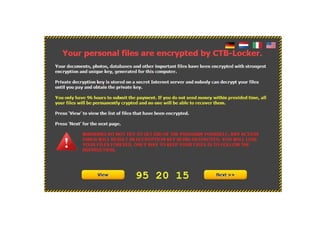
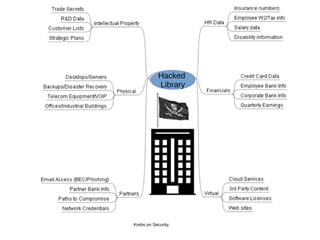
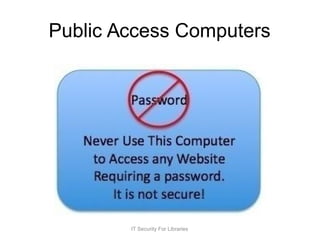
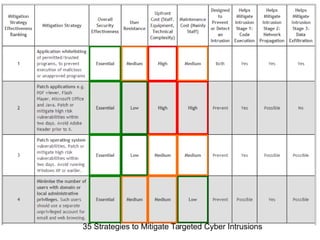
The document discusses IT security challenges faced by libraries, emphasizing that libraries often lack the resources for robust security measures. It highlights the importance of a defensible mindset, understanding vulnerabilities, and adopting effective threat modeling strategies. The document also stresses the need for ongoing training and awareness programs to foster a culture of security among staff and patrons.