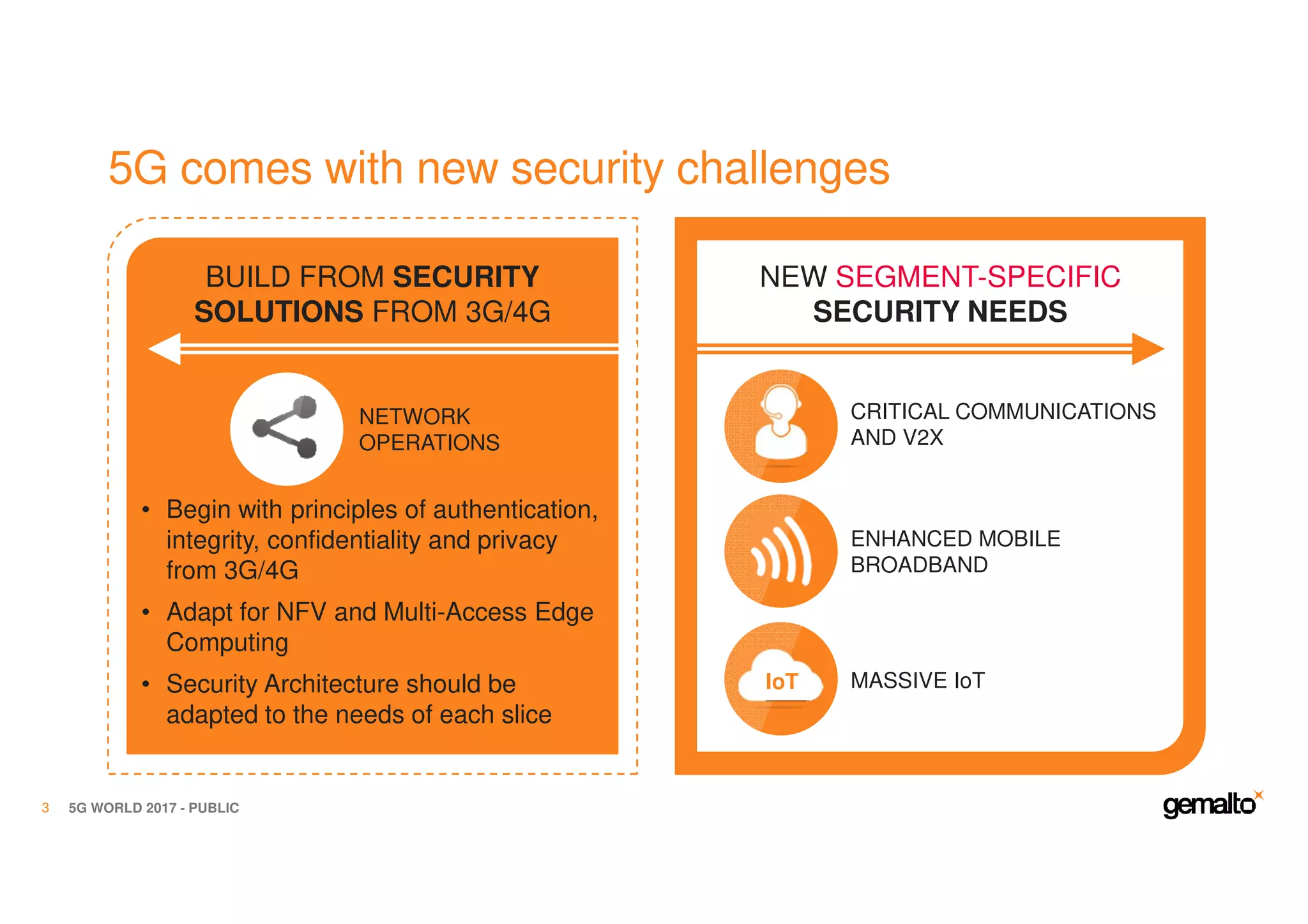
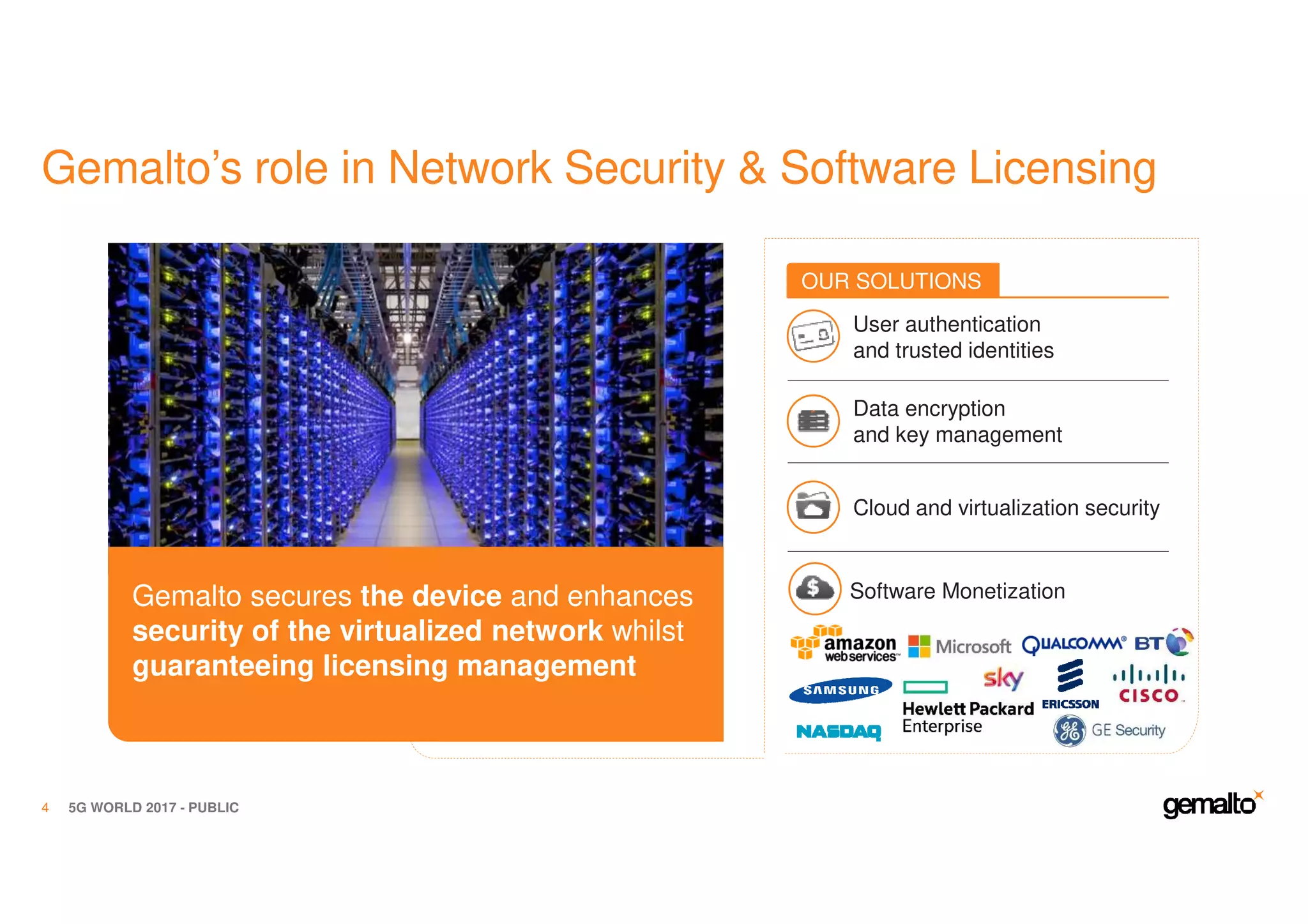
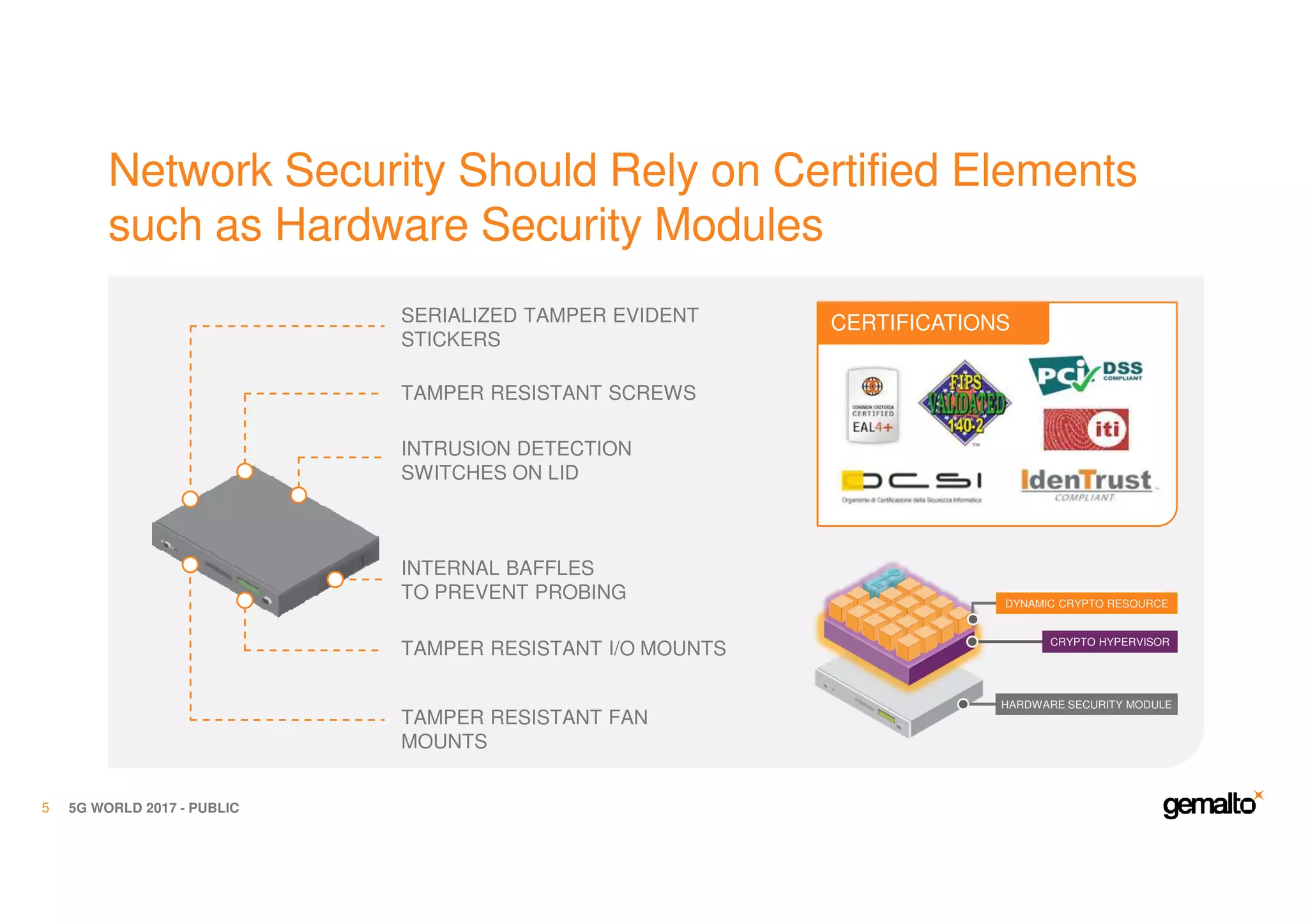
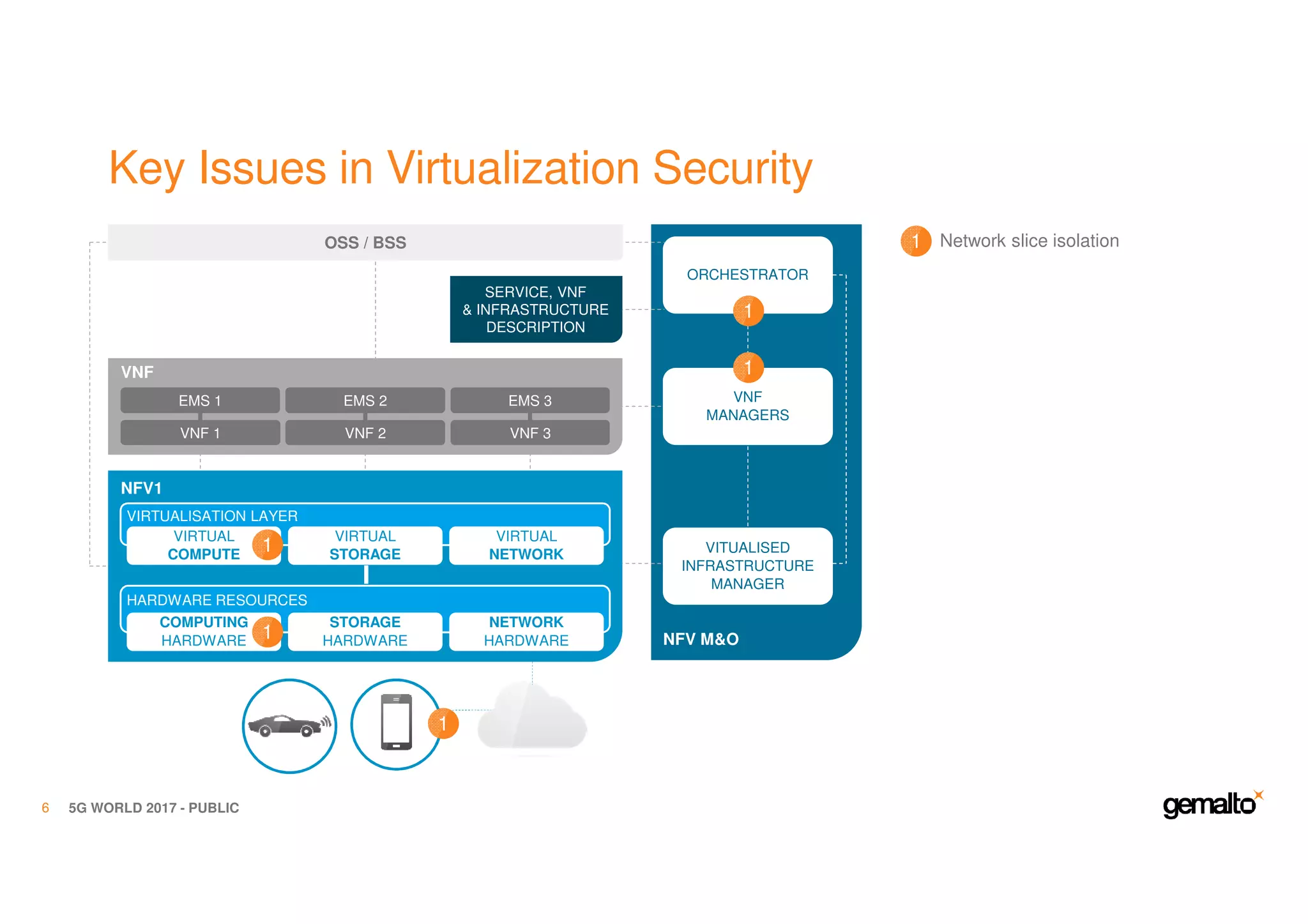
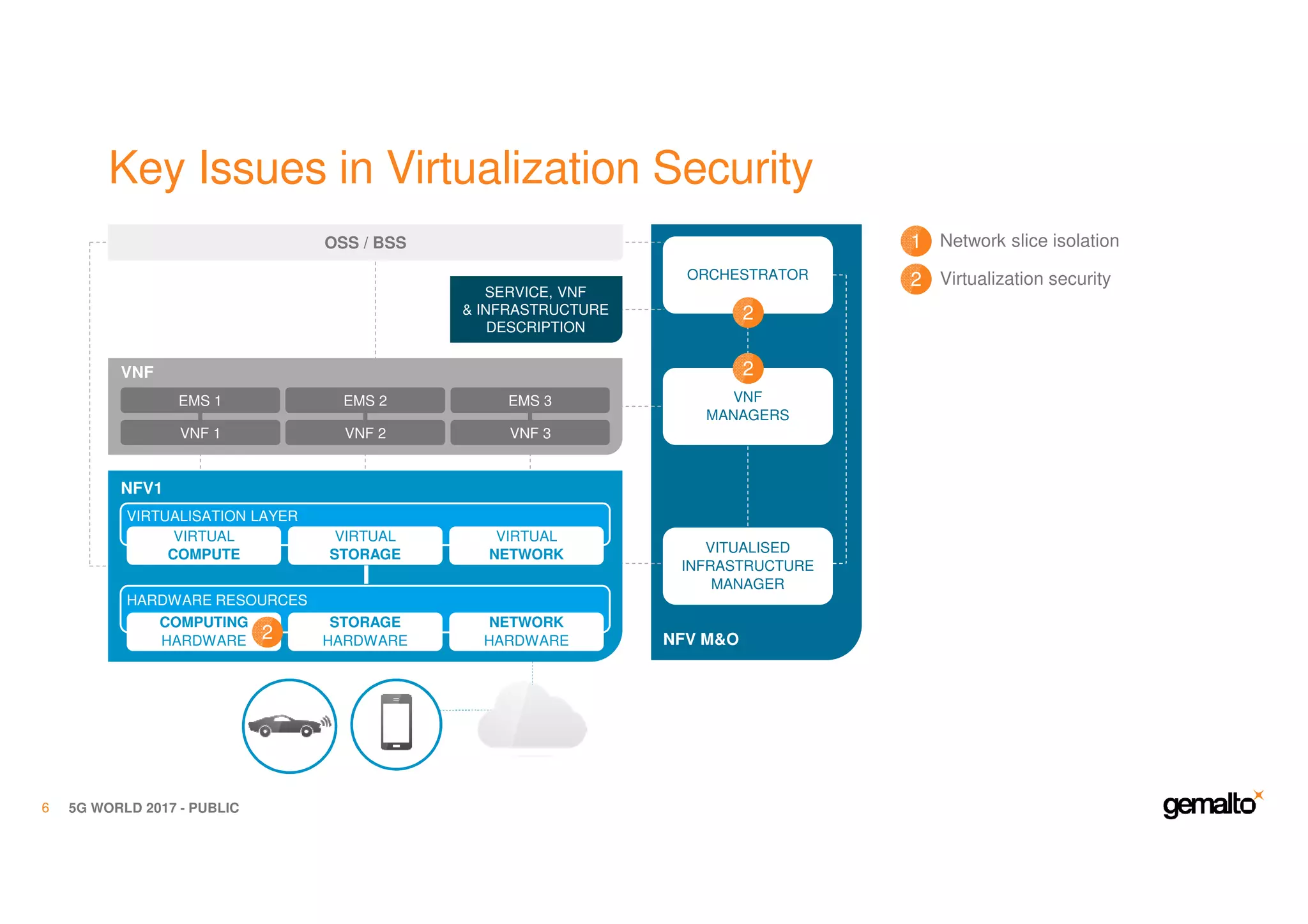
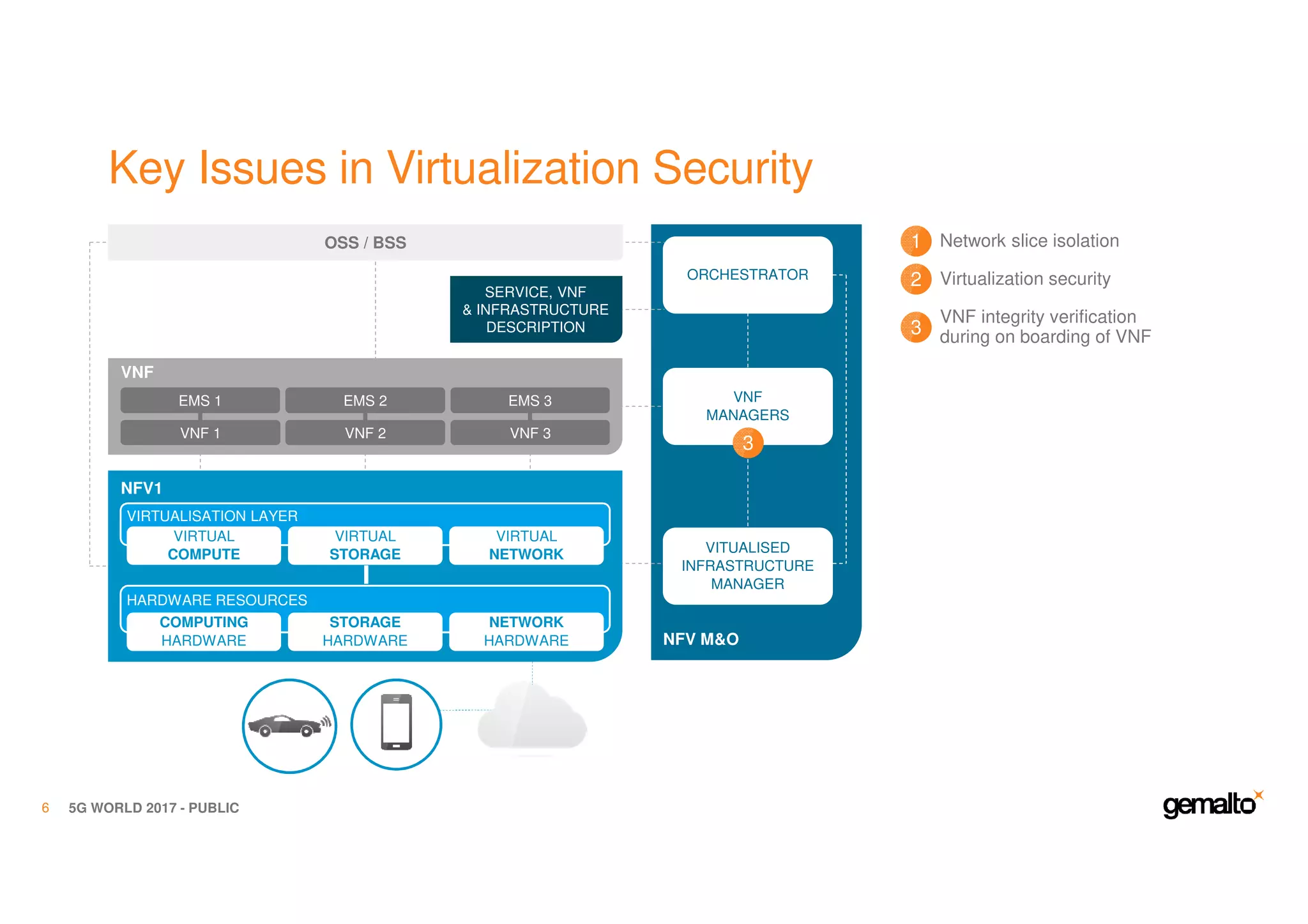
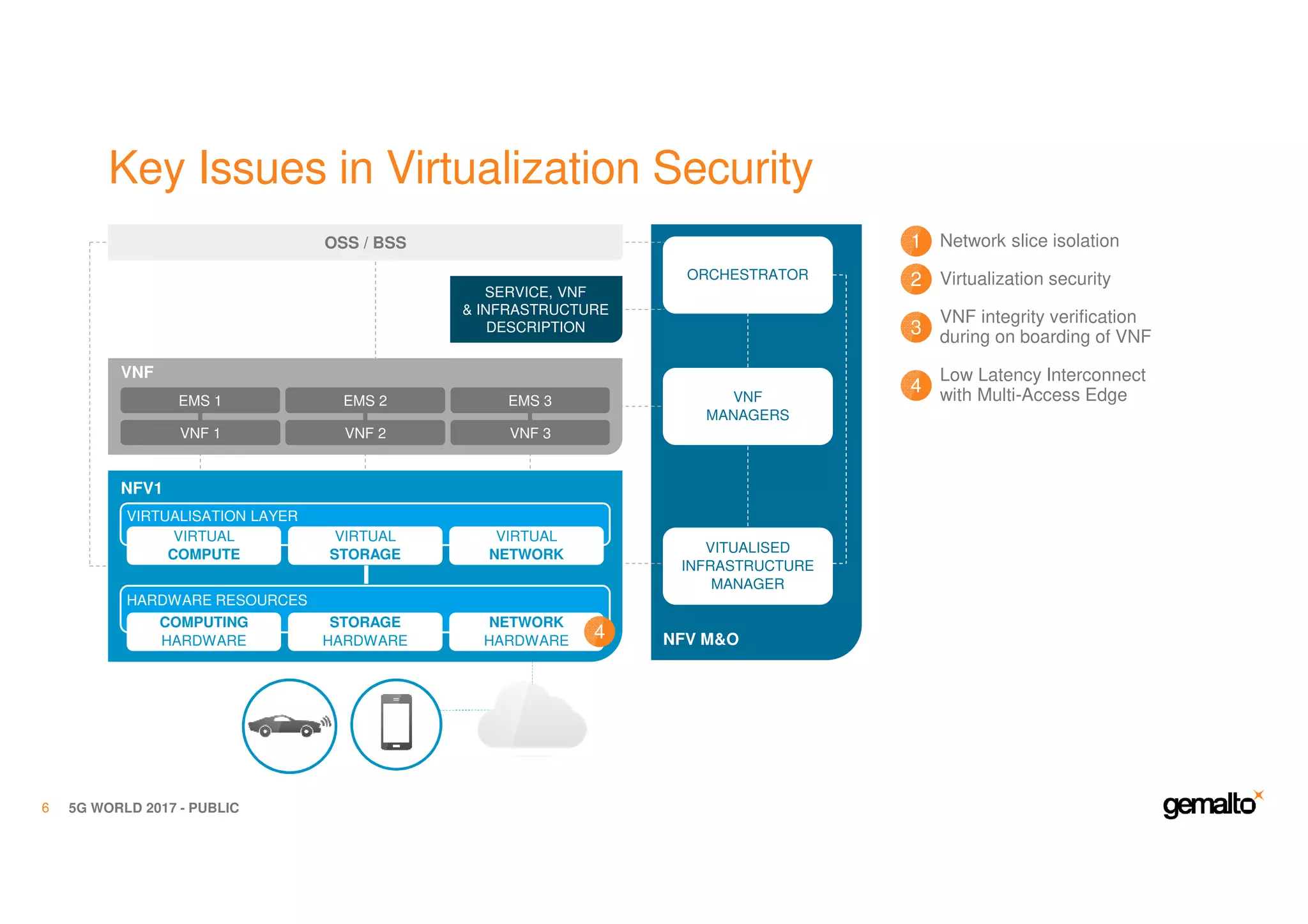
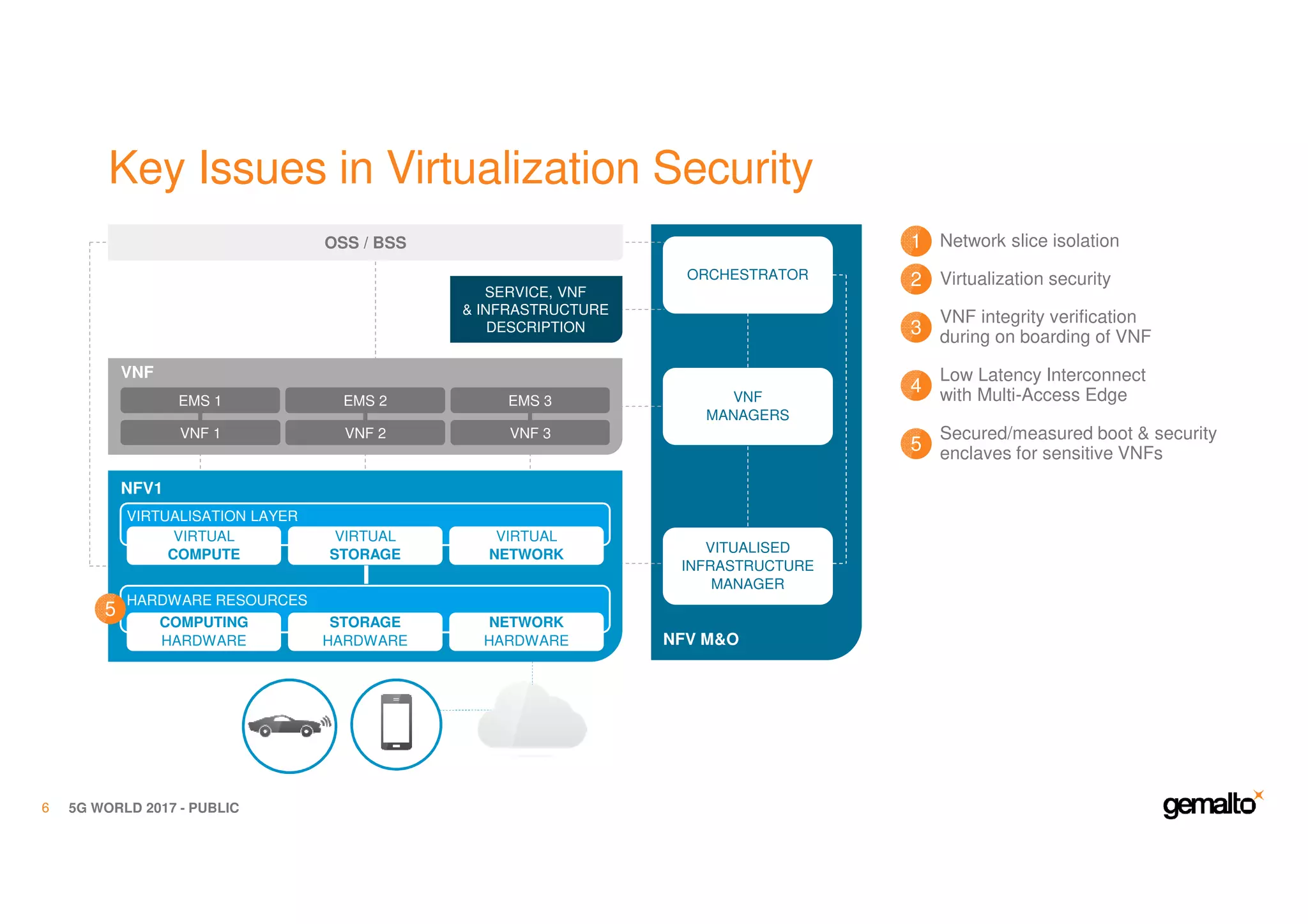
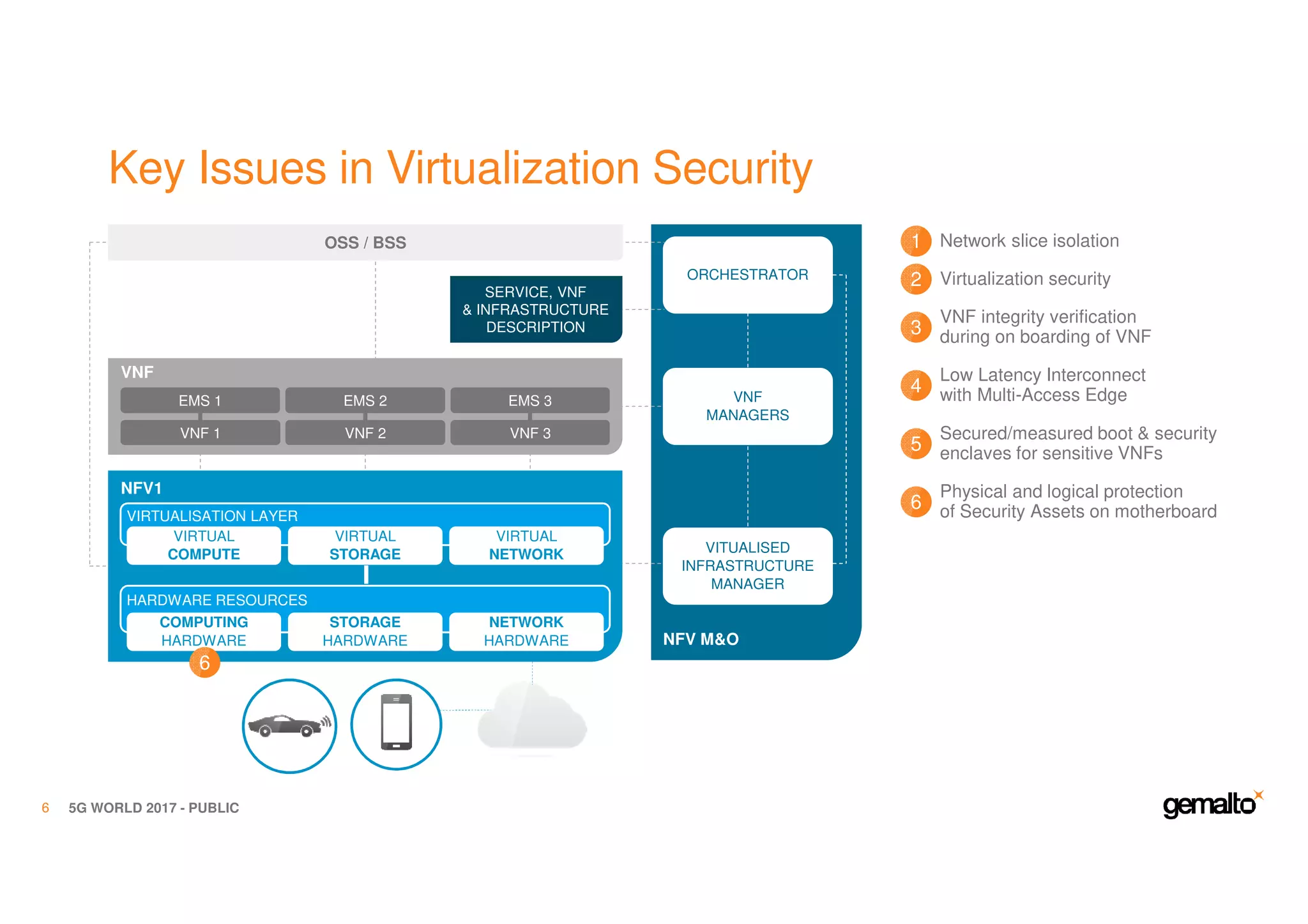
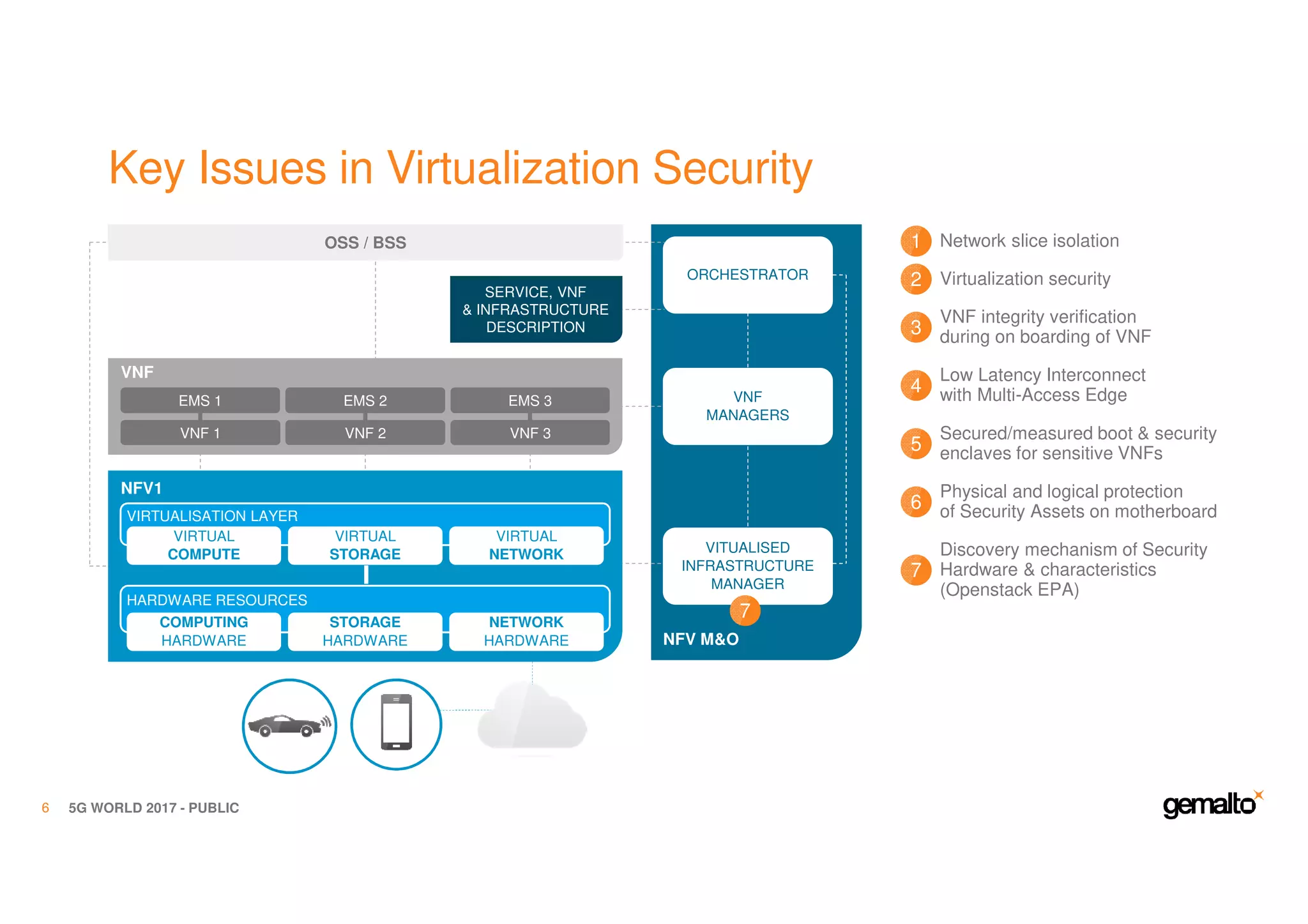
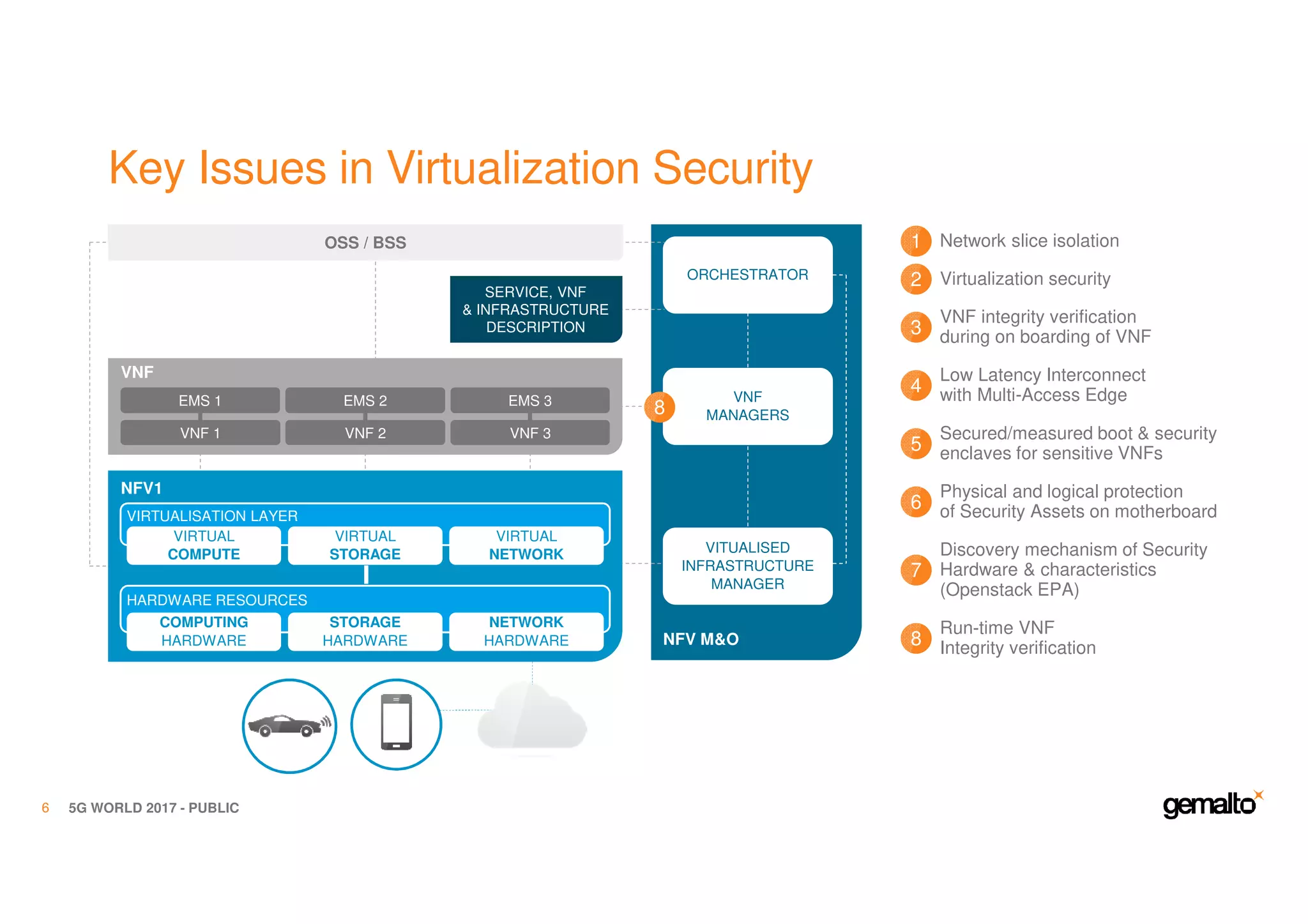
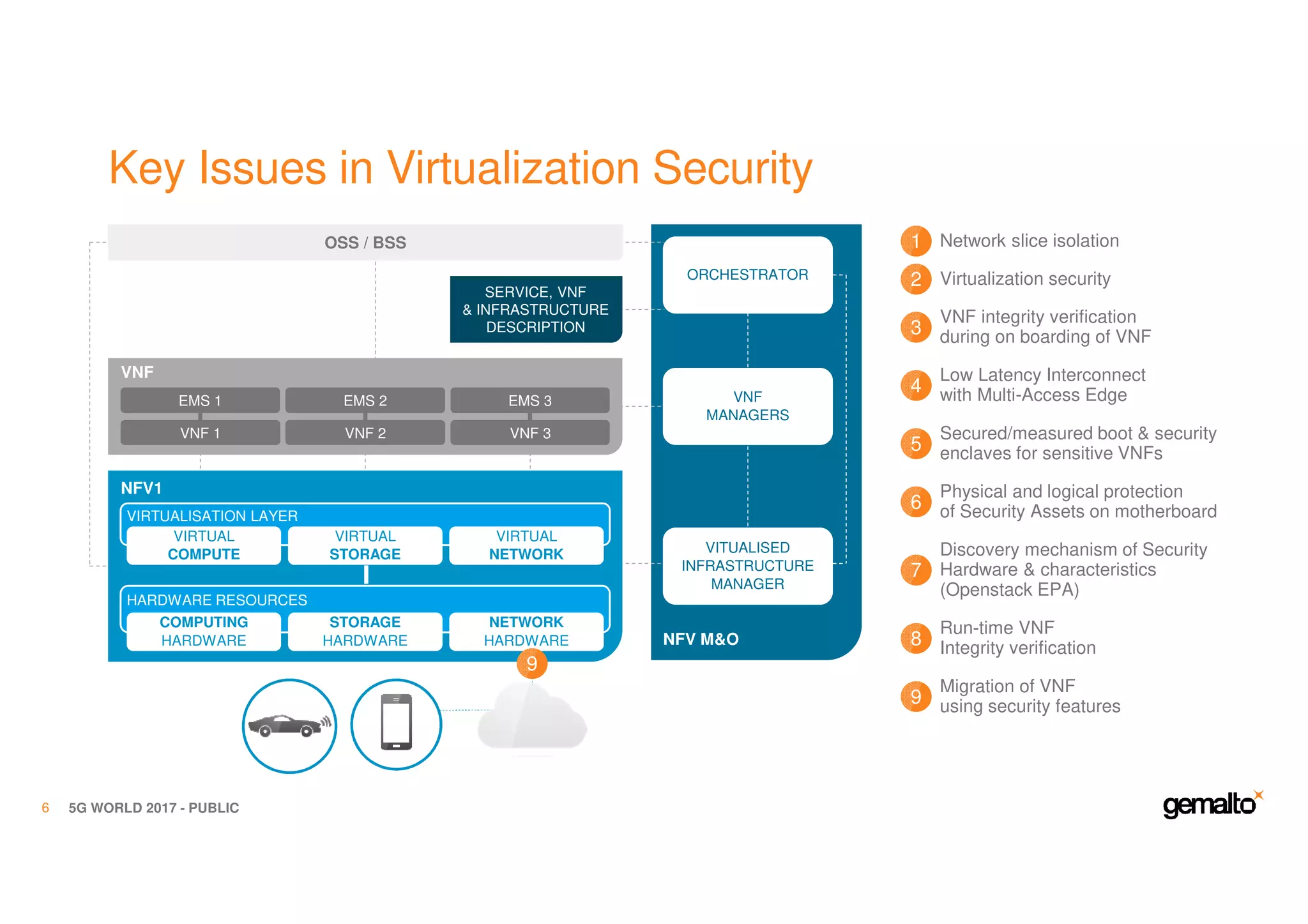
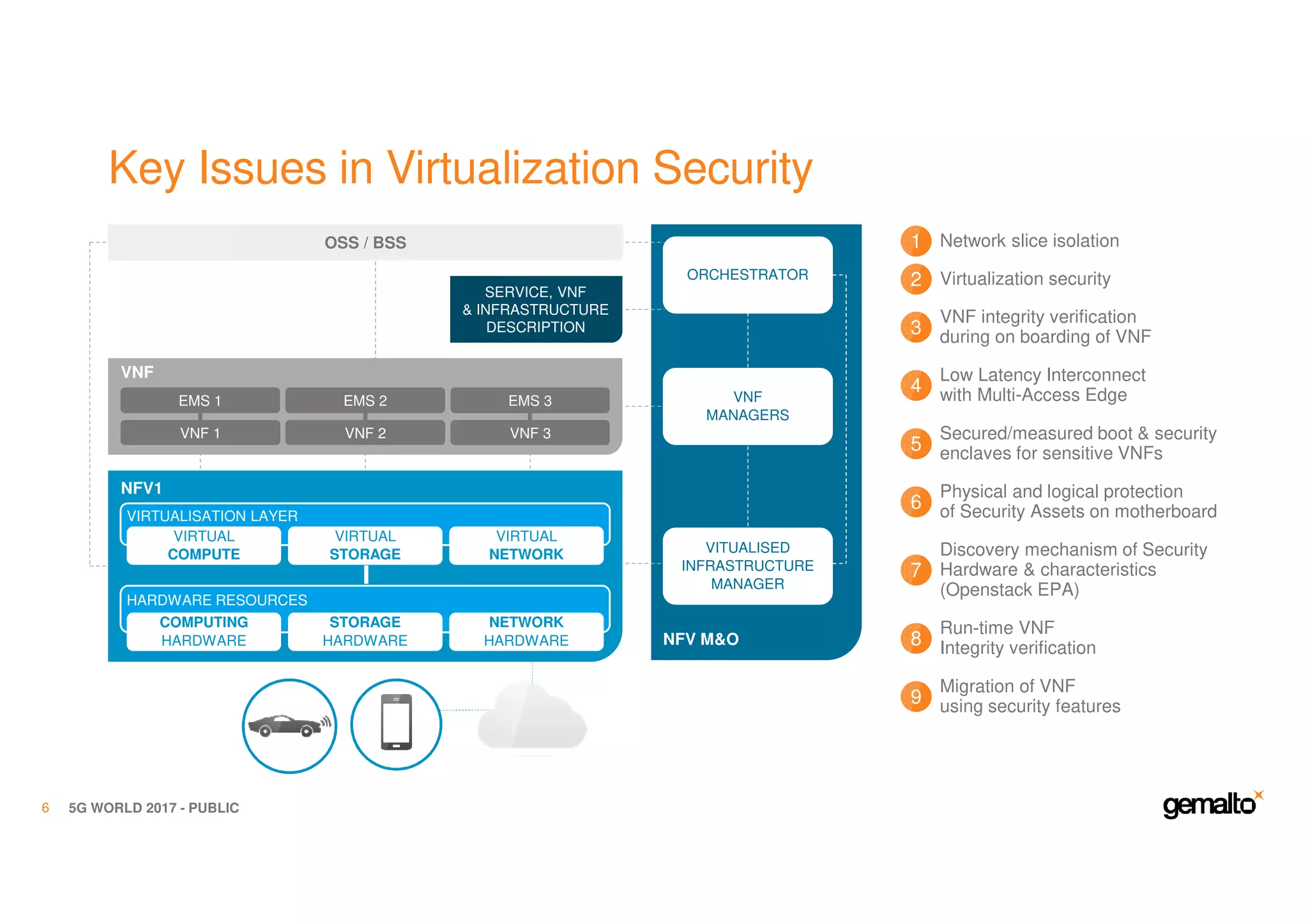
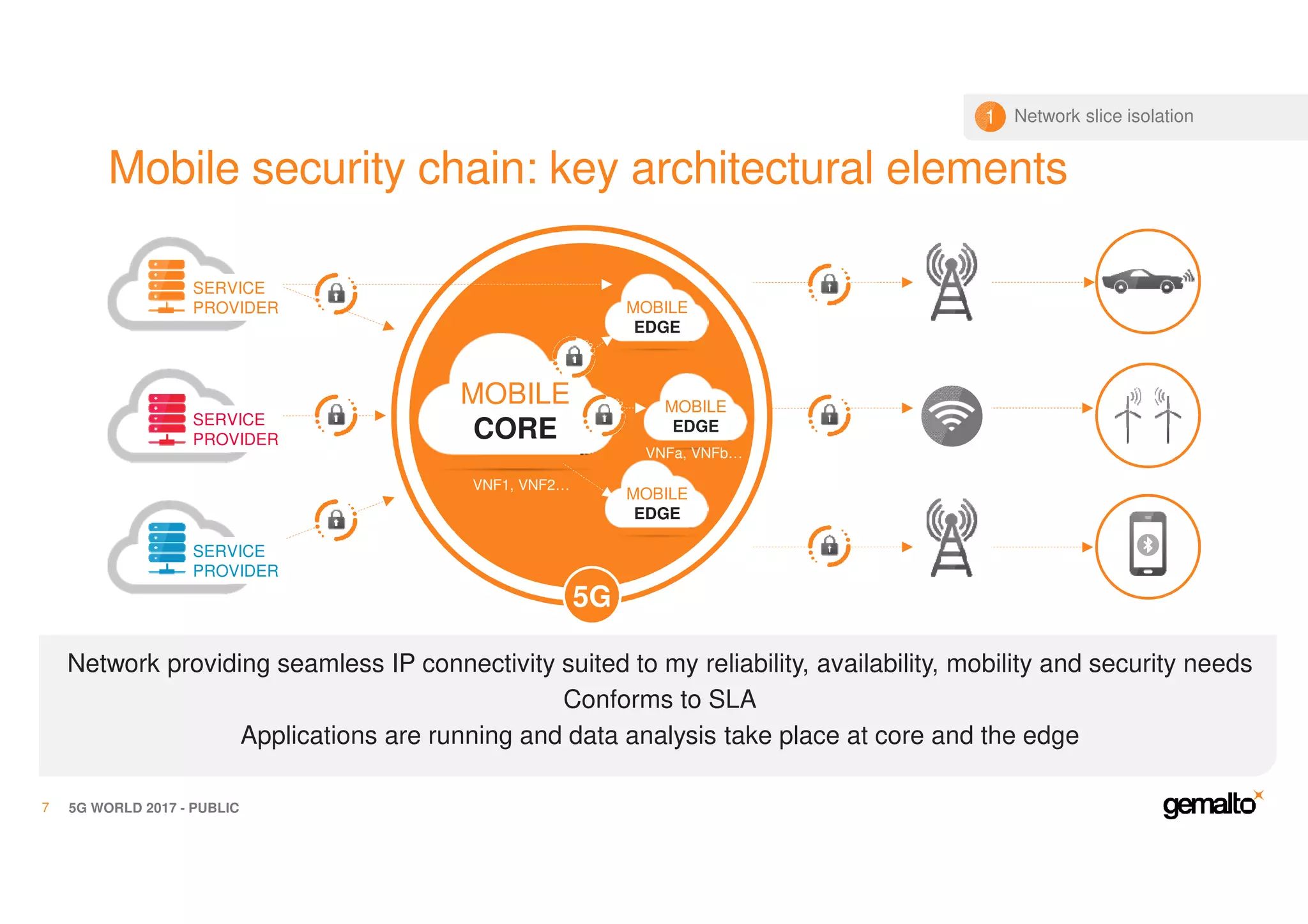
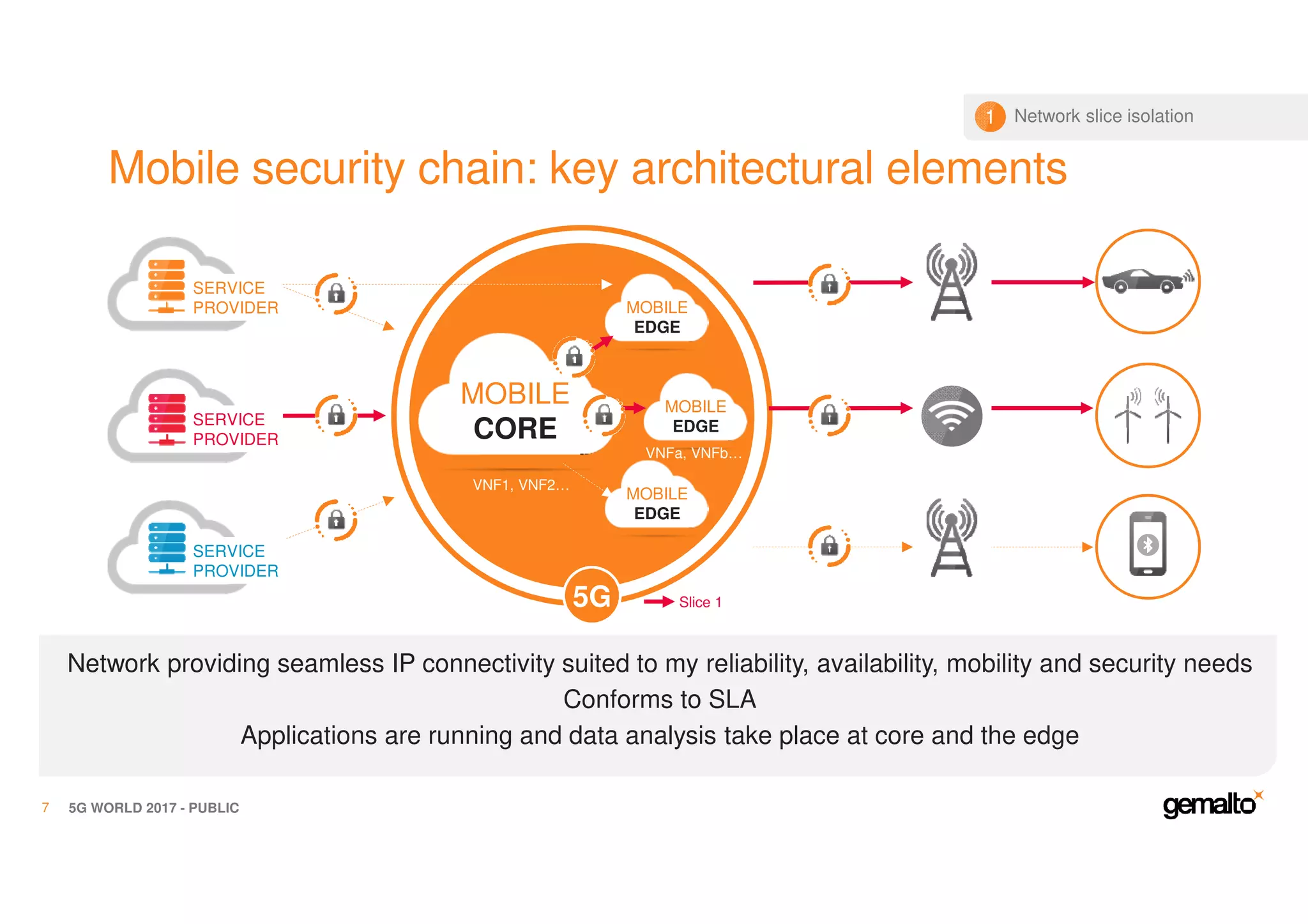
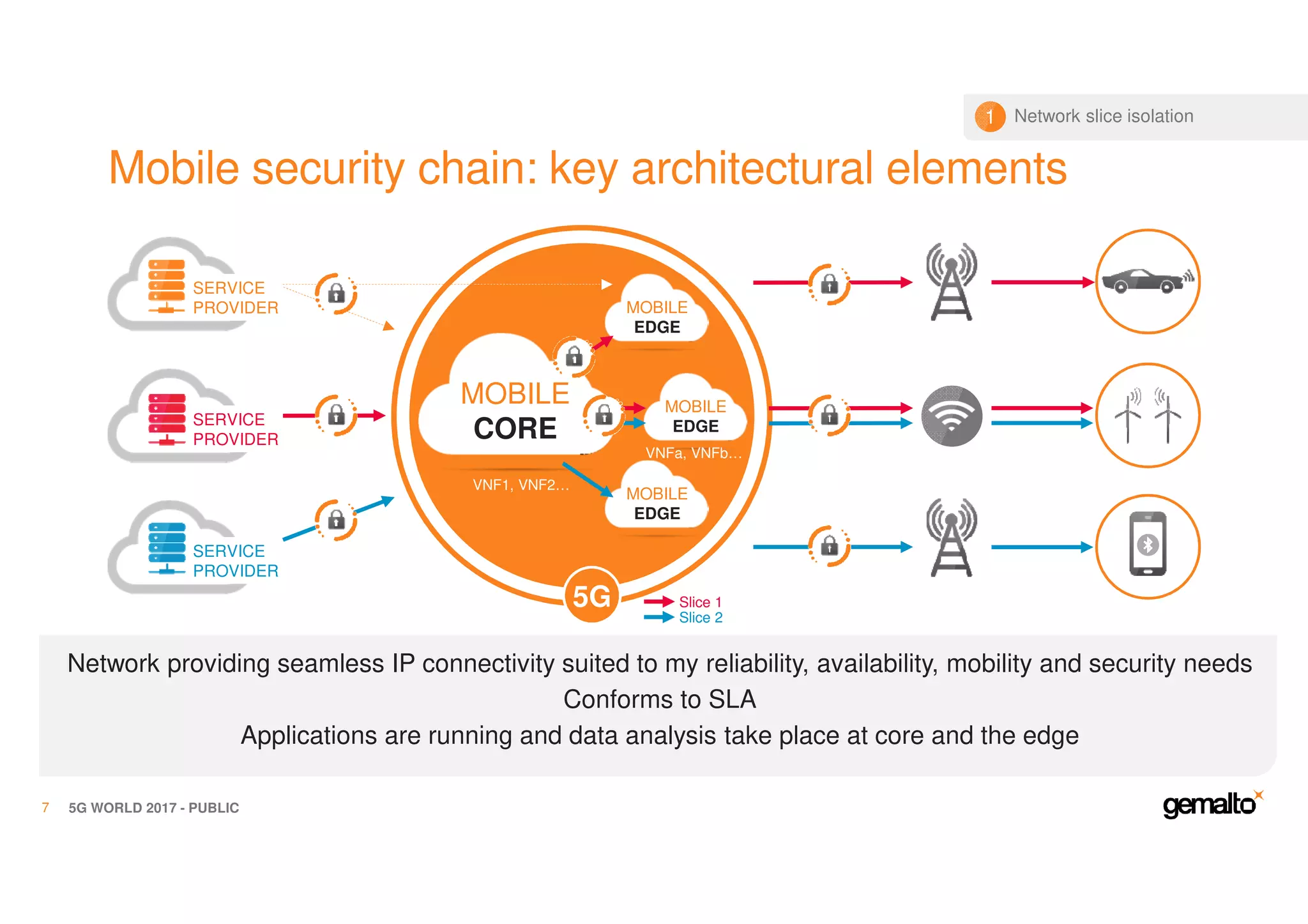
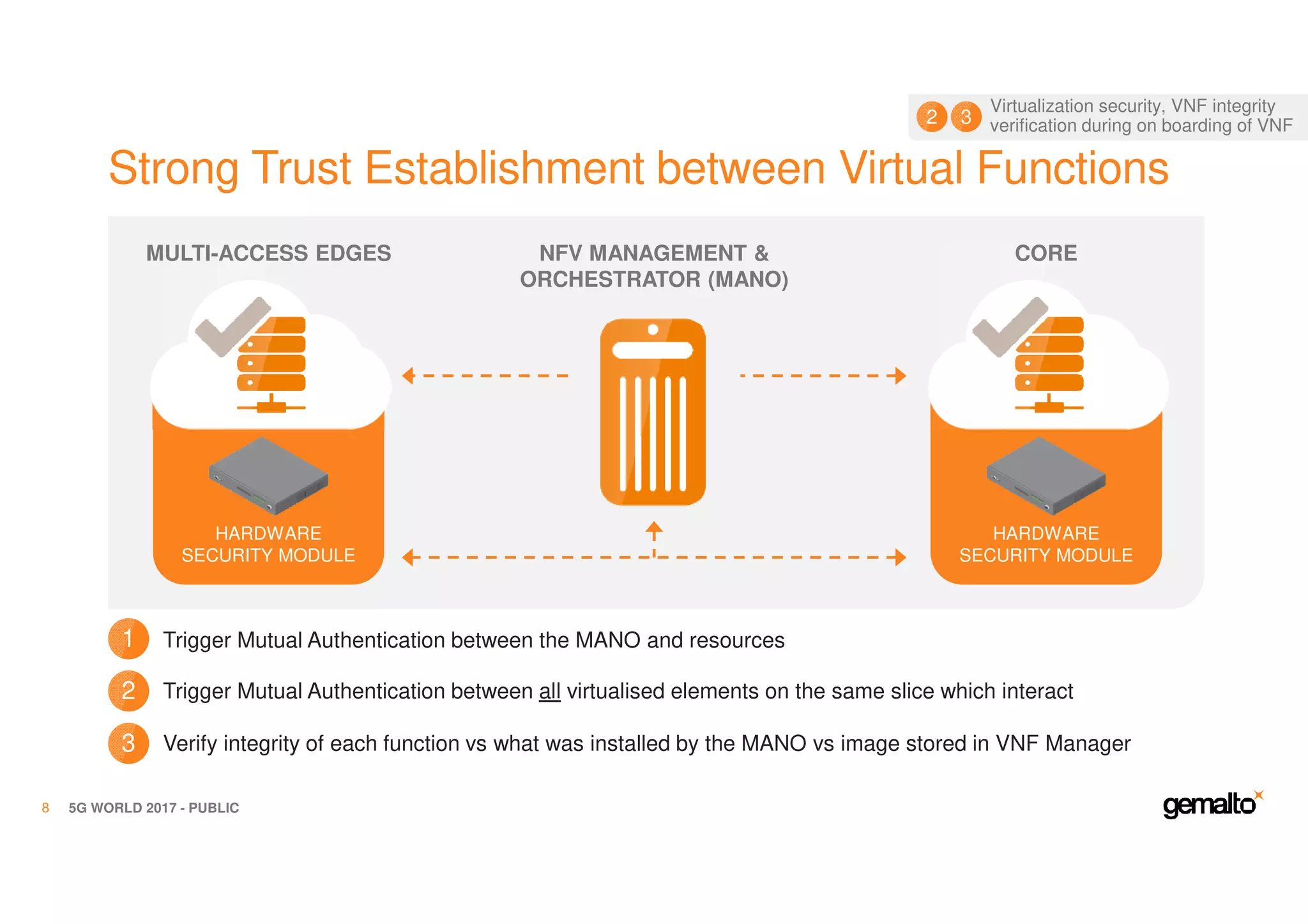
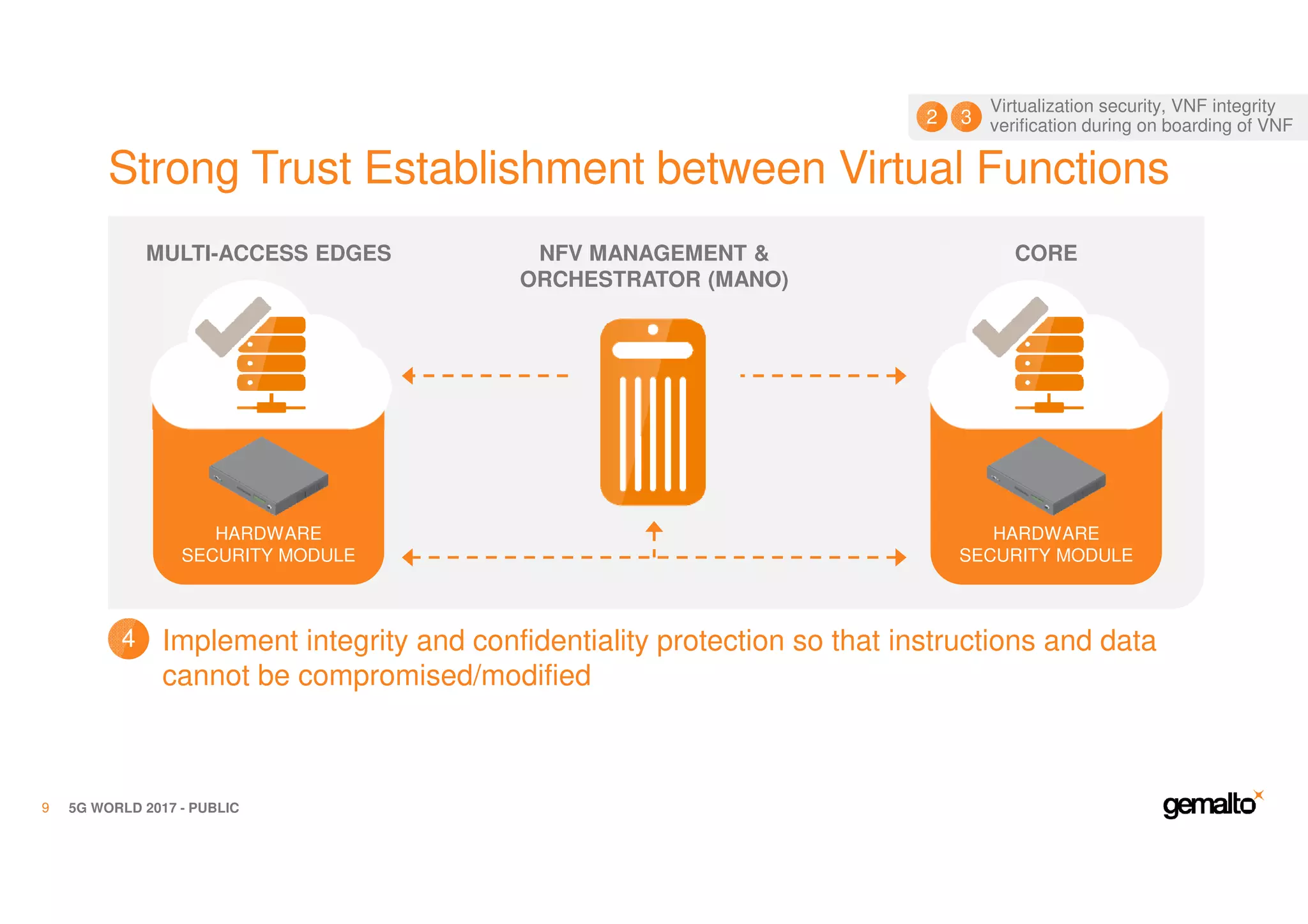
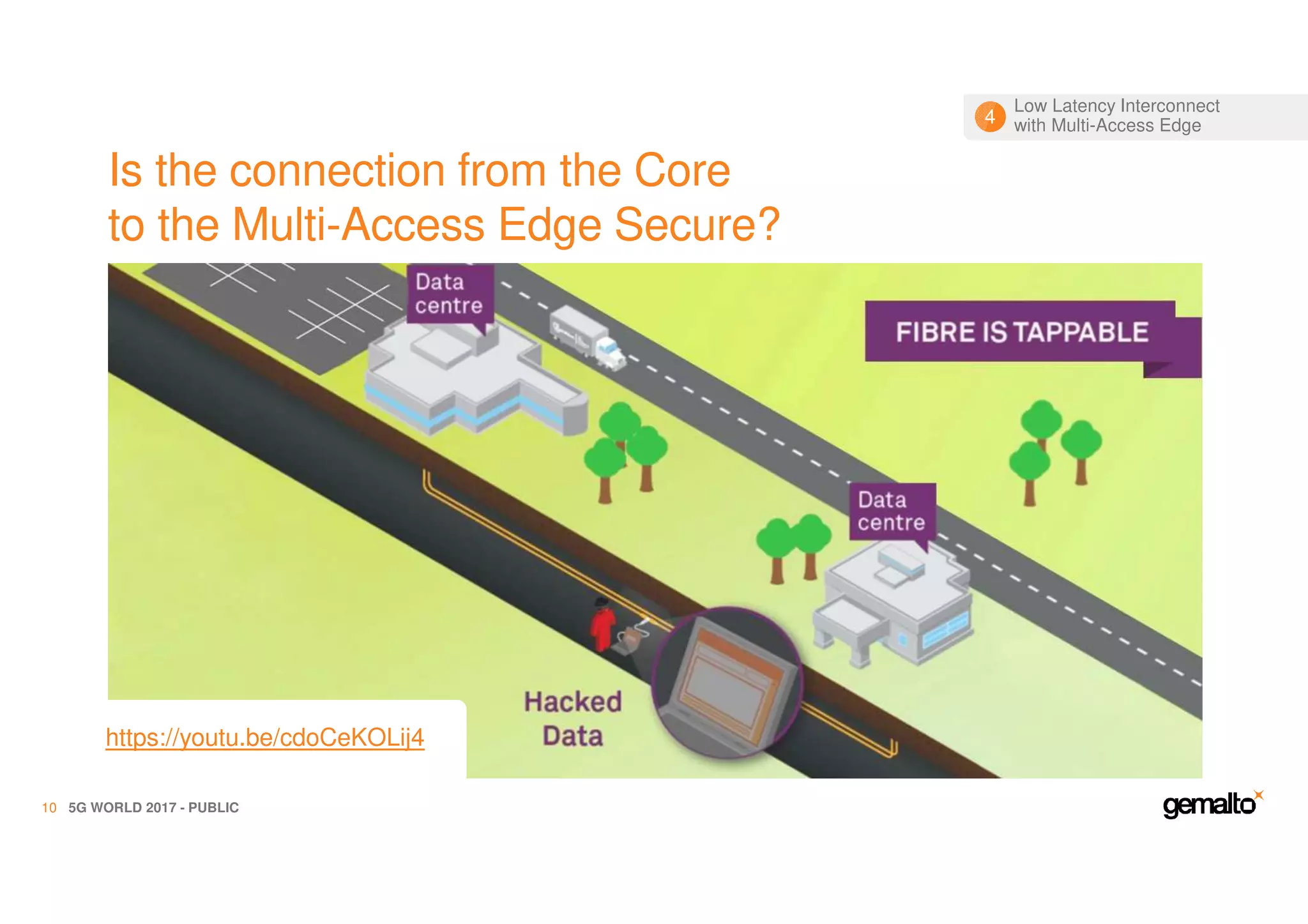
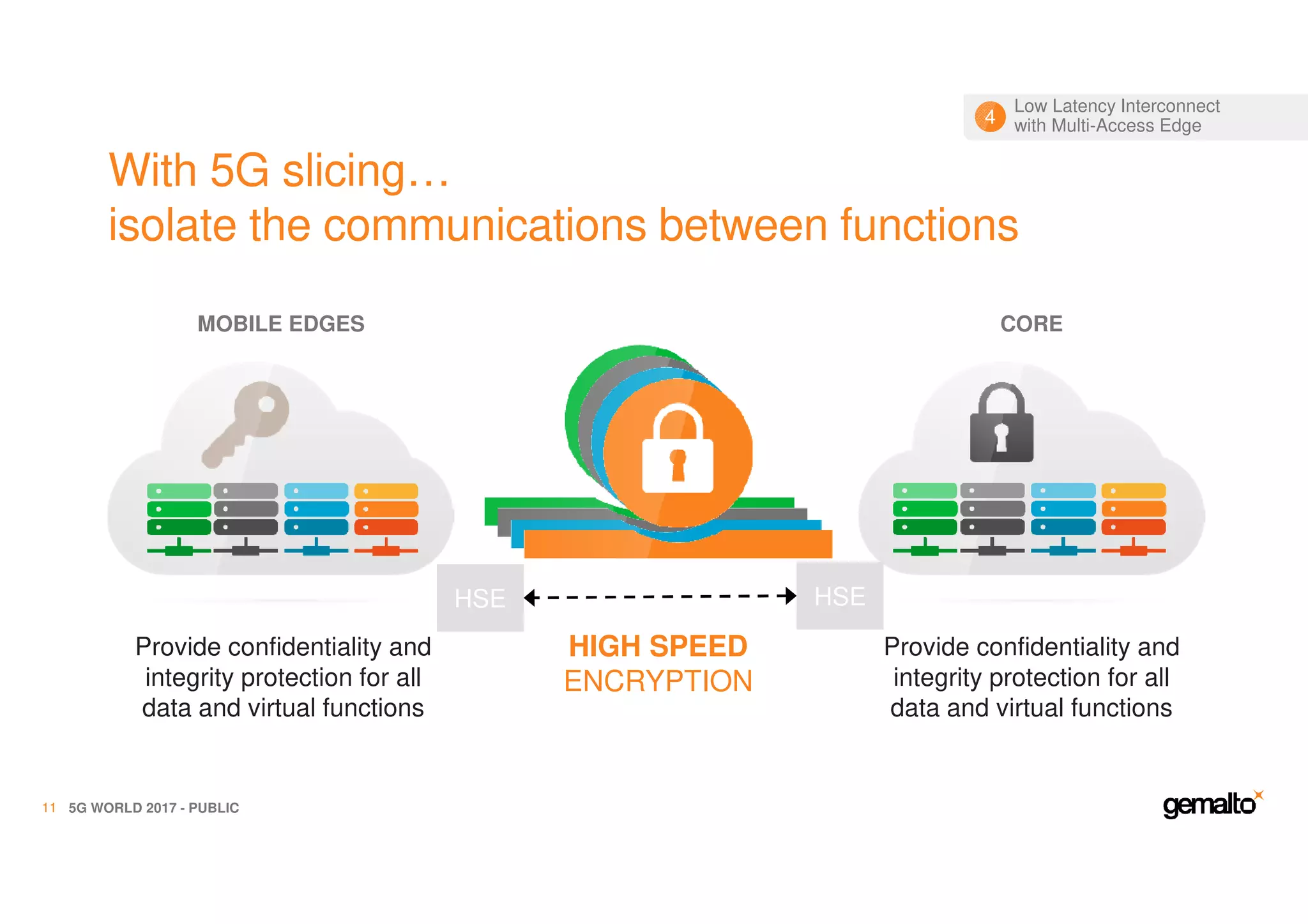
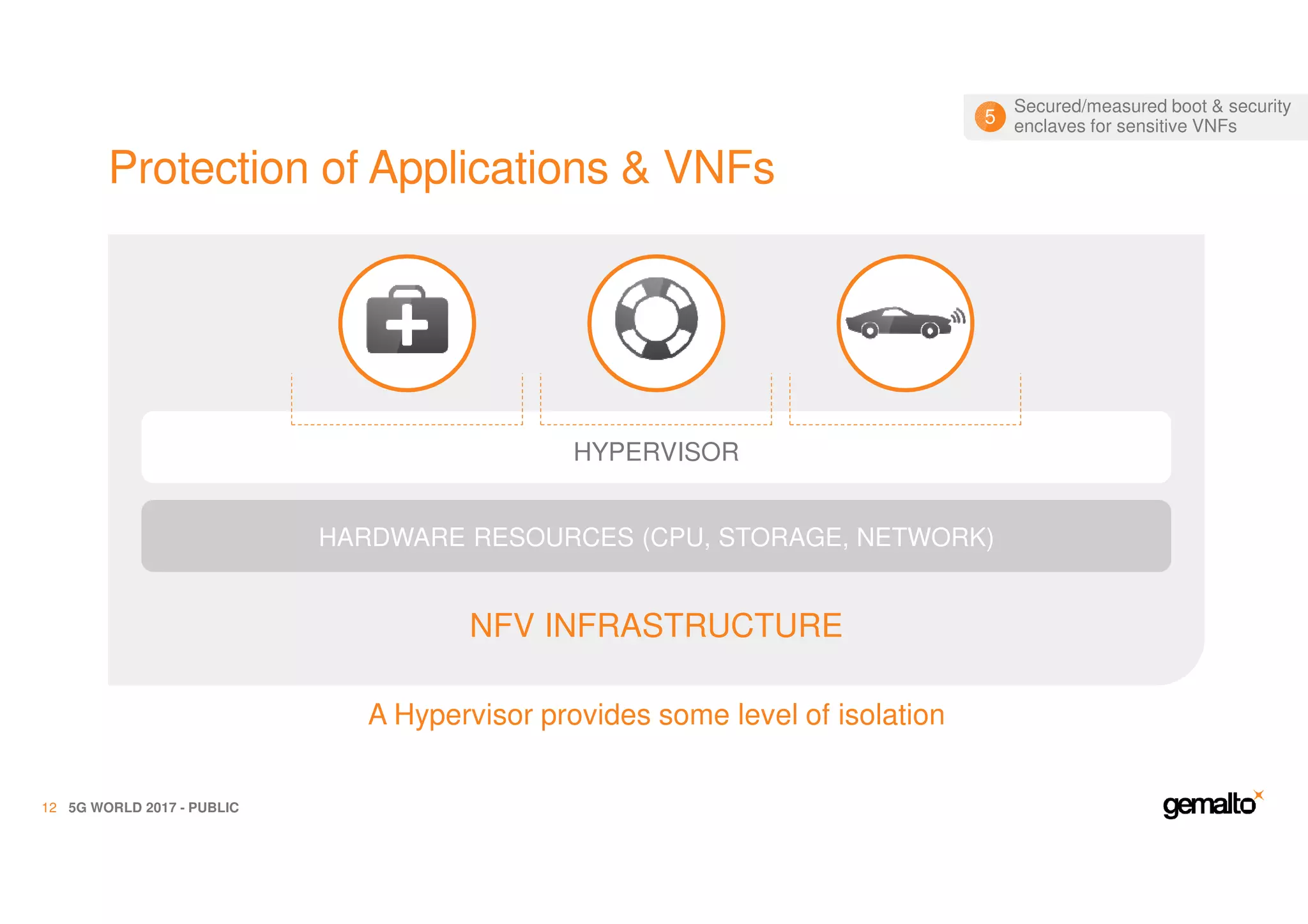
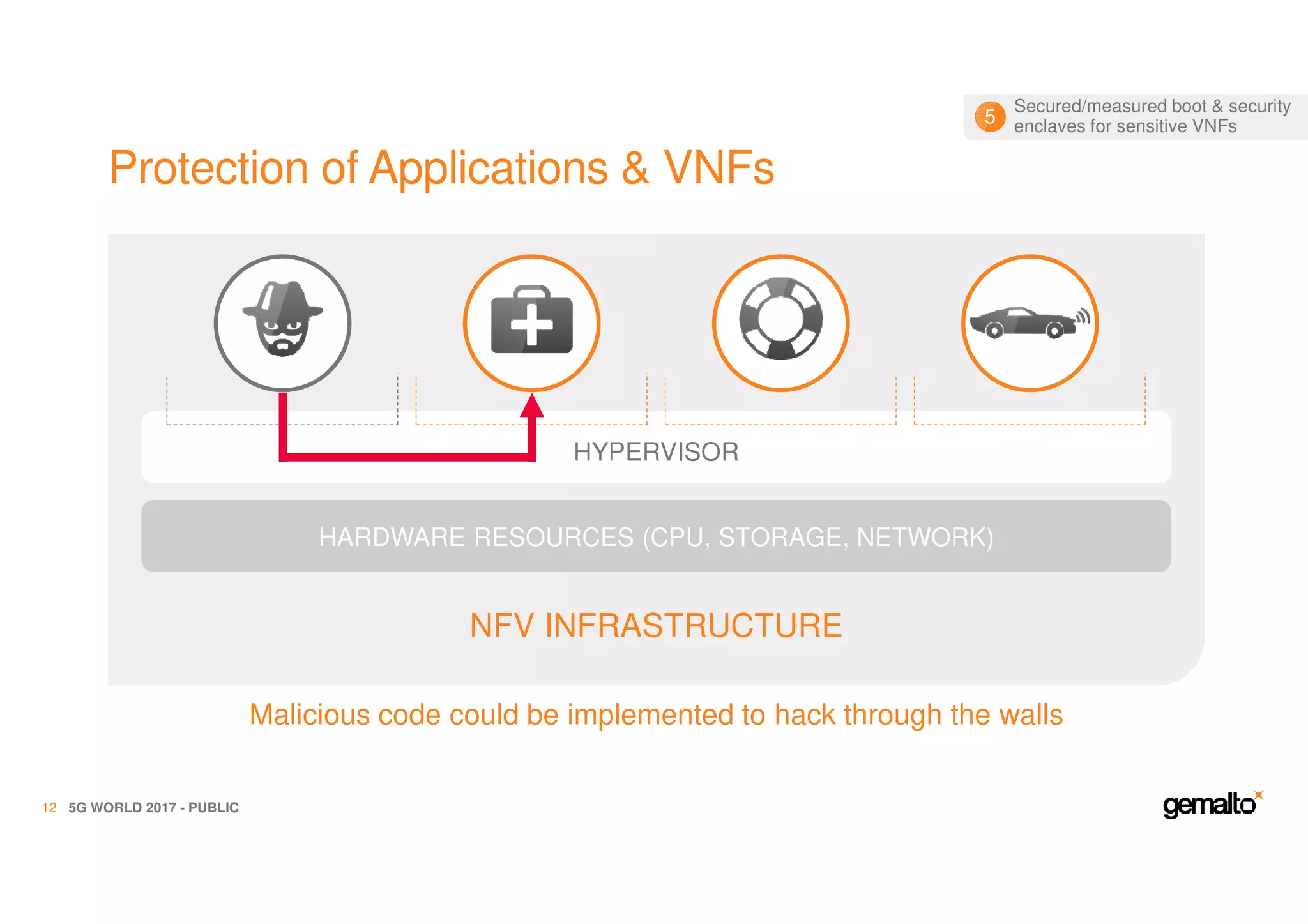
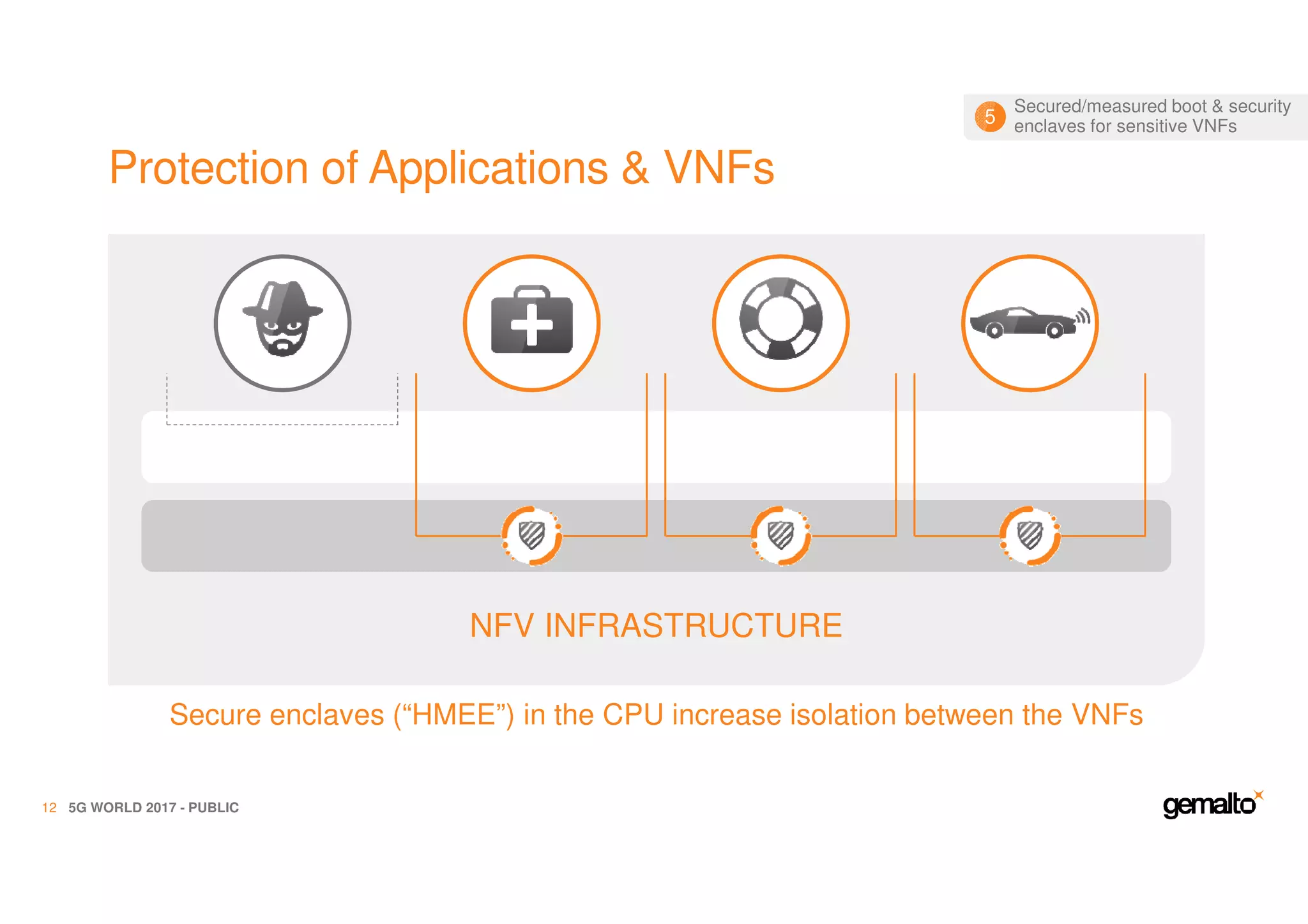
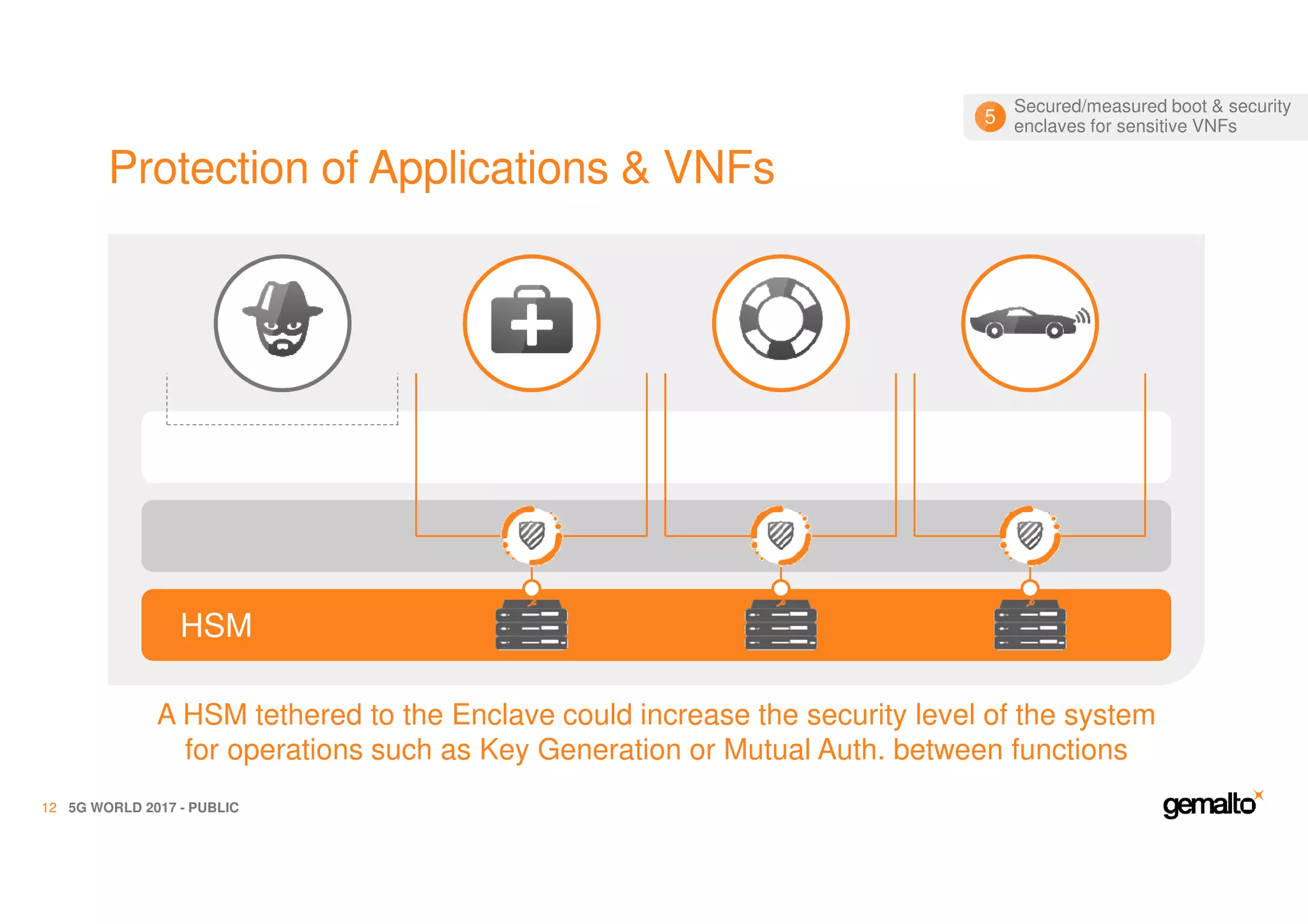
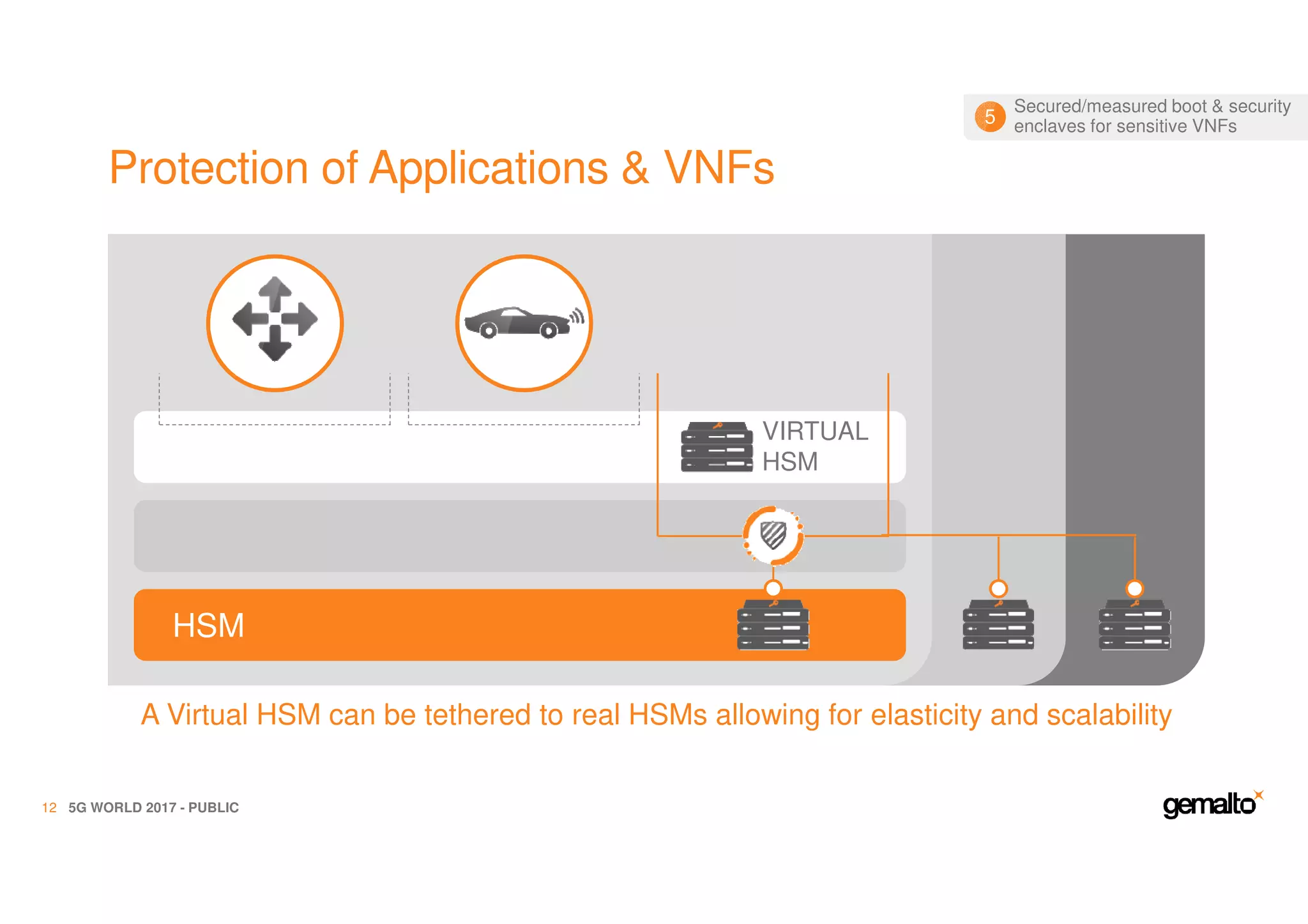
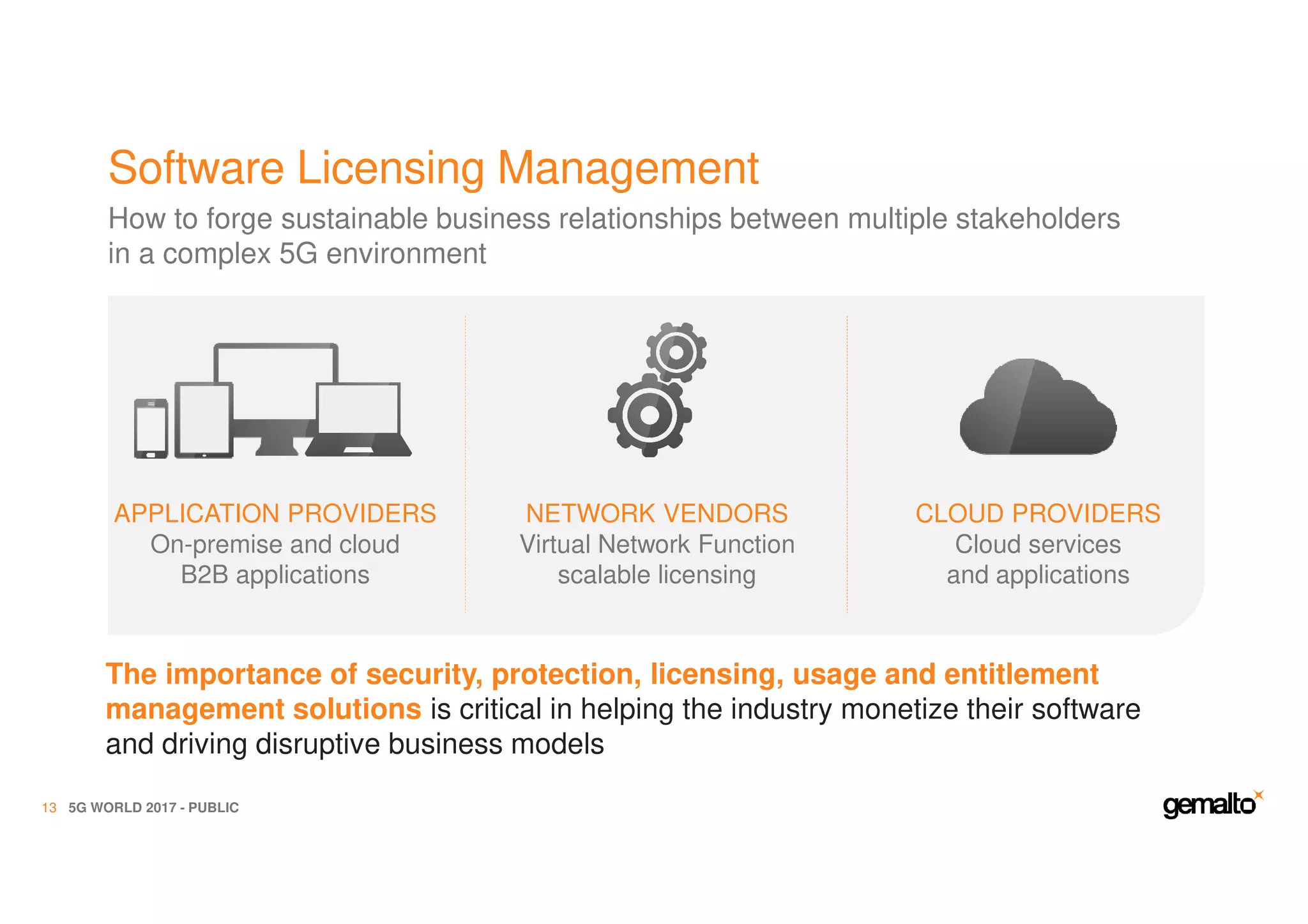
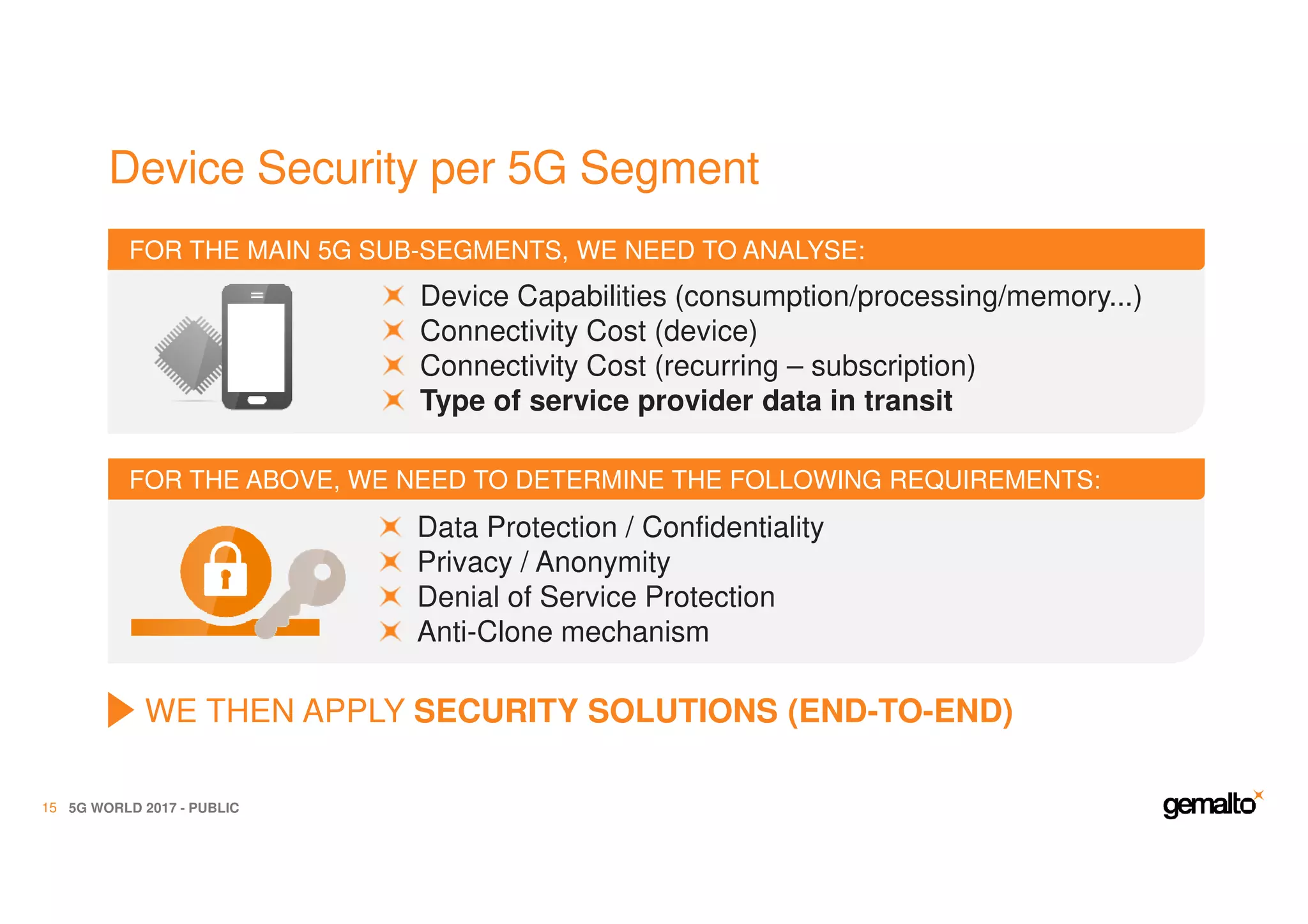
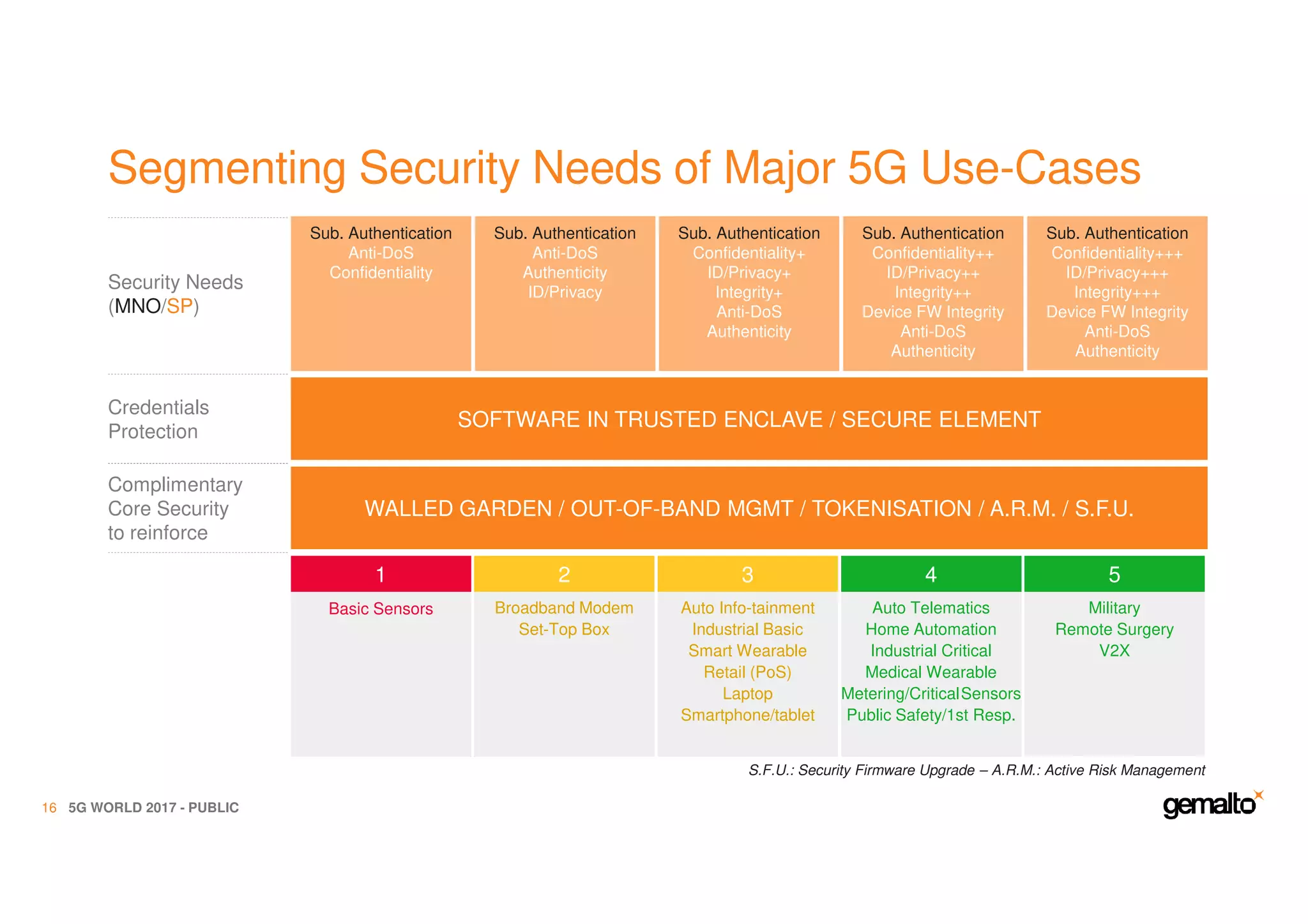
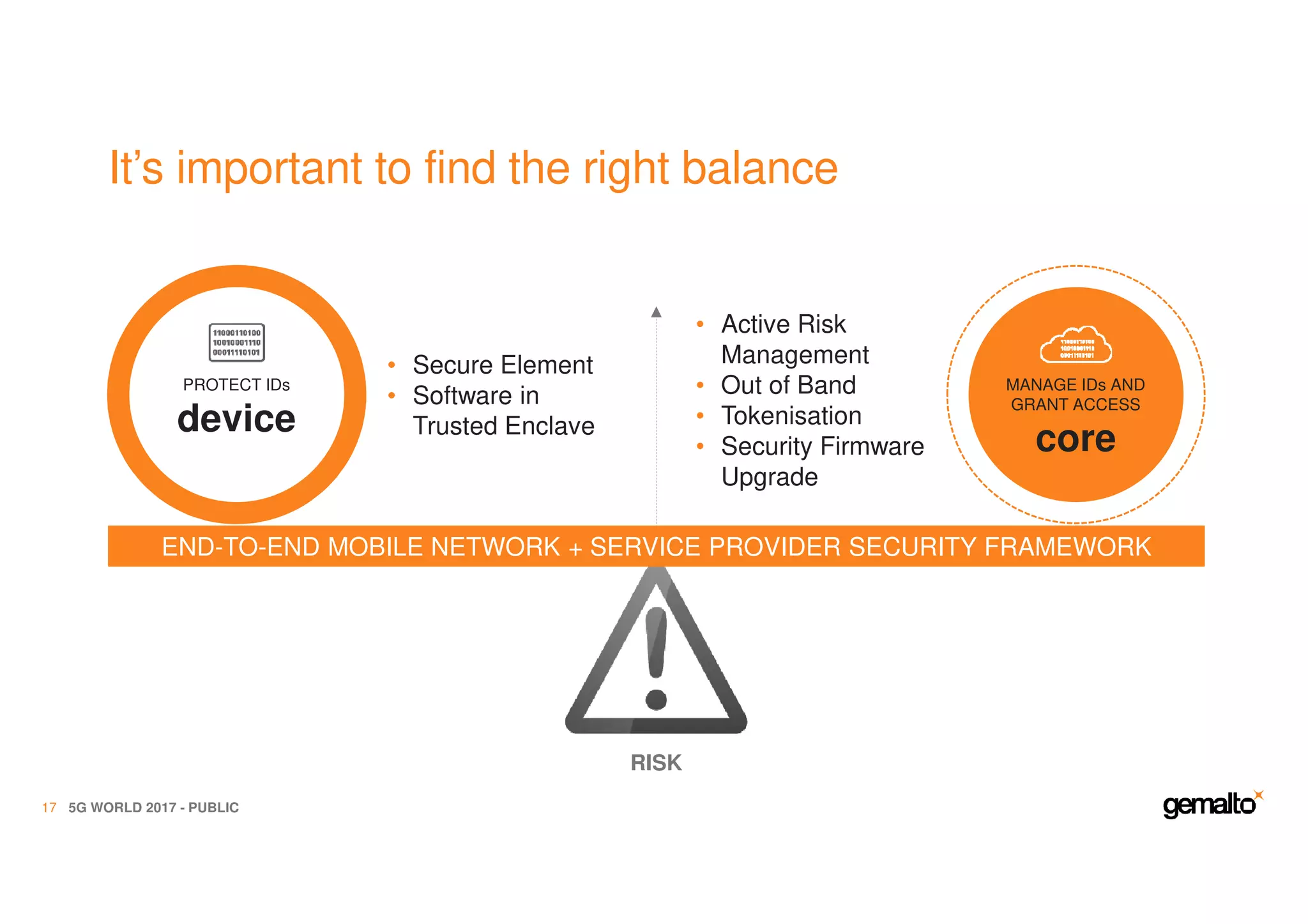
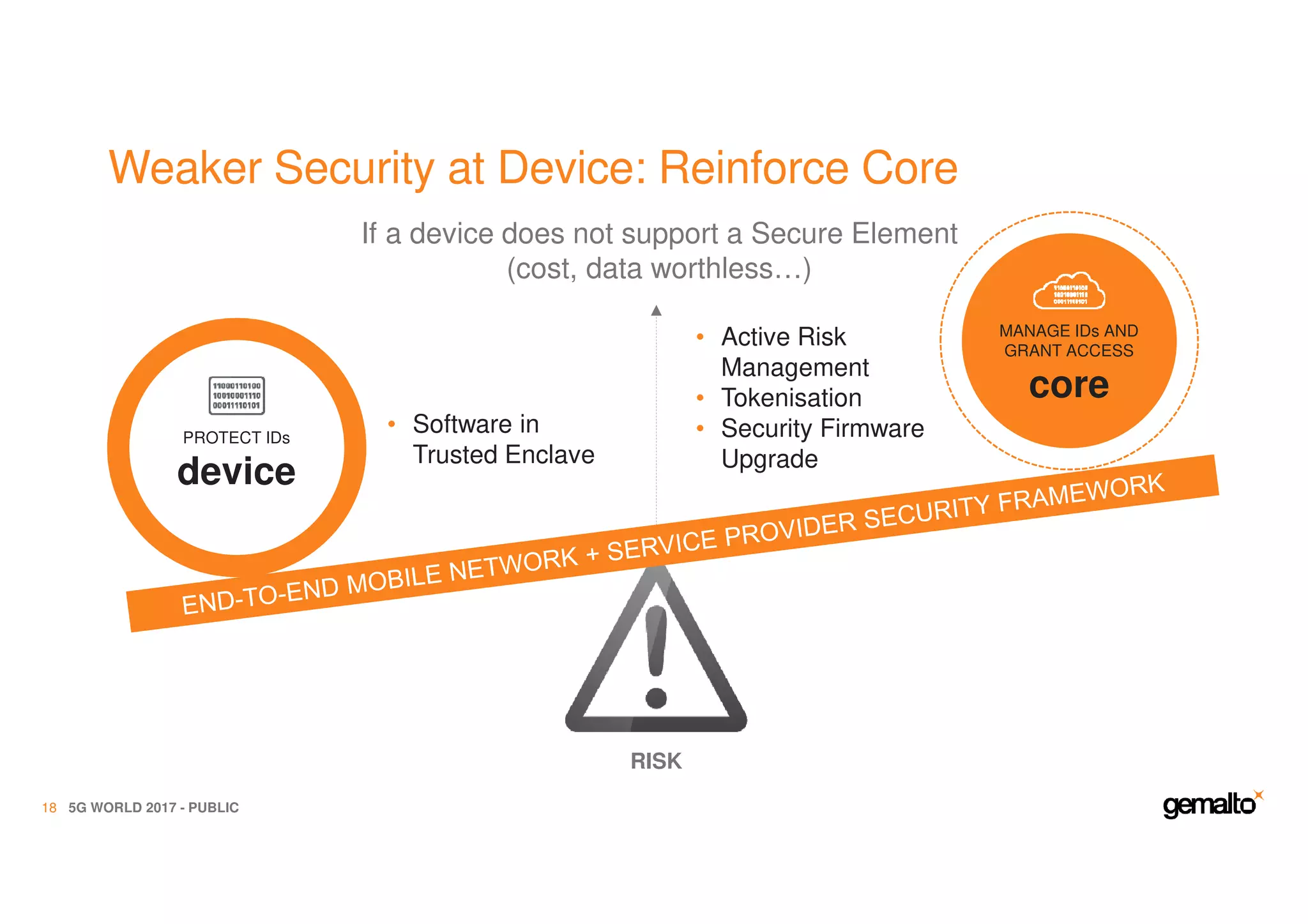
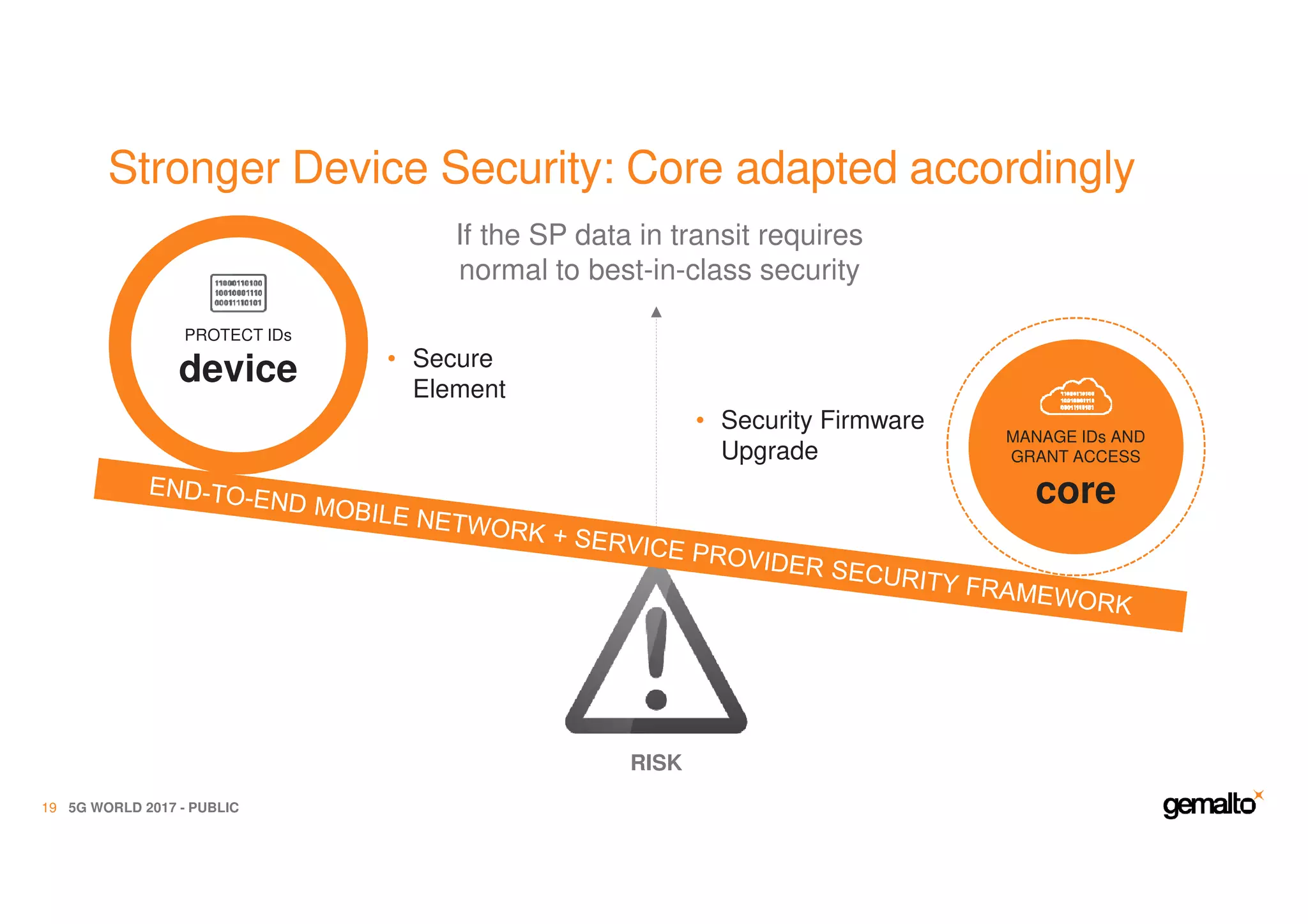
The document outlines the importance of security in 5G networks, emphasizing the need for a chain of trust from devices to the cloud. It discusses the essential security challenges and solutions, focusing on enhanced mobile broadband, network slicing, and the integration of software licensing management. Gemalto plays a crucial role in securing these networks by providing user authentication, data encryption, and comprehensive protection strategies tailored to various network segments.