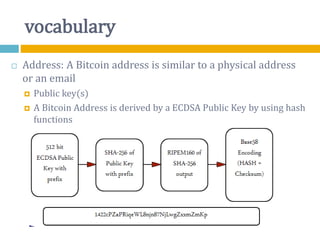
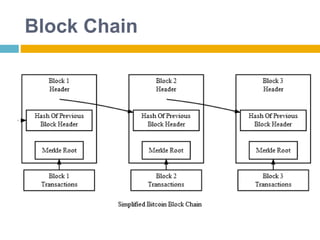
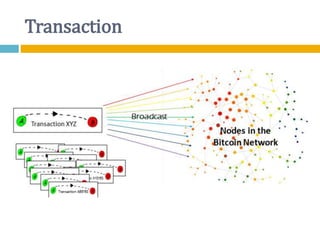
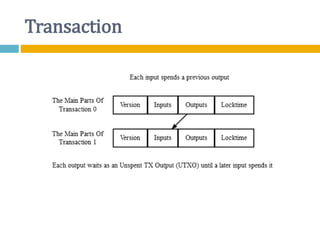
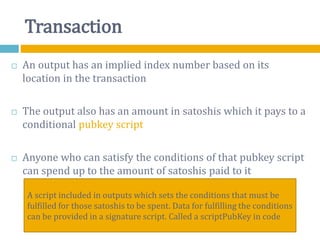
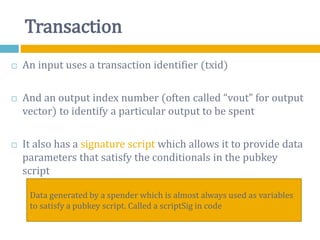
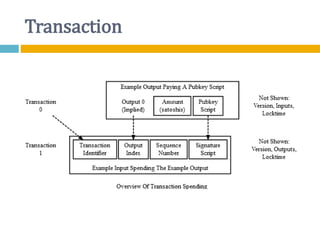
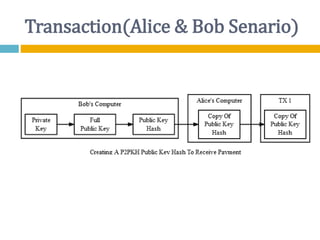
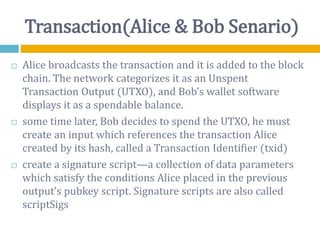
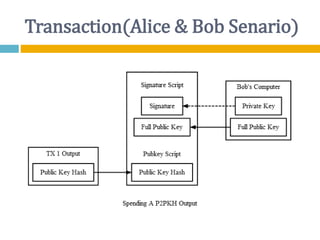
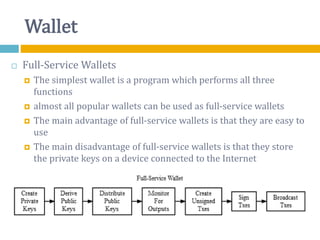
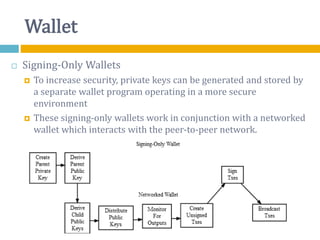
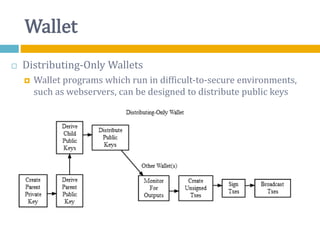
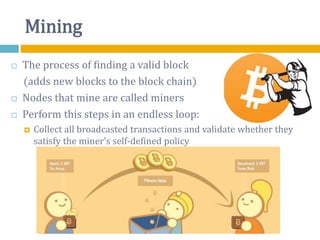
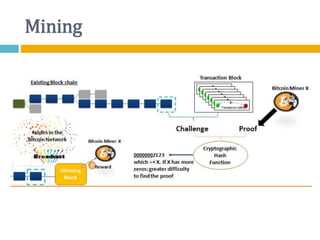
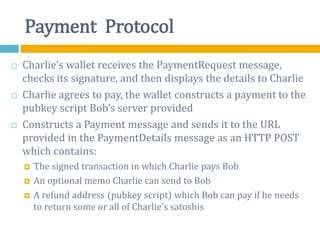
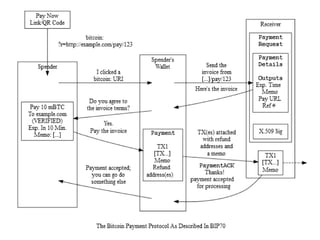
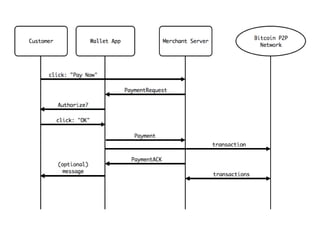
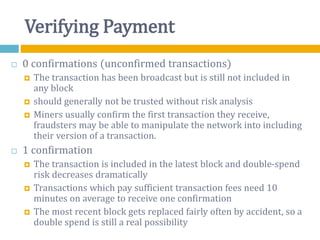
The document provides an overview of Bitcoin, including its history, key concepts, and technical aspects. It discusses how Bitcoin works as a decentralized digital currency using blockchain technology. Some key points covered include how Bitcoin is sent through peer-to-peer transactions, the role of miners in verifying transactions and creating new blocks, and how wallets are used to store public/private keys and interact with the Bitcoin network.