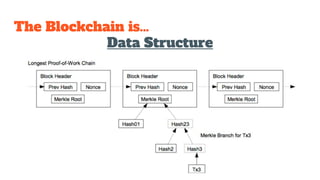
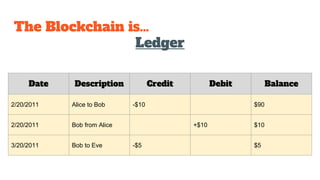
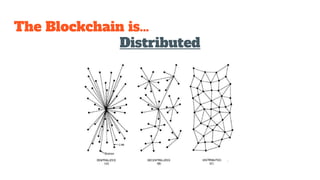
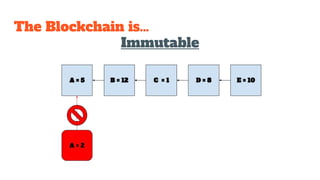
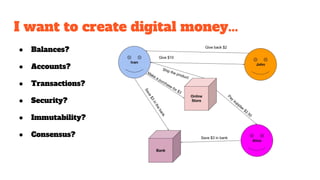
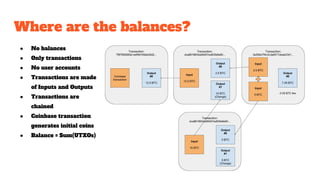
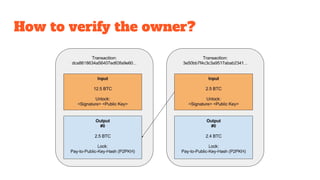
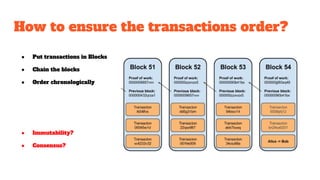
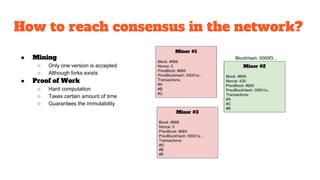
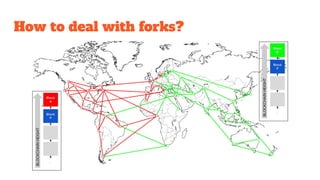
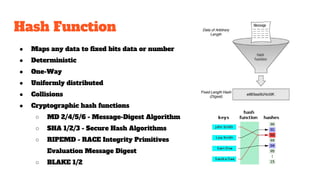
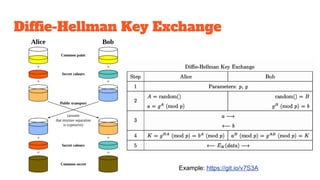
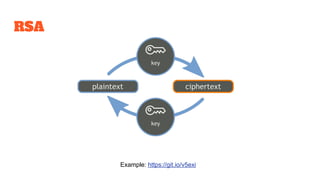
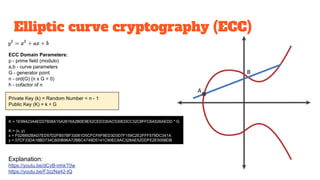
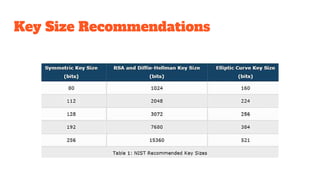
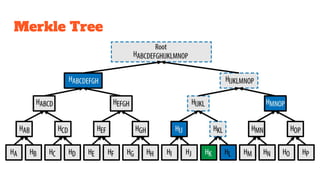
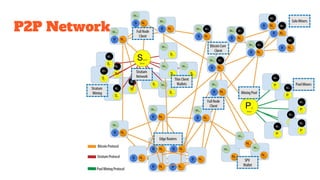
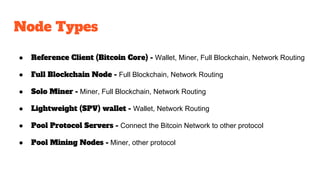
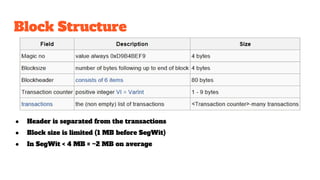
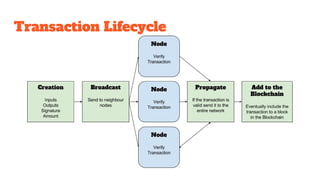
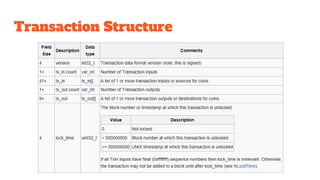
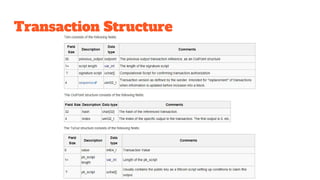
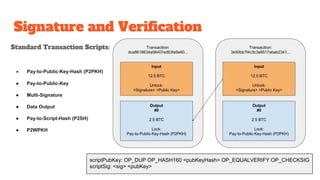
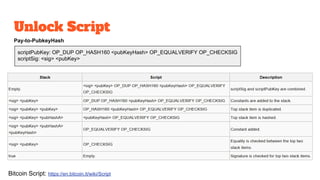
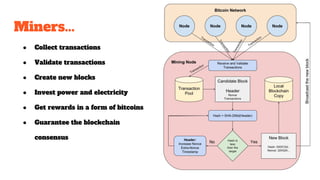
The document provides an in-depth analysis of Bitcoin's blockchain technology, explaining its decentralized nature, structure, and the cryptographic principles that secure it. It covers key aspects including transaction verification, mining, consensus mechanisms, cryptography, and wallet types within the Bitcoin ecosystem. Furthermore, it discusses network operations, block validation, and the lifecycle of transactions in the Bitcoin framework.