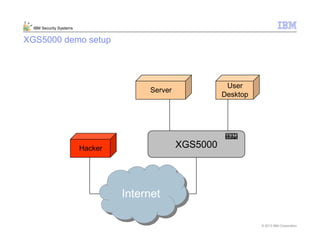
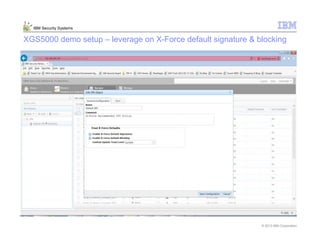
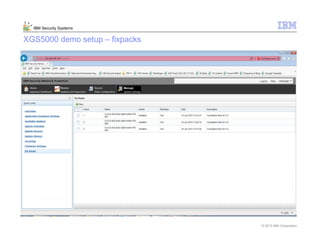
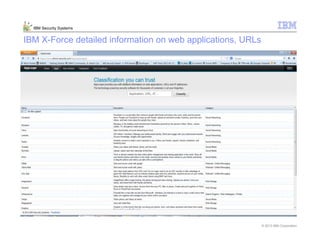
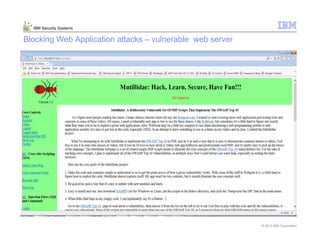
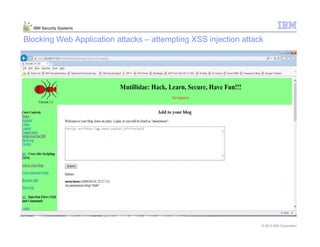
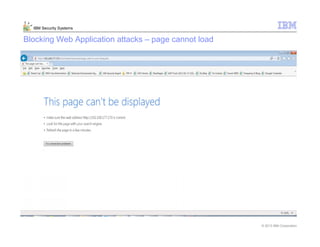
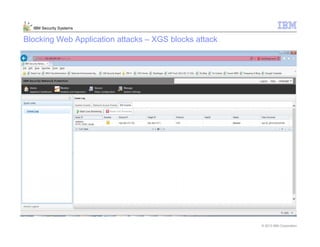
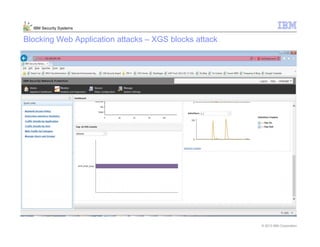
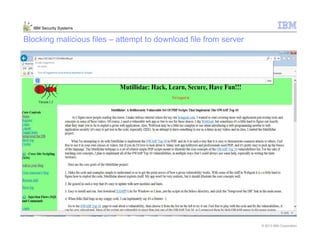
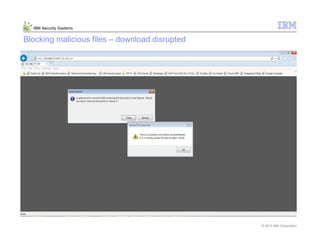
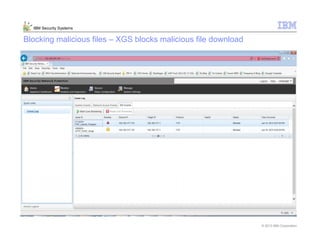
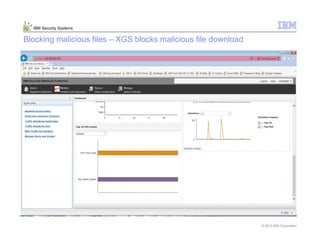
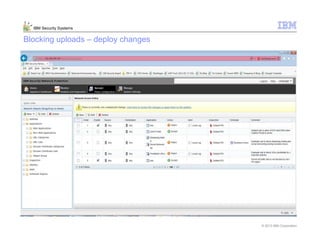
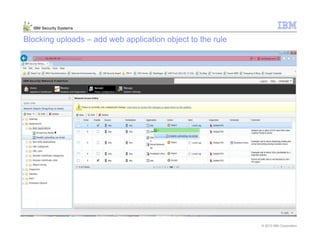
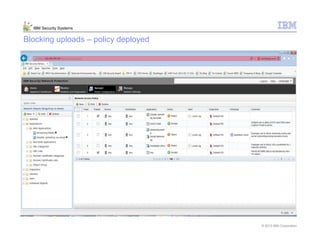
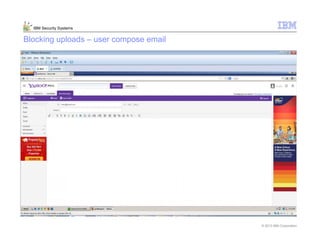
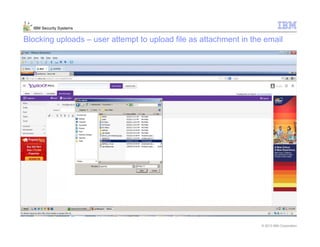
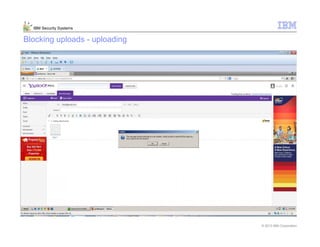
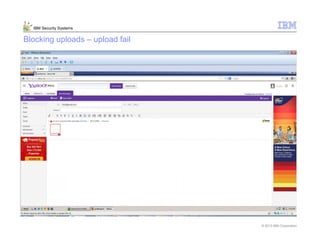
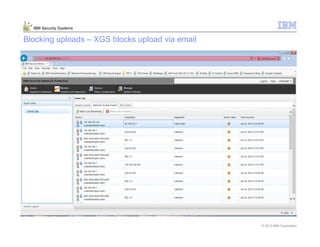
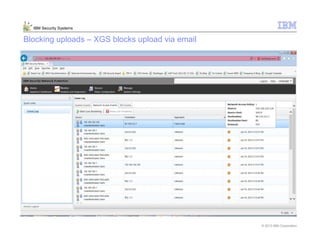
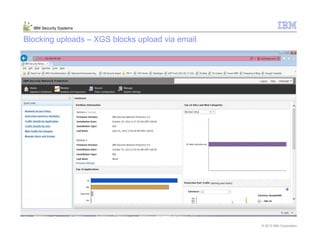
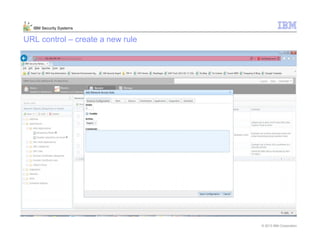
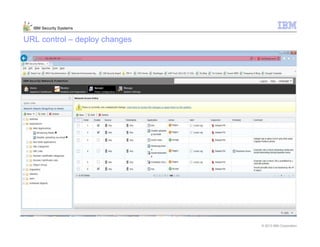
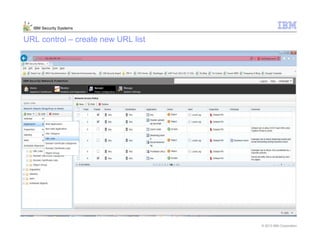
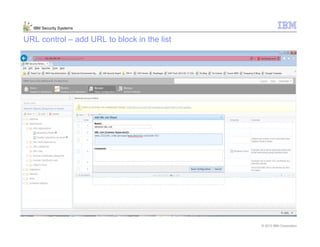
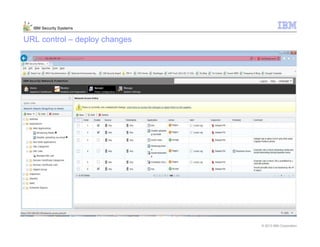
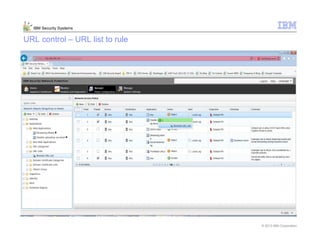
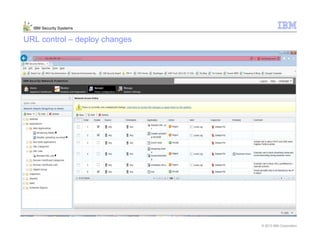
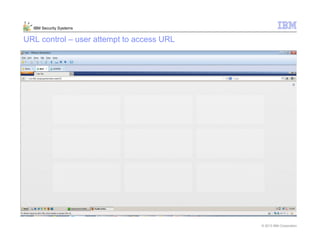
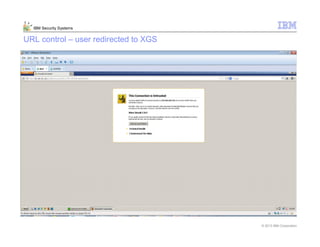
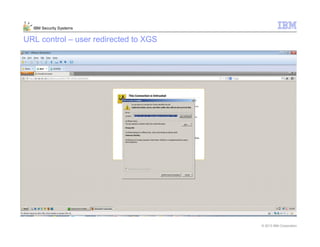
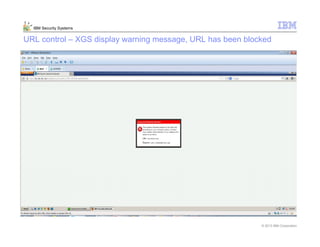
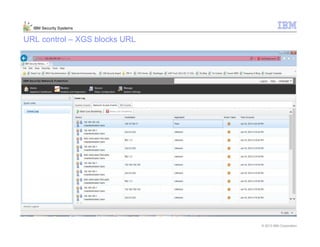
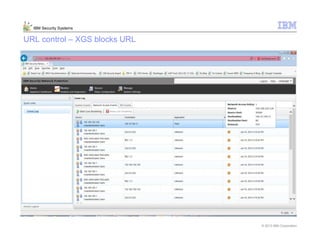
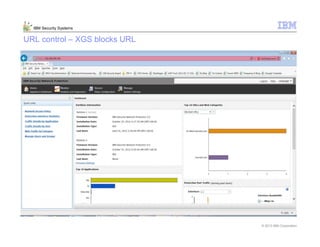
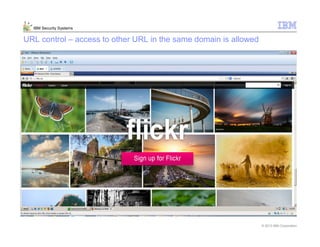
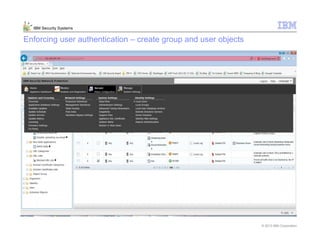
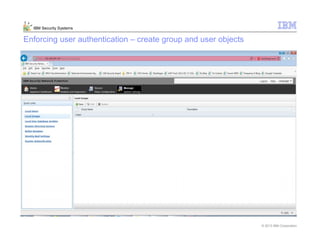
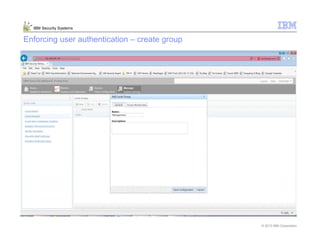
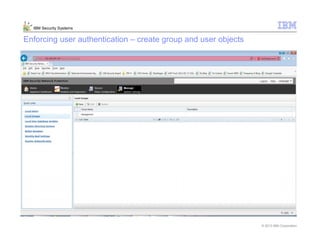
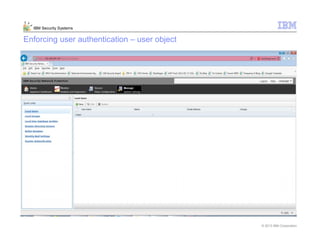
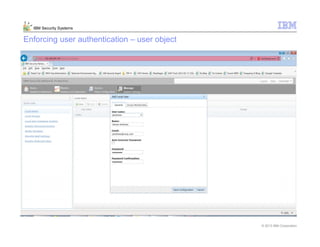
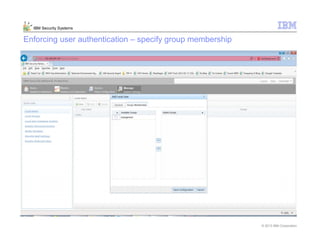
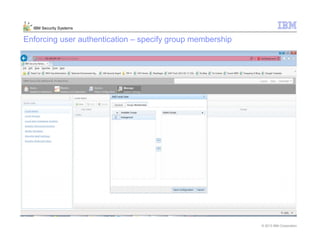
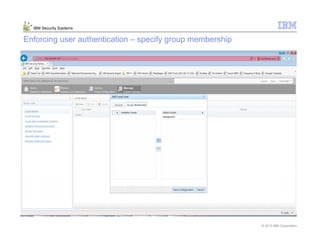
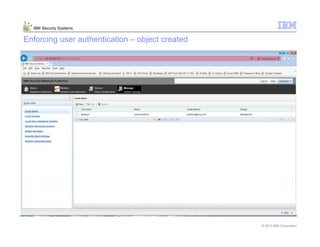
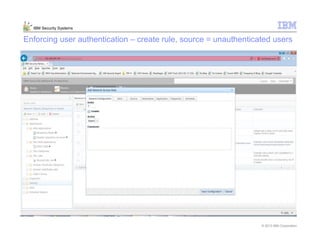
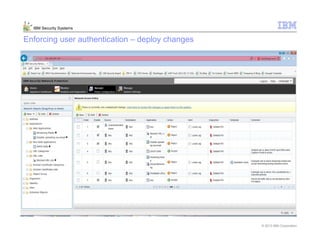
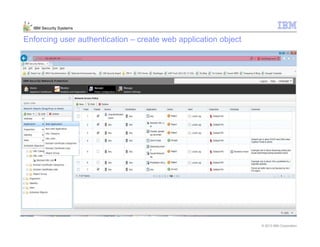
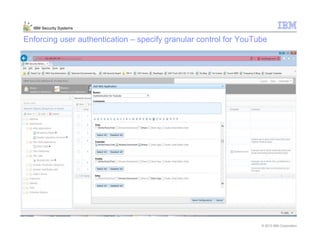
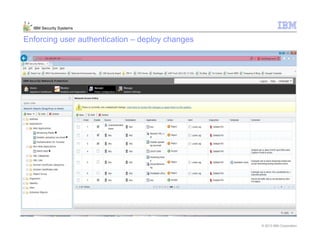
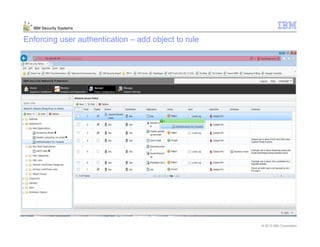
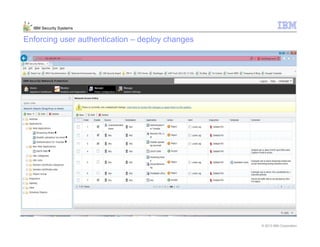
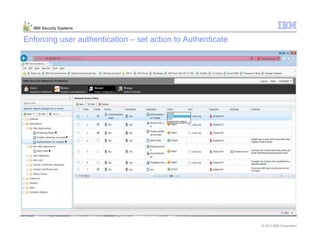
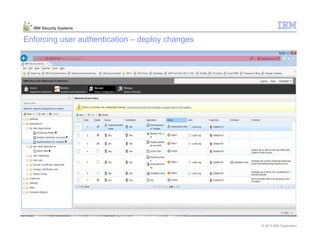
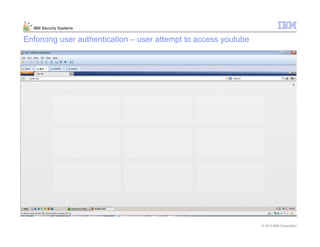
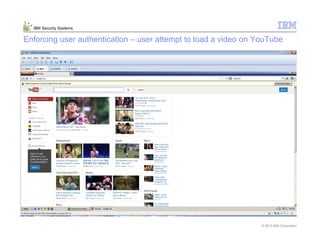
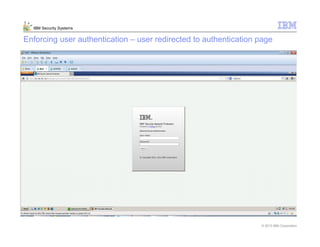
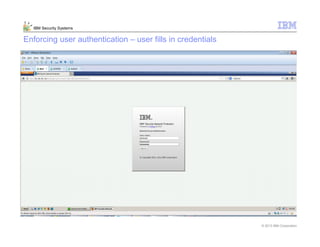
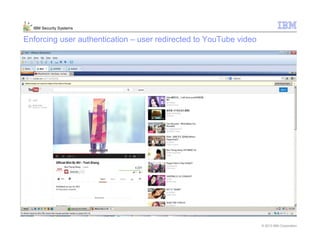
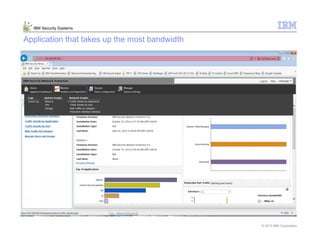
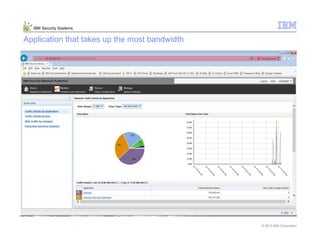
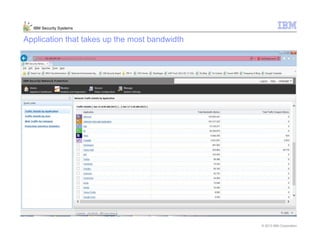
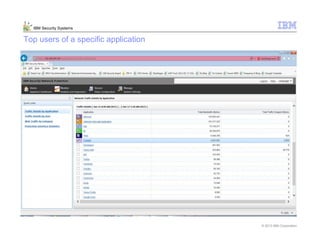
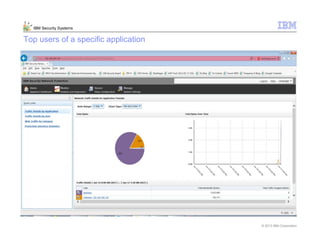
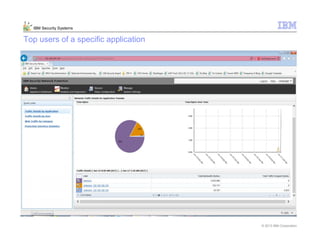
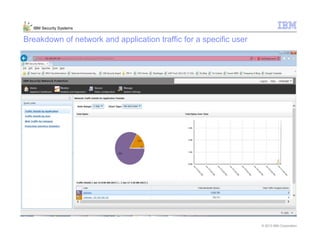
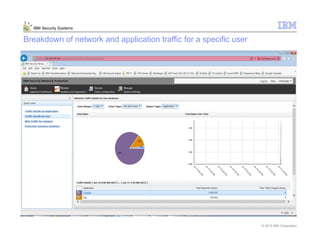
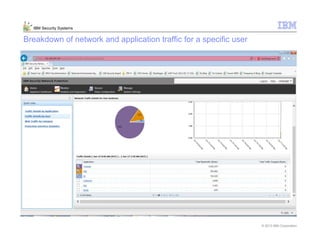
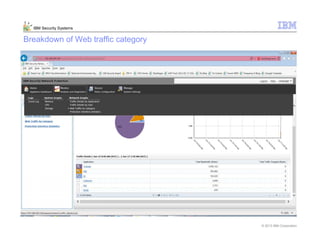
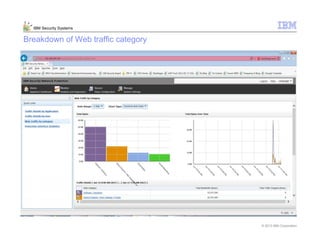
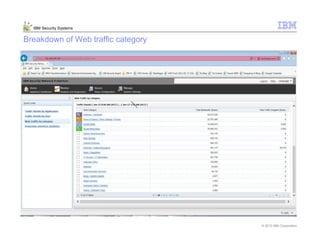
This document provides an overview and demonstration of the IBM Next Generation IPS (XGS5000). It describes setting up the XGS5000 demo including firmware, signatures, and fixpacks. It then outlines various test cases for the demo including blocking web application attacks, blocking malicious files, application control, URL control, enforcing user authentication, and identifying applications and users. Step-by-step instructions are provided for conducting demonstrations for each use case.