺳﻪi 3. ﺑﺎ وارد ﮐﺮدن ﻓﺮﻣﺎن
>I
System Bootstrap, Version 11.0(10c), SOFTWARE
Copyright (c) 1986-1996 by cisco Systems
2500 processor with 14336 Kbytes of main memory
[OUTPUT TRUNCATED]
Press RETURN to get started!
ﺳﺮور ﻧﺴﺒﺖ ﻣﯽ دﻫﯿﻢTftp ﺟﻬﺖ اﺗﺼﺎل ﺑﻪip 4. در اﯾﻦ ﻣﺮﺣﻠﻪ ﺑﻪ اﯾﻨﺘﺮﻓﯿﺲ روﺗﺮ
Press RETURN to get started!
Router(boot)>enable
Router(boot)#config t
Router(boot)(config)#interface e0
Router(boot)(config-if)#ip add 10.1.1.20 255.255.255.0
Router(boot)(config-if)#no shut
Router(boot)(config-if)#exit
****NOTE: The line below is optional if your TFTP server is not on the same
network****
Router(boot)(config)#ip default-gateway 10.1.1.254
Router(boot)(config)#end
. ﺑﻪ ﻓﻠﺶ ﻣﻤﻮري روﺗﺮ ﮐﭙﯽ ﻣﯿﮑﻨﯿﻢTftp را ازIOS Image 5. اﮐﻨﻮن
Router(boot)#copy tftp flash
System flash directory:
No files in System flash
Page 84 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-85-320.jpg)
![[0 bytes used, 8388608 available, 8388608 total]
Address or name of remote host [255.255.255.255]? 172.16.20.17
Source file name? c2500-i-l.121-27b.bin
Destination file name [c2500-i-l.121-27b.bin]?
Accessing file 'c2500-i-l.121-27b.bin' on 10.1.1.1...
Loading c2500-i-l.121-27b.bin from 172.16.20.17 (via Ethernet0): ! [OK]
Erase flash device before writing? [confirm]
Copy 'c2500-i-l.121-27b.bin' from server
as 'c2500-i-l.121-27b.bin' into Flash WITH erase? [yes/no]y
Erasing device... eeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee ...erased
Loading c2500-i-l.121-27b.bin from 172.16.20.17 (via Ethernet0):
!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!! [OUTPUT TRUNCATED]
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!
[OK - 8040260/8388608 bytes]
Verifying checksum... OK (0xCB96)
Flash copy took 0:03:58 [hh:mm:ss]
Router(boot)#
را ﺑﻪ ﻣﻘﺪار اوﻟﯿﻪ ﺑﺮ ﻣﯽ ﮔﺮداﻧﯿﻢ و روﺗﺮConfiguration register ﻣﺤﺘﻮايIOS 6. ﭘﺲ از ﮐﭙﯽ ﻣﻮﻓﻘﯿﺖ آﻣﯿﺰ
.را رﯾﺒﻮت ﻣﯽ ﮐﻨﯿﻢ ﺑﻪ اﻣﯿﺪ اﯾﻨﮑﻪ اﯾﻨﺒﺎر ﺑﺎﻻ ﺧﻮاﻫﺪ آﻣﺪ
Router(boot)#configure terminal
Router(boot)(config)#configuration-register 0x2102
Router(boot)(config)#end
Router(boot)#reload
System configuration has been modified. Save? [yes/no]: n
Proceed with reload? [confirm]
00:06:51: %SYS-5-RELOAD: Reload requested
System Bootstrap, Version 11.0(10c), SOFTWARE
Copyright (c) 1986-1996 by cisco Systems
2500 processor with 14336 Kbytes of main memory
Notice: NVRAM invalid, possibly due to write erase.
F3: 7916604+123624+619980 at 0x3000060
Restricted Rights Legend
Use, duplication, or disclosure by the Government is
subject to restrictions as set forth in subparagraph
(c) of the Commercial Computer Software - Restricted
Page 85 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-86-320.jpg)
![Rights clause at FAR sec. 52.227-19 and subparagraph
(c) (1) (ii) of the Rights in Technical Data and Computer
Software clause at DFARS sec. 252.227-7013.
cisco Systems, Inc.
170 West Tasman Drive
San Jose, California 95134-1706
Cisco Internetwork Operating System Software
IOS (tm) 2500 Software (C2500-I-L), Version 12.1(27b), RELEASE SOFTWARE (fc1)
Copyright (c) 1986-2005 by cisco Systems, Inc.
Compiled Tue 16-Aug-05 22:38 by pwade
Image text-base: 0x03041FDC, data-base: 0x00001000
cisco 2500 (68030) processor (revision N) with 14336K/2048K bytes of memory.
Processor board ID 11848462, with hardware revision 00000000
Bridging software.
X.25 software, Version 3.0.0.
1 Ethernet/IEEE 802.3 interface(s)
2 Serial network interface(s)
32K bytes of non-volatile configuration memory.
8192K bytes of processor board System flash (Read ONLY)
--- System Configuration Dialog --Would you like to enter the initial configuration dialog? [yes/no]:
7. ﺧﻮب ﺗﺎ اﯾﻨﺠﺎ روﺗﺮ ﺑﺎﻻ اﻣﺪ اﻣﺎ ﺑﺪون ﻫﯿﭻ ﮔﻮﻧﻪ اﺛﺮي از ﺗﻨﻈﯿﻤﺎت ﻗﺒﻠﯽ . اﮔﺮ از ﺗﻨﻈﯿﻤﺎت ﻗﺒﻠﯽ ﭘﺸﺘﯿﺒﺎن ﺗﻬﯿﻪ
.ﮐﺮده اﯾﺪ ﮐﻪ ﻫﯿﭻ ، اﮔﺮ ﻧﮑﺮده اﯾﺪ ﺑﻬﺘﺮ اﺳﺖ رزوﻣﻪ ﺧﻮد را ﺑﺮوز ﮐﻨﯿﺪ
Page 86 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-87-320.jpg)

![System Bootstrap, Version 12.2(8r) [cmong 8r], RELEASE SOFTWARE (fc1)
Copyright (c) 2003 by cisco Systems, Inc.
C2600 platform with 262144 Kbytes of main memory
device does not contain a valid magic number
boot: cannot open "flash:"
boot: cannot determine first file name on device "flash:"
rommon 1 >
1562 وﺟﻮد دارﻧﺪ راXM روي ﭘﻠﺘﻔﺮمROMMON ﻣﯽ ﺗﻮان ﻟﯿﺴﺖ دﺳﺘﻮراﺗﯽ را ﮐﻪ در ﺣﺎﻟﺖhelp ﺑﺎ اﺟﺮاي دﺳﺘﻮر
.ﻣﺸﺎﻫﺪه ﮐﺮد
rommon 1 > help
alias
boot
break
confreg
cont
context
cookie
dev
dir
dis
dnld
frame
help
history
meminfo
repeat
reset
set
stack
sync
sysret
tftpdnld
unalias
unset
xmodem
rommon 2 >
set and display aliases command
boot up an external process
set/show/clear the breakpoint
configuration register utility
continue executing a downloaded image
display the context of a loaded image
display contents of cookie PROM in hex
list the device table
list files in file system
display instruction stream
serial download a program module
print out a selected stack frame
monitor builtin command help
monitor command history
main memory information
repeat a monitor command
system reset
display the monitor variables
produce a stack trace
write monitor environment to NVRAM
print out info from last system return
tftp image download
unset an alias
unset a monitor variable
x/ymodem image download
را ﺑﻪ درون ﻓﻠﺶ ﻣﻤﻮري روﺗﺮ داﻧﻮدIOS image اﺳﺖ.اﯾﻦ دﺳﺘﻮرtftpdnld 2. اﮐﻨﻮن ﻧﻮﺑﺖ ﮐﺎر ﺑﺎ دﺳﺘﻮر
را ﻧﯿﺰ دارا اﺳﺖ.ﺑﺎ ﺗﺎﯾﭗ اﯾﻦ دﺳﺘﻮر ﭘﺎراﻣﺘﺮﻫﺎﯾﯽ ﮐﻪ راRam ﻣﯿﮑﻨﺪ ﻫﻤﯿﻨﻄﻮر ﻗﺎﺑﻠﯿﺖ ﺑﺎرﮔﺬاري ﻣﺴﺘﻘﯿﻢ درون
ﮐﻪ ﺑﺮاي اﺟﺮا ﺑﻪ آﻧﻬﺎ ﻧﯿﺎز دارد را ﻣﺸﺎﻫﺪه ﻣﯿﮑﻨﯿﻢ
rommon 2 > tftpdnld
Page 88 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-89-320.jpg)
![Missing or illegal ip address for variable IP_ADDRESS
Illegal IP address.
usage: tftpdnld [-r]
Use this command for disaster recovery only to recover an image via TFTP.
Monitor variables are used to set up parameters for the transfer.
(Syntax: "VARIABLE_NAME=value" and use "set" to show current variables.)
"ctrl-c" or "break" stops the transfer before flash erase begins.
The following variables are REQUIRED to be set for tftpdnld:
IP_ADDRESS: The IP address for this unit
IP_SUBNET_MASK: The subnet mask for this unit
DEFAULT_GATEWAY: The default gateway for this unit
TFTP_SERVER: The IP address of the server to fetch from
TFTP_FILE: The filename to fetch
The following variables are OPTIONAL:
TFTP_VERBOSE:
Print
setting.
0=quiet,
1=progress(default),
2=verbose
TFTP_RETRY_COUNT: Retry count for ARP and TFTP (default=12)
TFTP_TIMEOUT:
Overall
timeout
of
operation
in
seconds
(default=7200)
TFTP_CHECKSUM:
Perform
checksum
test
on
image,
0=no,
1=yes
(default=1)
FE_SPEED_MODE:
0=10/hdx,
1=10/fdx,
2=100/hdx,
3=100/fdx,
4=Auto(deflt)
Command line options:
-r: do not write flash, load to DRAM only and launch image
rommon 3 >
را وارد ﻣﯿﮑﻨﯿﻢset دﺳﺘﻮرimage ﺟﻬﺖ ﻣﻘﺪار دﻫﯽ ﺑﻪ ﭘﺎراﻣﺘﺮﻫﺎي ﻣﻮرد ﻧﯿﺎز ﺟﻬﺖ داﻧﻠﻮد
rommon 3 > set
PS1=rommon ! >
BOOT=
RET_2_RUTC=0
BSI=0
RANDOM_NUM=1492875412
ROM_PERSISTENT_UTC=1016225763
RET_2_RTS=
RET_2_RCALTS=
?=1
rommon 24 > set
PS1=rommon ! >
BOOT=
RET_2_RUTC=0
BSI=0
RANDOM_NUM=1492875412
ROM_PERSISTENT_UTC=1016225763
RET_2_RTS=
RET_2_RCALTS=
?=0
rommon 4 >
Page 89 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-90-320.jpg)
![در زﯾﺮ ﻟﯿﺴﺖ ﭘﺎراﻣﺘﺮﻫﺎ و ﻣﻘﺎدﯾﺮ ﻣﻮرد ﻧﯿﺎز آﻧﻬﺎ را ﻣﺸﺎﻫﺪه ﻣﯿﮑﻨﯿﺪ
rommon
rommon
rommon
rommon
rommon
4
5
6
7
8
>
>
>
>
>
IP_ADDRESS=10.1.1.10
IP_SUBNET_MASK=255.255.255.0
DEFAULT_GATEWAY=10.1.1.254
TFTP_SERVER=172.16.20.17
TFTP_FILE=c2600-i-mz.123-26.bin
اﺳﺘﻔﺎدهRam درونimage ﺑﻪ ﻣﻨﻈﻮر ﺑﺎرﮔﺬاري ﻣﺴﺘﻘﯿﻢtftpdnld –r ﭘﺲ از ﻣﻘﺪار دﻫﯽ ﭘﺎراﻣﺘﺮﻫﺎ از دﺳﺘﻮر
ﻣﯿﮑﻨﯿﻢ
rommon 9 > tftpdnld -r
IP_ADDRESS:
IP_SUBNET_MASK:
DEFAULT_GATEWAY:
TFTP_SERVER:
TFTP_FILE:
10.1.1.10
255.255.255.0
10.1.1.254
172.16.20.17
c2600-i-mz.123-26.bin
.....
Receiving c2600-i-mz.123-26.bin from 172.16.20.17 !!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
File reception completed.
program load complete, entry point: 0x80008000, size: 0x765238
Self decompressing the image : ##############################################
####################################################################### [OK]
Smart Init is enabled
smart init is sizing iomem
ID
MEMORY_REQ
00036F
0X00103980
000065
0X00031500
0X00098670
0X00211000
TOTAL:
0X003DE4F0
TYPE
C2651XM Dual Fast Ethernet
Four port Voice PM
public buffer pools
public particle pools
If any of the above Memory Requirements are
"UNKNOWN", you may be using an unsupported
configuration or there is a software problem and
system operation may be compromised.
Rounded IOMEM up to: 4Mb.
Using 3 percent iomem. [4Mb/128Mb]
Page 90 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-91-320.jpg)
![Restricted Rights Legend
Use, duplication, or disclosure by the Government is
subject to restrictions as set forth in subparagraph
(c) of the Commercial Computer Software - Restricted
Rights clause at FAR sec. 52.227-19 and subparagraph
(c) (1) (ii) of the Rights in Technical Data and Computer
Software clause at DFARS sec. 252.227-7013.
cisco Systems, Inc.
170 West Tasman Drive
San Jose, California 95134-1706
Cisco Internetwork Operating System Software
IOS (tm) C2600 Software (C2600-I-M), Version 12.3(26), RELEASE SOFTWARE (fc2)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2008 by cisco Systems, Inc.
Compiled Mon 17-Mar-08 15:23 by dchih
cisco 2651XM (MPC860P) processor (revision 0x200) with 126976K/4096K bytes of
memory.
Processor board ID JAE08030QZL (457188033)
M860 processor: part number 5, mask 2
Bridging software.
X.25 software, Version 3.0.0.
2 FastEthernet/IEEE 802.3 interface(s)
2 Serial network interface(s)
32K bytes of non-volatile configuration memory.
49152K bytes of processor board System flash (Read/Write)
--- System Configuration Dialog --Would you like to enter the initial configuration dialog? [yes/no]:
ﺳﺮور ﺑﻪ ﻓﻠﺶTftp ازISO image ﺷﺮوع ﺑﻪ ﮐﭙﯽcli را ﺗﺎﯾﭗ ﻣﯿﮑﻨﯿﻢ و ﺑﻪ ﻣﺤﺾ وارد ﺷﺪن ﺑﻪ ﻣﺤﯿﻂno ﻋﺒﺎرت
ﻣﻤﻮري روﺗﺮ ﻣﯿﮑﻨﯿﻢ. ﻣﻤﮑﻦ اﺳﺖ از ﺧﻮد ﺑﭙﺮﺳﯿﺪ ﭼﺮا از اﺑﺘﺪا اﯾﻨﮑﺎر اﻧﺠﺎم ﻧﺸﺪ و ﻋﻠﺖ اﯾﻦ دوﺑﺎره ﮐﺎري ﭼﯿﺴﺖ ؟ ﻋﻠﺖ
image اﺳﺖ ﻧﺴﺒﺖ ﺑﻪ ﺳﺮﻋﺖ ﮐﭙﯽTFTPDNLD ﺑﻪ ﻓﻠﺶ ﺑﺎ اﺳﺘﻔﺎده از دﺳﺘﻮرTftp در ﮐﻨﺪ ﺑﻮدن ﻓﺮاﯾﻨﺪ ﮐﭙﯽ از
ﺑﻪTftp ازIOS اﻧﺠﺎم ﻣﯿﺸﻮد و ﺑﻌﺪ از آن ﻣﺎﻧﻨﺪ درس 9.2 اﻗﺪام ﺑﻪ ﮐﭙﯽRam . در ﻧﺘﯿﺠﻪ اﺑﺘﺪا ﺑﻮت ﺑﻪRam ﻓﺎﯾﻞ ﺑﻪ
ﻓﻠﺶ ﻣﯿﮑﻨﯿﻢ. اﺑﺘﺪا ﺗﻨﻈﯿﻤﺎت آدرس اﯾﻨﺘﺮﻓﯿﺲ روﺗﺮرا ﺑﻪ ﻗﺮار زﯾﺮ اﻧﺠﺎم ﻣﯽ دﻫﯿﻢ
Router>enable
Router#configure terminal
Router(config)#interface fa0/0
Router(config-if)#ip add 10.1.1.10 255.255.255.0
Router(config-if)#no shut
Router(config-if)#exit
Router(config)#ip route 0.0.0.0 0.0.0.0 10.1.1.254
Router(config)#end
Router#
Page 91 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-92-320.jpg)
![ ﺑﻪ ﻓﻠﺶ ﻣﻤﻮريIOS وﺑﻌﺪ از آن ﮐﭙﯽ
Router#copy tftp flash
Address or name of remote host []? 172.16.20.17
Source filename []? c2600-adventerprisek9-mz.124-1.bin
Destination filename [c2600-adventerprisek9-mz.124-1.bin]?
Accessing tftp://172.16.20.17/c2600-adventerprisek9-mz.124-1.bin...
Erase flash: before copying? [confirm]
Erasing the flash filesystem will remove all files! Continue? [confirm]
Erasing
device...
eeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee
eeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee
e
eeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee ...erased
Erase of flash: complete
Loading
c2600-adventerprisek9-mz.124-1.bin
from
172.16.20.17
(via
FastEthernet0/0):
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!
[OK - 34634180 bytes]
Verifying checksum... OK (0x8E89)
34634180 bytes copied in 279.014 secs (124131 bytes/sec)
Router#
ﺑﻪ ﻓﻠﺶ ﻣﻤﻮري ، روﺗﺮ را رﯾﺴﺖ ﻣﯽ ﮐﻨﯿﻢ و ﺑﺎ ﺳﯿﺴﺘﻢ ﻋﺎﻣﻞ ﺟﺪﯾﺪ ﻣﺴﺘﻘﺮ در ﻓﻠﺶ ﺑﻮتIOS اﮐﻨﻮن ﭘﺲ از اﺗﻤﺎم ﮐﭙﯽ
!ﻣﯽ ﺷﻮﯾﻢ
Page 92 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-93-320.jpg)

![ ﺑﻮت ﻣﯿﮑﻨﯿﻢ.ﺑﺮاي ﻣﺸﺎﻫﺪه ﺟﺰﺋﯿﺎتstat از ﻃﺮﯾﻖ ﭘﺎﯾﯿﻦ ﻧﮕﻪ داﺷﺘﻦ دﮐﻤﻪRom mode 1. ﺳﻮﯾﯿﭻ را ﺑﻪ ﻣﺤﯿﻂ
/ﺑﺒﯿﺸﺘﺮ ﺑﻪ آزﻣﺎﯾﺶ 3.2 ﻣﺮاﺟﻌﻪ ﮐﻨﯿﺪ
.ﺧﺮوﺟﯽ زﯾﺮ ﻣﺤﺘﻮاي ﺗﺮﻣﯿﻨﺎل ﭘﺲ از ورود ﺑﻪ اﯾﻦ ﻣﺤﯿﻂ را ﻧﺸﺎن ﻣﯽ دﻫﺪ
Boot Sector Filesystem (bs) installed, fsid: 2
Base ethernet MAC Address: 00:14:f2:d2:41:80
Xmodem file system is available.
The password-recovery mechanism is enabled.
The system has been interrupted prior to initializing the
flash filesystem. The following commands will initialize
the flash filesystem, and finish loading the operating
system software:
flash_init
boot
switch:
ﺧﻮاﻫﺪ ﺷﺪ ﻣﻄﺎﺑﻖ ﺑﺎ روش زﯾﺮinitialize 2. ﭘﺲ از ورود ﺑﻪ اﯾﻦ ﻣﺤﯿﻂ ﻓﺎﯾﻞ ﺳﯿﺴﺘﻢ ﻓﻠﺶ
switch: flash_init
Initializing Flash...
flashfs[0]: 1 files, 1 directories
flashfs[0]: 0 orphaned files, 0 orphaned directories
flashfs[0]: Total bytes: 15998976
flashfs[0]: Bytes used: 12474880
flashfs[0]: Bytes available: 3524096
flashfs[0]: flashfs fsck took 10 seconds.
...done Initializing Flash.
switch:
ﻓﺮﻣﺖformat flash: ﺗﺨﺮﯾﺐ ﺷﺪه اﺳﺖ ﻣﯿﺘﻮان ﻓﻠﺶ را ﺑﺎ اﺳﺘﻔﺎده ازios - در ﺻﻮرﺗﯿﮑﻪOpitonal .3
! را ﻫﻢ ﭘﺎك ﻣﯿﮑﻨﺪstartup config ﮐﺮد.اﯾﻨﮑﺎر
Switch: format flash:
Are you sure you want to format "flash:" (all data will be lost) (y/n)?y
flashfs[0]: 0 files, 1 directories
flashfs[0]: 0 orphaned files, 0 orphaned directories
flashfs[0]: Total bytes: 7741440
flashfs[0]: Bytes used: 1024
flashfs[0]: Bytes available: 7740416
flashfs[0]: flashfs fsck took 12 seconds.
Page 94 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-95-320.jpg)

![Initializing flashfs...
flashfs[1]: 1 files, 1 directories
flashfs[1]: 0 orphaned files, 0 orphaned directories
flashfs[1]: Total bytes: 15998976
flashfs[1]: Bytes used: 12474880
flashfs[1]: Bytes available: 3524096
flashfs[1]: flashfs fsck took 1 seconds.
flashfs[1]: Initialization complete....done Initializing flashfs.
Checking for Bootloader upgrade.. not needed
POST: CPU MIC register Tests : Begin
POST: CPU MIC register Tests : End, Status Passed
POST: PortASIC Memory Tests : Begin
POST: PortASIC Memory Tests : End, Status Passed
POST: CPU MIC interface Loopback Tests : Begin
POST: CPU MIC interface Loopback Tests : End, Status Passed
POST: PortASIC RingLoopback Tests : Begin
POST: PortASIC RingLoopback Tests : End, Status Passed
POST: Inline Power Controller Tests : Begin
POST: Inline Power Controller Tests : End, Status Passed
POST: PortASIC CAM Subsystem Tests : Begin
POST: PortASIC CAM Subsystem Tests : End, Status Passed
POST: PortASIC Port Loopback Tests : Begin
POST: PortASIC Port Loopback Tests : End, Status Passed
Waiting for Port download...Complete
This product contains cryptographic features and is subject to United
States and local country laws governing import, export, transfer and
use. Delivery of Cisco cryptographic products does not imply
third-party authority to import, export, distribute or use encryption.
Importers, exporters, distributors and users are responsible for
compliance with U.S. and local country laws. By using this product you
agree to comply with applicable laws and regulations. If you are unable
to comply with U.S. and local laws, return this product immediately.
A summary of U.S. laws governing Cisco cryptographic products may be found
at:
http://www.cisco.com/wwl/export/crypto/tool/stqrg.html
If you require further assistance please contact us by sending email to
export@cisco.com.
cisco WS-C3560-24PS (PowerPC405) processor (revision M0) with 131072K bytes
of
memory.
Processor board ID CAT0928Z2EE
Page 97 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-98-320.jpg)






![آزﻣﺎﯾﺶ 1.3 – ﺗﻨﻈﯿﻤﺎت ﭘﺎﯾﻪ ﺗﺼﺪﯾﻖ ﻫﻮﯾﺖ ﮐﺎرﺑﺮ ﺑﺮ ﻣﺒﻨﺎي ﭘﺴﻮرد
در اﯾﻦ آزﻣﺎﯾﺶ ﺑﺎ روش ﭘﺎﯾﻪ اي ﺗﺼﺪﯾﻖ ﻫﻮﯾﺖ ﮐﺎرﺑﺮان ﻣﺒﺘﻨﯽ ﺑﺮ ﭘﺴﻮرد ﻣﺸﺘﻤﻞ ﺑﺮ -Consoel-VTY lines
Auxiliaryآﺷﻨﺎ ﺧﻮاﻫﯿﻢ ﺷﺪ.
ﮐﺎرﺑﺮد ﻋﻤﻠﯽ
اﻣﻨﯿﺖ در ﺷﺒﮑﻪ ﻫﺎي واﻗﻌﯽ از ﻣﻬﻤﺘﺮﯾﻦ ﭼﺎﻟﺸﻬﺎﯾﯽ اﺳﺖ ﮐﻪ ﻣﻬﻨﺪﺳﯿﻦ ﺑﺎ آن دﺳﺖ ﺑﻪ ﮔﺮﯾﺒﺎن ﻫﺴﺘﻨﺪ،ﺑﺎﻻﺧﺺ در
ﺷﺒﮑﻪ ﻫﺎﯾﯽ ﮐﻪ ﺑﺎ اﯾﻨﺘﺮﻧﺖ در ﺗﻤﺎس ﻫﺴﺘﻨﺪ.داﺷﺘﻦ روﺗﺮ/ﺳﻮﯾﯿﭽﻬﺎي ﻧﺎ اﻣﻦ ﮐﻞ ﺷﺒﮑﻪ را در ﻣﻘﺎﺑﻞ ﺗﻌﺪاد ﻧﺎﻣﺤﺪودي از
رﯾﺴﮑﻬﺎي اﻣﻨﯿﺘﯽ ﻗﺮار ﻣﯽ دﻫﺪ.اﯾﻦ آزﻣﺎﯾﺶ ﺑﻪ ﺑﺮرﺳﯽ ﭘﺎﯾﻪ اي ﺗﺮﯾﻦ روش اﻓﺰاﯾﺶ ﺳﻄﺢ اﻣﻨﯿﺘﯽ ادوات ﻣﺒﺘﻨﯽ ﺑﺮ IOS
ﯾﺎ ﻫﻤﺎن ﺗﺼﺪﯾﻖ ﻫﻮﯾﺖ ﺑﺮ اﺳﺎس رﻣﺰ ﻋﺒﻮر اﺳﺖ ﻣﯽ ﭘﺮدازد
ﭘﯿﺶ ﻧﯿﺎز ﻫﺎي آزﻣﺎﯾﺶ
ﺑﺮﻗﺮاري اﺗﺼﺎل ﮐﻨﺴﻮل ﺑﻪ ﯾﮏ روﺗﺮ در ﻣﺤﯿﻂ 3GNS
اﻫﺪاف آزﻣﺎﯾﺶ
ﺗﻨﻈﯿﻢ رﻣﺰ ﻋﺒﻮر ﺑﺮاي ﮐﻨﺴﻮل روﺗﺮ ﻫﻨﮕﺎم درﺧﻮاﺳﺖ ﺑﺮﻗﺮاري اﺗﺼﺎل ﺑﻪ ﮐﻨﺴﻮل
ﺗﻨﻈﯿﻢ رﻣﺰ ﻋﺒﻮر 4-0 VTY lineﺗﺎ در ﻫﻨﮕﺎم ﺑﺮﻗﺮاري اﺗﺼﺎﻟﻬﺎي ﻣﺒﺘﻨﯽ ﺑﺮ Telnet-SSHﺑﻪ ﮐﺎرﺑﺮ ﻧﻤﺎﯾﺶ داده
ﺗﻨﻈﯿﻢ Enable secretو Enable password
ﺷﻮد
ﺗﻨﻈﯿﻢ رﻣﺰ ﻋﺒﻮر ﺑﺮاي Auxiliary line
دﺳﺘﻮر اﻟﻌﻤﻞ آزﻣﺎﯾﺶ
1. ﺑﺮاي اﻋﻤﺎل ﺗﻨﻈﯿﻤﺎت ﻣﺮﺑﻮط ﺑﻪ ﺣﻔﺎﻇﺖ ﮐﻨﺴﻮل روﺗﺮ ﺑﺎ رﻣﺰ ﻋﺒﻮر ﻧﯿﺎز اﺳﺖ وارد ﻣﺤﯿﻂ ﺗﻨﻈﯿﻤﺎت Console
lineﺷﻮﯾﻢ
-- --- System Configuration DialogWould you like to enter the initial configuration dialog? [yes/no]: no
!Press RETURN to get started
092 Page 105 of](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-106-320.jpg)

![Router(config-line)#interface lo0
Router(config-if)#ip add 10.1.1.1 255.255.255.255
Router(config-if)#end
Router#
از ﻃﺮﯾﻖ اﯾﻨﺘﺮﻓﯿﺲ اﯾﺠﺎد ﺷﺪه، از درون روﺗﺮي ﮐﻪ ﺑﺎ ﮐﻨﺴﻮل ﺑﻪ آن ﻣﺘﺼﻞ ﻫﺴﺘﯿﻢ ﺑﻪVty اﮐﻨﻮن ﺑﺮاي ﺗﺴﺖ رﻣﺰ ﻋﺒﻮر
. ﻣﯽ ﮐﻨﯿﻢTelnet اﯾﻨﺘﺮﻓﯿﺲ ﻣﺬﮐﻮرIp
Router#telnet 10.1.1.1
Trying 10.1.1.1 ... Open
User Access Verification
Password:
Password:
Router>
Priviliged ﺧﻮاﻫﯿﻢ ﺷﺪ و در ﺻﻮرت ﻧﯿﺎز ﺑﻪ ورود ﺑﻪuser mode ﭘﺲ از ورود رﻣﺰ ﻋﺒﻮر ﺗﻌﯿﯿﻦ ﺷﺪه وارد ﻣﺤﯿﻂ
. ﻣﻮاﺟﻪ ﺧﻮاﻫﯿﻢ ﺷﺪEnable ﺑﺎ ﺻﻔﺤﻪ ورود رﻣﺰ ﻋﺒﻮرmode
Router>enable
Password:
Password:
Password:
% Bad passwords
Router>
را ﺟﻬﺖ ﭘﺮﺳﯿﺪن رﻣﺰﻋﺒﻮر از ﮐﺎرﺑﺮ ﻫﻨﮕﺎم ورود ﺑﻪEnable Secret وEnable password 3. در اﯾﻦ ﻗﺴﻤﺖ
اﻧﺠﺎم ﺧﻮاﻫﺪGlobal configuration mode ﺗﻨﻈﯿﻢ ﺧﻮاﻫﯿﻢ ﮐﺮد.اﯾﻦ ﺗﻨﻈﯿﻢ در ﻣﺤﯿﻂPrivilege mode
وارد اﯾﻦ ﻣﺤﯿﻂ ﺷﻮﯾﺪConfig terminal ﻫﺴﺘﯿﺪ ﺑﺎ دﺳﺘﻮرTelnet ﺷﺪ ﭘﺲ اﮔﺮ ﻫﻨﻮز در ﻣﺤﯿﻂ
Router>exit
[Connection to 10.1.1.1 closed by foreign host]
Router#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#enable password Cisco1
Router(config)#enable secret Cisco2
Router(config)#end
Router#
:ﻧﮑﺘﻪ
Page 107 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-108-320.jpg)









![Router>enable
Password:
Router#configure terminal
Enter configuration commands, one per line.
Router(config)#hostname R1
R1(config)#
End with CNTL/Z.
. اﺳﺖRsa certificate ﺑﻪ روﺗﺮ ﺟﻬﺖ ﺗﻮﻟﯿﺪdomain name 2. ﻗﺪم ﺑﻌﺪي ﺗﺨﺼﯿﺺ
R1(config)#ip domain-name freeccnaworkbook.com
crypto key generate rsa ﻫﺴﺘﯿﻢ. ﺑﺮاي ﺗﻮﻟﯿﺪ آن از دﺳﺘﻮرRsa certificate 3. اﻻن آﻣﺎده ﺗﻮﻟﯿﺪ
ﺑﻪ ﻫﻤﺮاه ﺳﺎﯾﺰ ﺑﺮ ﺣﺴﺐ ﺑﯿﺖ ﮐﻠﯿﺪ ﻣﺪ ﻧﻈﺮ.در زﯾﺮ روﻧﺪ ﺗﻮﻟﯿﺪ ﮐﻠﯿﺪ 8402 ﺑﯿﺘﯽ را ﻣﺸﺎﻫﺪه ﻣﯿﮑﻨﯿﺪmodulus
R1(config)#crypto key generate rsa modulus 2048
The name for the keys will be: R1.freeccnaworkbook.com
% The key modulus size is 2048 bits
% Generating 2048 bit RSA keys, keys will be non-exportable...[OK]
R1(config)#
%SSH-5-ENABLED: SSH 1.99 has been enabled
در روﺗﺮ ﻓﻌﺎل ﻣﯽ ﺷﻮد و ﻣﯿﺘﻮان ﺑﺎSSH v1.99 ﻗﺎﺑﻠﯿﺖRsa ﻫﻤﺎﻧﻄﻮر ﮐﻪ ﻣﺸﺎﻫﺪه ﻣﯽ ﮐﻨﯿﺪ ﺑﻪ ﻣﺤﺾ اﯾﺠﺎد ﮐﻠﯿﺪ
. ﺑﻪ روﺗﺮ ﻣﺘﺼﻞ ﺷﺪSSH وﺑﺎ ﺑﻬﺮه ﮔﯿﺮي ازSecurecrt ﯾﺎputty اﺳﺘﻔﺎده از
را ﺑﻪ ﮔﻮﻧﻪ اي ﮐﺎﻧﻔﯿﮓ ﻣﯽ ﮐﻨﯿﻢ ﮐﻪ ﺗﻨﻬﺎ ﭘﺬﯾﺮاي ارﺗﺒﺎﻃﺎت ﻣﺒﺘﻨﯽ ﺑﺮVTY ، ﺧﻄﻮطSSH 4. ﭘﺲ از ﻓﻌﺎل ﺷﺪن
. ﻏﯿﺮ ﻓﻌﺎل ﻣﯽ ﺷﻮدTelnet ﺑﺎﺷﻨﺪ ﺑﻪ ﺑﯿﺎن دﯾﮕﺮSSH
R1(config)#line vty 0 4
R1(config-line)#transport input ssh
آداﭘﺘﺮ ﺳﺎﺧﺘﻪ ﺷﺪه اﻧﺠﺎم ﻣﯽ دﻫﯿﻢLoopback ﮐﺮدن ﺑﻪssh 5. ﺗﺴﺖ ﺻﺤﺖ ﺗﻨﻈﻤﯿﺎت را ﺑﺎ
R1(config-line)#end
R1#ssh -l john 10.1.1.1
Password:
Page 117 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-118-320.jpg)










![User Access Verification
Username: tom
Password:
R1#show users
Line
0 con 0
* 2 vty 0
Interface
User
tom
User
Host(s)
idle
idle
Idle
Location
00:14:12
00:00:00 10.1.1.2
Mode
Idle
Peer Address
R1#exit
[Connection to 10.1.1.1 closed by foreign host]
R2#ssh -l tom 10.1.1.1
Password:
R1#sh ssh
Connection
Version
Mode
Encryption
Hmac
Username
0
1.99
IN
aes128-cbc hmac-sha1
Session started
0
1.99
OUT aes128-cbc hmac-sha1
Session started
%No SSHv1 server connections running.
R1#
State
tom
tom
ازTelnet اﻧﺠﺎم ﻣﯽ دﻫﯿﻢ. ﻫﻤﺎﻧﻄﻮر ﮐﻪ در ﻗﺴﻤﺘﻬﺎي ﻗﺒﻞ دﯾﺪﯾﻢ ﺗﻨﻈﺎر ﻣﯽ رود ﺗﺮاﻓﯿﮏR3 ﺗﺴﺖ ﺑﻌﺪي را از ﺳﻤﺖ
. ﻣﺠﺎز ﺑﻪ ﻋﺒﻮر ﺑﺎﺷﺪSSH ﺳﻤﺖ آن ﺑﻼك ﺷﻮد و
R3#telnet 10.1.1.1
Trying 10.1.1.1 ...
% Connection refused by remote host
R3#ssh -l tom 10.1.1.1
Password:
R1#show ssh
Connection
Version
Mode
Encryption
Hmac
Username
0
1.99
IN
aes128-cbc hmac-sha1
Session started
0
1.99
OUT aes128-cbc hmac-sha1
Session started
%No SSHv1 server connections running.
R1#show users
Line
User
Host(s)
Idle
Location
0 con 0
idle
00:13:53
* 2 vty 0
tom
idle
00:00:00 10.1.1.3
Interface
User
Mode
Idle
State
tom
tom
Peer Address
R1#
Page 128 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-129-320.jpg)



![R1>enable
R1#configure terminal
Enter configuration commands, one per line.
R1(config)#line vty 0 4
R1(config-line)#exec-timeout 2
R1(config-line)#end
R1#telnet 10.1.1.1
Trying 10.1.1.1 ... Open
End with CNTL/Z.
User Access Verification
Username: tom
Password:
R1#
[Connection to 10.1.1.1 closed by foreign host]
R1#
دودﻗﯿﻘﻪ اي ﺑﻪ ﺟﺎي آن اﯾﺠﺎدAbsolute timeout 2. در ﻗﺪم ﺑﻌﺪي ﺗﻨﻈﯿﻤﺎت ﻗﺒﻠﯽ را ﭘﺎك ﻣﯿﮑﻨﯿﻢ و ﯾﮏ
. ﺗﺴﺖ ﻣﯿﮑﻨﯿﻢLoopback ﻣﺠﺪد ﺑﻪTelnet ﻣﯿﮑﻨﯿﻢ . ﻧﺘﯿﺠﻪ را ﺑﺎ ﯾﮏ
R1#configure terminal
Enter configuration commands, one per line.
R1(config)#line vty 0 4
R1(config-line)#no exec-timeout
R1(config-line)#absolute-timeout 2
R1(config-line)#end
R1#telnet 10.1.1.1
Trying 10.1.1.1 ... Open
End with CNTL/Z.
User Access Verification
Username: tom
Password:
R1#
*
*
* Line timeout expired
*
[Connection to 10.1.1.1 closed by foreign host]
R1#
.
Page 132 of 290](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-133-320.jpg)
![آزﻣﺎﯾﺶ 11.3 –وب ﺳﺮور داﺧﻠﯽ ادوات ﺳﯿﺴﮑﻮ
در اﯾﻦ آزﻣﺎﯾﺶ ﺑﺎ ﭼﮕﻮﻧﮕﯽ ﺗﻨﻈﯿﻤﺎت ادوات ﺳﯿﺴﮑﻮ ﺟﻬﺖ اﺣﺮاز ﻫﻮﯾﺖ ارﺗﺒﺎﻃﻬﺎي ﺑﺮﻗﺮار ﺷﺪه ﺑﺎ وب ﮐﻨﺴﻮل اﯾﻦ ادوات
آﺷﻨﺎ ﺧﻮاﻫﯿﻢ ﺷﺪ.
ﮐﺎرﺑﺮد ﻋﻤﻠﯽ
ﺗﻨﻈﯿﻤﺎت ﻣﺮﺗﺒﻂ ﺑﺎ اﺣﺮاز ﻫﻮﯾﺖ از ﻃﺮﯾﻖ Cisco IOS web serverﺟﻬﺖ اﯾﺠﺎد و ﮐﻨﺘﺮل دﺳﺘﺮﺳﯽ ﺑﺮﺧﯽ ﮐﺎرﺑﺮان ﺑﻪ
وب ﮐﻨﺴﻮل ادوات ﯾﺎ SDMدر ﻣﺤﯿﻄﻬﺎي ﻋﻤﻠﯿﺎﺗﯽ اﻣﺮي راﯾﺞ ﻣﯽ ﺑﺎﺷﺪ. در اﯾﻦ ﻧﻮﺷﺘﻪ ﺑﻪ ﭼﮕﻮﻧﮕﯽ اﯾﻦ ﺗﻨﻈﯿﻤﺎت
ﺧﻮاﻫﯿﻢ ﭘﺮداﺧﺖ
ﭘﯿﺶ ﻧﯿﺎزﻫﺎي آزﻣﺎﯾﺶ
ﺑﺮﻗﺮاري ارﺗﺒﺎط ﮐﻨﺴﻮل ﺑﺎ ﯾﮏ روﺗﺮ در ﻣﺤﯿﻂ 3Gns
اﯾﺠﺎد ارﺗﺒﺎط Cloudاﯾﻨﺘﺮﻓﯿﺲ 0/1 Faﺑﺎ ﮐﺎرت ﺷﺒﮑﻪ ﮐﺎﻣﭙﯿﻮﺗﺮ
اﯾﺠﺎد ﮐﺎرﺑﺮ ﺑﺎ ﺳﻄﺢ دﺳﺘﺮﺳﯽ 51 ﺟﻬﺖ اﺣﺮاز ﻫﻮﯾﺖ از ﻃﺮﯾﻖ وب
ﺗﺨﺼﯿﺺ آدرس ﺑﻪ 0/0 Faﺟﻬﺖ دﺳﺘﺮﺳﯽ ﺗﺤﺖ وب ﺑﻪ ﮐﻨﺴﻮل روﺗﺮ از ﻃﺮﯾﻖ IE
اﻫﺪاف آزﻣﺎﯾﺶ
ﺗﺨﺼﯿﺺ ﻧﺎم داﻣﻨﻪ stubarea.netﺑﻪ روﺗﺮ
ﻓﻌﺎل ﺳﺎزي وب ﺳﺮور داﺧﻠﯽ روﺗﺮ ﺑﺎ دﺳﺘﻮر the ip http secure-server
ﺗﻨﻈﯿﻢ وب ﺳﺮور داﺧﻠﯽ ﺑﻪ ﻣﻨﻈﻮر اﺧﺬ اﻃﻼﻋﺎت ﻫﻮﯾﺘﯽ از ﭘﺎﯾﮕﺎه داده داﺧﻠﯽ ﺣﺴﺎﺑﻬﺎي ﮐﺎرﺑﺮي
ﻻﮔﯿﻦ ﺗﺤﺖ وب از ﻃﺮﯾﻖ IEﺑﻪ روﺗﺮ و وارد ﮐﺮدن اﻃﻼﻋﺎت ﻫﻮﯾﺘﯽ
دﺳﺘﻮراﻟﻌﻤﻞ آزﻣﺎﯾﺶ
1. ﺗﺨﺼﯿﺺ ﻧﺎم داﻣﻨﻪ stubarea.netﺑﻪ روﺗﺮ و ﻓﻌﺎل ﺳﺎزي وب ﺳﺮور داﺧﻠﯽ آن
R1 con0 is now available
.Press RETURN to get started
R1>enable
R1#configure terminal
.Enter configuration commands, one per line. End with CNTL/Z
R1(config)#ip domain-name stubarea.net
R11(config)#ip http secure-server
]% Generating 1024 bit RSA keys, keys will be non-exportable...[OK
%SSH-5-ENABLED: SSH 1.99 has been enabled
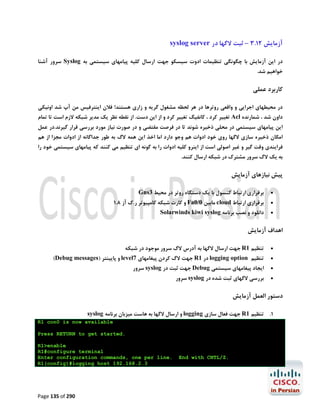
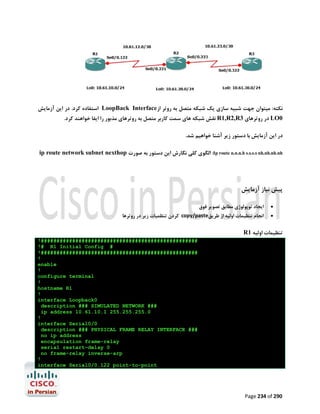
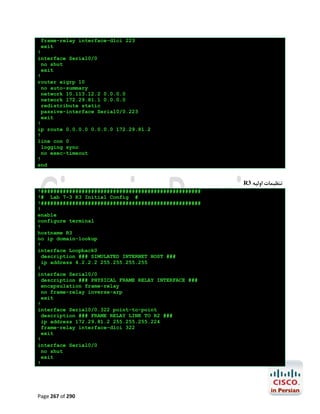
092 Page 133 of](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-134-320.jpg)

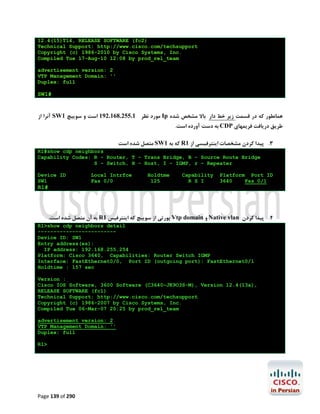





















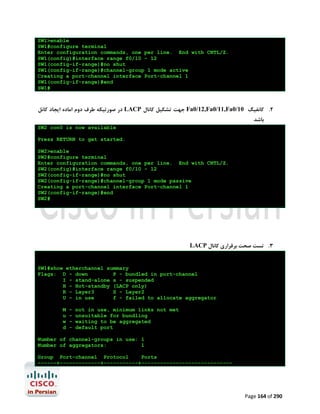



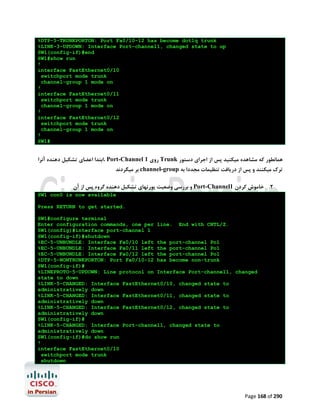


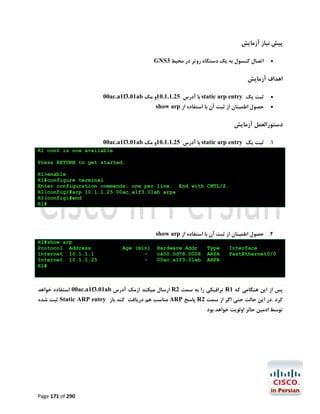


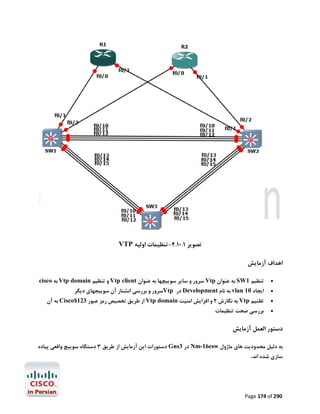







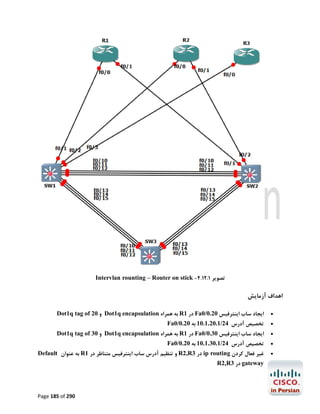













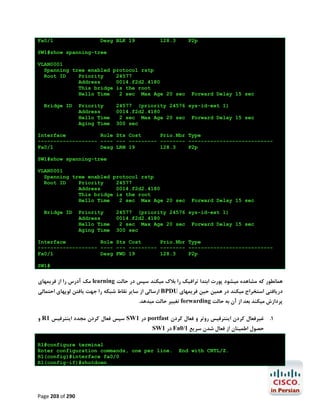






![آزﻣﺎﯾﺶ 1.5-ﺗﻨﻈﯿﻤﺎت ﻟﯿﻨﮑﻬﺎي 1 PtP Tاز ﻃﺮﯾﻖ PPPﯾﺎ HDLC
در اﯾﻦ آزﻣﺎﯾﺶ ﺑﺎ ﭼﮕﻮﻧﮕﯽ ﺗﻨﻈﻤﯿﺎت ﻟﯿﻨﮑﻬﺎي ﺳﺮﯾﺎل 1 Point-to-Point Tدر روﺗﺮﻫﺎي ﺳﯿﺴﮑﻮ از ﻃﺮﯾﻖ
) PPP (Point to Point Protocolﯾﺎ ) HDPC (High-Level Data Link Control Protocolآﺷﻨﺎ
ﺧﻮاﻫﯿﻢ ﺷﺪ.
ﮐﺎرﺑﺮد ﻋﻤﻠﯽ و ﻣﺮور ﻣﻔﺎﻫﯿﻢ
ﺑﻪ ﻋﻨﻮان ﯾﮏ ﻣﻬﻨﺪس ﺷﺒﮑﻪ ﻧﯿﺎز اﺳﺖ ﺗﺎ ﺑﺎ ﺧﻄﻮط 1 Tﮐﻪ ﺳﺎﻟﻬﺎﺳﺖ ﺑﻪ ﻋﻨﻮان اﺳﺘﺎﻧﺪاردي ﺑﺎﻟﻔﻌﻞ ﺟﻬﺖ ﺑﺮﻗﺮاري
ارﺗﺒﺎط ﻣﺤﺪود ﺑﻪ ﺳﺮﻋﺖ 1.544Mbpsﺑﺎ ﺷﻌﺐ ﮐﻮﭼﮏ ﻣﻮرد اﺳﺘﻔﺎده ﻗﺮار ﻣﯿﮕﯿﺮد آﺷﻨﺎ ﺑﺎﺷﯿﺪ.اﺳﺘﺎﻧﺪارد 1 Tدر ﻋﻤﻞ
ﺑﻪ ﻣﺸﺘﻘﺎﺗﯽ ﺑﺎ ﭘﻬﻨﺎي ﺑﺎﻧﺪﻫﺎي ﮐﻤﺘﺮ ﻣﺎﻧﻨﺪ ﻣﺎﻧﻨﺪ 786Kbps،512Kbpsﯾﺎ ﺣﺘﯽ 1Mbpsﺗﻘﺴﯿﻢ ﻣﯿﺸﻮد. ﺧﻄﻮط 1 Tاز
ﺑﻌﺪ ﻓﯿﺰﯾﮑﯽ زوج ﺳﯿﻤﻬﺎي ﻣﺴﯽ ﺑﻪ ﻫﻢ ﺗﺎﺑﯿﺪه ﺷﺪه اي ﻫﺴﺘﻨﺪ ﮐﻪ از ﻃﺮﯾﻖ ﮐﺎرﺗﻬﺎي اﻣﺮوزي ﺗﺮ ,1WIC-1DSU-T
2 WIC-1DSU-T1-Vﯾﺎ 1 CSU/DSU Tﮐﻨﺘﺮﻟﺮﻫﺎي دروﻧﯽ ﺧﻮد روﺗﺮ ﺑﻪ آن ﻣﺘﺼﻞ ﻣﯿﺸﻮﻧﺪ.در ﻧﻤﻮﻧﻪ ﻫﺎي ﻗﺪﯾﻤﯽ
ﺗﺮ ﻧﯿﺰ ﻣﯿﺘﻮان اﯾﻦ اﺗﺼﺎﻻت را از ﻃﺮﯾﻖ ﮐﺎﺑﻠﻬﺎي 53. Vو ﮐﺎرﺗﻬﺎي WIC-1Tﯾﺎ WIC-2Tﻣﺸﺎﻫﺪه ﮐﺮد.
WIC-1Tراﯾﺞ ﺗﺮﯾﻦ راﺑﻂ ﺳﺮﯾﺎل در ﻣﺤﯿﻄﻬﺎي آزﻣﺎﯾﺸﮕﺎﻫﯽ ﻣﯿﺒﺎﺷﺪ و در ﻫﻨﮕﺎم ﮐﺎﻧﻔﯿﮓ آن ﻧﯿﺎز ﺑﻪ ﺗﻨﻈﯿﻢ ﻧﺰخ
Clockدر ﺳﻤﺖ DCEﮐﻪ ﺗﻮﺳﻂ ﺳﺮوﯾﺲ ﭘﺮواﯾﺪر ﺻﻮرت ﻣﯿﮕﯿﺮد و ﻫﻤﯿﻨﻄﻮر DTEﮐﻪ ﺗﻮﺳﻂ ﺷﻤﺎ ﺻﻮرت ﻣﯿﮕﯿﺮد
ﻣﯿﺒﺎﺷﺪ.
در اﯾﻦ آزﻣﺎﯾﺶ ﺑﺎ دﺳﺘﻮرات زﯾﺮ آﺷﻨﺎ ﺧﻮاﻫﯿﻢ ﺷﺪ.
#/# :show controller serialﺟﻬﺖ ﻧﻤﺎﯾﺶ اﻃﻼﻋﺎت ﻣﺨﺘﺺ ﺑﻪ ﮐﻨﺘﺮﻟﺮ ﯾﮏ ﺳﺮﯾﺎل اﯾﻨﺘﺮﻓﯿﺲ ﺧﺎص ﺷﺎﻣﻞ
ﻧﺮخ Clockو ﻧﻮع ﺗﺮﻣﯿﻨﯿﺸﻦ ﮐﺎﺑﻞ )(DTE or DCE
# :clock rateﺟﻬﺖ ﺗﻨﻈﯿﻢ ﻧﺮخ Clockدر ﺳﻤﺖ DCE
] :encapsulation [ HDLC | PPPﺟﻬﺖ اﻧﺘﺨﺎب ﻧﻮع Encapsulation
#/# :show interface serialﺟﻬﺖ ﻧﻤﺎﯾﺶ اﯾﻨﺘﺮﻓﯿﺲ ﺳﺮﯾﺎل ﻣﺸﺨﺺ ﺷﺪه ﻣﺎﻧﻨﺪ ﻧﻮع
Utilization،Uptime،MTU،Encapsulationو ﻣﻮاردي از اﯾﻦ دﺳﺖ.
ﭘﯿﺶ ﻧﯿﺎز ﻫﺎي آزﻣﺎﯾﺶ
ﺑﺮﻗﺮاري اﺗﺼﺎل ﮐﻨﺴﻮل ﺑﻪ 2R1,R
ﺗﺨﺼﯿﺺ آدرﺳﻬﺎي 03/1.12.81.271 ﺑﻪ 1/0 Sدر 1 Rو 03/2.12.81.271 ﺑﻪ 1/0 Sدر 2R
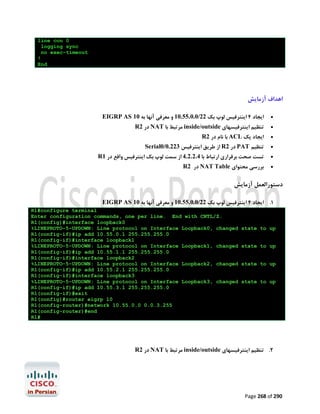
092 Page 212 of](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-213-320.jpg)

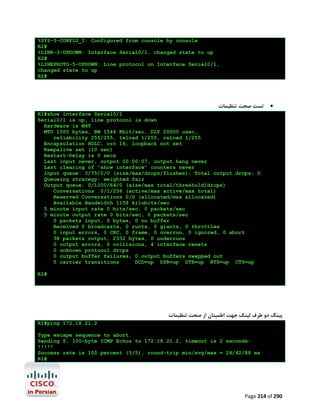



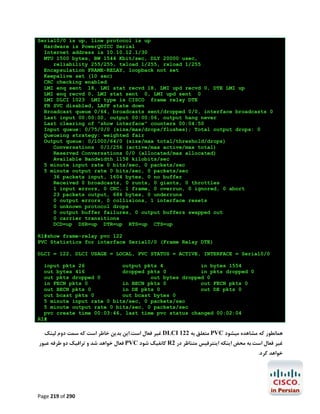



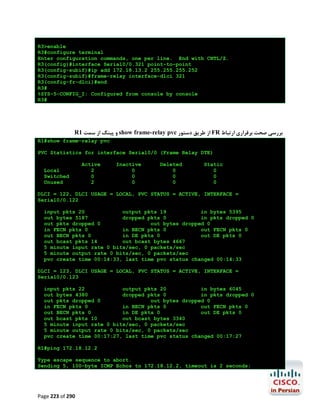



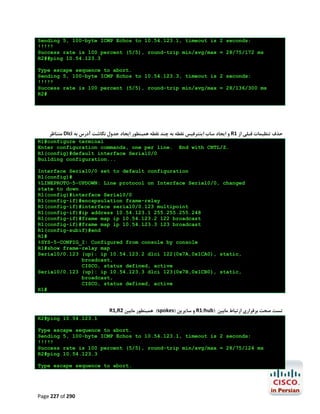









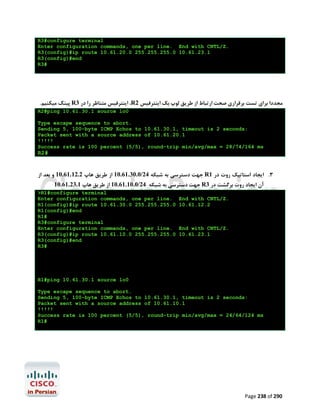

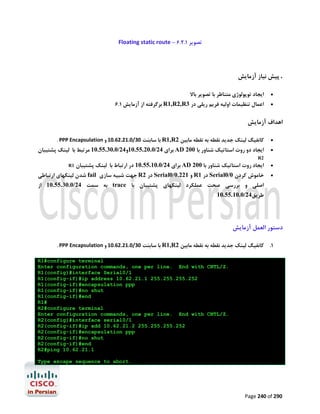
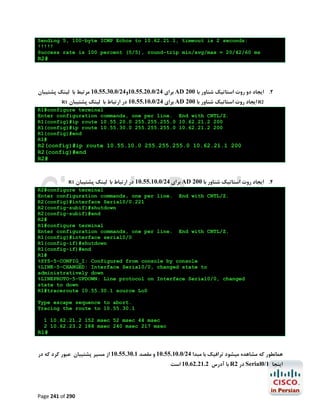

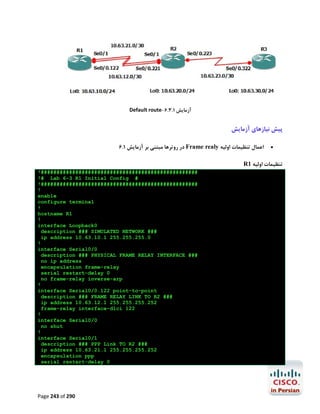
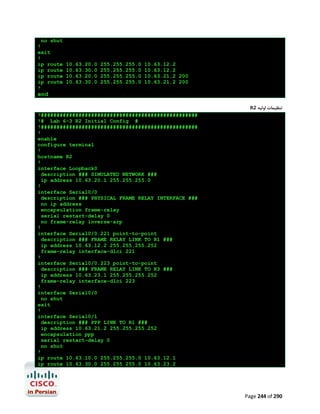
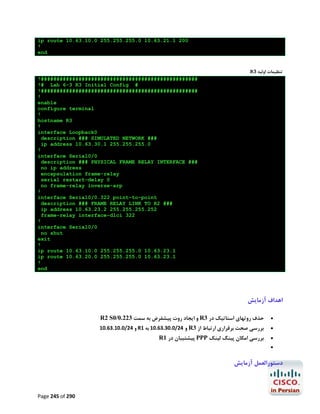




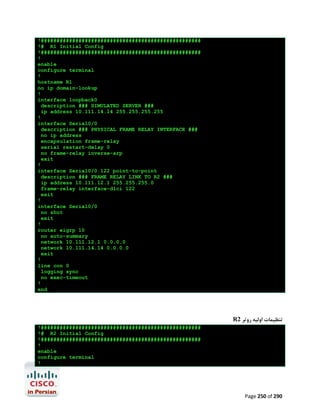







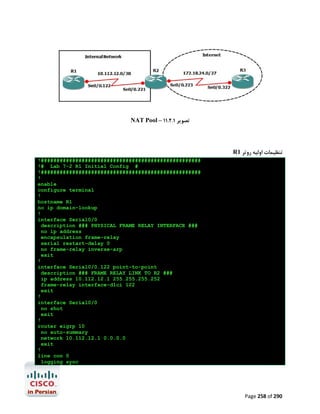
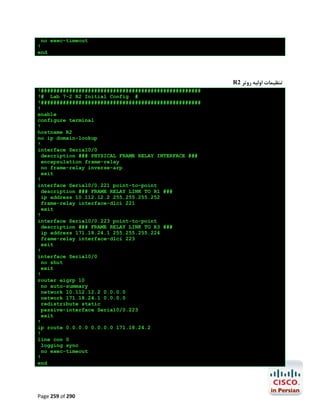
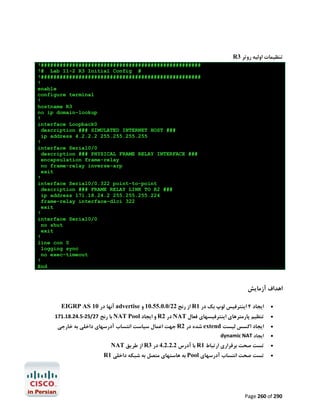
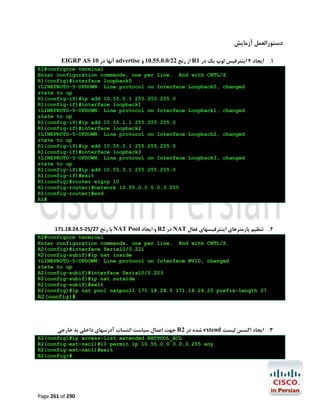




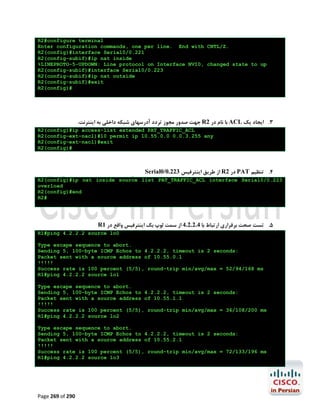















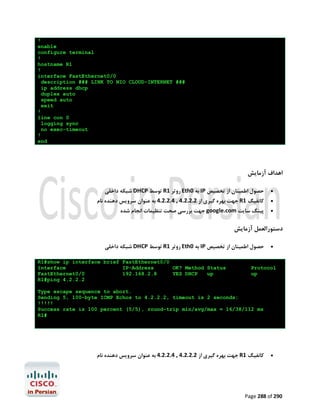
![R1#configure terminal
Enter configuration commands, one per line.
R1(config)#ip name-server 4.2.2.2 4.2.2.4
R1(config)#end
R1#
End with CNTL/Z.
ﺟﻬﺖ ﺑﺮرﺳﯽ ﺻﺤﺖ ﺗﻨﻈﯿﻤﺎت اﻧﺠﺎم ﺷﺪهgoogle.com ﭘﯿﻨﮓ ﺳﺎﯾﺖ
R1#ping google.com
Translating "google.com"...domain server (192.168.2.1) [OK]
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 72.14.204.104, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 24/35/56 ms
R1#
Page 289 of 290
](https://image.slidesharecdn.com/ccnalabinpersian-140126034115-phpapp02/85/CCNA-laboratory-in-persian-290-320.jpg)