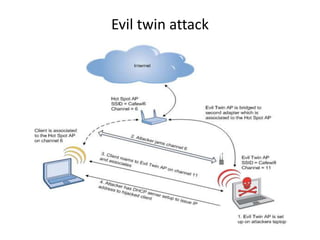
The document discusses various cybersecurity concepts, including OSI protocols, attacks like the evil twin attack and ARP poisoning, and cryptanalysis techniques for MS-CHAPv2. It also covers post-MITM attack vectors and reverse shell methods, detailing the steps attackers might use to exploit network vulnerabilities. Mitigation strategies such as SSL certificate pinning and proper configuration of network security measures are emphasized for protecting against these attacks.











![Cryptanalysis of MS-CHAPv2
ChallengeHash = SHA1(random|| username)[0:8]
ChallengeHash
ChallengeResponse
Note: Original complexity analysis has been done by Moxie Marlinspike](https://image.slidesharecdn.com/gvjno45qrwiqfbal2i57-signature-d94f514d124e6f4b977c9cbe170e7b1ee5bffed4f15e3d52ac0eb65e922954b4-poli-161211082846/85/Breaking-Bad-Enterprise-Network-Security-13-320.jpg)






![Certificate Collision Attack
CA
DomainA
isCA?
CSR Ekey[Sha(csr.tbs)]
DomainA
isCA?
DomainA
isCA?
CertificateCSR.TBS
Sha( domainA.csr ) Sha( domainB.csr )
md5( domainA.csr
)
md5( domainB.csr )
True
False
MD5 Collision
Certificate Collision](https://image.slidesharecdn.com/gvjno45qrwiqfbal2i57-signature-d94f514d124e6f4b977c9cbe170e7b1ee5bffed4f15e3d52ac0eb65e922954b4-poli-161211082846/85/Breaking-Bad-Enterprise-Network-Security-20-320.jpg)
