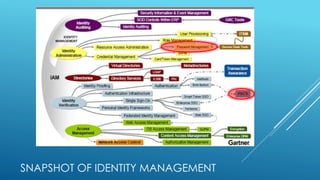
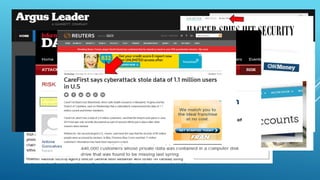
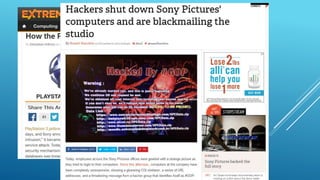
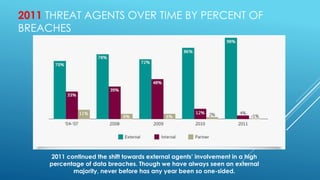
This document discusses trends in data breaches and cybersecurity threats. It notes that data breaches have been doubling in cost year-over-year, now averaging over $5.5 million per breach and $200 per compromised record. While external agents were responsible for most breaches in 2011, retailers experienced many breaches in 2013. The document advocates for educating employees, implementing two-factor authentication, developing strong and changing passwords, having an incident response plan, and exploring new security technologies using machine learning to help limit organizations' risk and reduce costs from breaches.