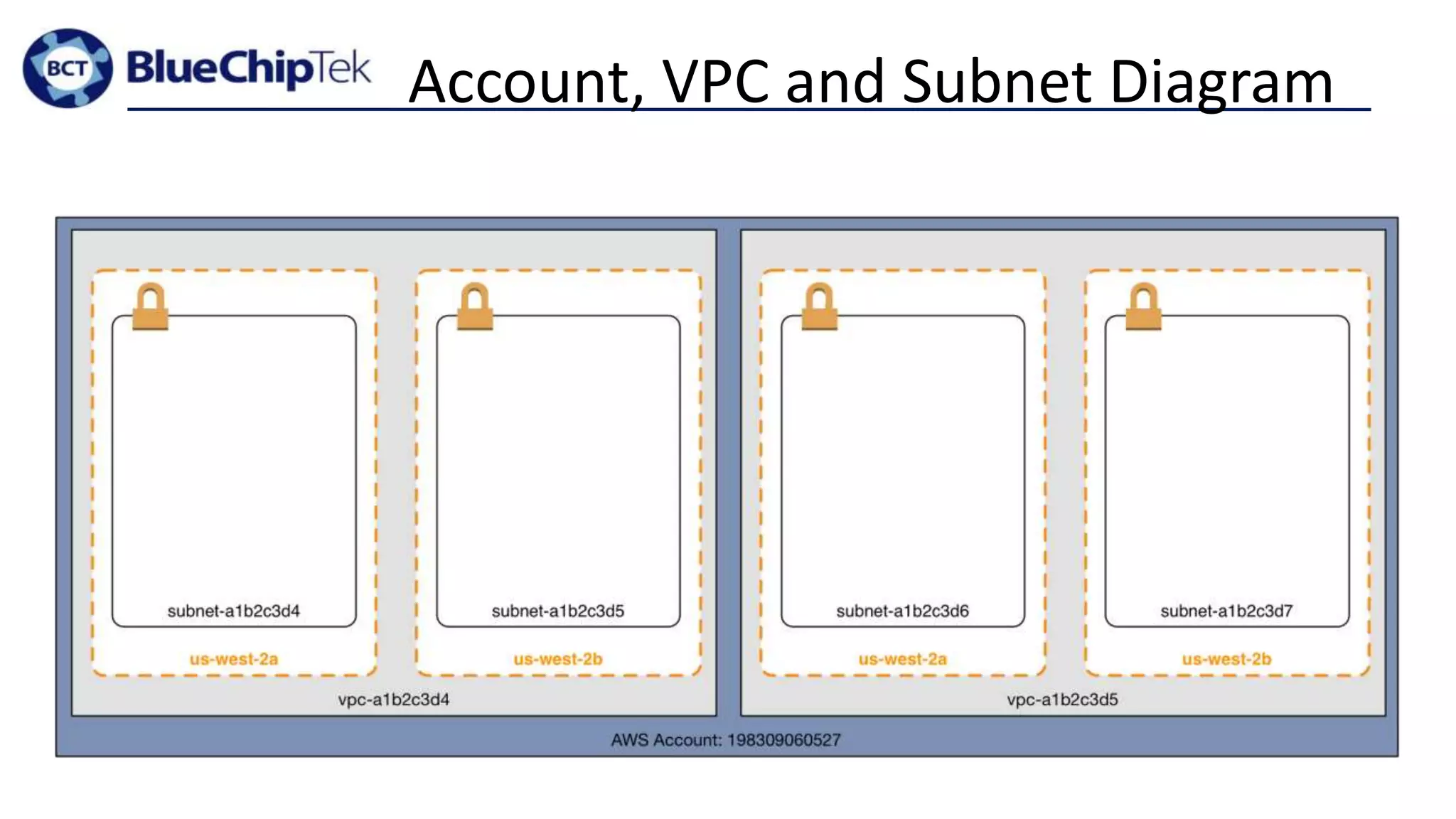
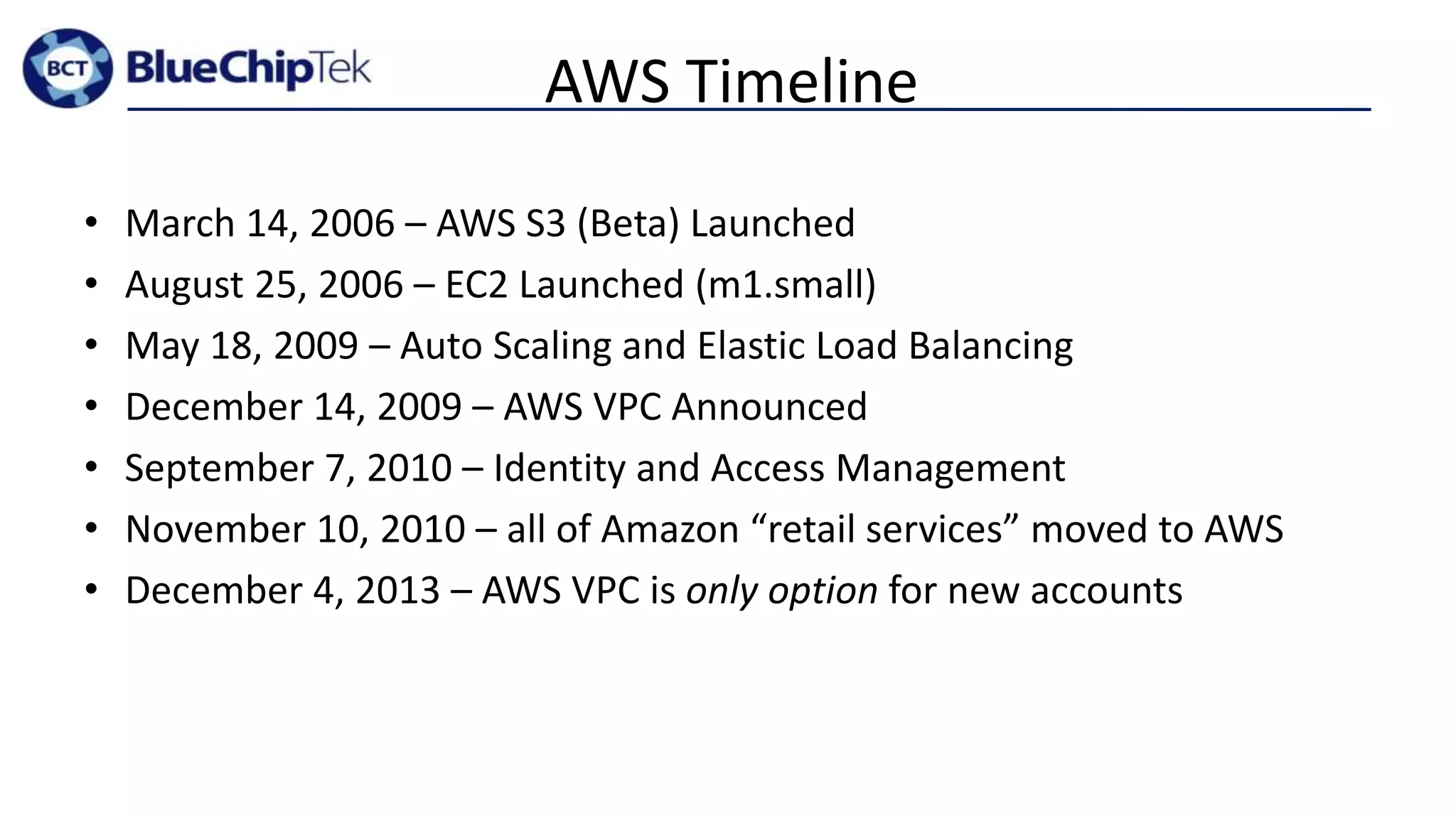
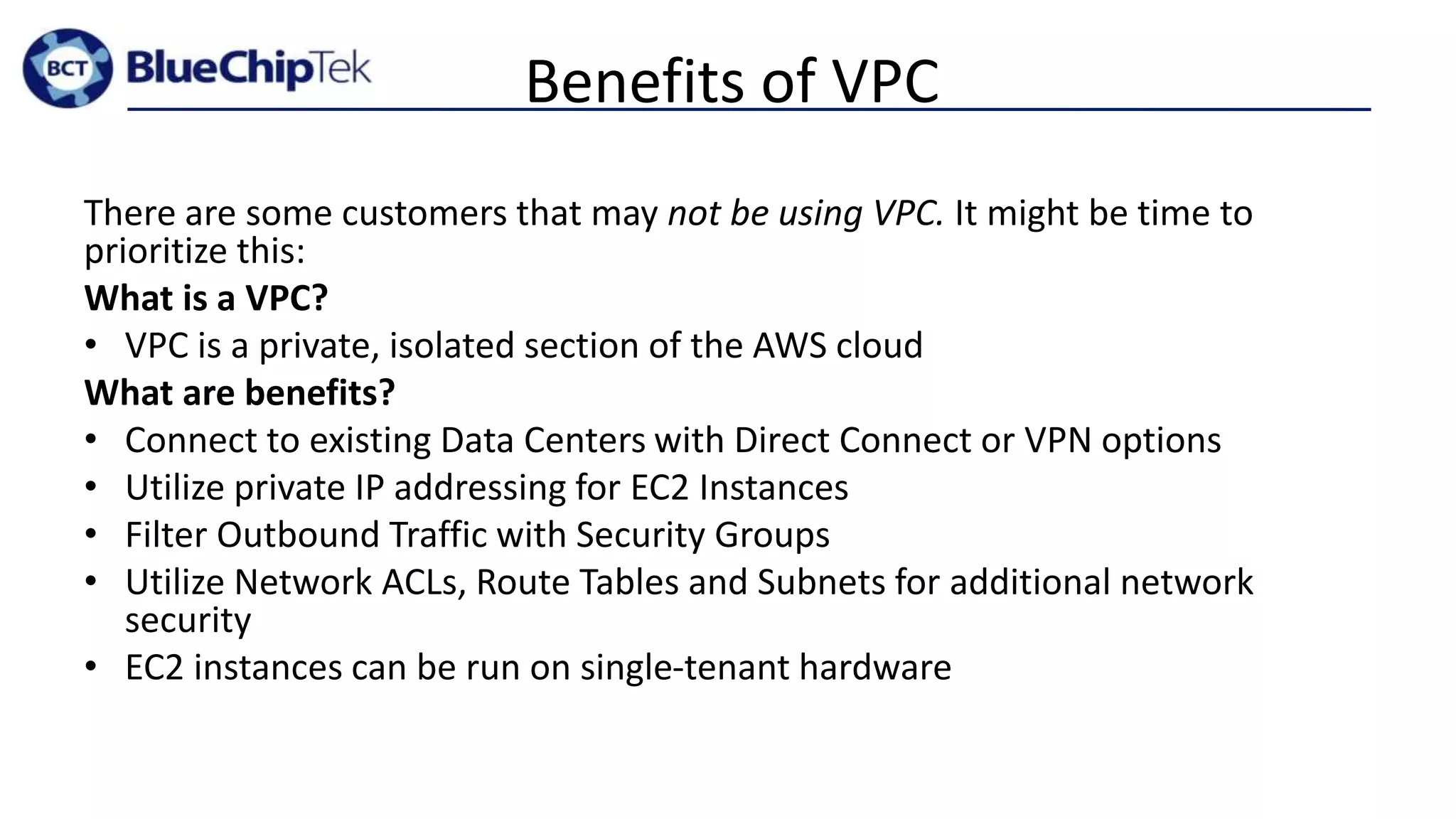
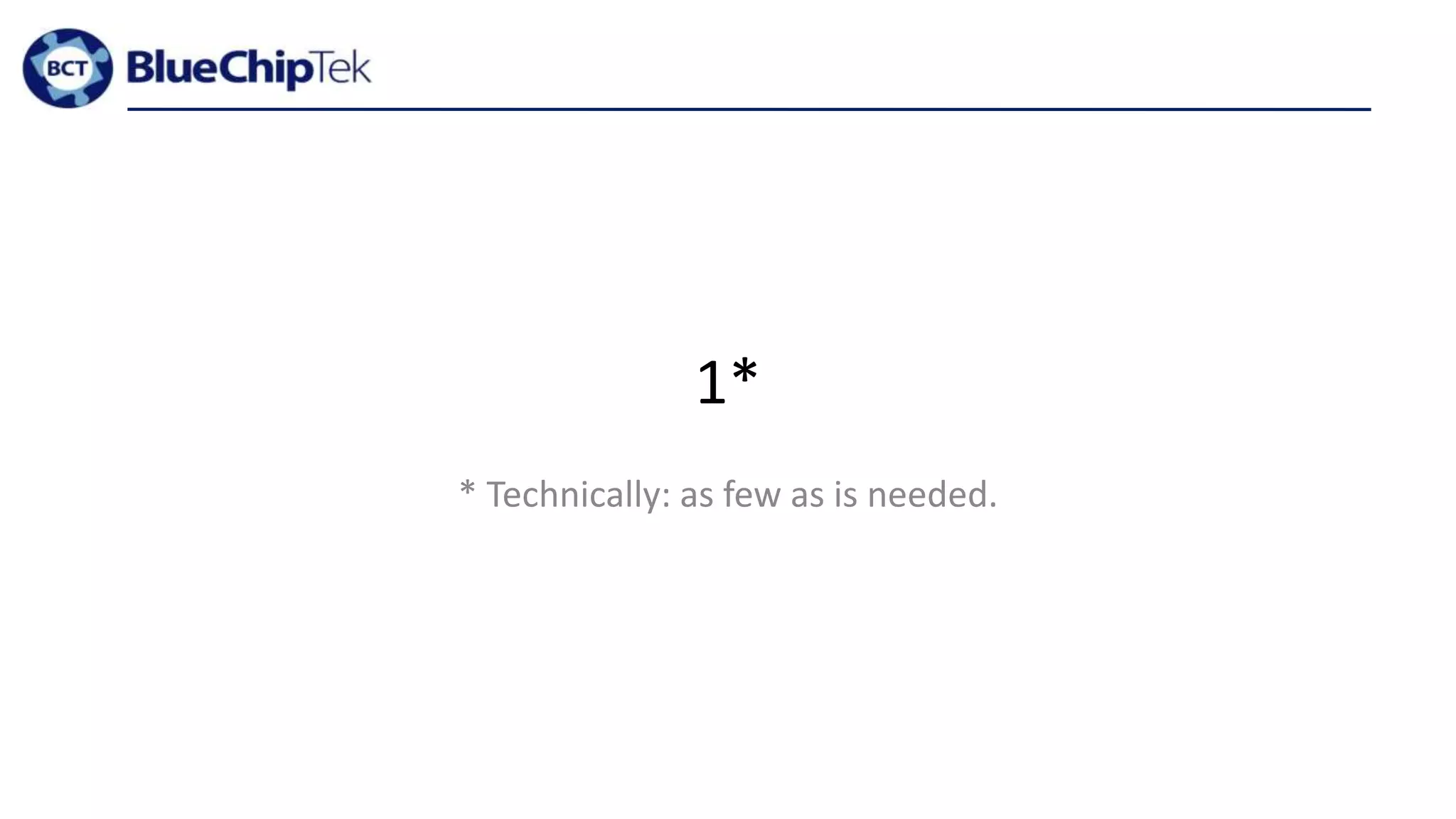
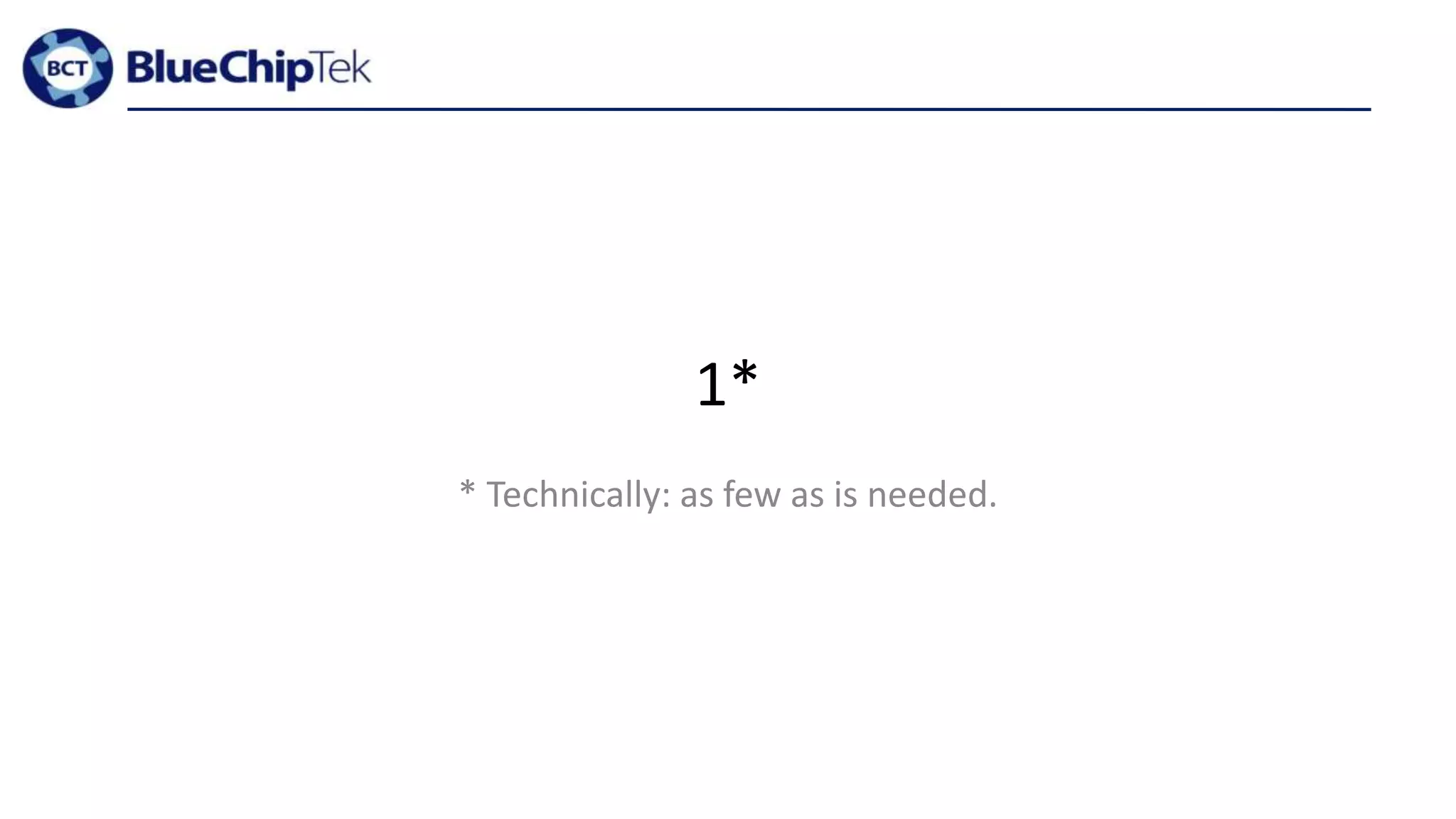
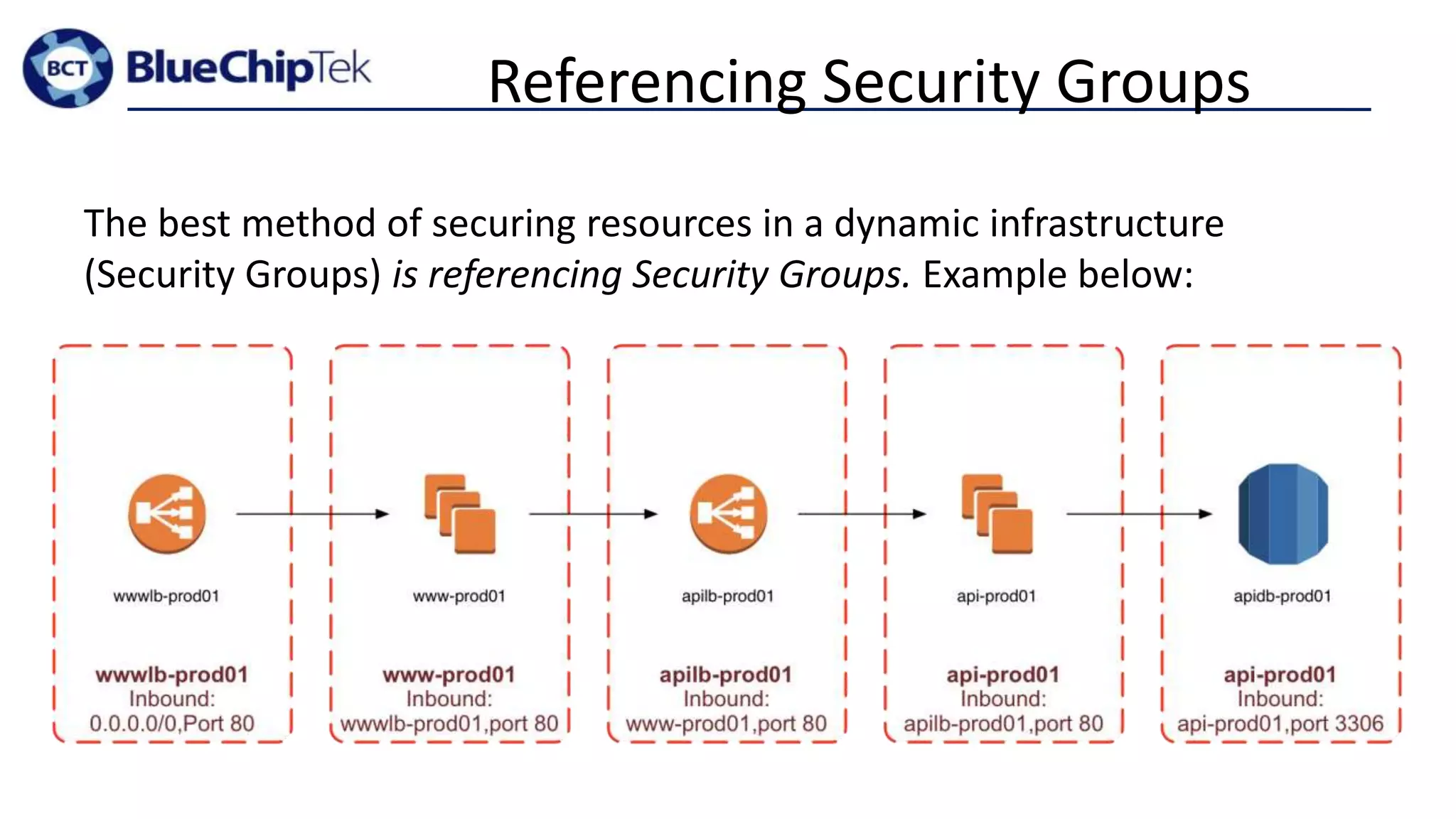
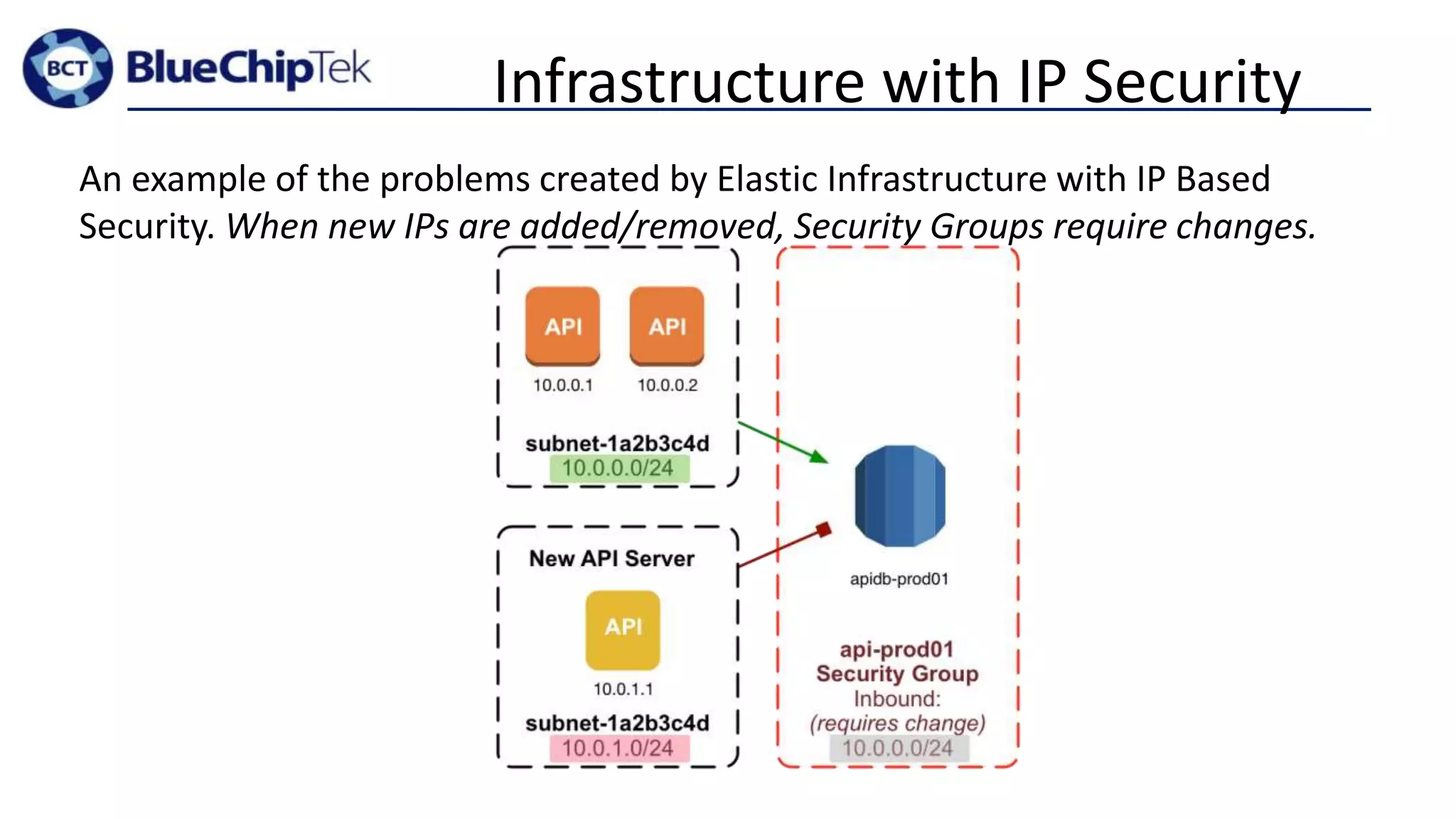
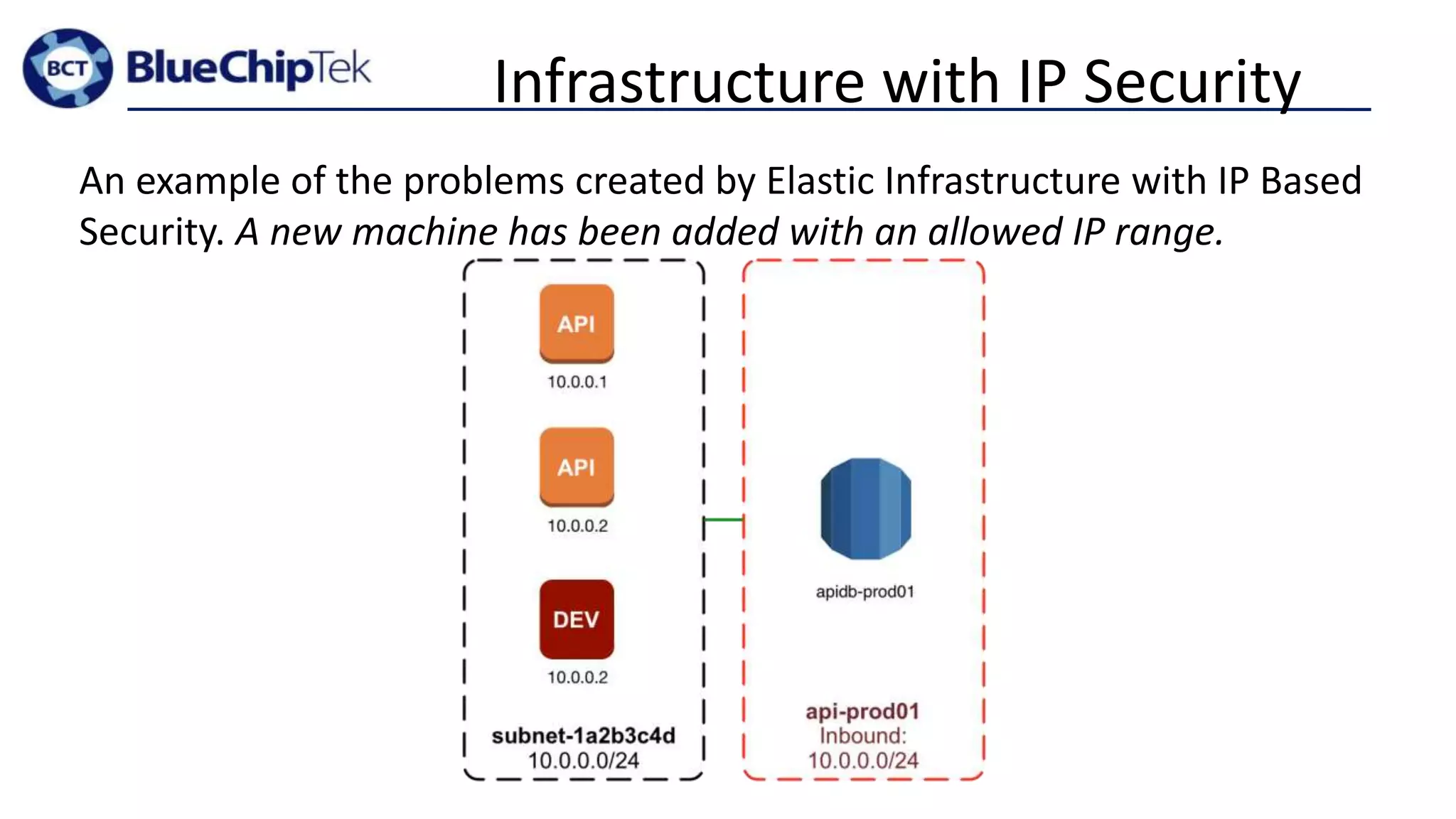
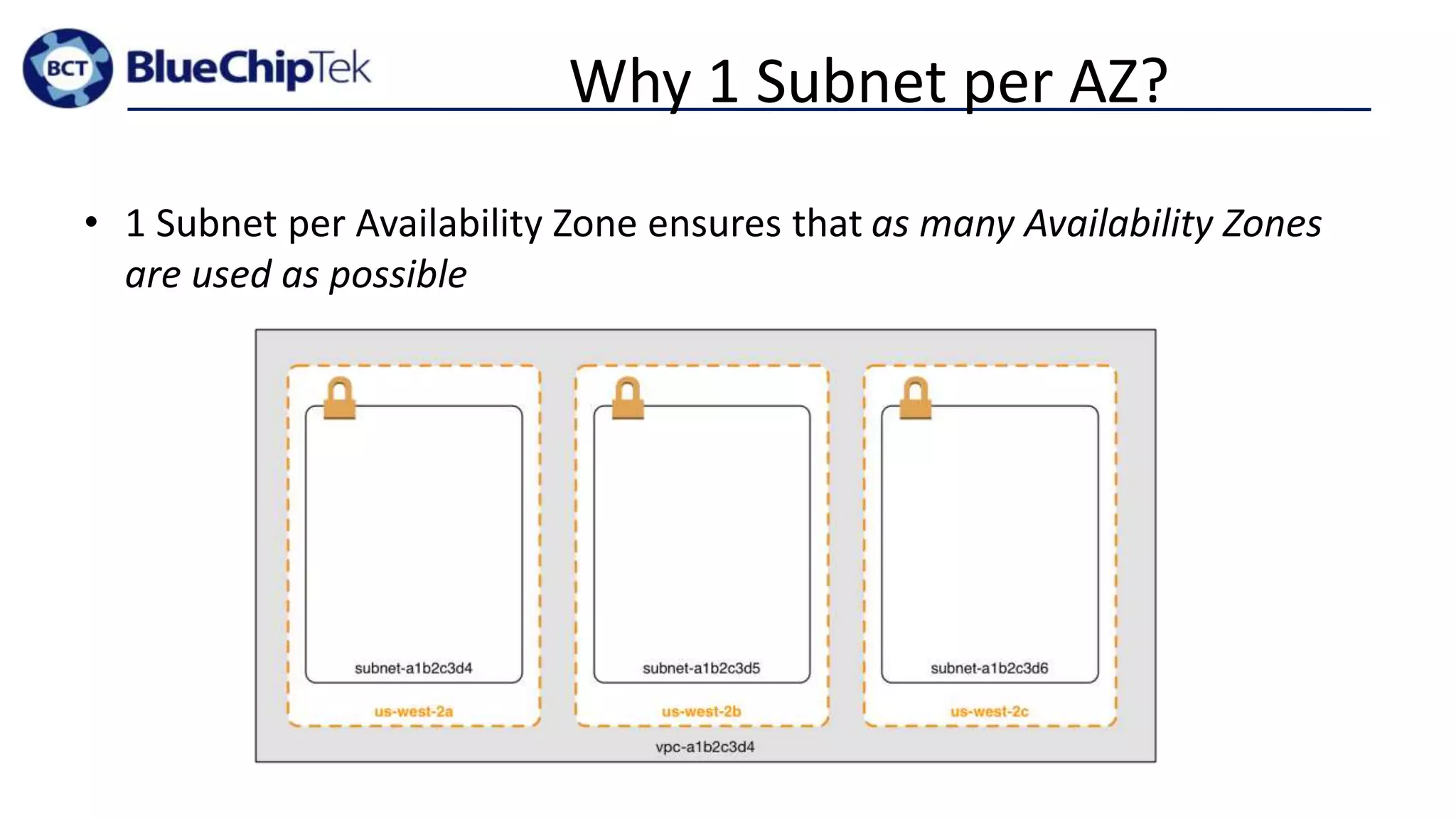
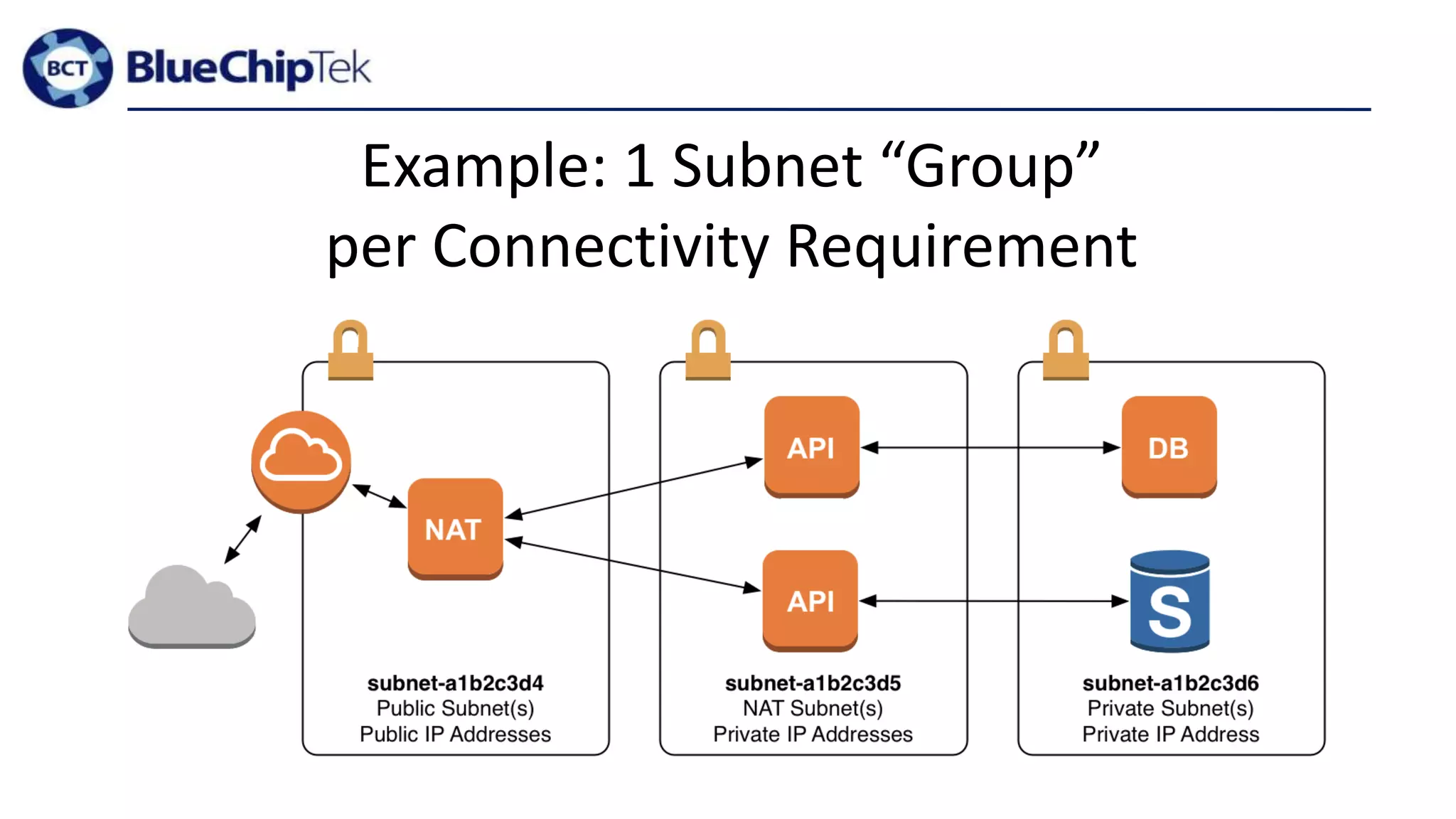
The document discusses account, VPC and subnet design for AWS infrastructure. It recommends starting with 1 AWS account, 1 VPC, and between 9-16 subnets, with 1 subnet per availability zone and 1 subnet group per connectivity requirement. This simple design focuses on security, flexibility and ease of administration while allowing for complexity to be added later if needed.