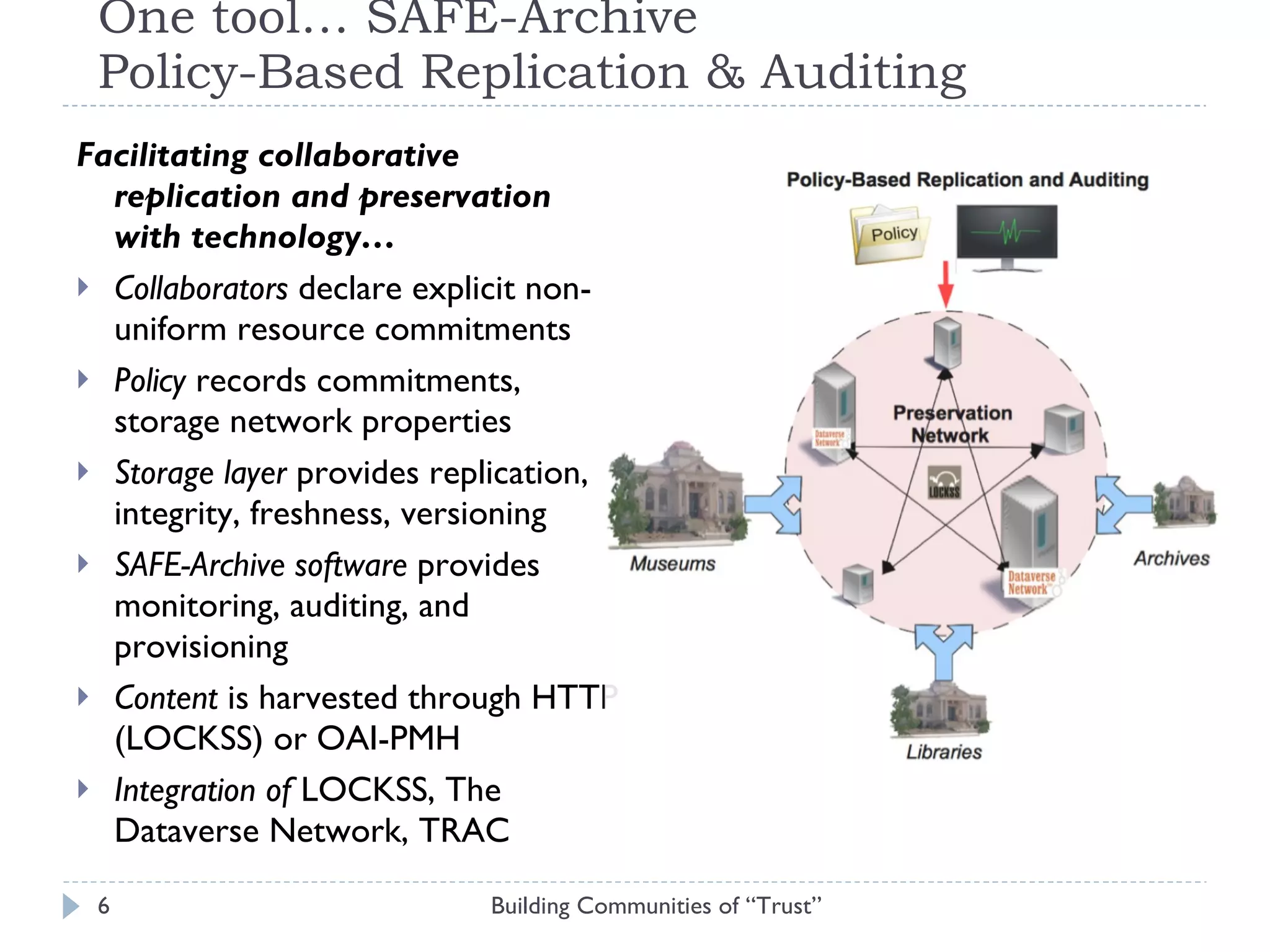
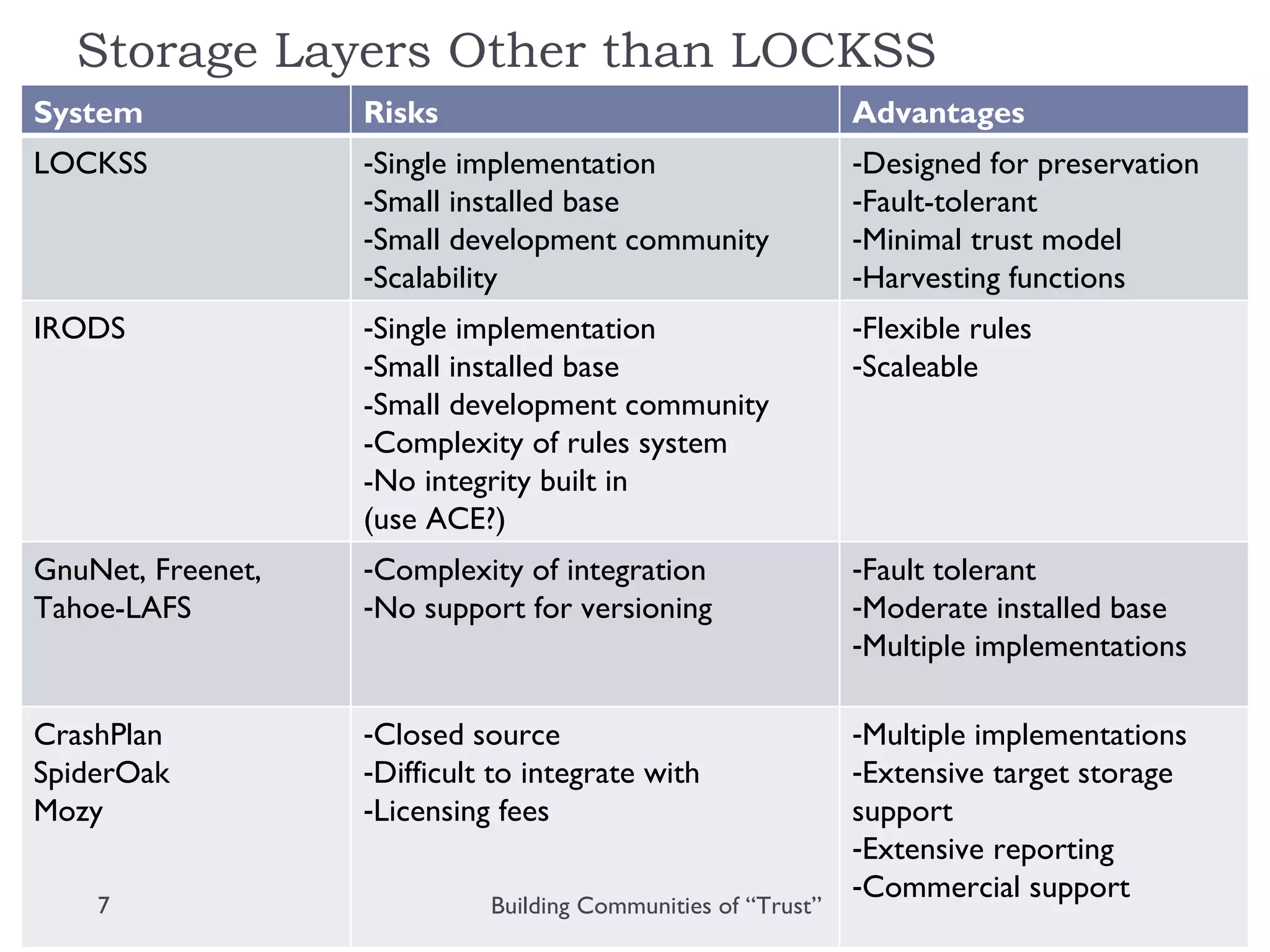
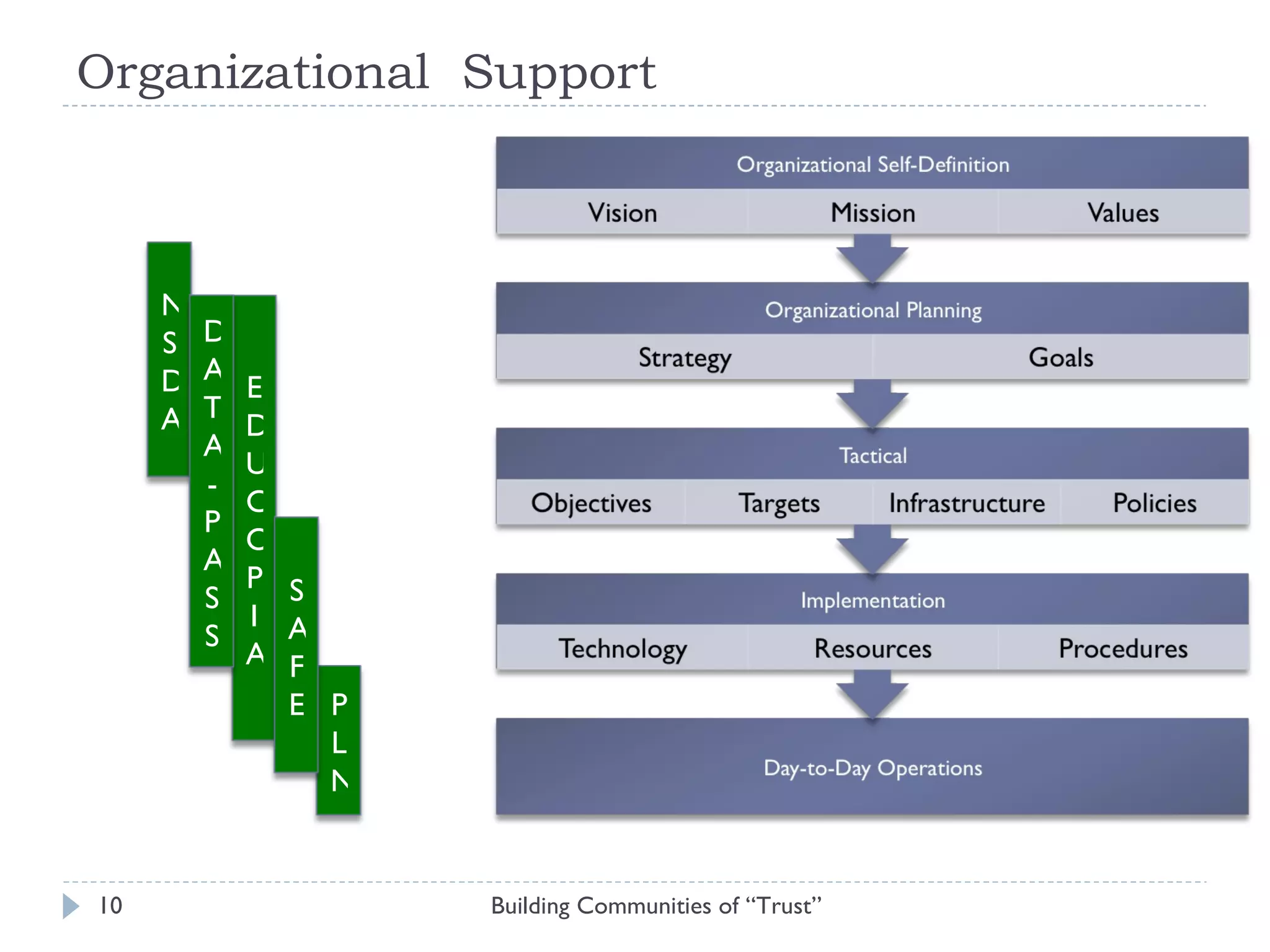
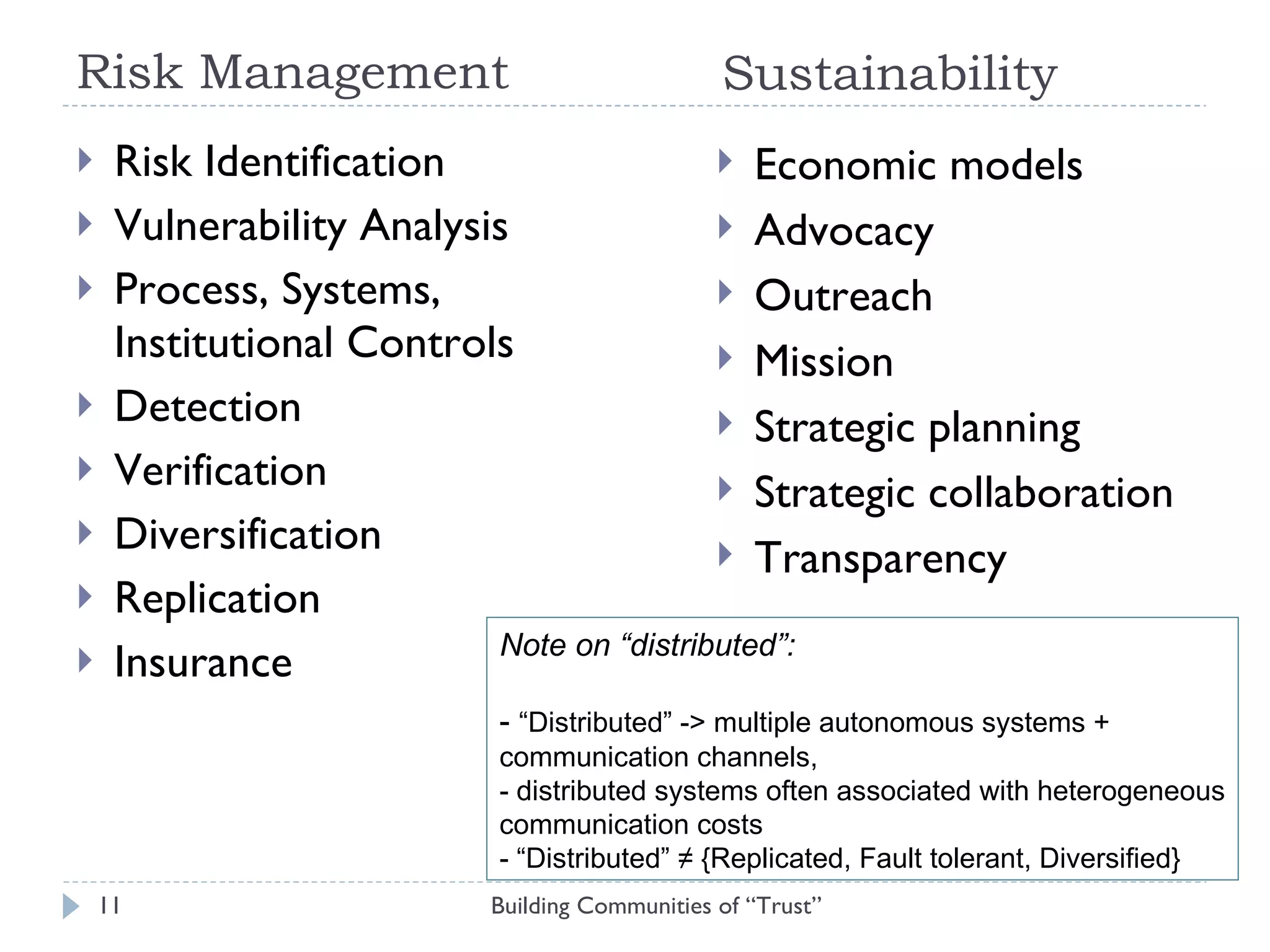
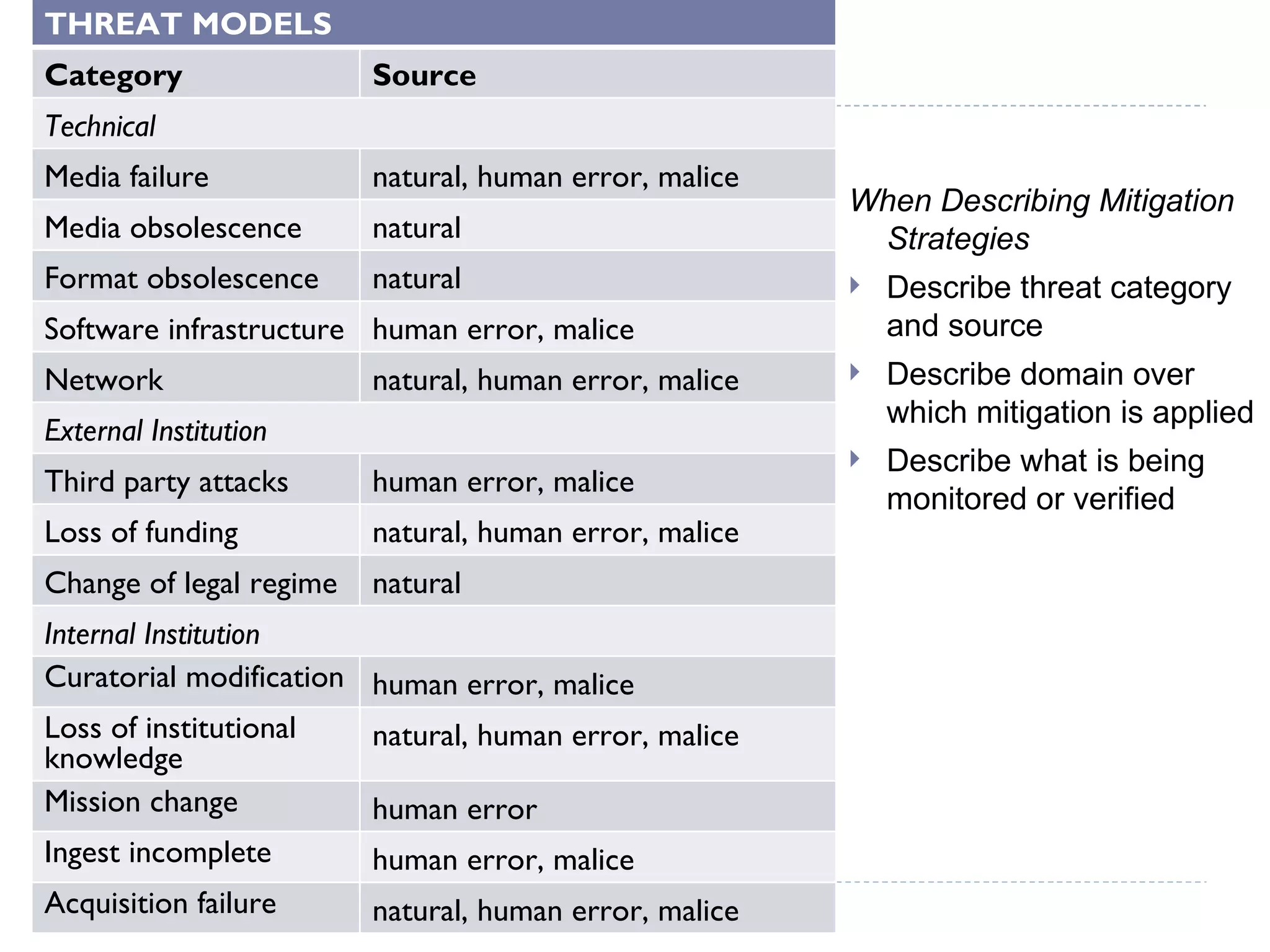
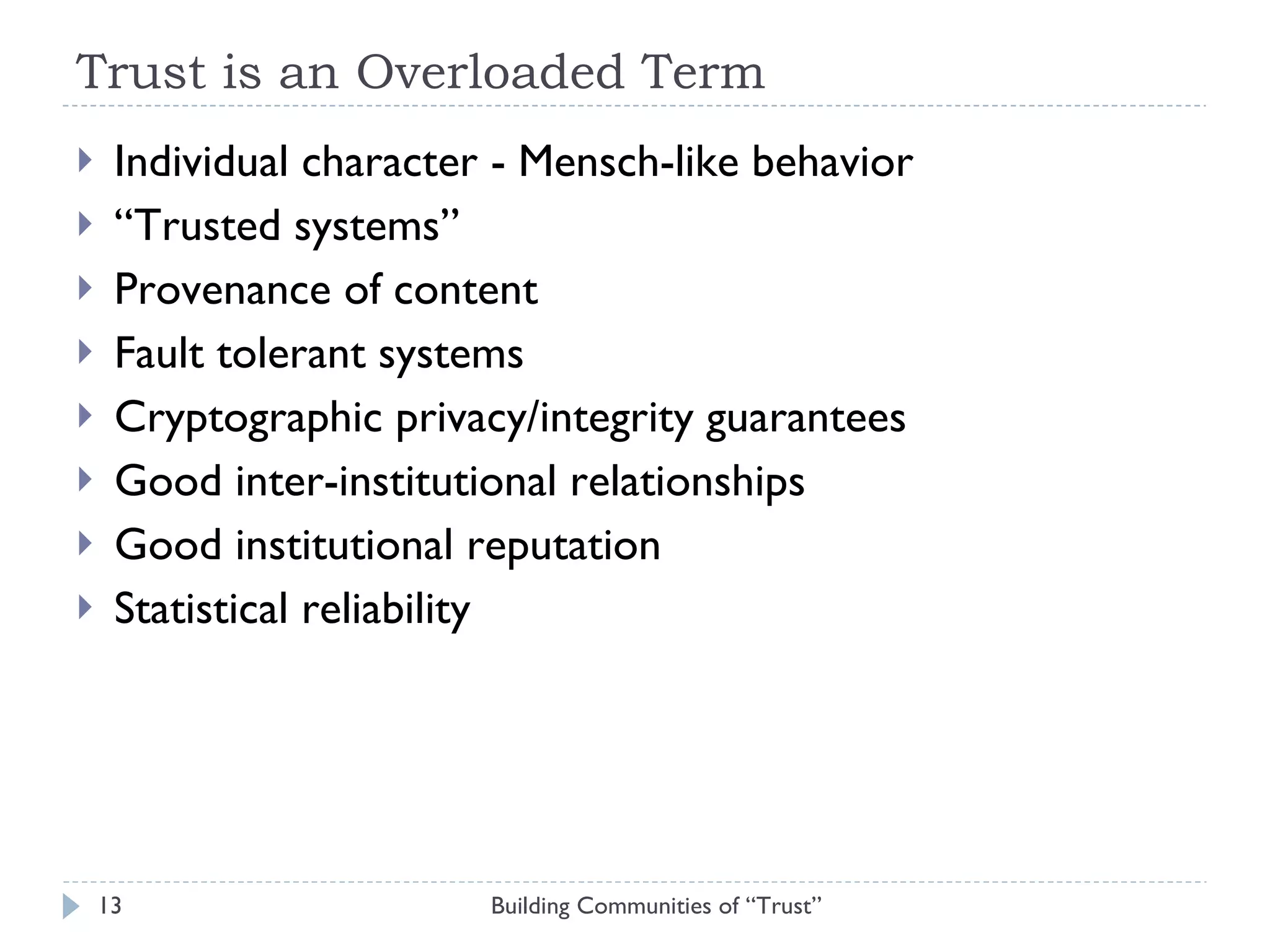
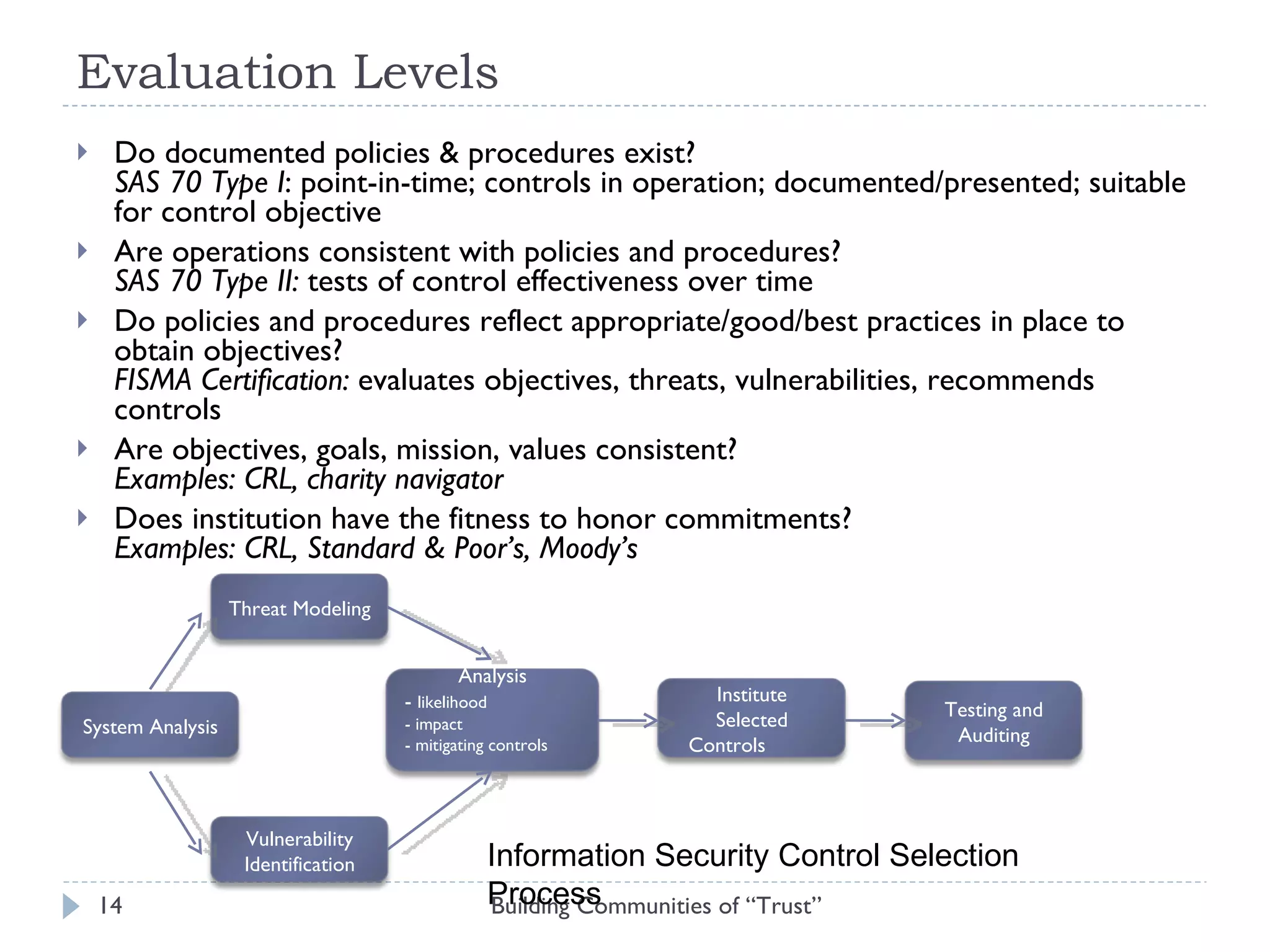
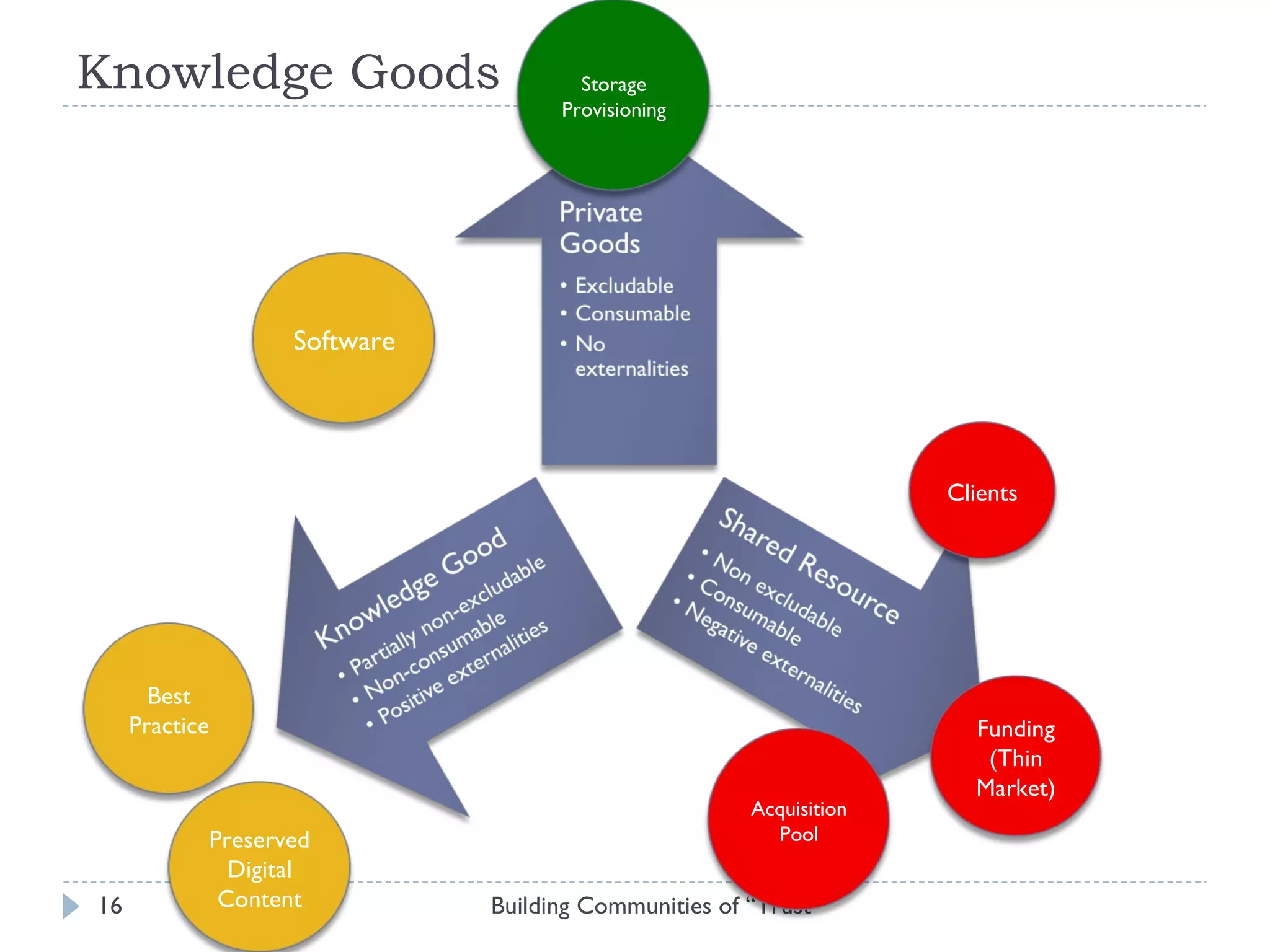
The document discusses the importance of building communities of trust for effective digital preservation strategies, outlining how virtual organizations can mitigate preservation risks through systematic collaboration. It emphasizes the needs for clear roles, continuous evaluation, and adherence to best practices to ensure reliable archival processes. The text also explores technical approaches, necessary relationships, and the complexity of trust in collaborative preservation environments.