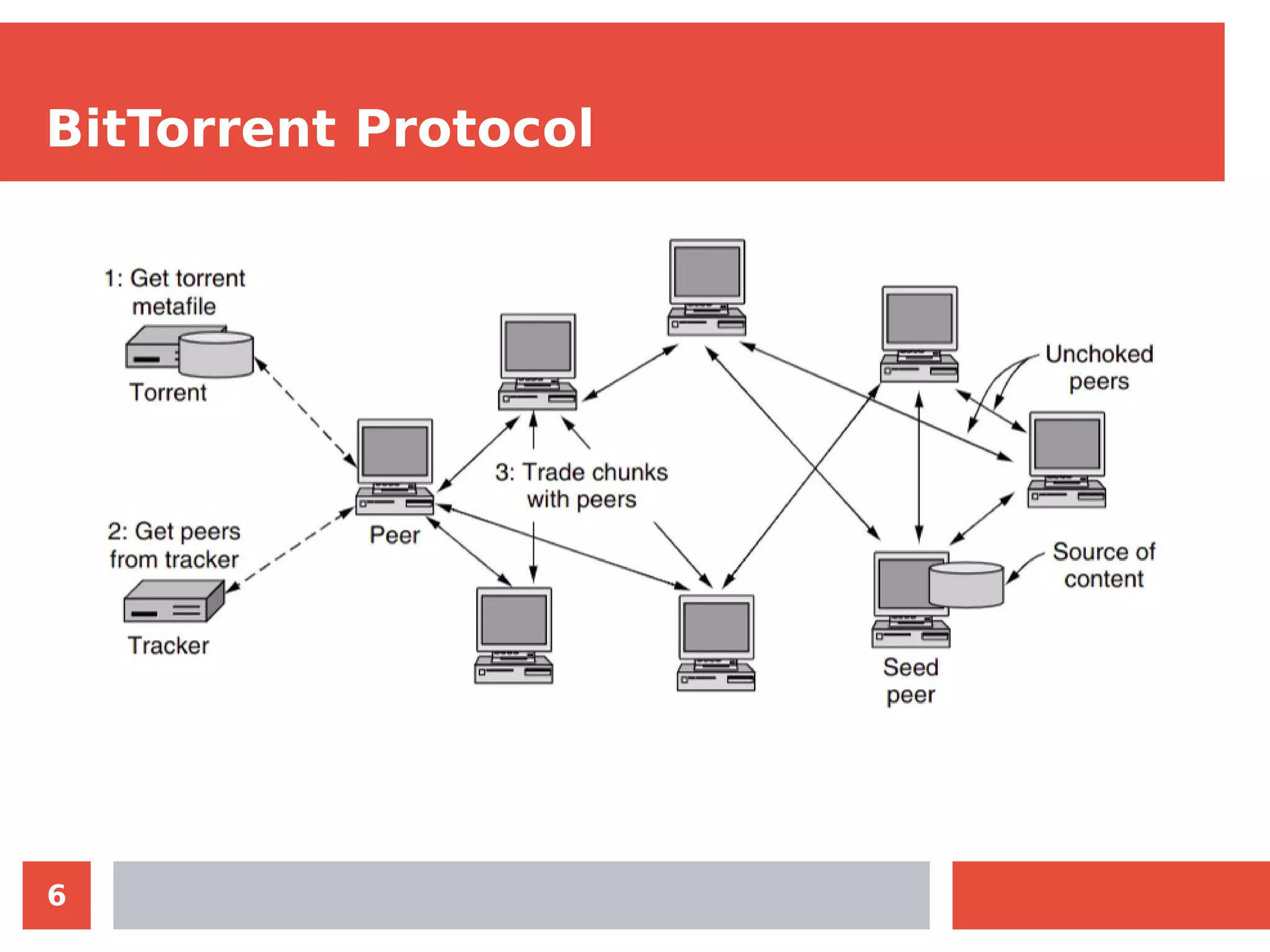
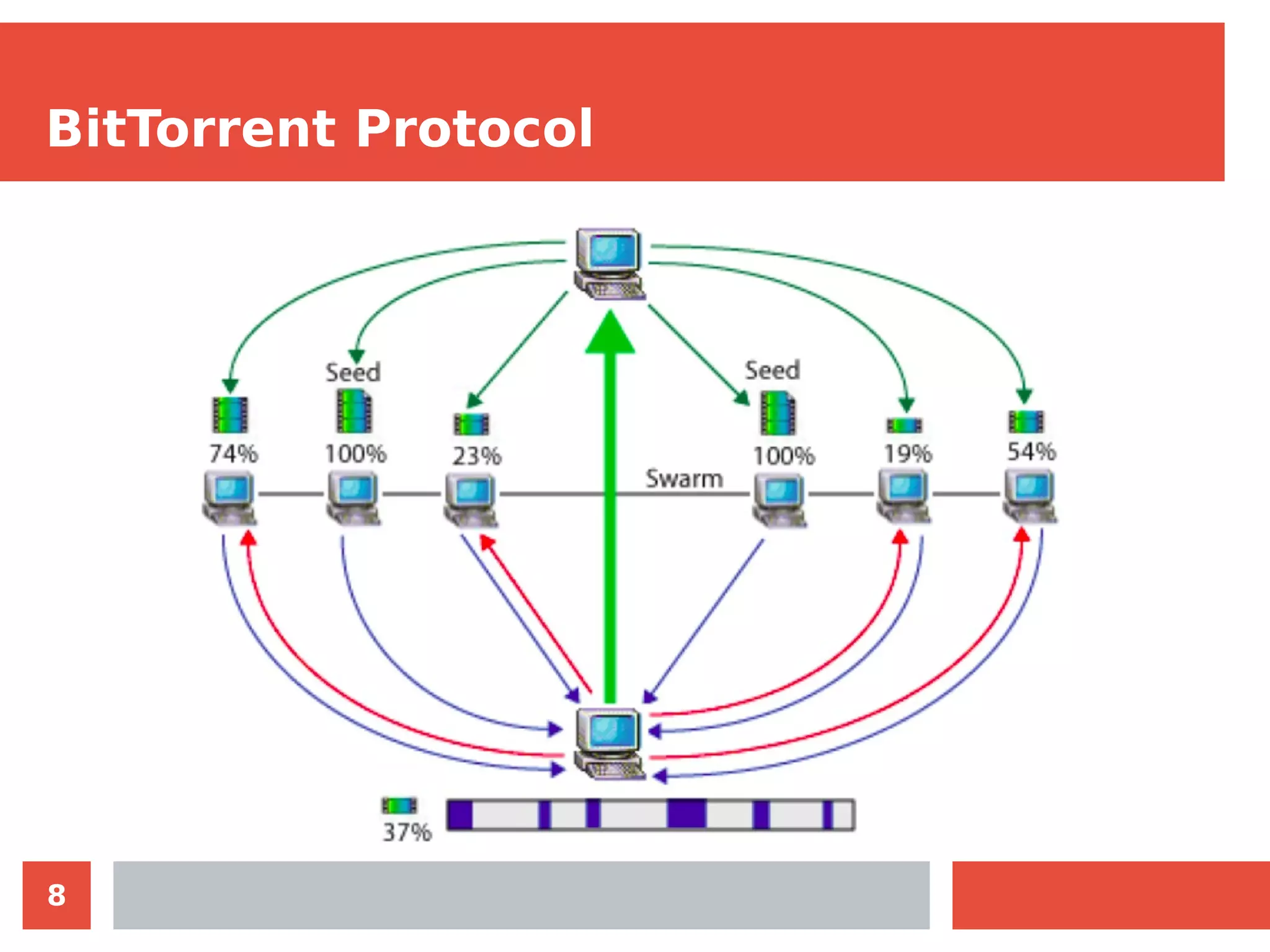
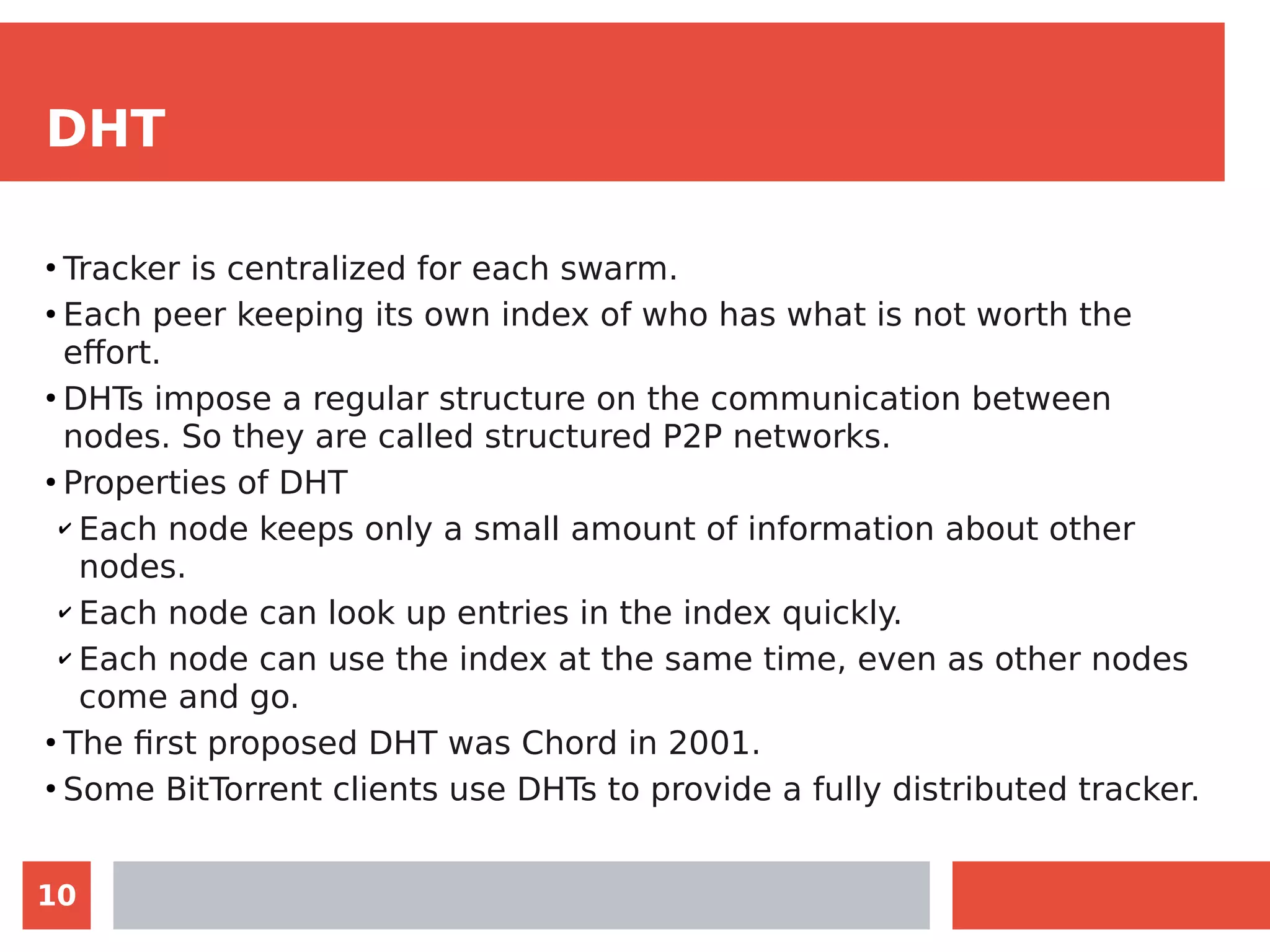
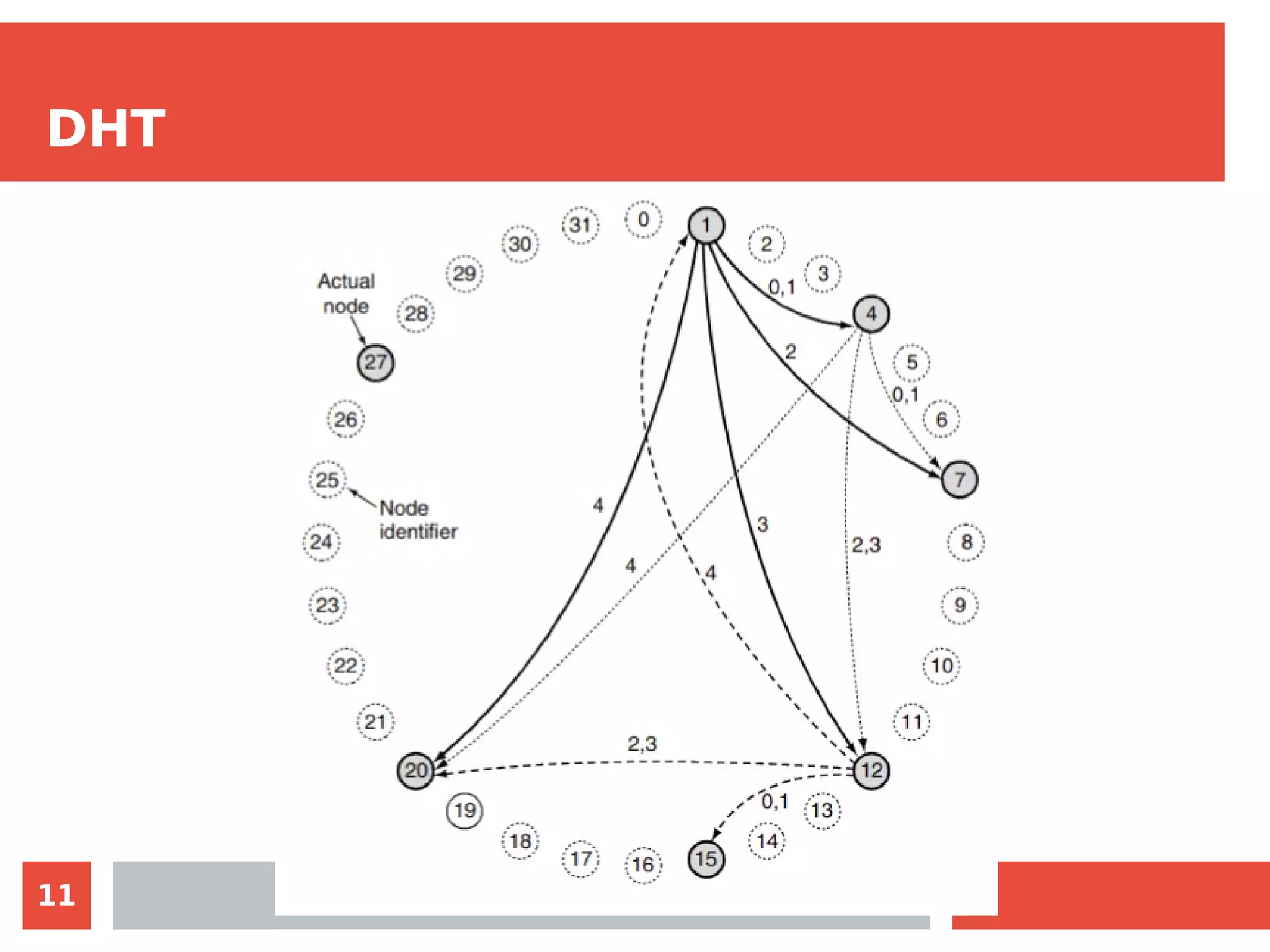
The document summarizes the BitTorrent protocol. It describes how peer-to-peer networks allow computers to pool resources for content distribution without a central point of control. It then explains that BitTorrent was developed in 2001 as a protocol for quick file sharing among peers. The key aspects covered are how torrent files allow peers to find content and verify integrity, how trackers maintain lists of peers sharing content, and how the protocol encourages uploading through rewarding peers with high download performance.