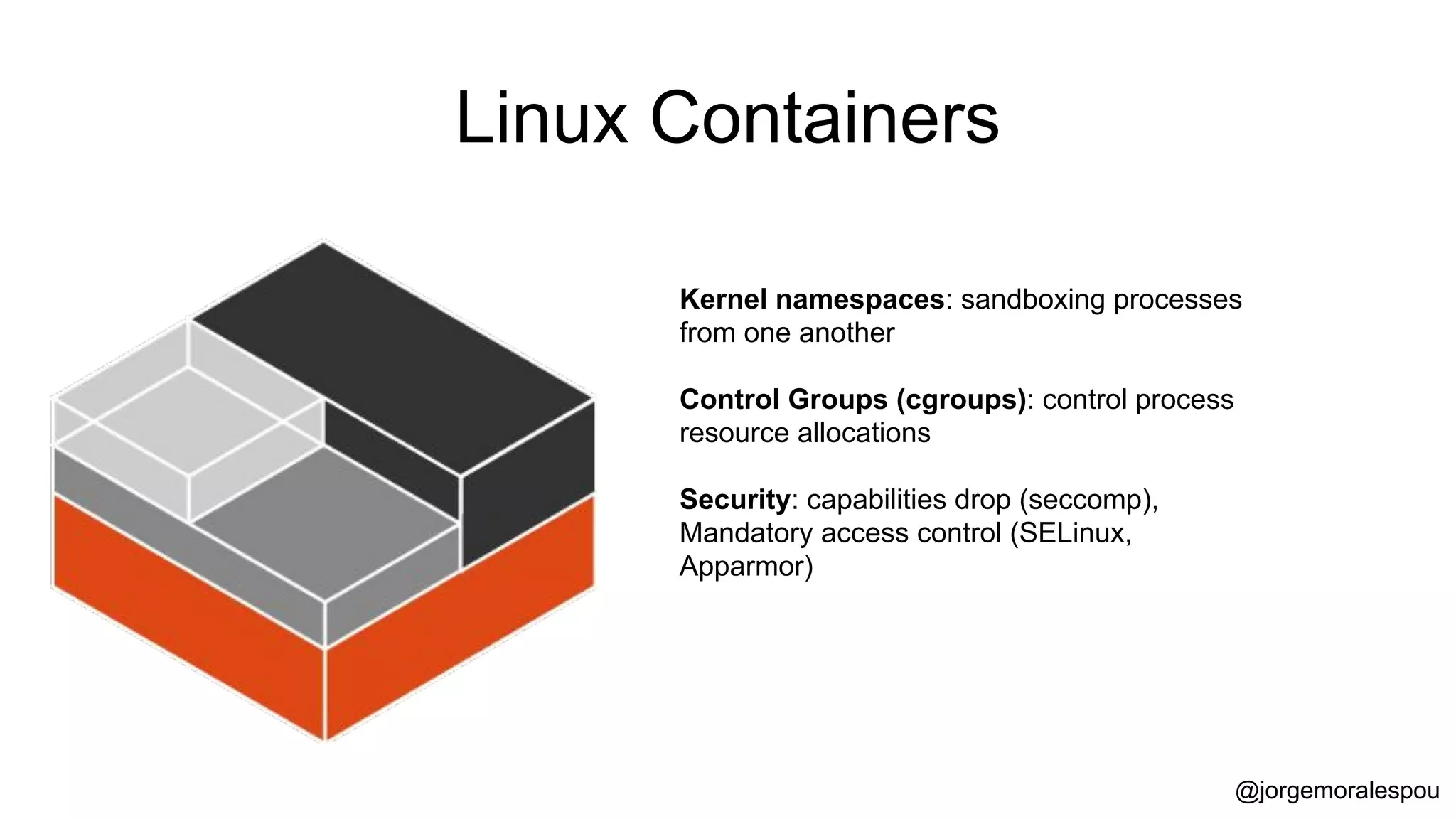
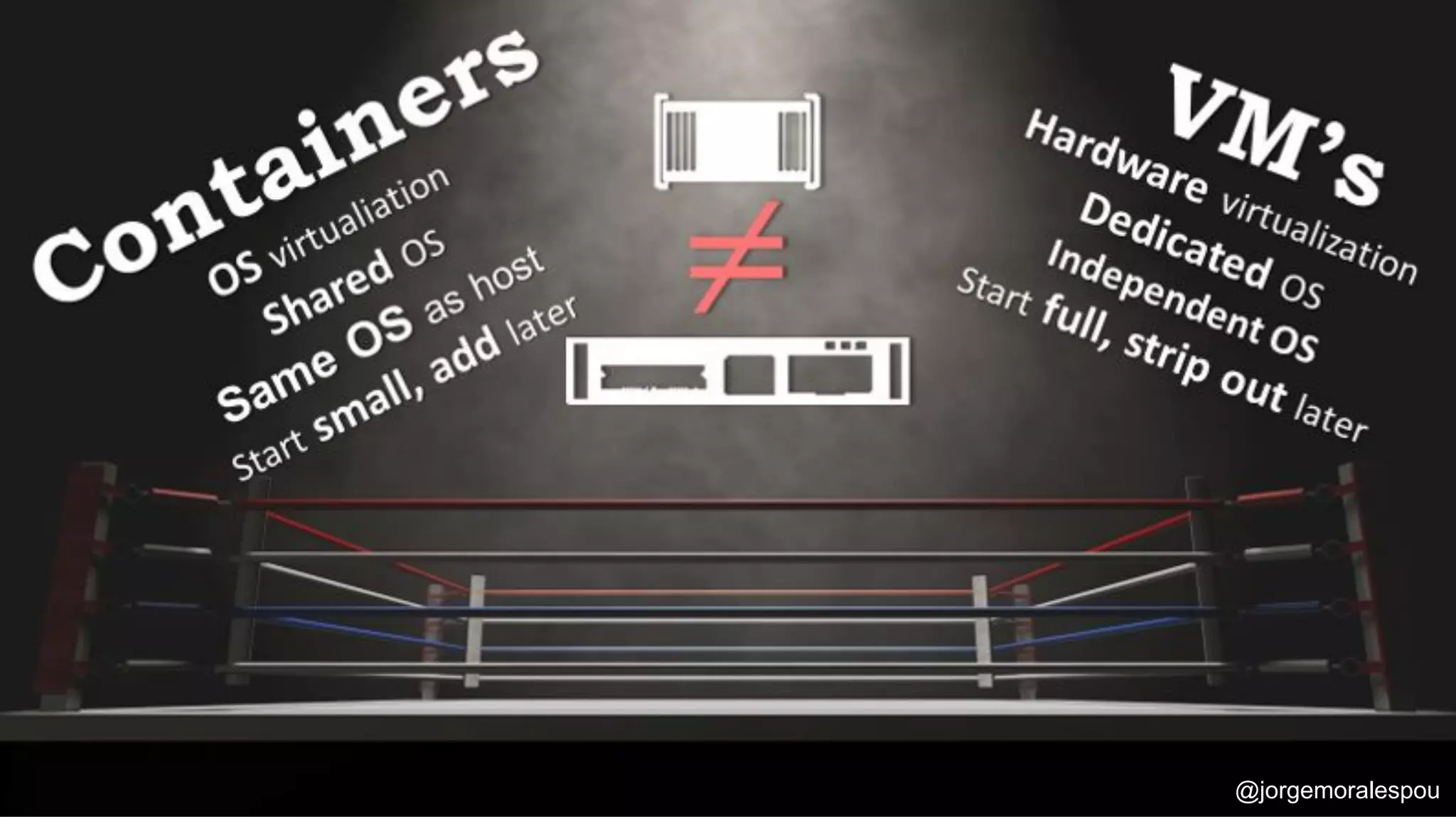
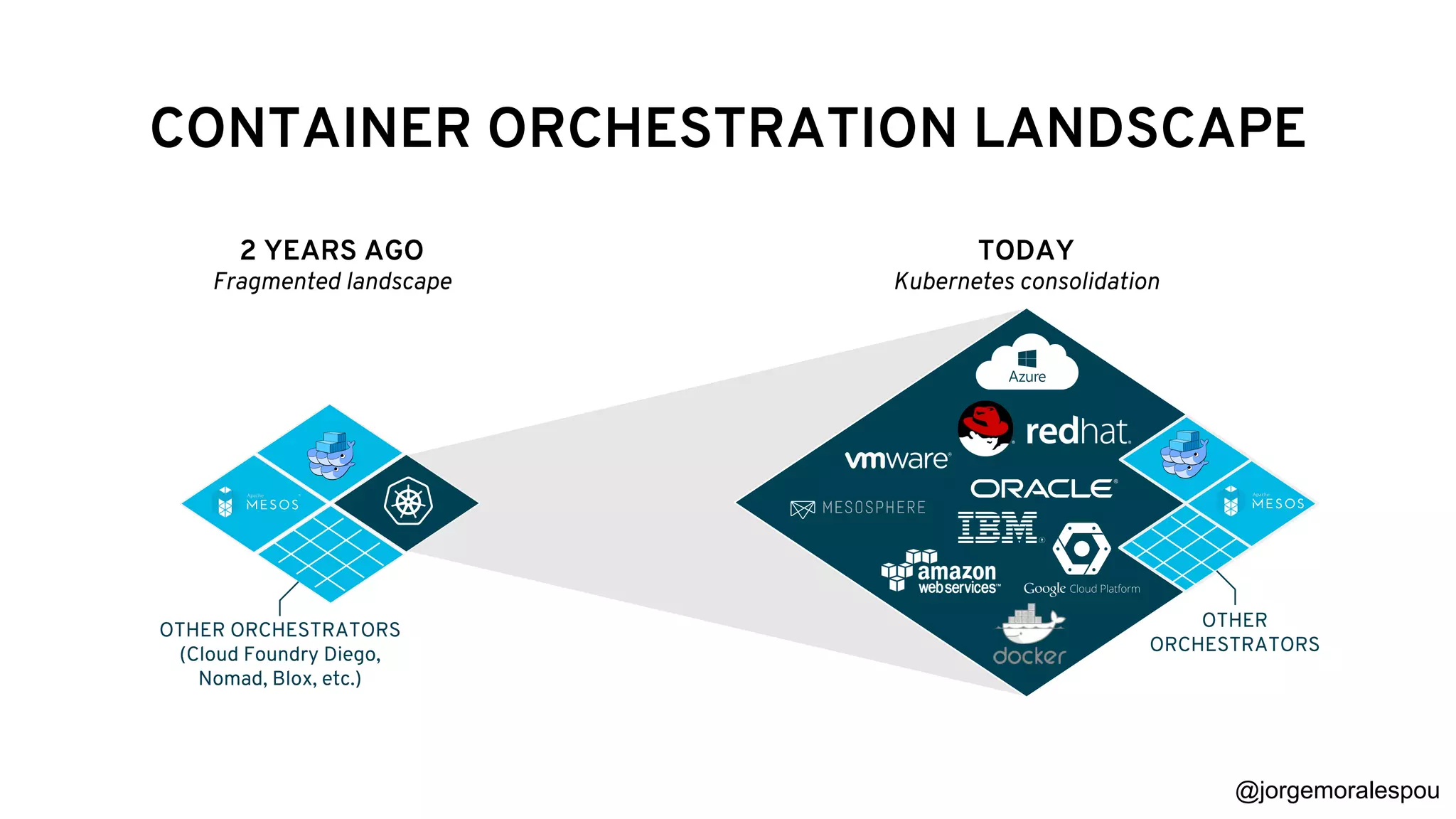
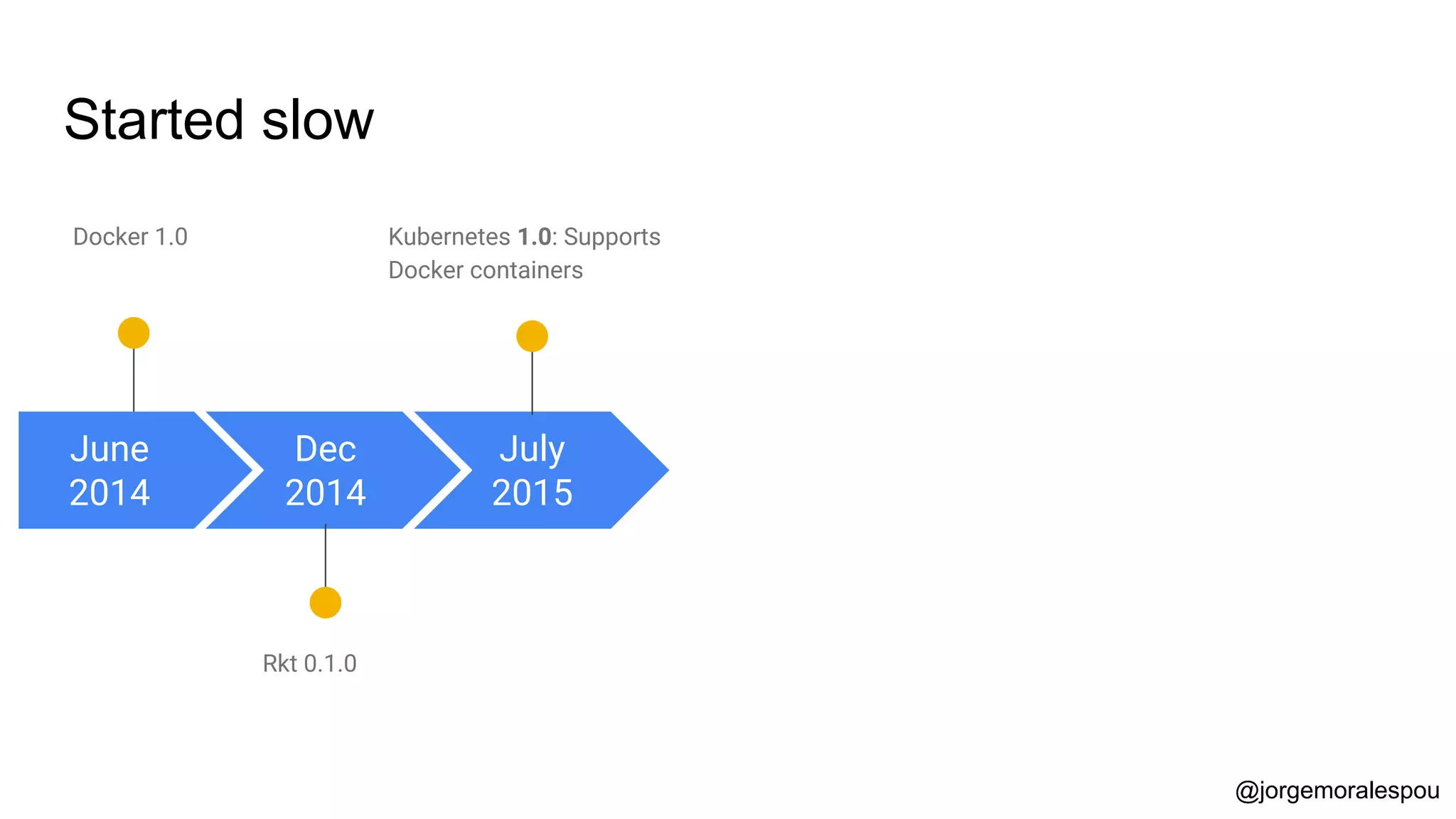
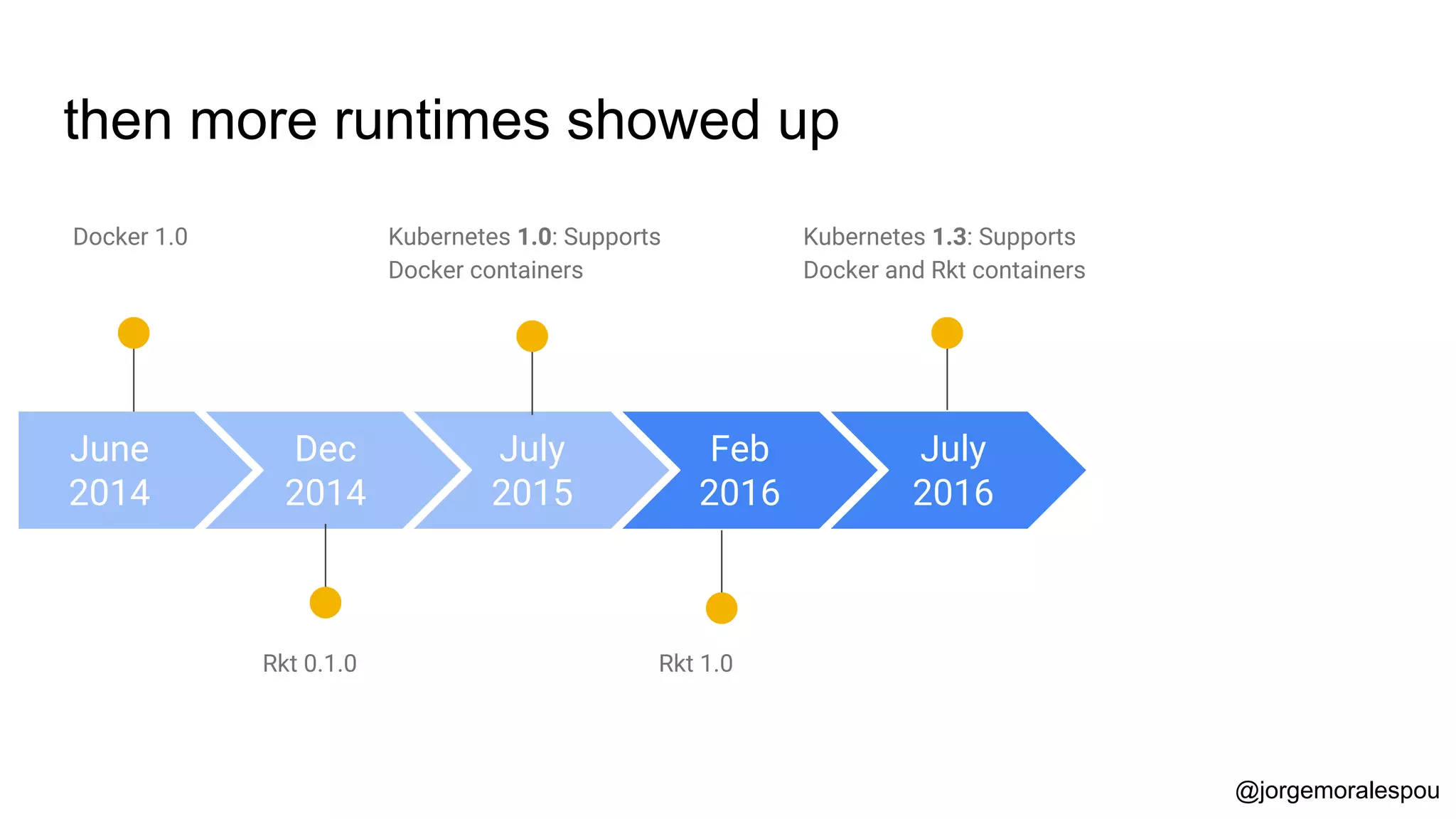
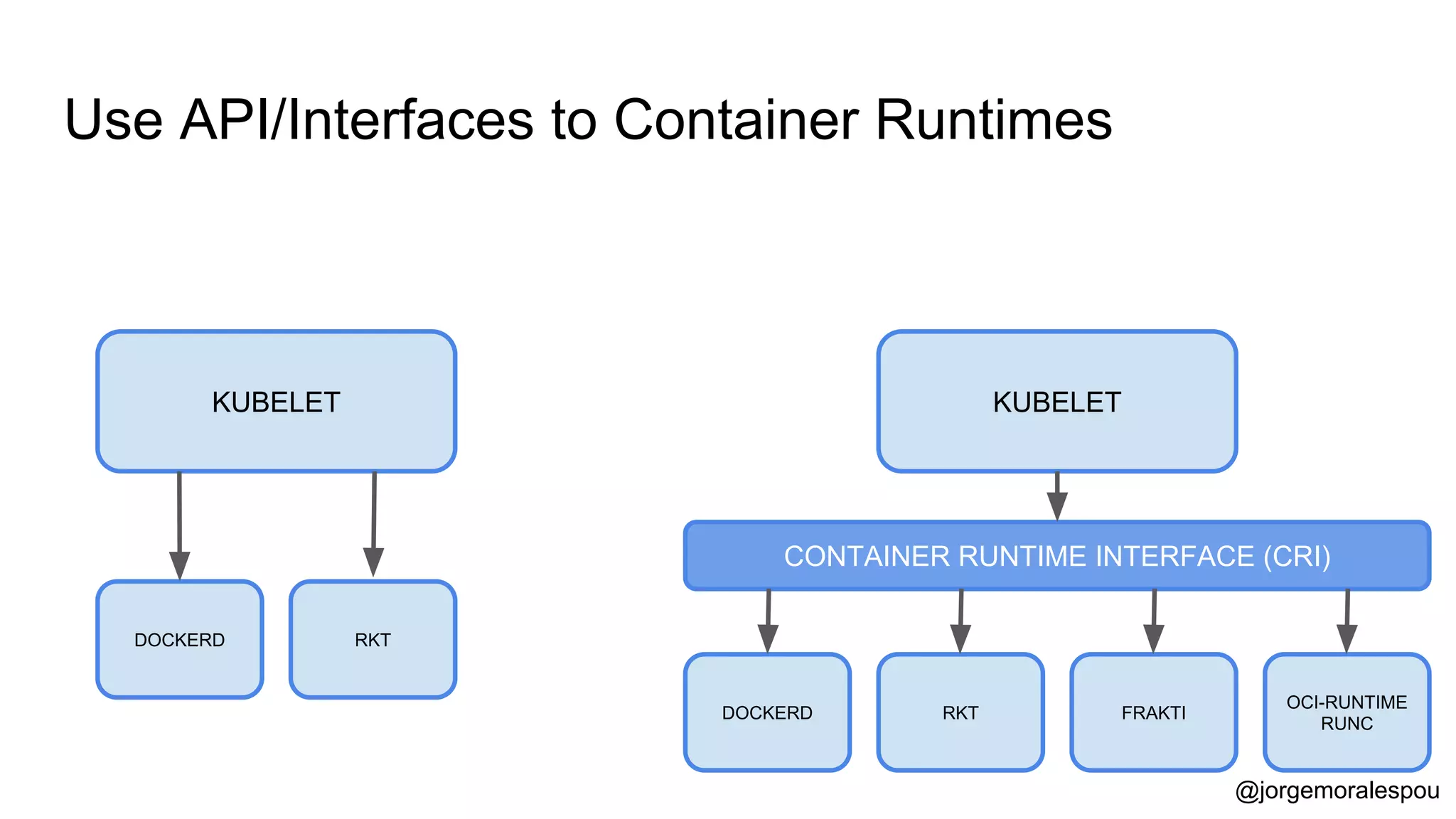
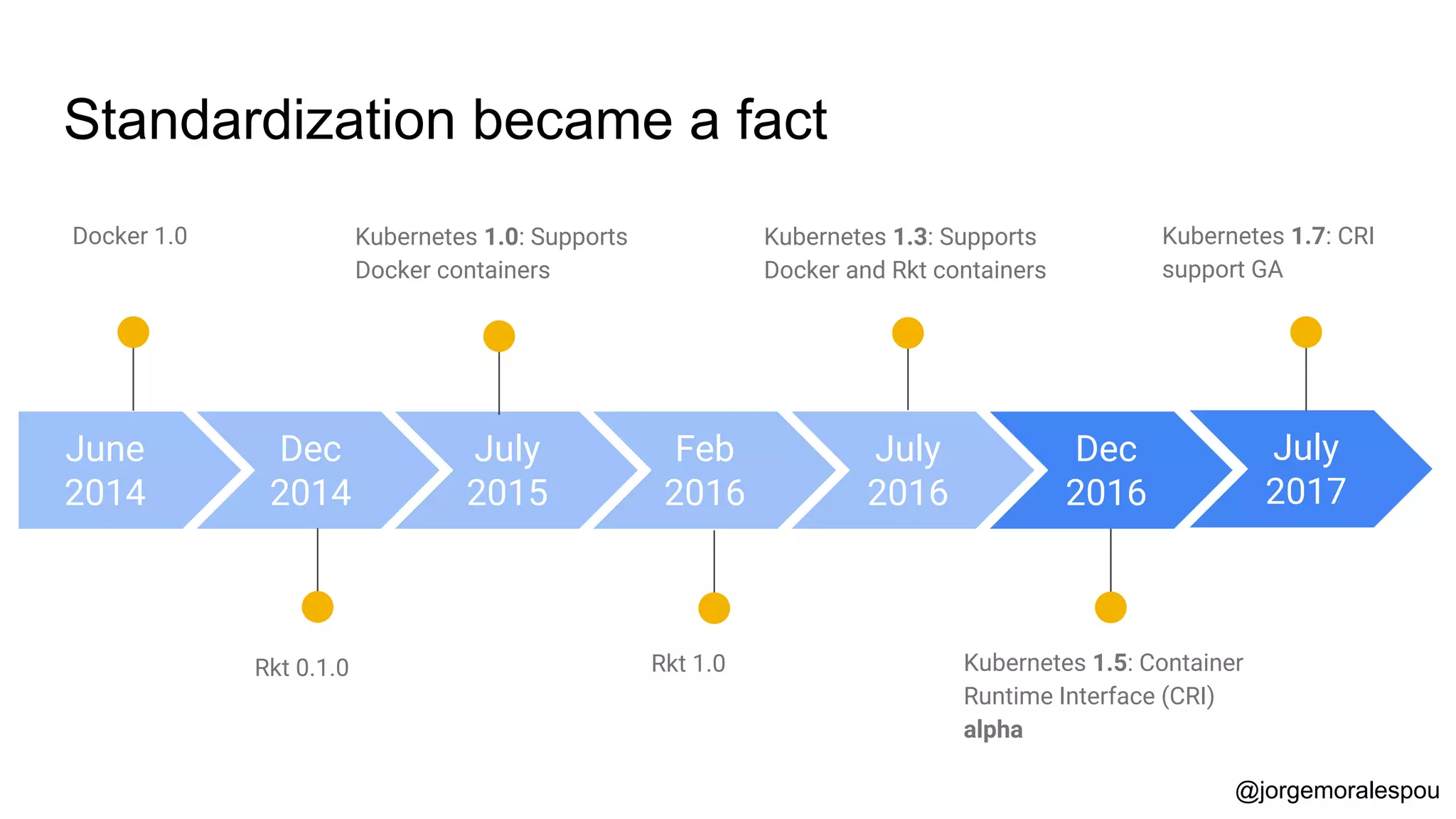
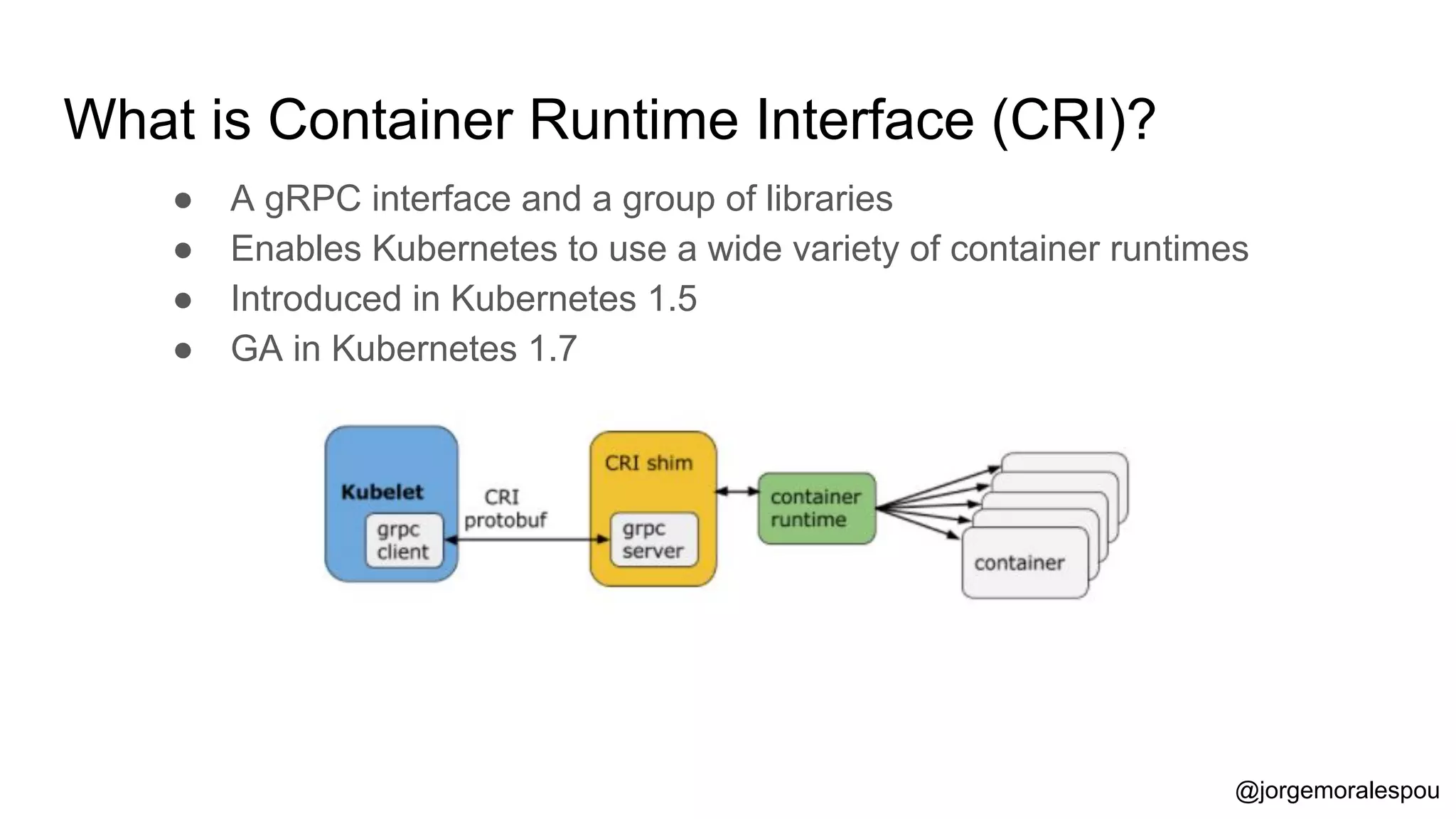
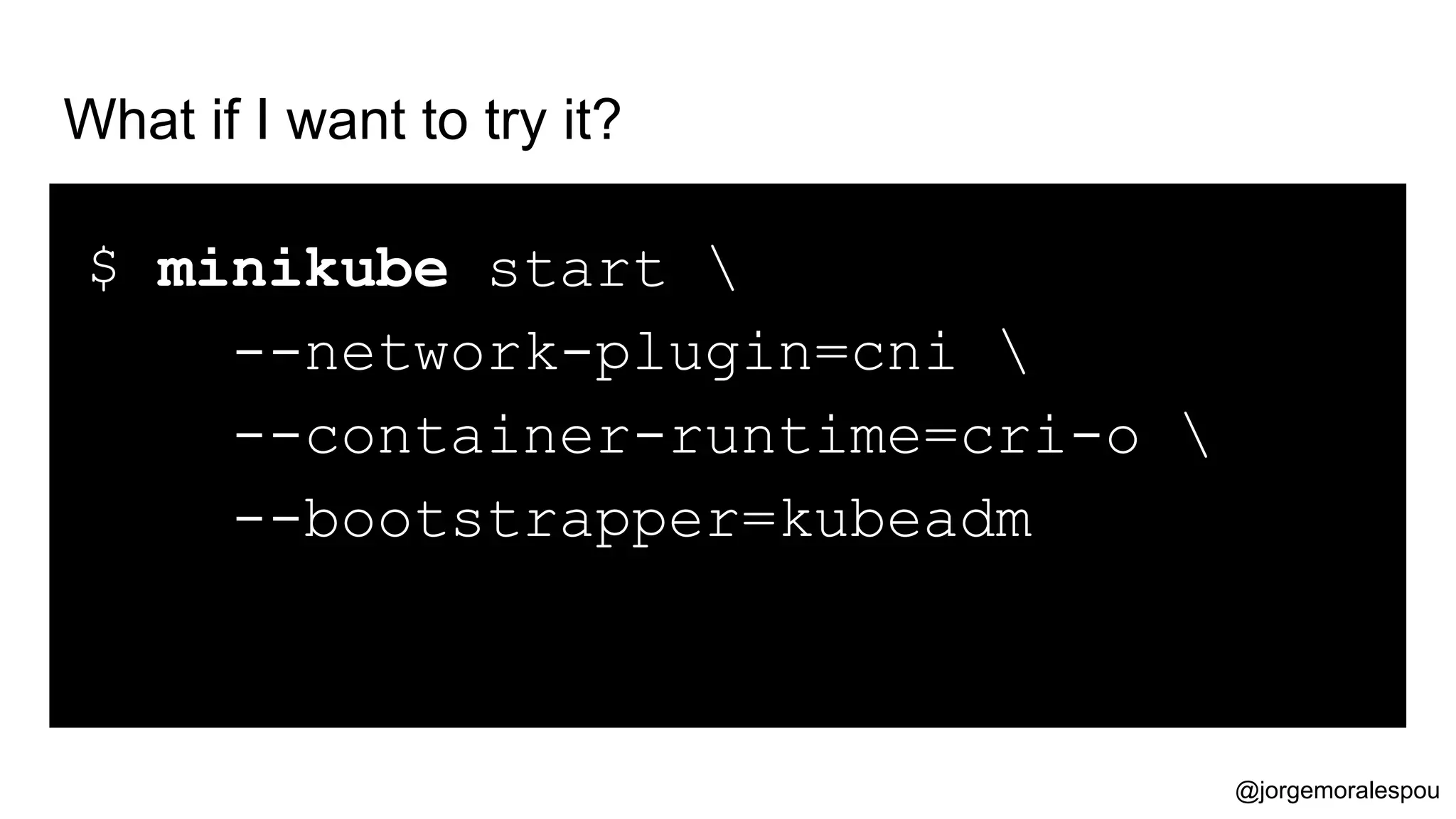
The document discusses the evolution and standardization of container management in a Kubernetes environment, emphasizing the Container Runtime Interface (CRI) introduced in Kubernetes 1.5 and its impact on container orchestration. It highlights the benefits and methodologies of building container images without relying on a Docker daemon through tools such as Buildah, Kaniko, and Podman. Additionally, various approaches to Dockerfile and Dockerfile-less builds are presented, showcasing their pros and cons in the context of developer experience and efficiency.

















![skopeo
● Copy images from/to (multiple transports/storages):
○ containers-storage:docker-reference
○ dir:path
○ docker://docker-reference
○ docker-archive:path[:docker-reference]
○ docker-daemon:docker-reference
○ oci:path:tag
○ ostree:image[@/absolute/repo/path]
● Inspect images
● Delete an image from a repository
● Standalone binary / No daemon running
● Perfect for pipelines (e.g. Jenkins)
@jorgemoralespou](https://image.slidesharecdn.com/buildandrunapplicationsinadockerlesskubernetesworld-devconf-india-18-180805071518/75/Build-and-run-applications-in-a-dockerless-kubernetes-world-DevConf-India-18-29-2048.jpg)



![“Our ancestors called it
magic, but you call it
[computer] science.
I come from a land where
they are one and the same.”
—THOR](https://image.slidesharecdn.com/buildandrunapplicationsinadockerlesskubernetesworld-devconf-india-18-180805071518/75/Build-and-run-applications-in-a-dockerless-kubernetes-world-DevConf-India-18-35-2048.jpg)