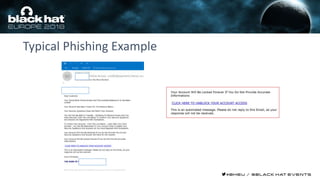
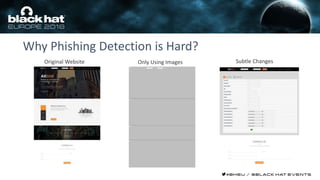
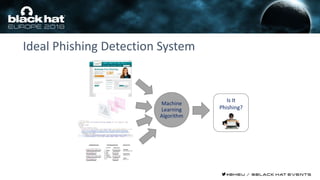
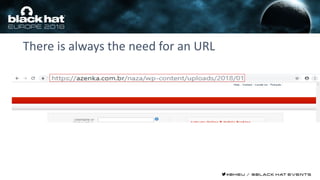
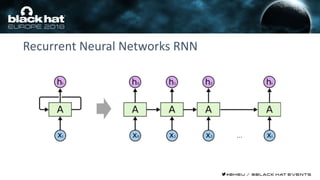
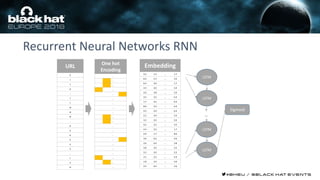
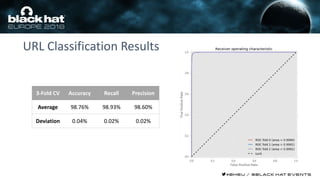
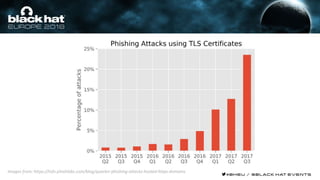
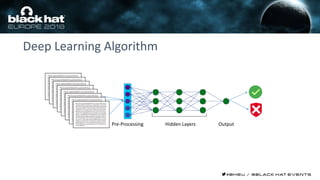
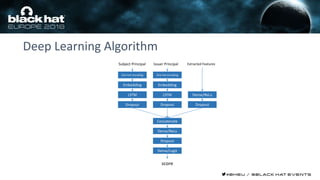
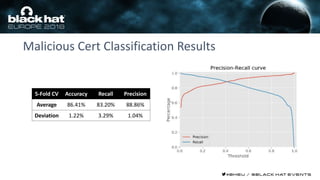
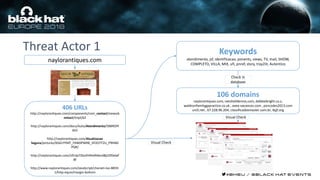
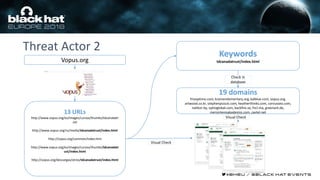
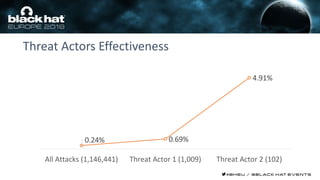
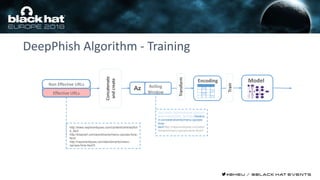
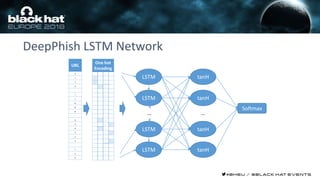
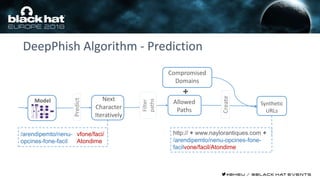
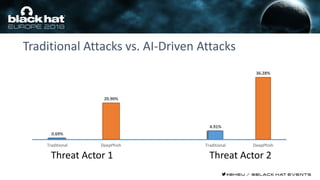
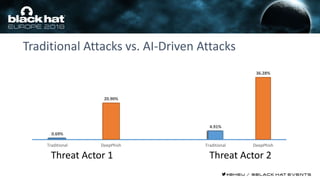
This document discusses using machine learning and deep learning techniques to detect malicious URLs and TLS certificates. It describes building recurrent neural network models to classify URLs and certificates based on their content. The models were able to achieve over 98% accuracy on URL classification and can be used to detect phishing URLs and malicious TLS certificates that aim to mimic legitimate ones. A demo of these techniques is also mentioned. The goal is to develop more robust detection of malicious AI that is trying to simulate legitimate behavior.