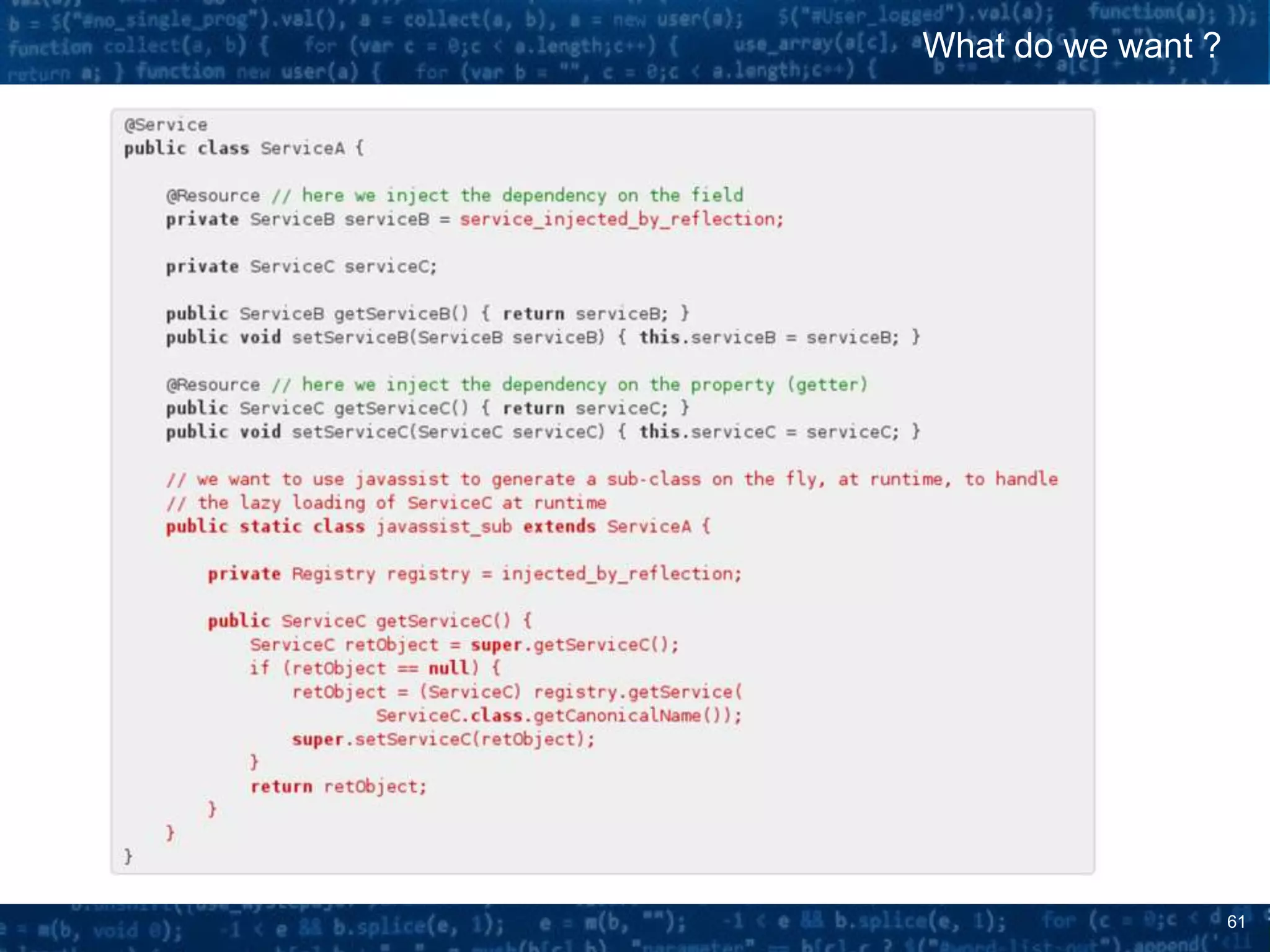
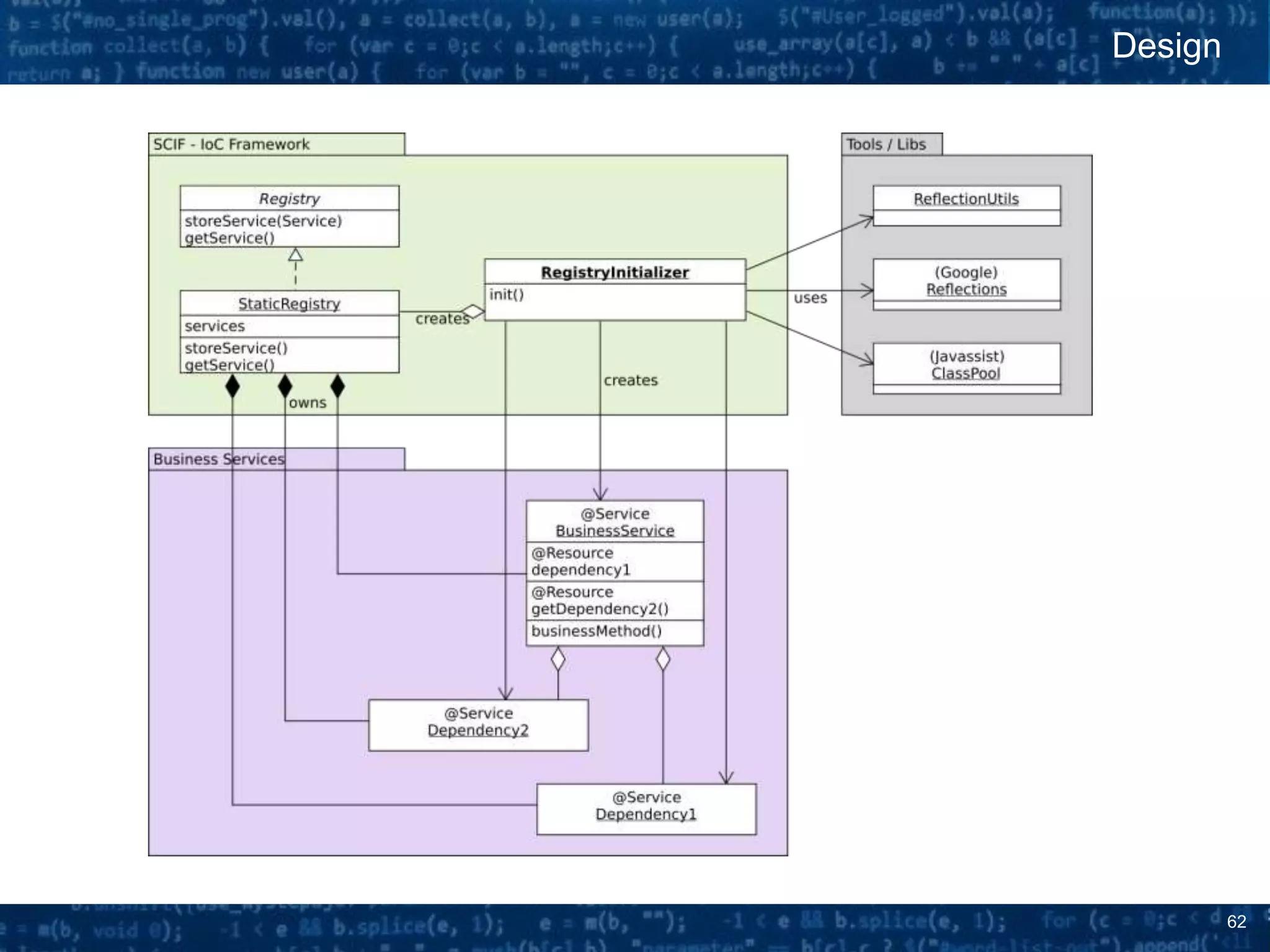
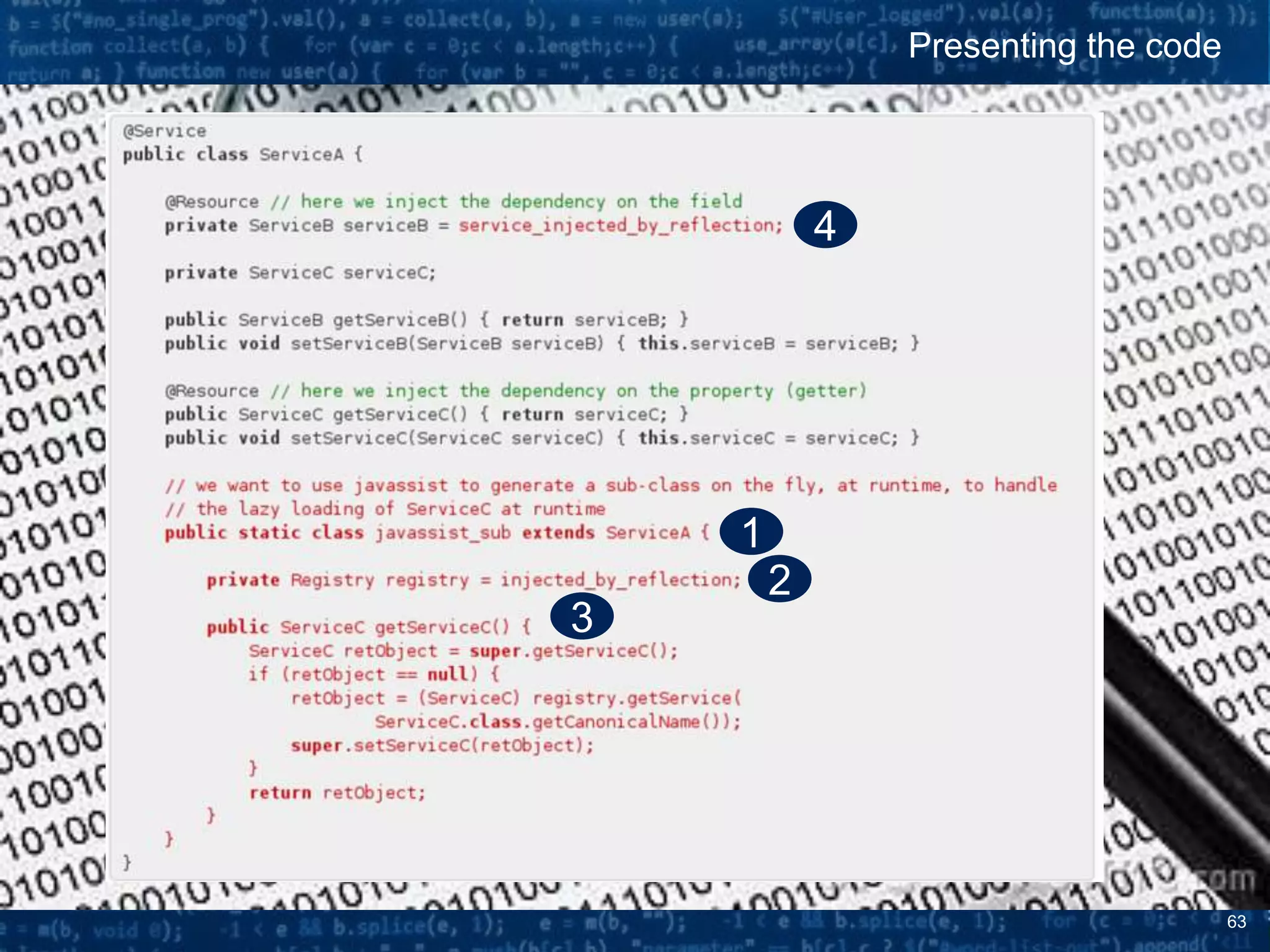
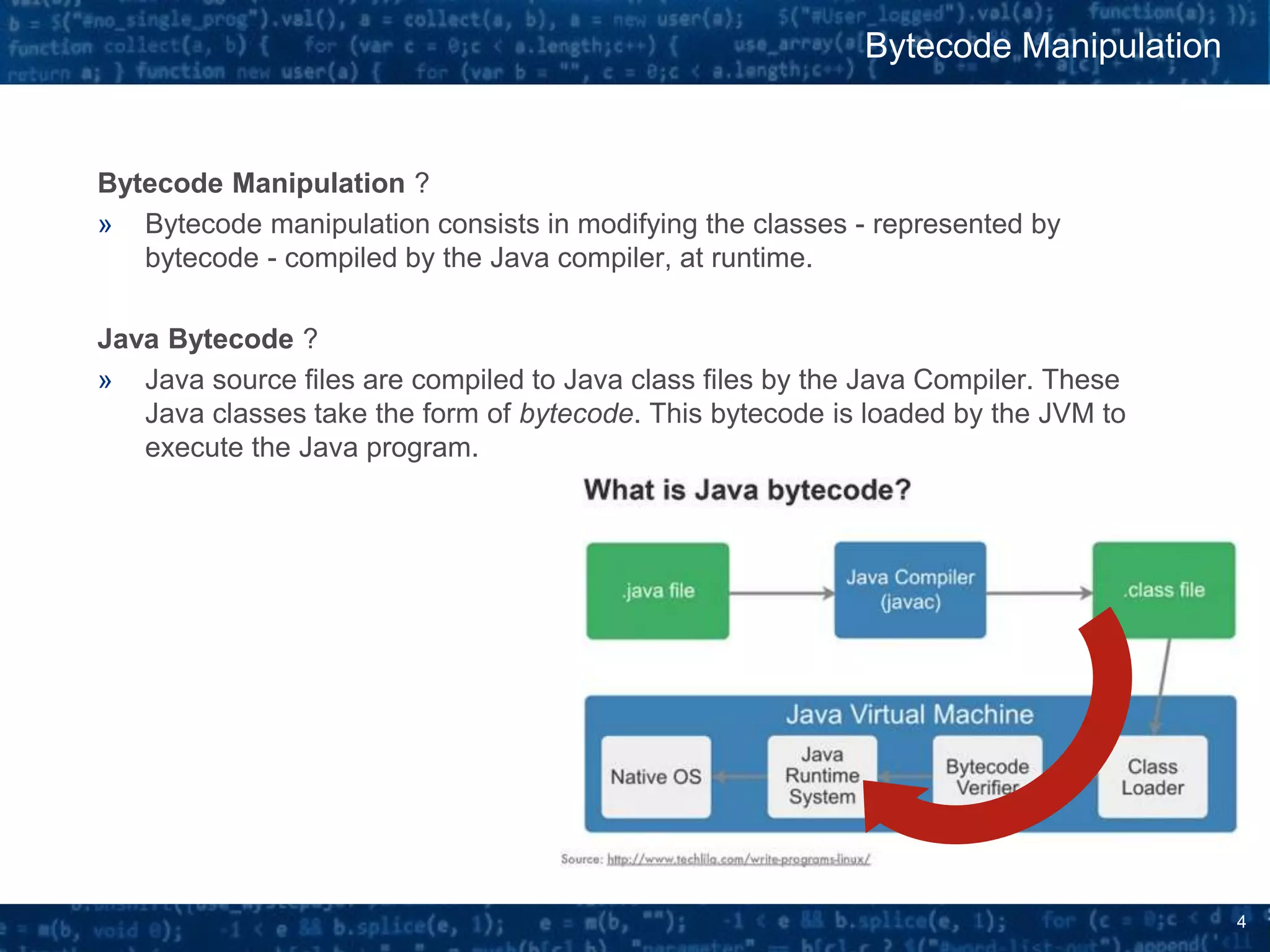
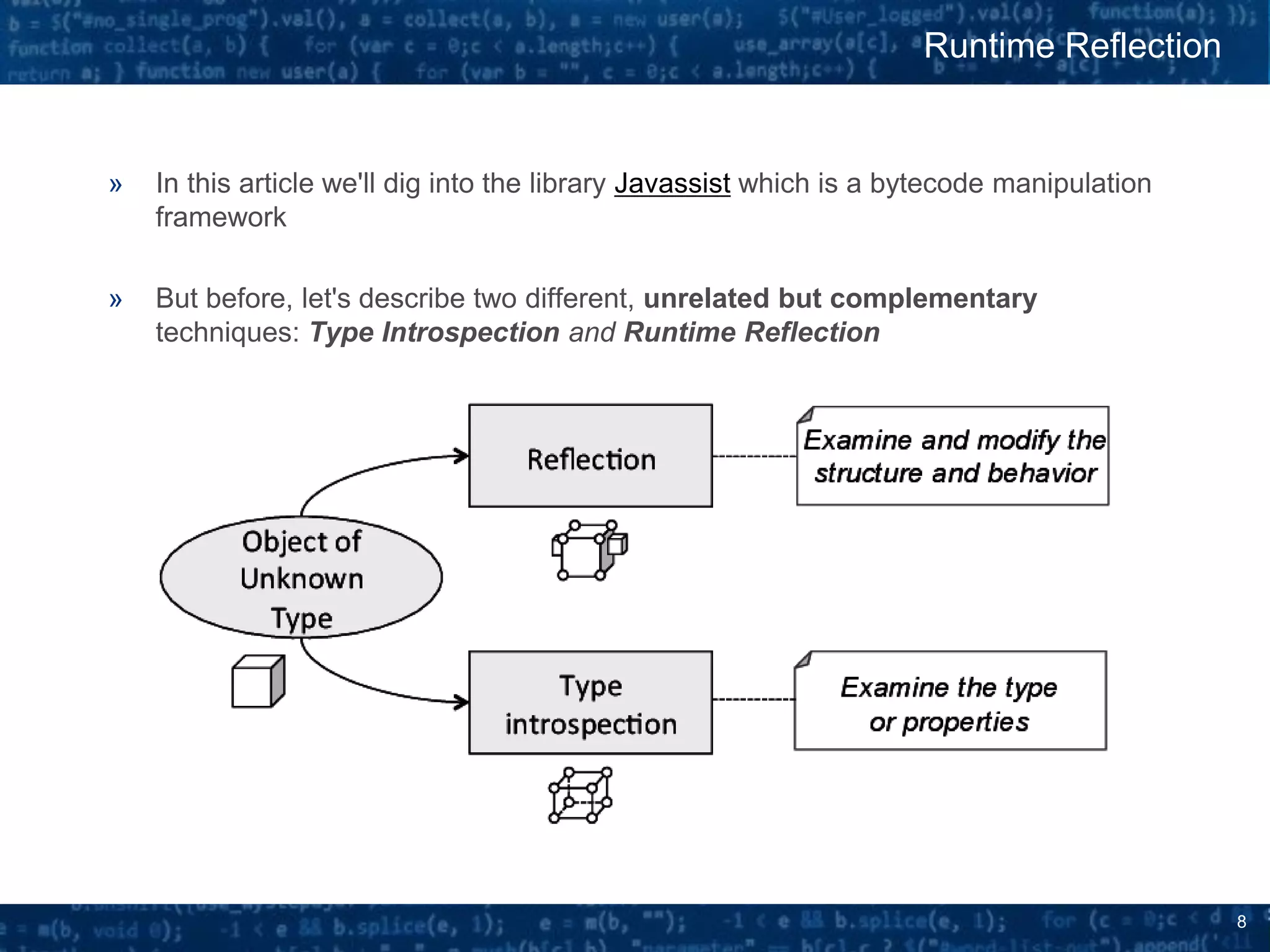
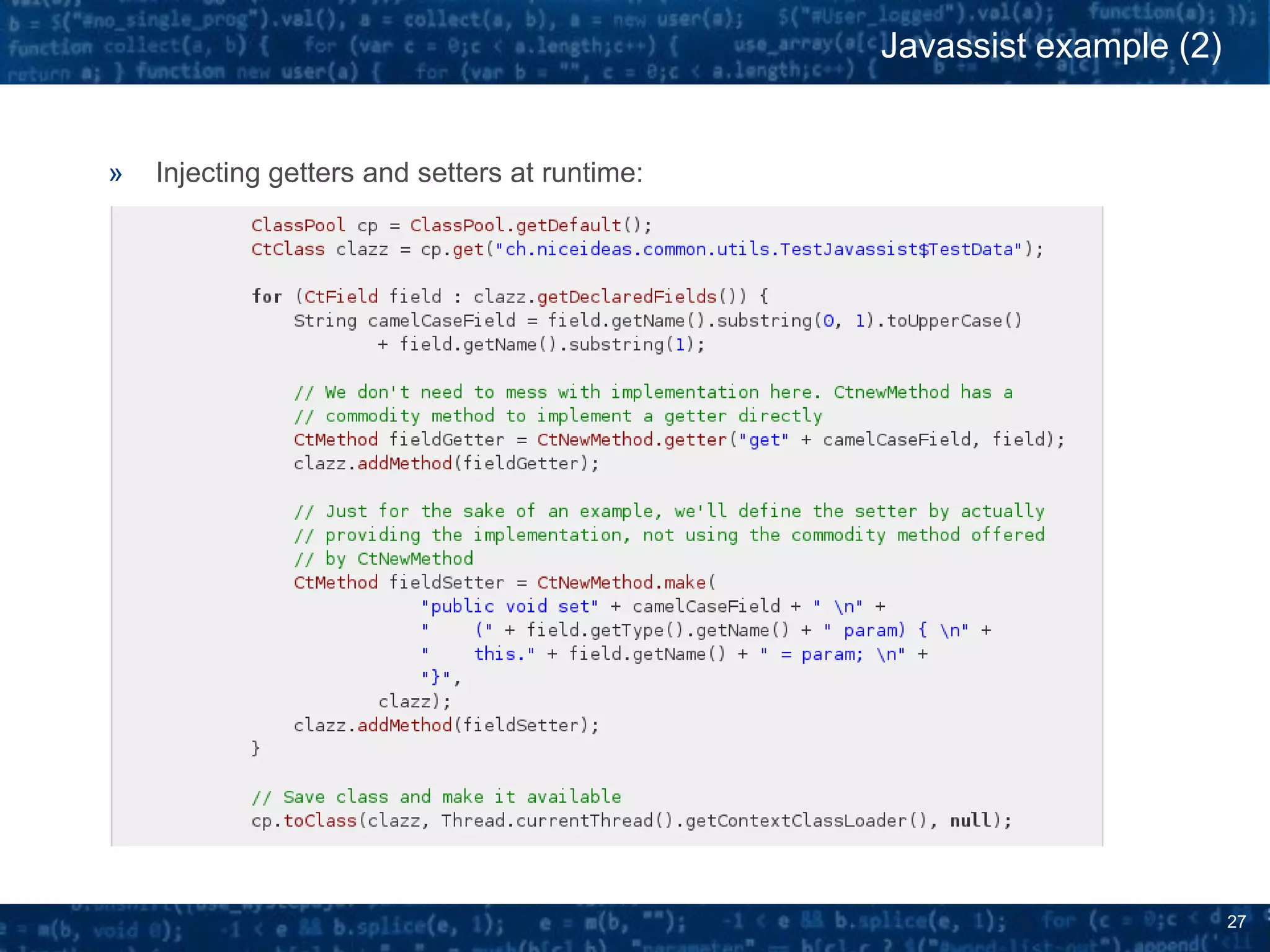
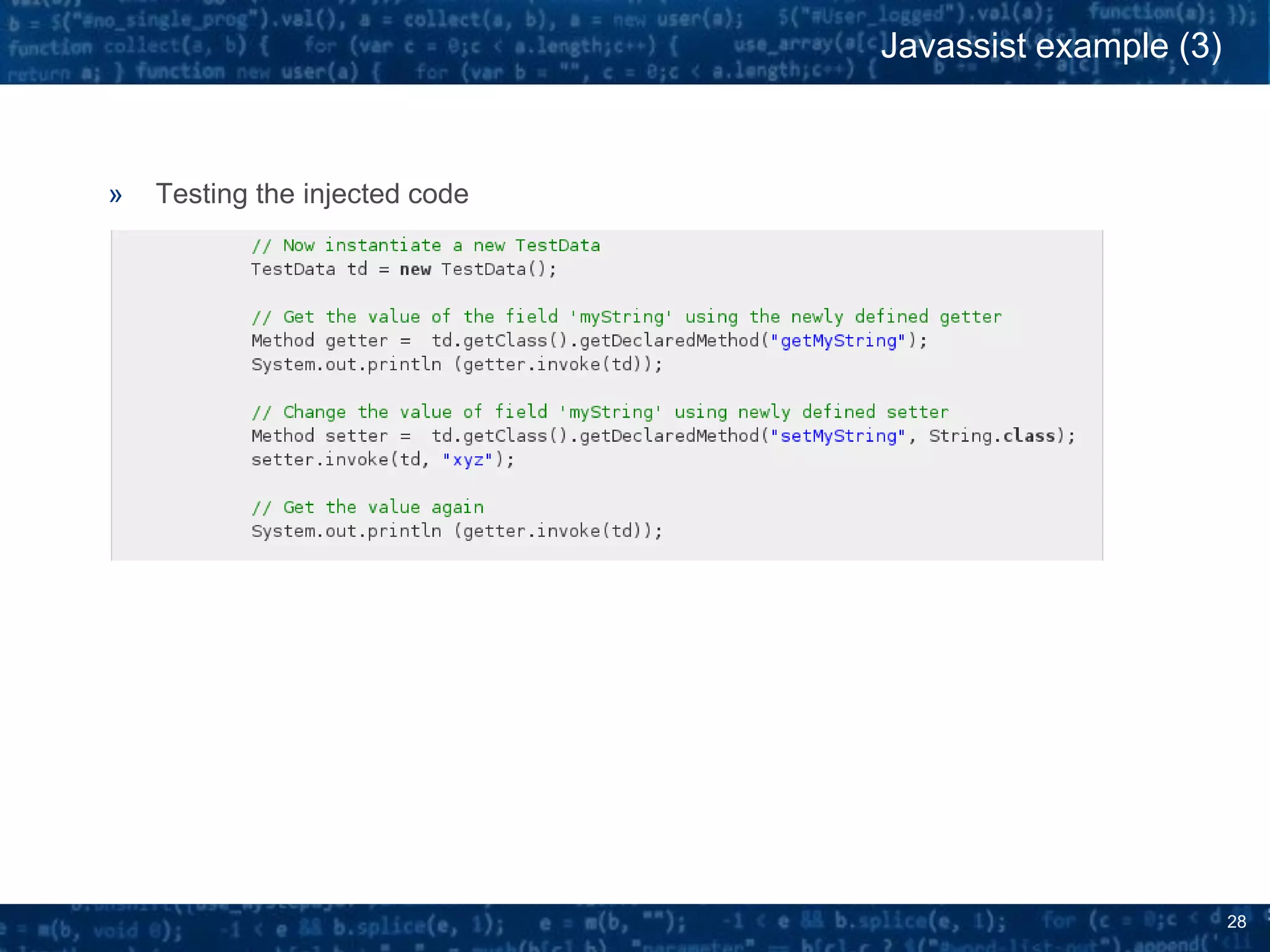
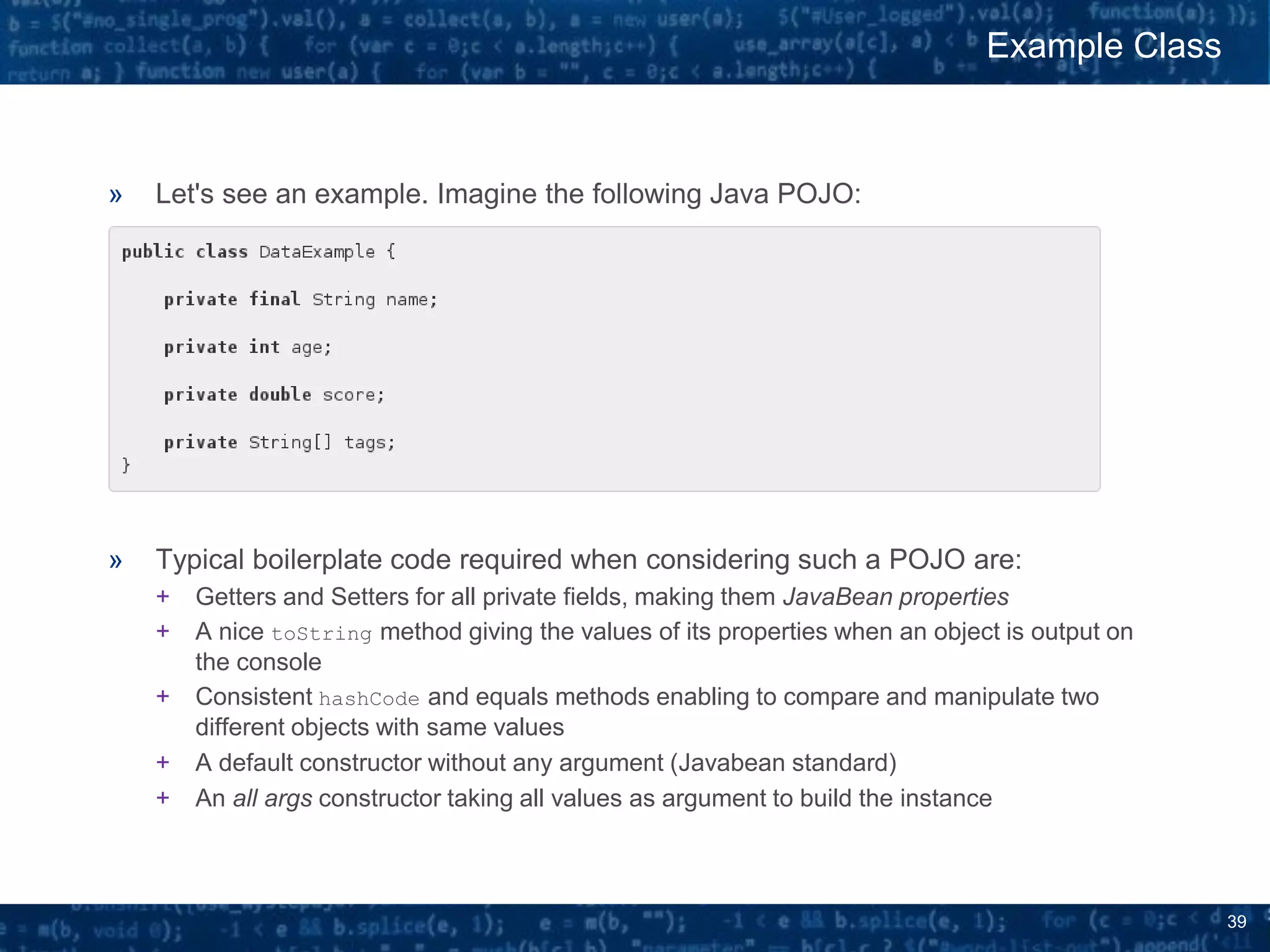
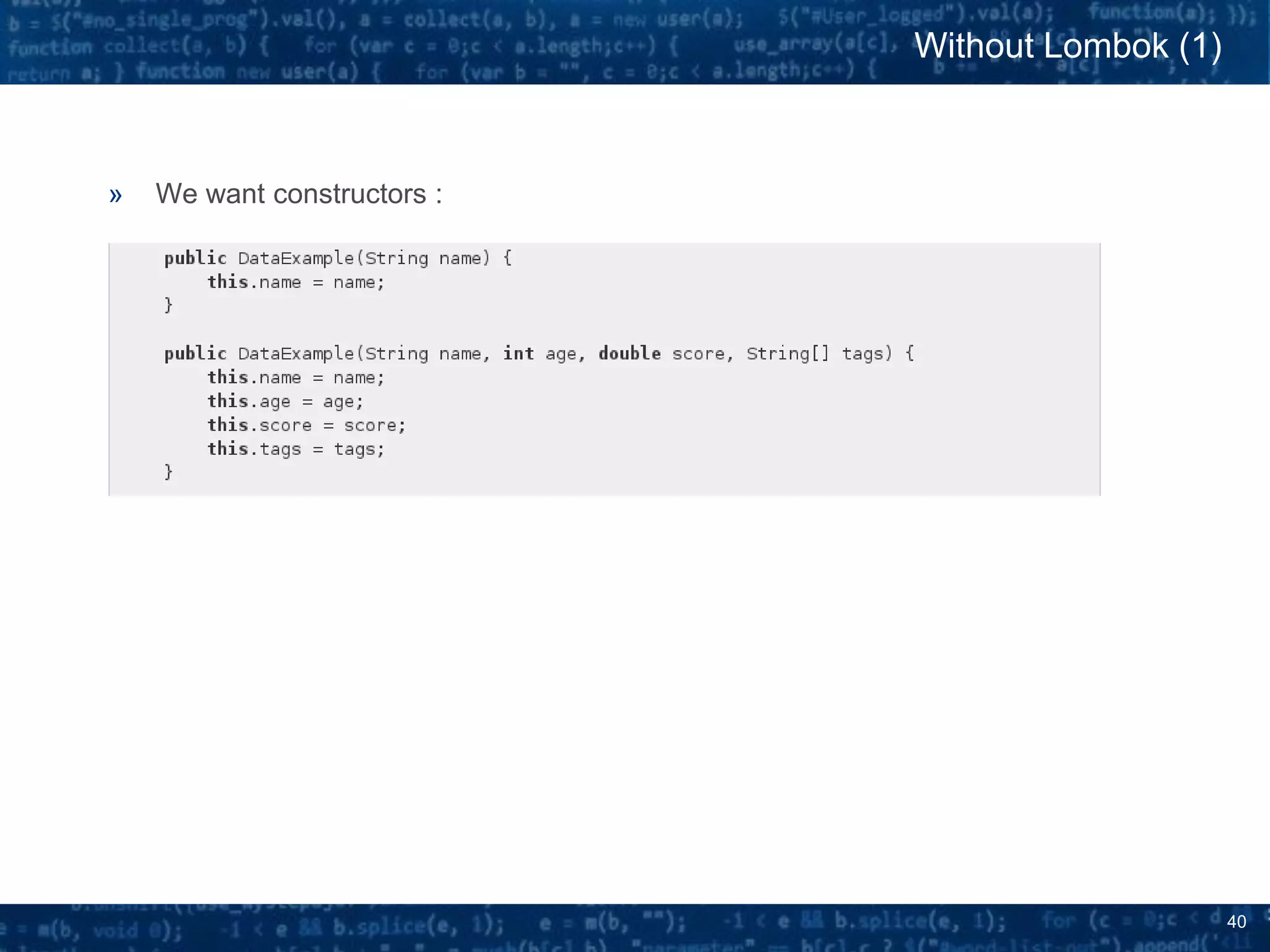
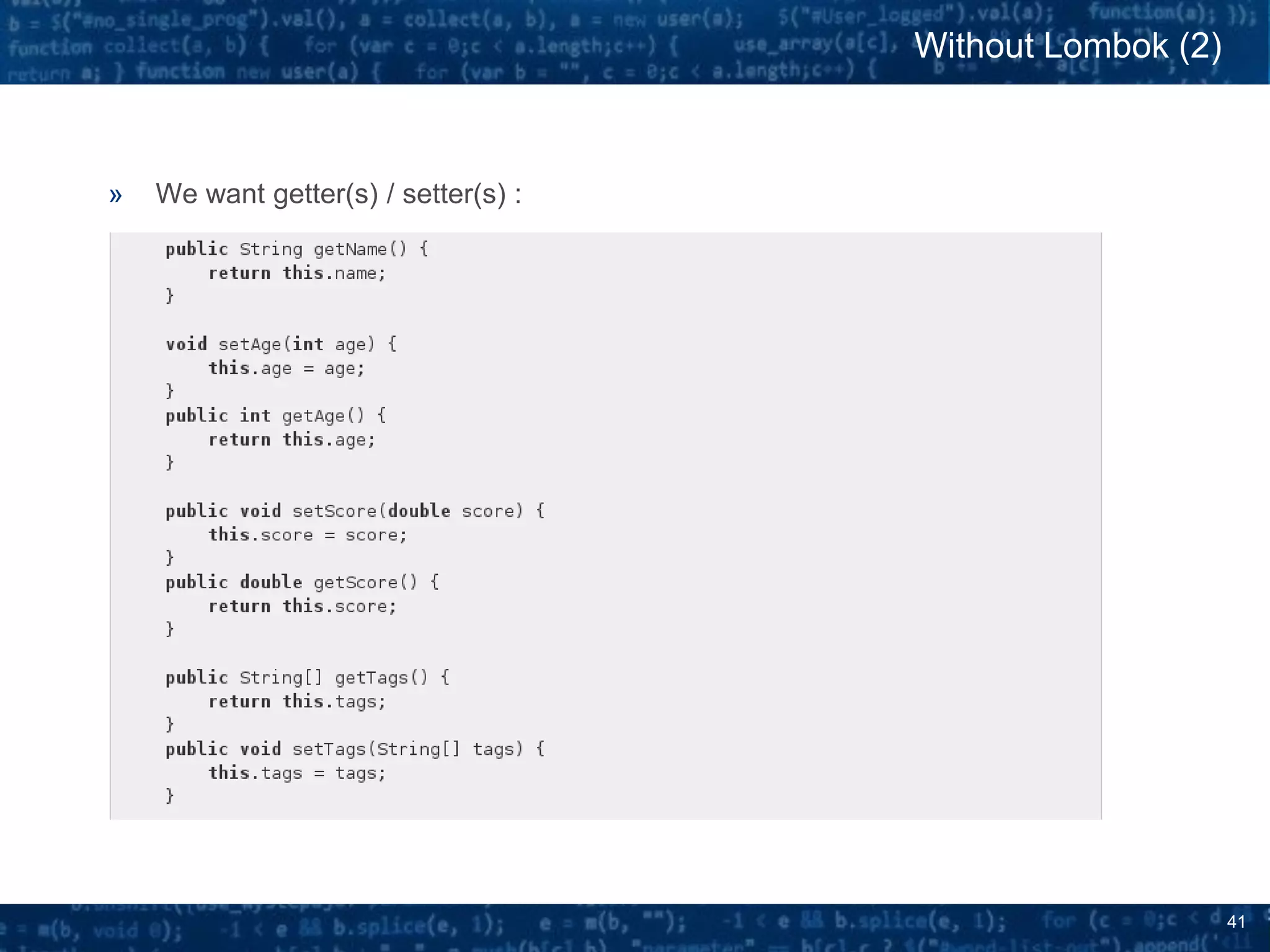
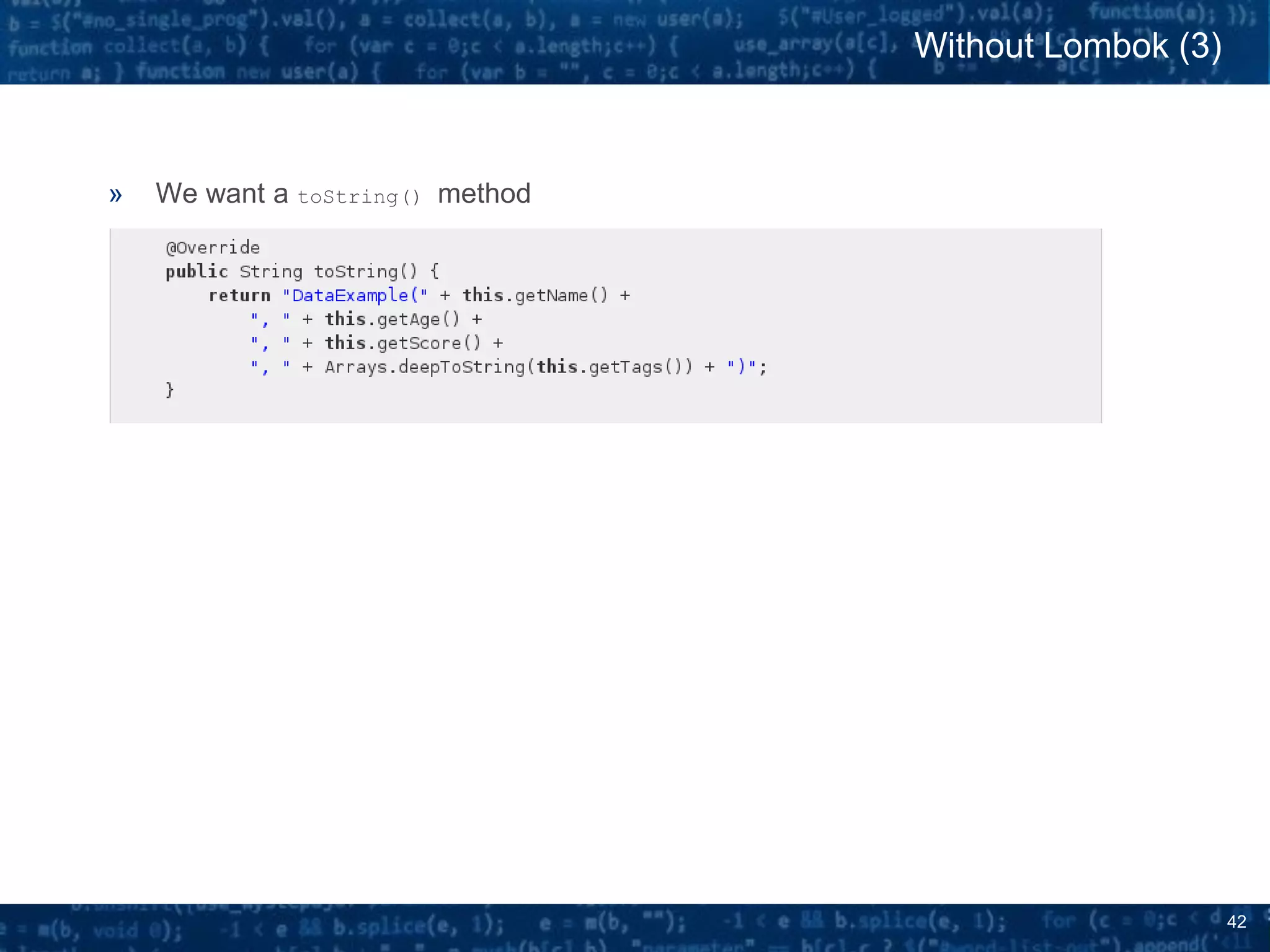
The document discusses bytecode manipulation in Java using the Javassist library, emphasizing its simplicity and efficiency for developers. It covers techniques like type introspection and runtime reflection, outlines typical use cases, and introduces Java agents that allow for runtime modifications to bytecode. Two specific use cases are presented: boilerplate code generation with Project Lombok and creating a simple lightweight IoC container.




![19
+ to define a new class at runtime and
+ to modify a class file at loading time
» The Linkage problem !
+ Once a class has already been
loaded, changing it would result in a
Linkage Error (unless the JVM is
launched with the JPDA [Java
Platform Debugger Architecture]
enabled, which would make a class
dynamically reloadable).
+ Interestingly, Javasssist is perfectly
able to modify a class long after the
application has started as long as
that specific class has not been
loaded.
Runtime vs. Loading Time
Loading
Time
Runtime](https://image.slidesharecdn.com/javassist-170427213300/75/Bytecode-manipulation-with-Javassist-for-fun-and-profit-19-2048.jpg)


![33
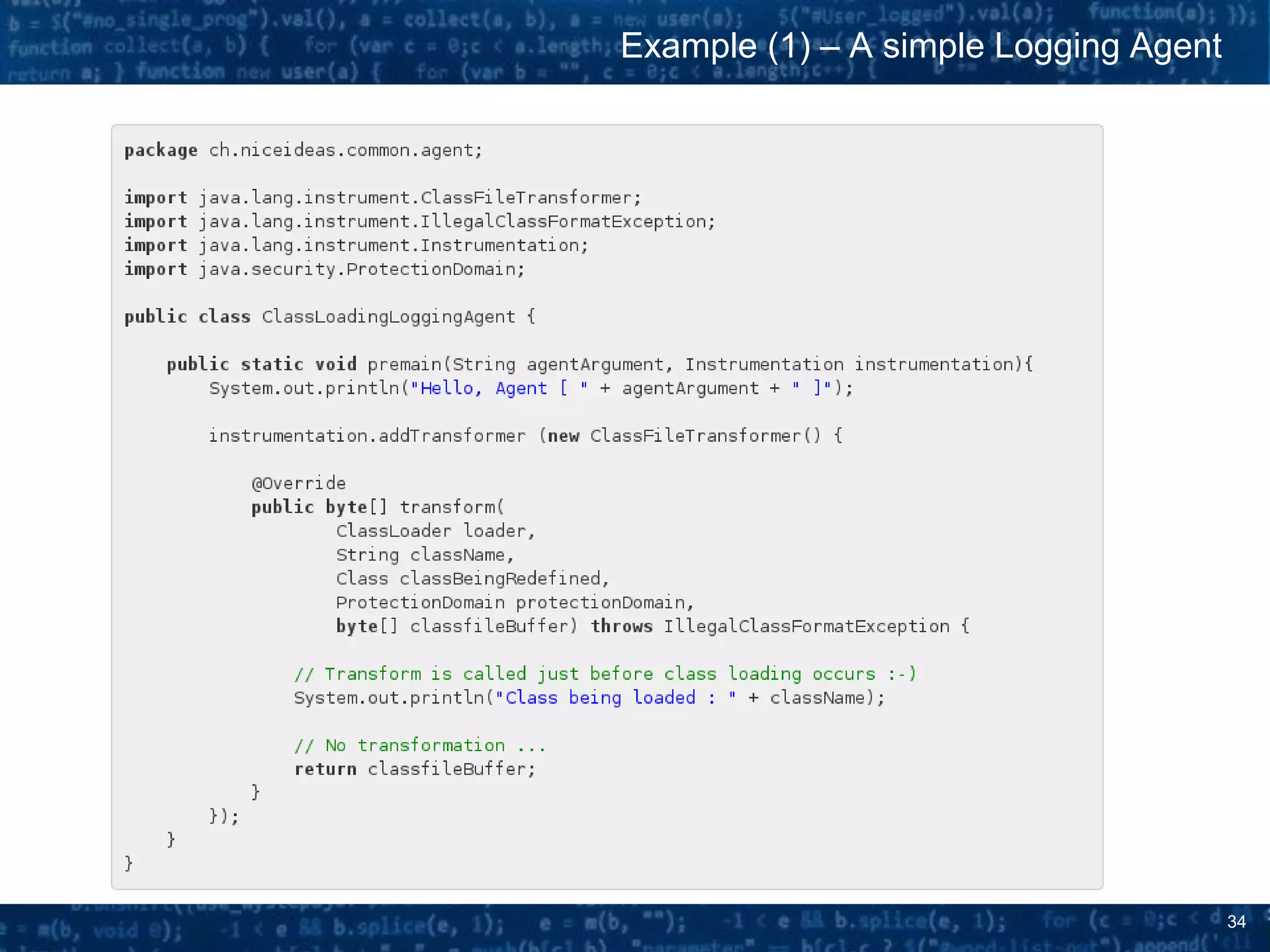
» A Java agent premain method takes the Instrumentation entry point -
class java.lang.instrument.Instrumentation - as argument.
» The most important API of the java.lang.instrument.Instrumentation class
is the method void addTransformer(ClassFileTransformer transformer);
» The ClassFileTransformer
interface defines one single
method
byte[] transform(byte[] …)
that is responsible to apply
transformations to a class being
loaded.
» The transform(...) method is
called for each and every class
being loaded by a classloader.
Behaviour of Agents](https://image.slidesharecdn.com/javassist-170427213300/75/Bytecode-manipulation-with-Javassist-for-fun-and-profit-33-2048.jpg)
![35
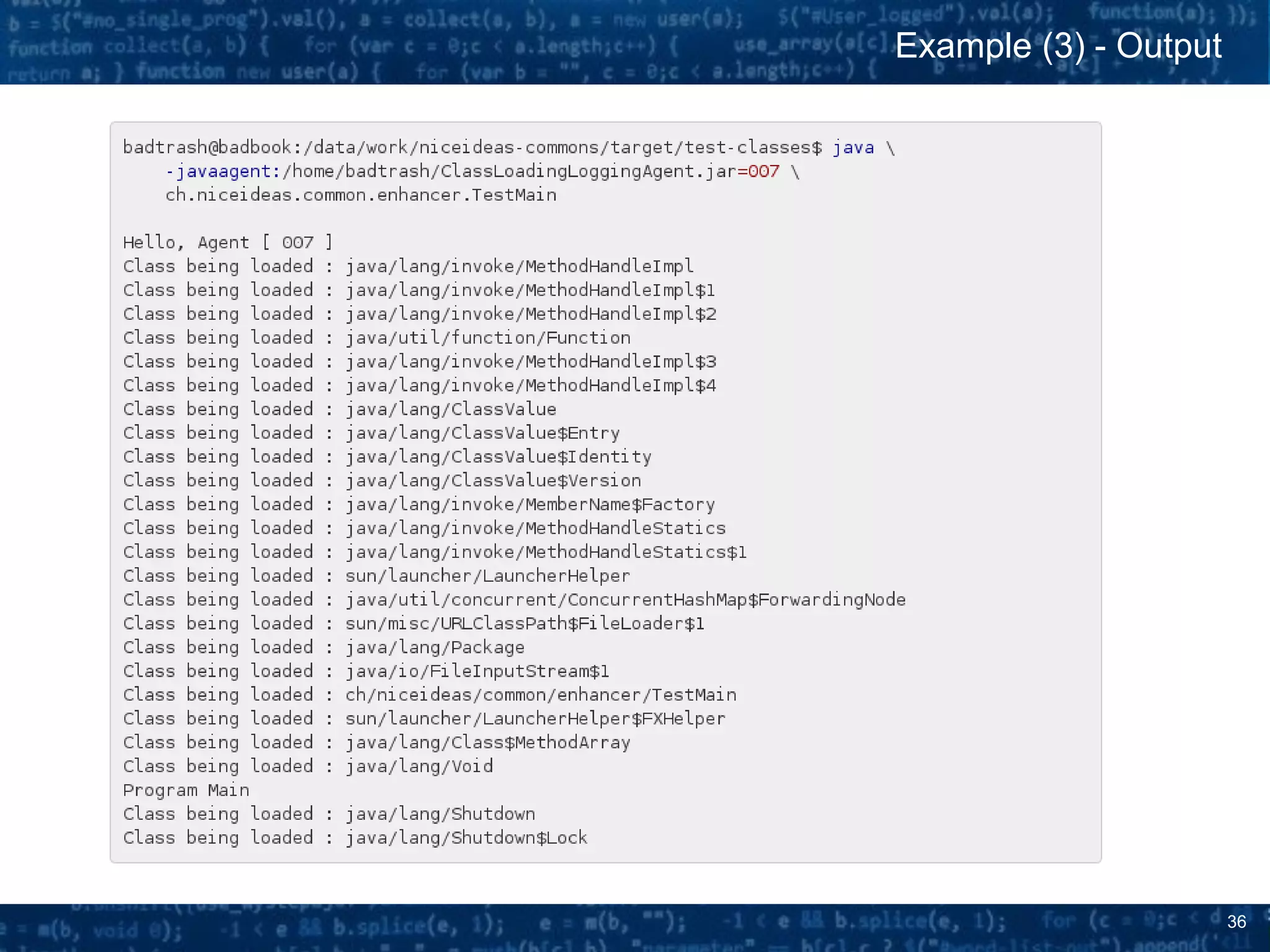
» When running from the command line, the Java agent could be passed to JVM
instance using -javaagent argument which has following semantic -
javaagent:<path-to-jar>[=options].
» A java agent needs to be packaged in a jar file and that jar file needs to have a
specific and proper MANIFEST.MF file indicating the class containing
the premain method.
» A proper manifest file for the agent above should be packaged within the jar
archive containing the agent classes under META-INF/MANIFEST.MF and would
be as follows:
» Now let's imagine we invoke our agent on a simple program defined as follows:
Example (2) - Packaging](https://image.slidesharecdn.com/javassist-170427213300/75/Bytecode-manipulation-with-Javassist-for-fun-and-profit-35-2048.jpg)

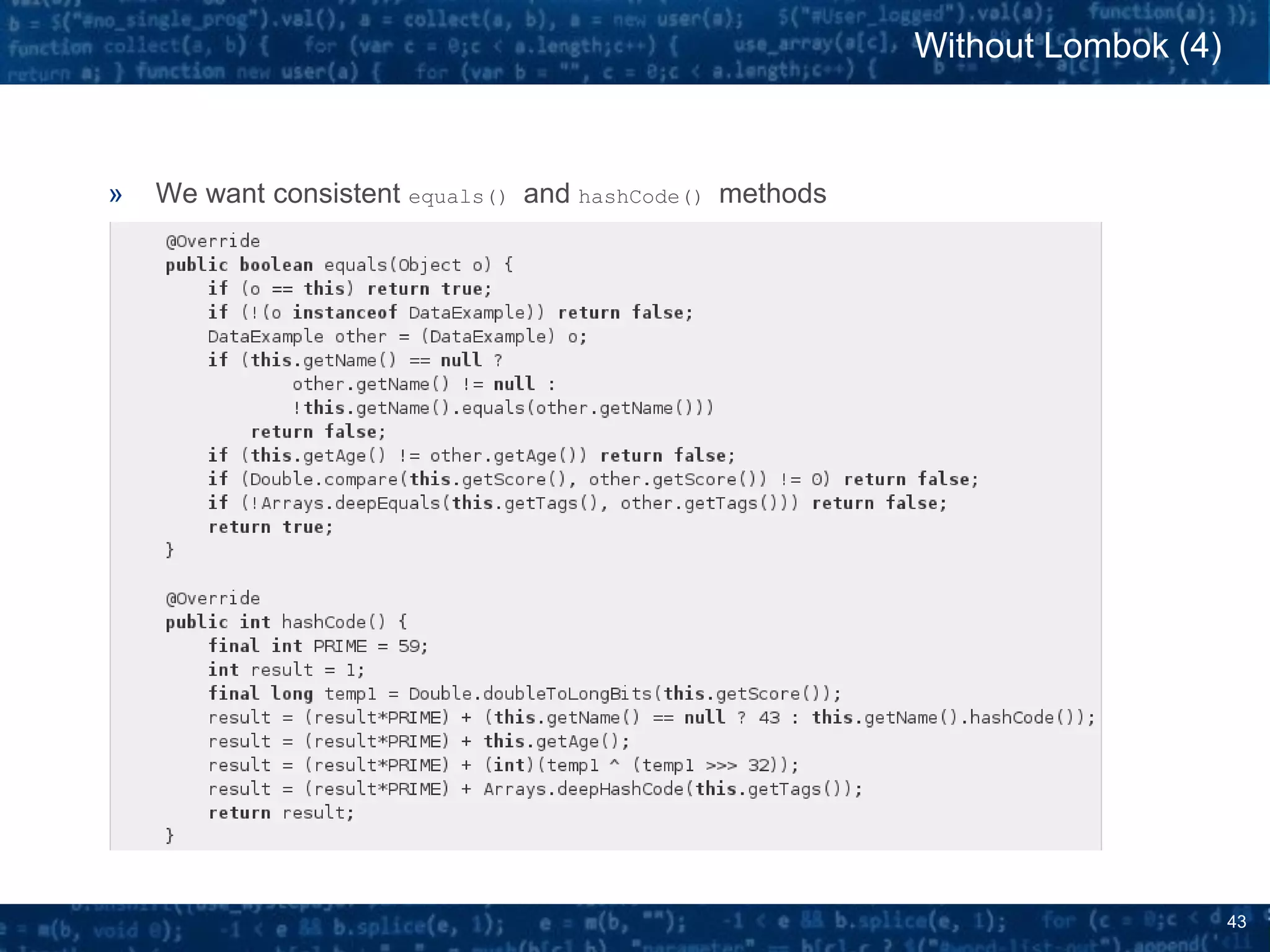
![44
» No added value : an IDE can write this code for you !
» ratio of [Boilerplate code / Useful Code] of more than 1200% !
Without Lombok (5)
5 lines of code
4 fields
Initial Class
60 lines of code
4 fields
2 constructors
10 methods
Without Lombok](https://image.slidesharecdn.com/javassist-170427213300/75/Bytecode-manipulation-with-Javassist-for-fun-and-profit-44-2048.jpg)
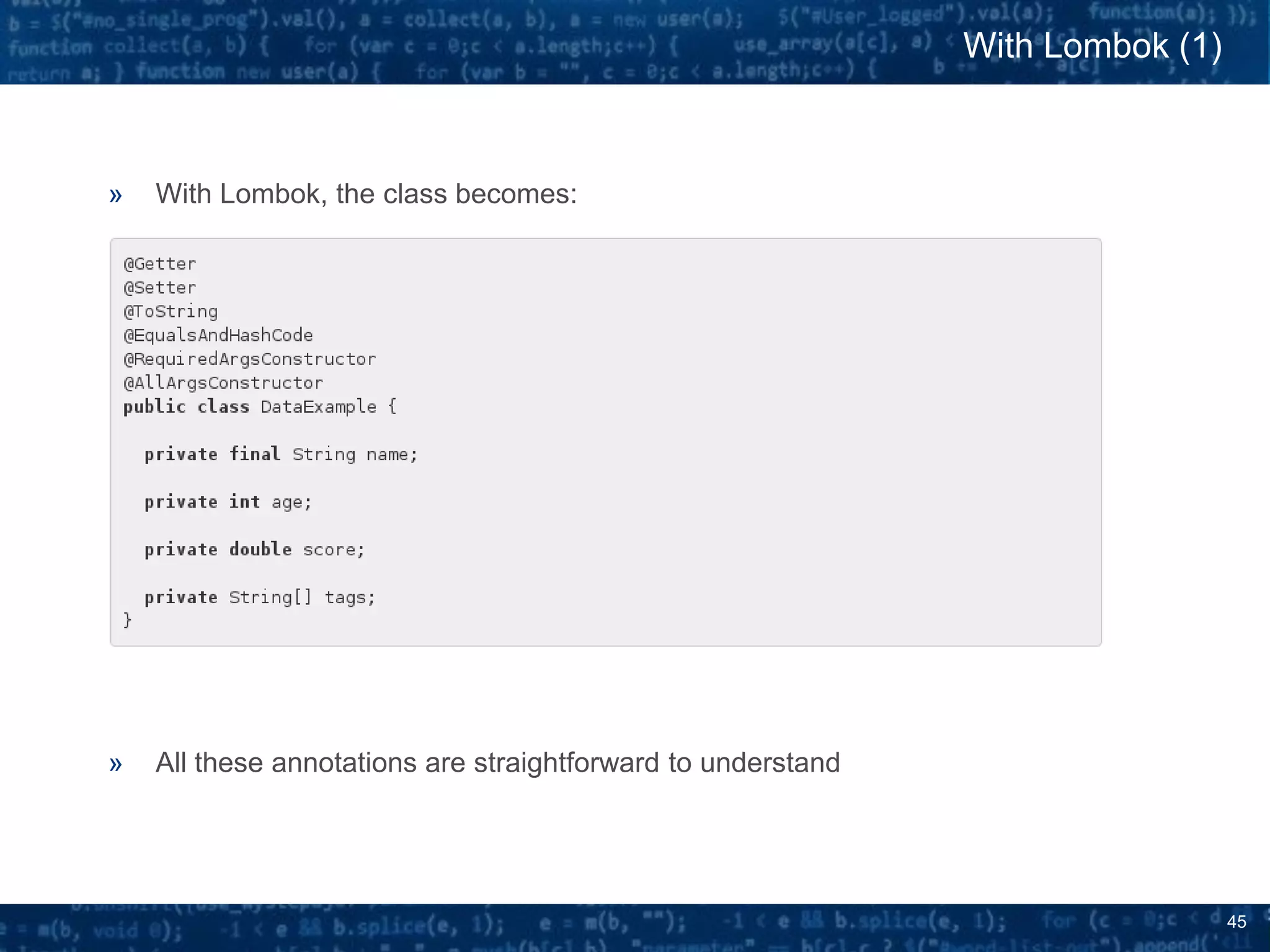
![46
» Thanks to AST Transformation approach, really behaves as if all this boilerplate
code was actually written !
» Much better ratio of [Boilerplate code / Useful Code]
With Lombok (2)
5 lines of code
4 fields
Initial Class
10 lines of code
4 fields
5 annotations
With Lombok](https://image.slidesharecdn.com/javassist-170427213300/75/Bytecode-manipulation-with-Javassist-for-fun-and-profit-46-2048.jpg)